Cross-domain rights management system and method
A rights management, cross-domain technology, applied in the field of cross-domain user rights management system, can solve the problems that the application container does not provide support, increases the difficulty of system development, and is difficult to manage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
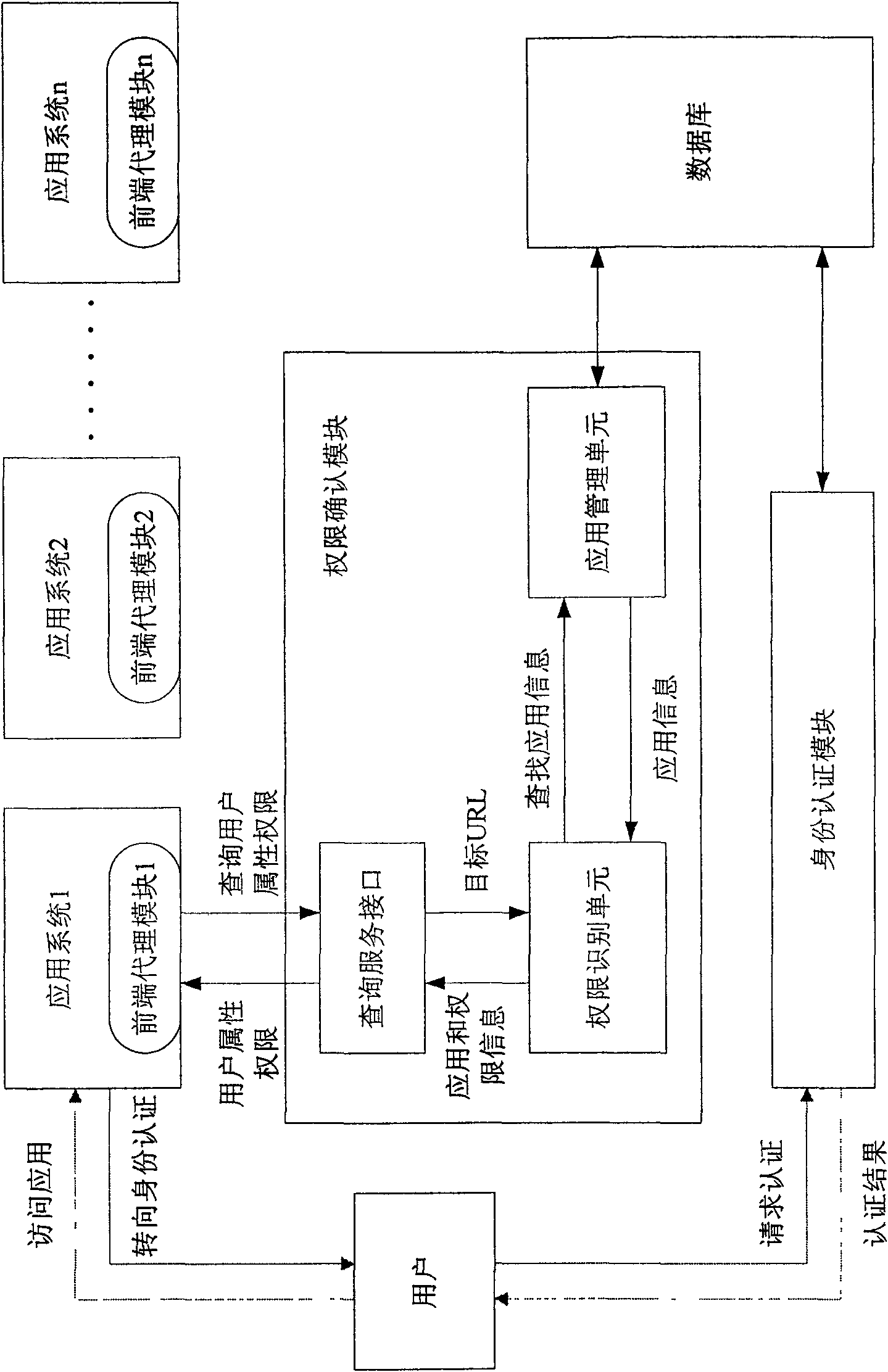
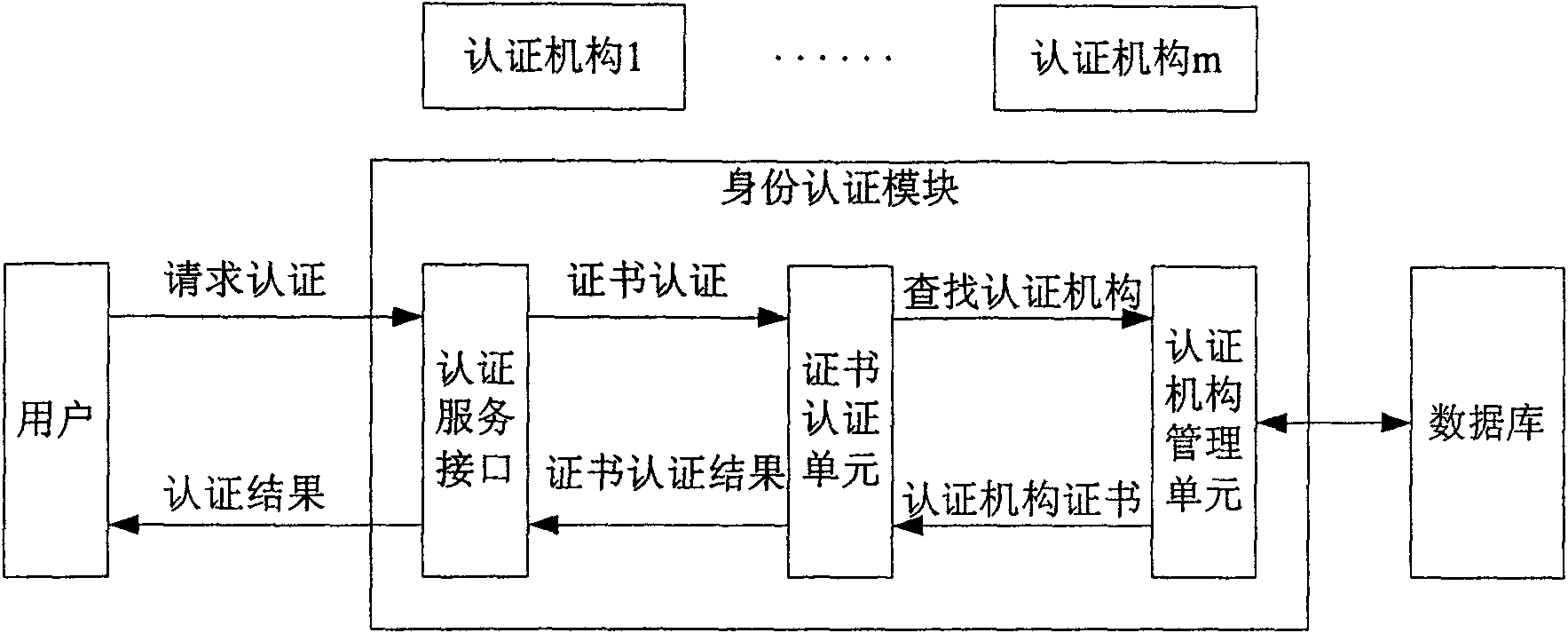
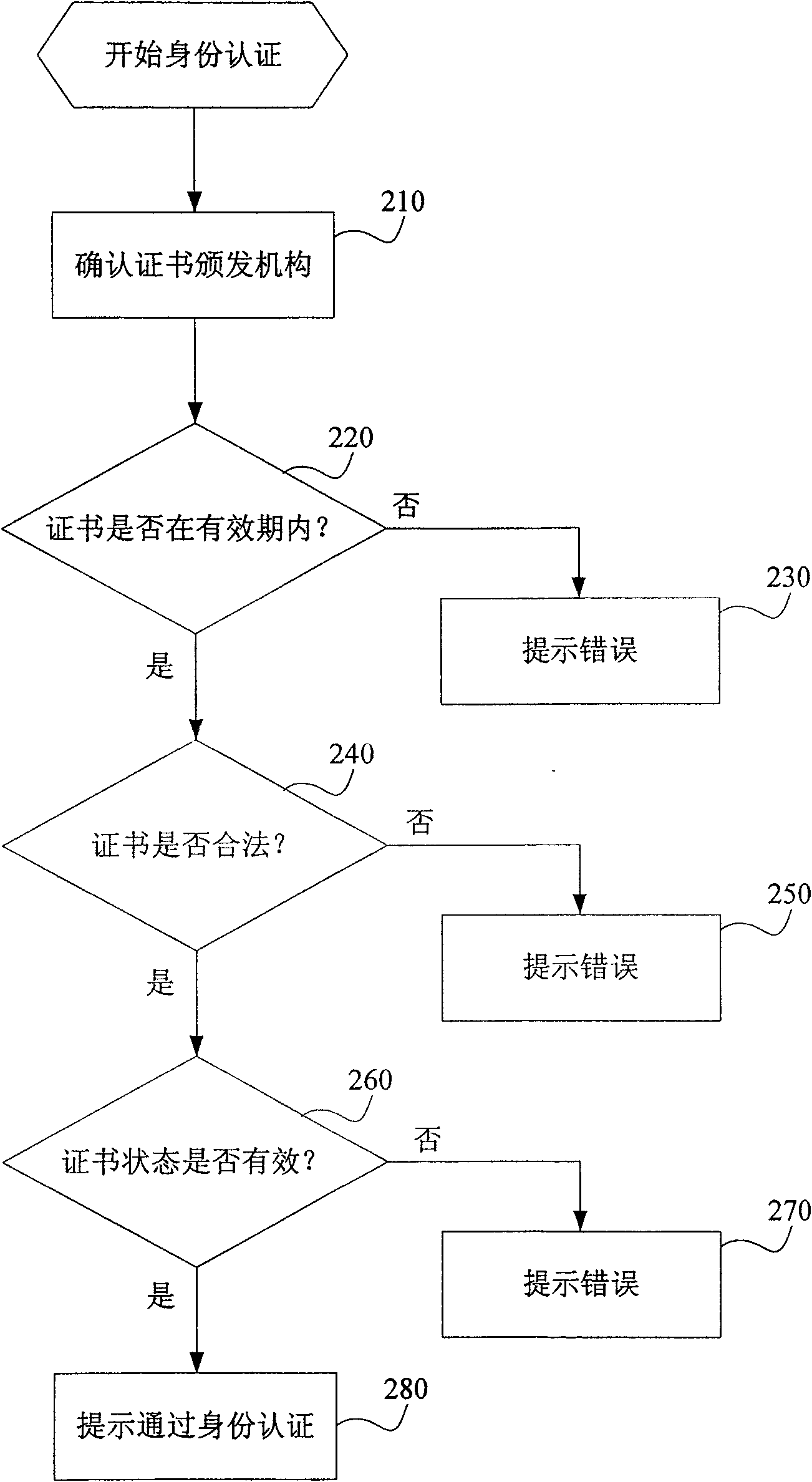
[0026] In order to enable those skilled in the art to better understand the technical solutions of the present invention, the cross-domain rights management system and cross-domain rights management method provided by the present invention will be described in detail below with reference to the accompanying drawings.
[0027]First, some terms involved in the present invention are defined. In recent years, with the rapid development of digital identity authentication technology and the popularization of national information construction, some domain concepts are often mentioned, such as security domain, trust domain, application domain and so on. In order to avoid confusion, it is necessary to define the "domain" involved in the present invention: the "domain" mentioned in the present invention includes the trust domain and the application domain, and the so-called trust domain refers to the CA institution as the basis for division, that is, Said that the units and individuals ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com