Terminal protecting methdo and system
A terminal protection and terminal technology, applied in the field of communication, to achieve the effect of simple and convenient
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] Functional Overview
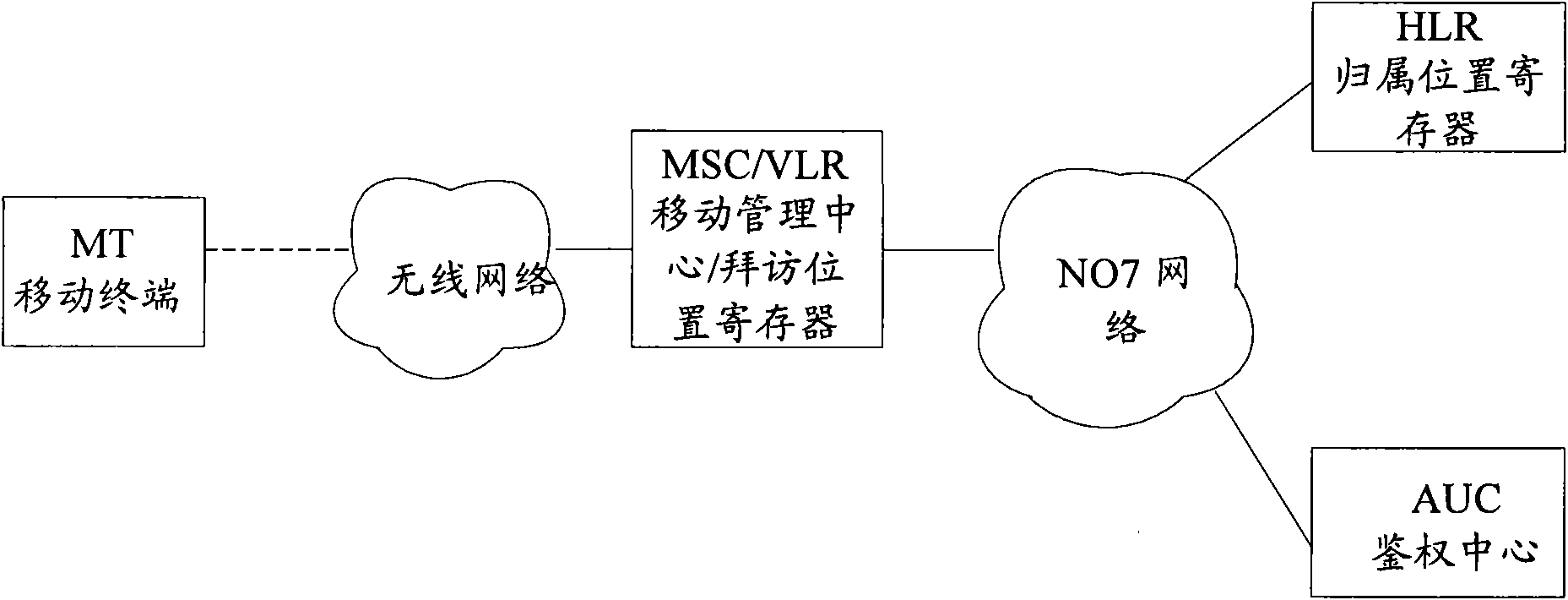
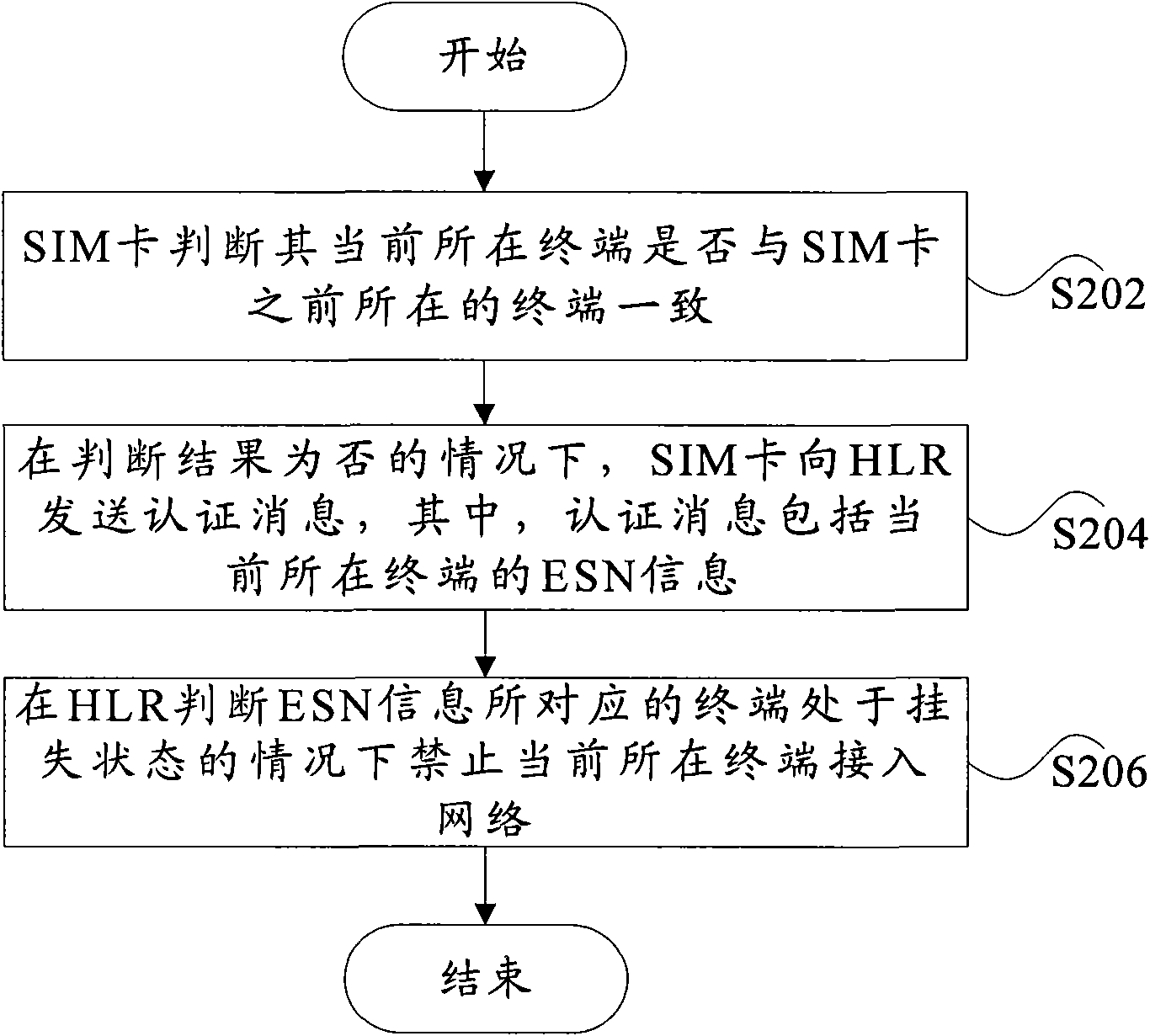
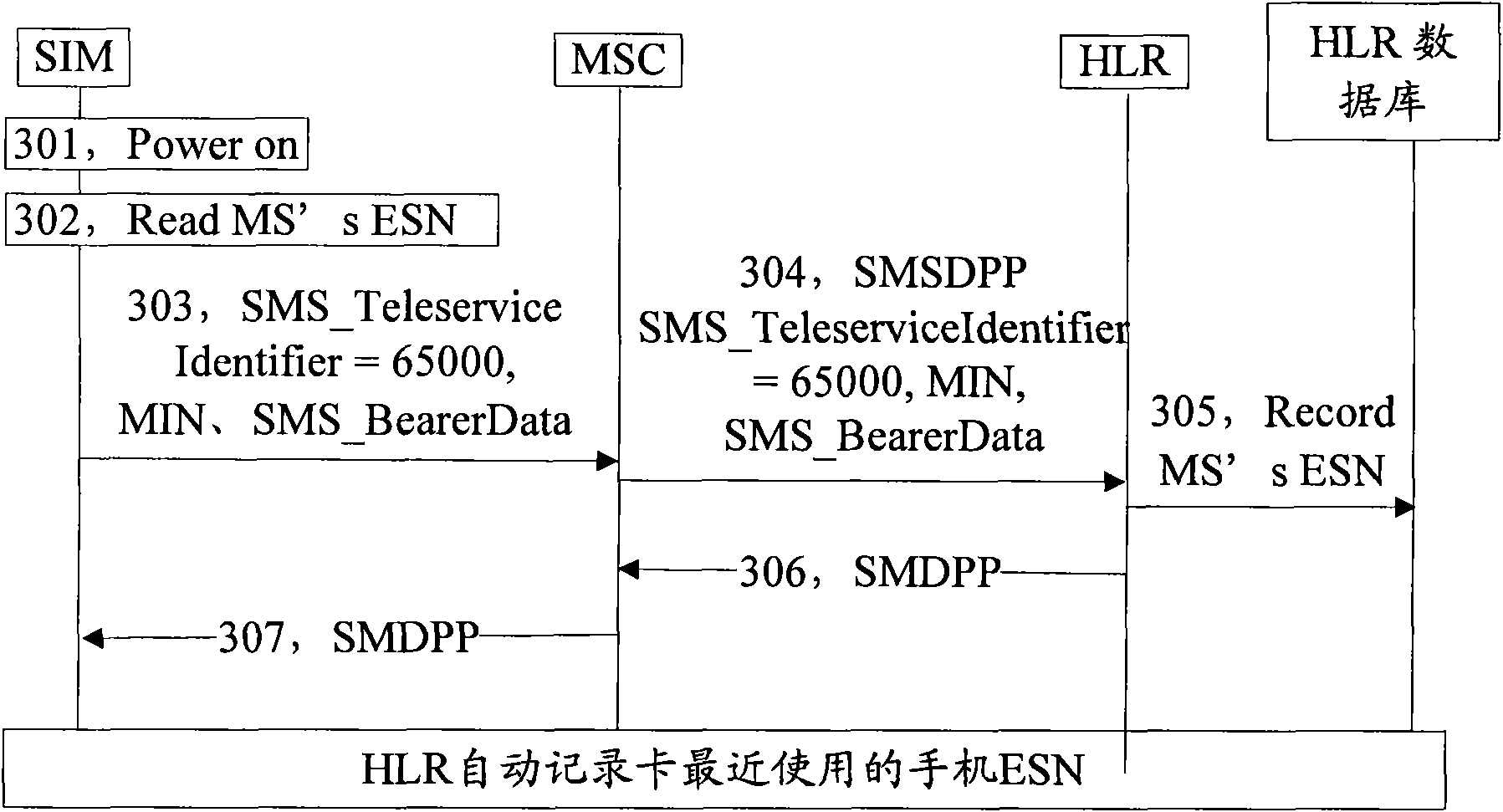
[0032] As mentioned above, since it is currently impossible to restrict the use of a terminal that supports machine-card separation after being stolen, based on this, the present invention provides an improved terminal protection scheme to simply and conveniently solve the problem of using other cards after the terminal is stolen. Questions that can be used. The basic idea of the present invention is: after the terminal (the terminal supports machine-card separation, denoted as terminal 1) is turned on, the SIM card therein judges whether the terminal 1 is consistent with the terminal where the SIM card was before, and when the judgment result is inconsistent, the SIM card Send an authentication message comprising the ESN information of the terminal 1 to the HLR, and the HLR determines the state of the terminal corresponding to the ESN information (that is, the state of the terminal 1 recorded at the HLR side) according to the authentication mess...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com