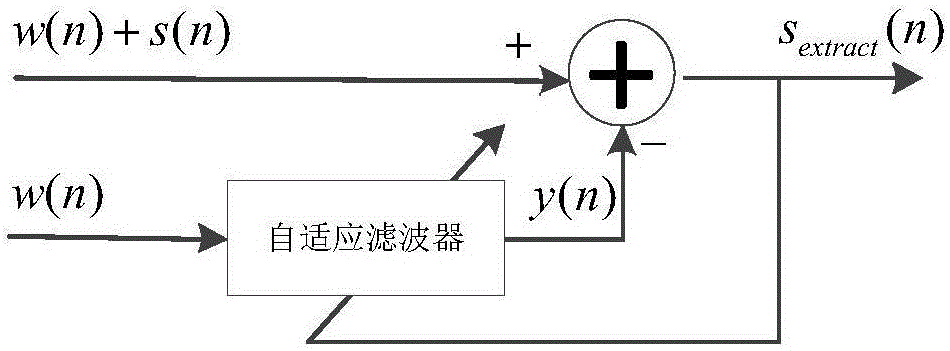
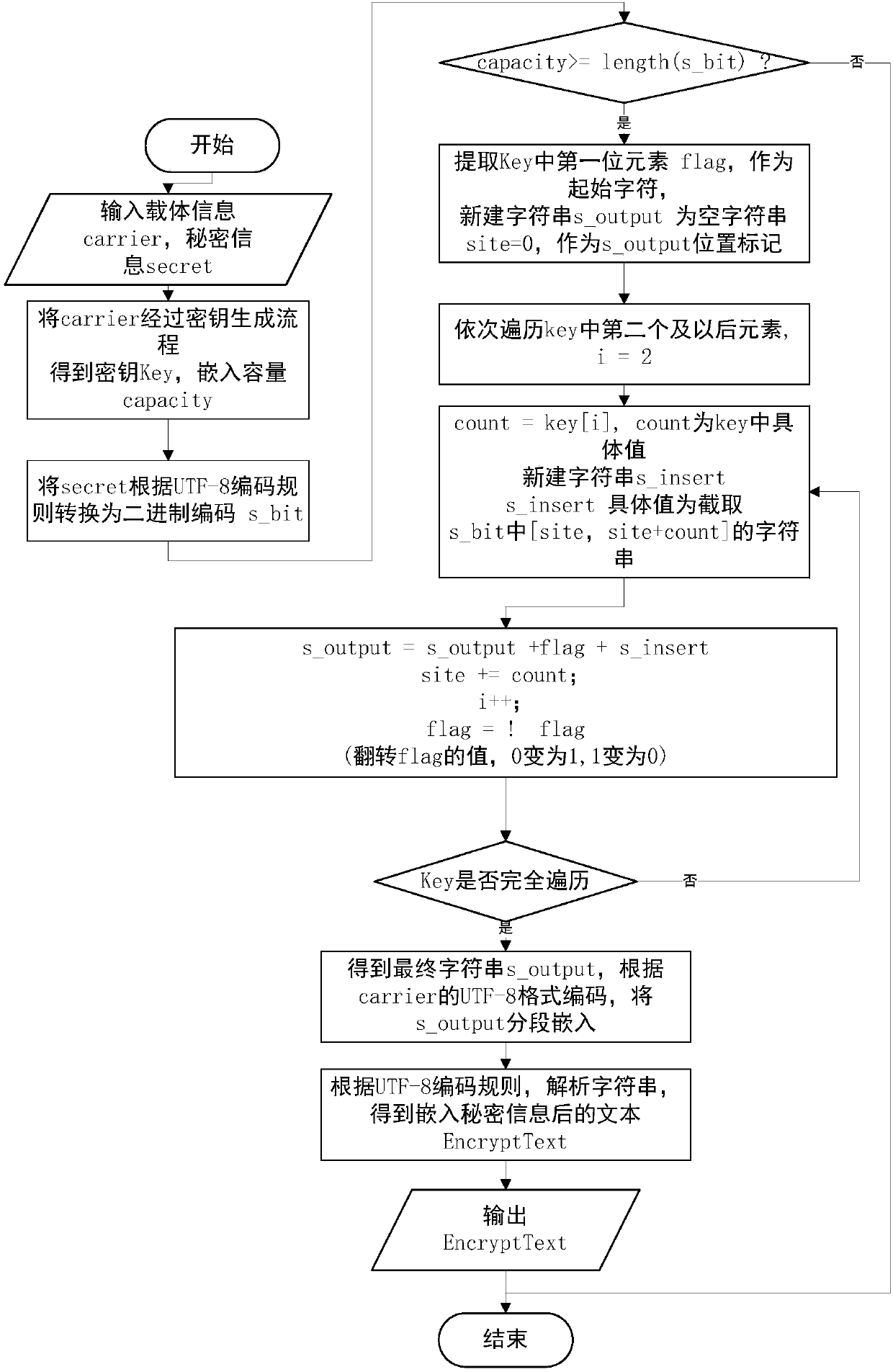
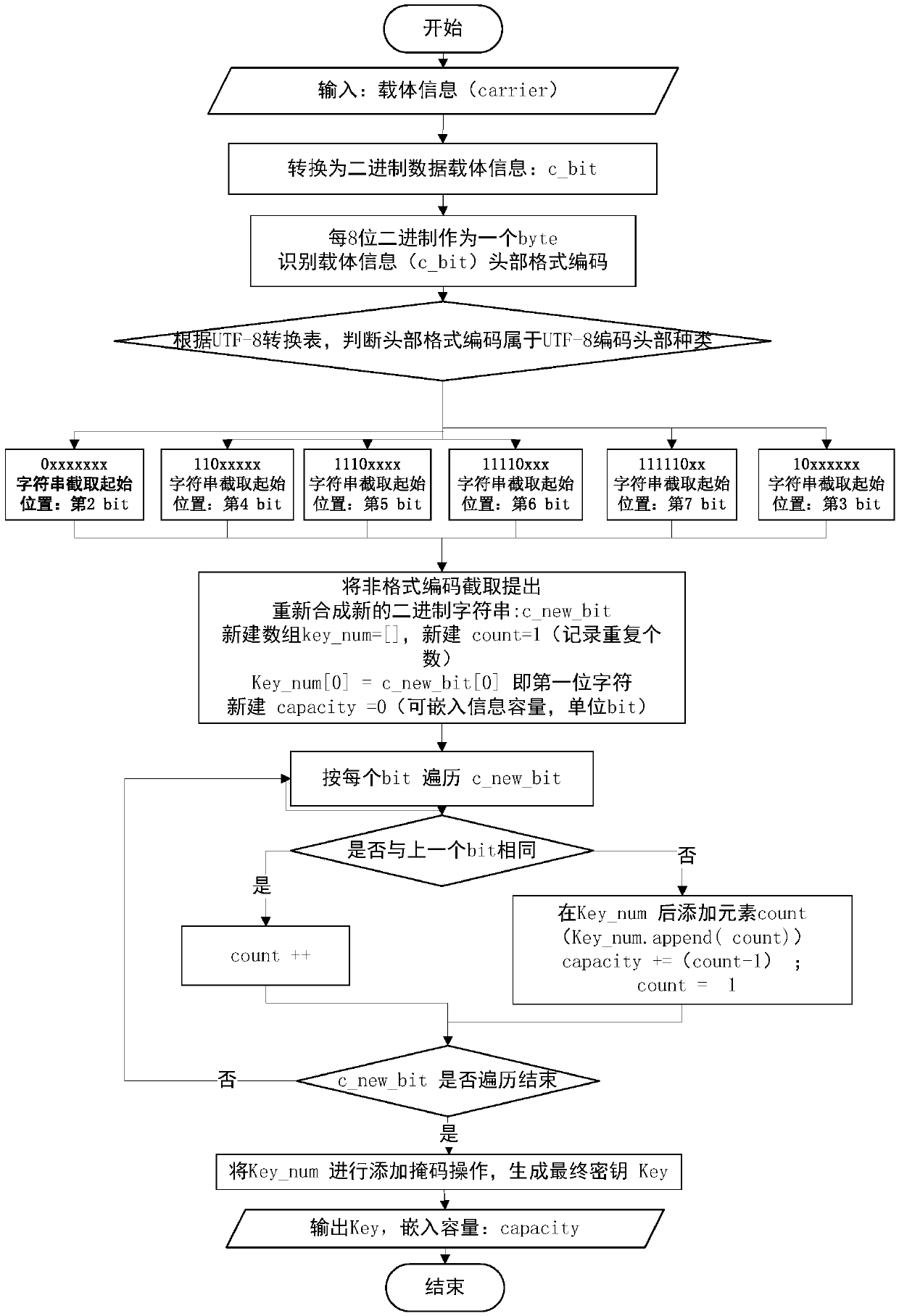
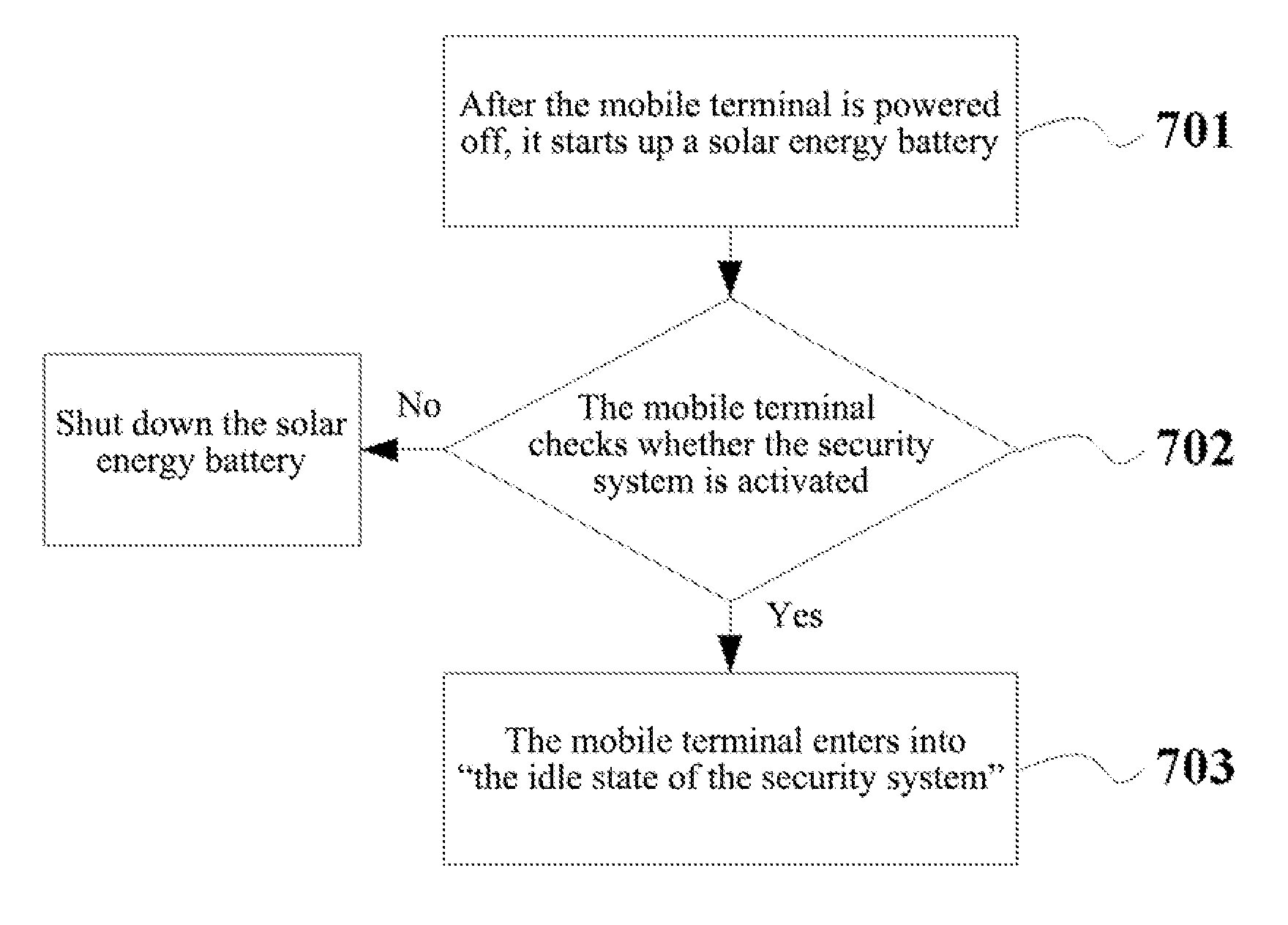
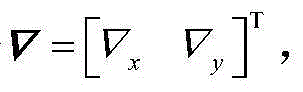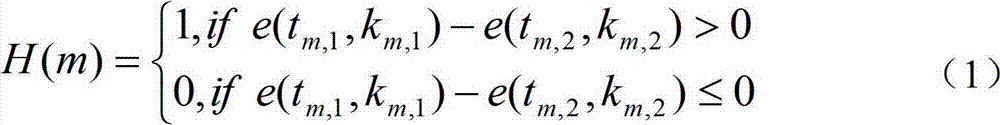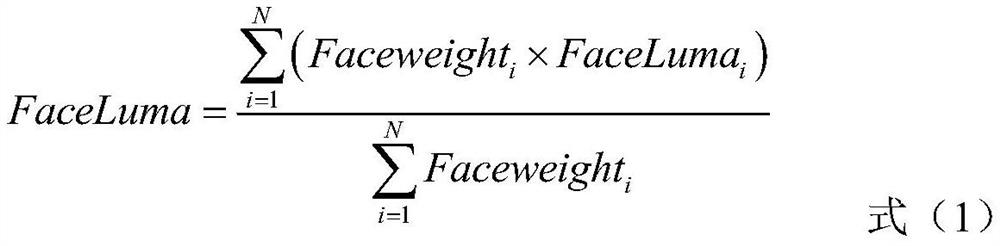Patents
Literature
165results about How to "Guaranteed concealment" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
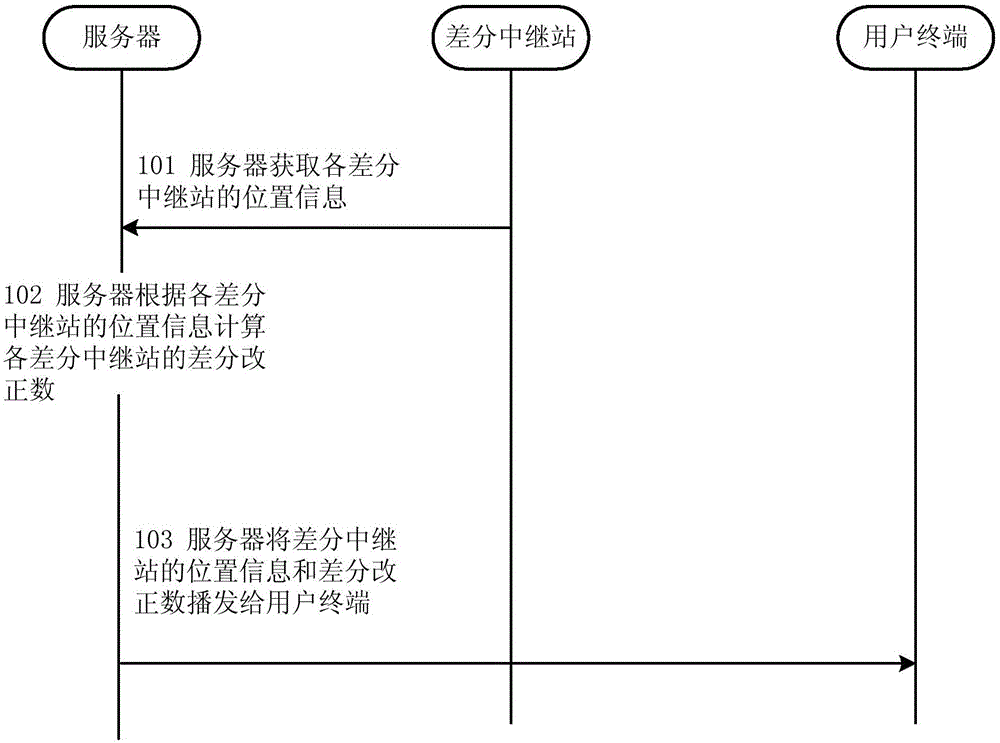
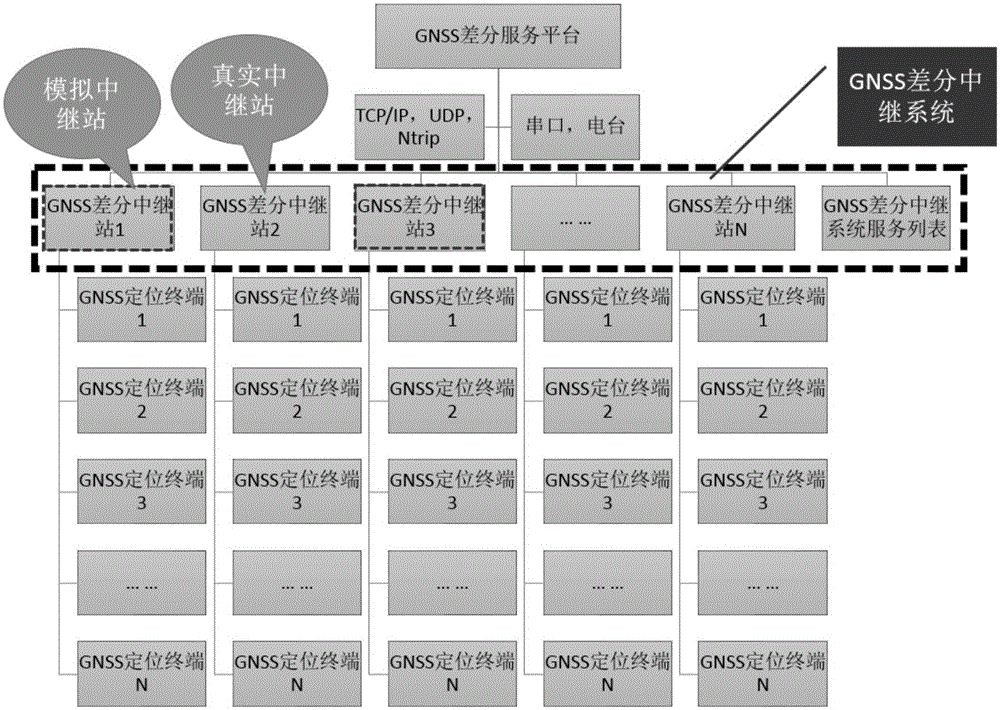
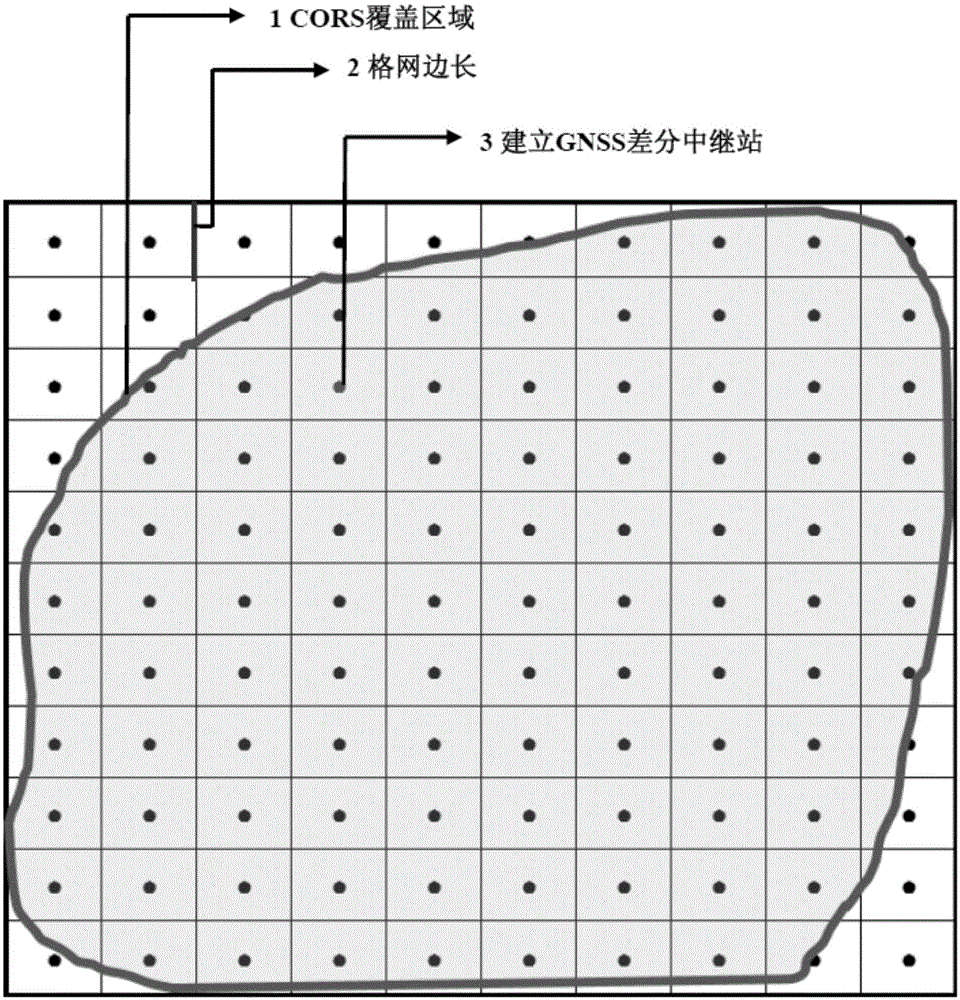
Differential relay method and device for global navigation satellite system
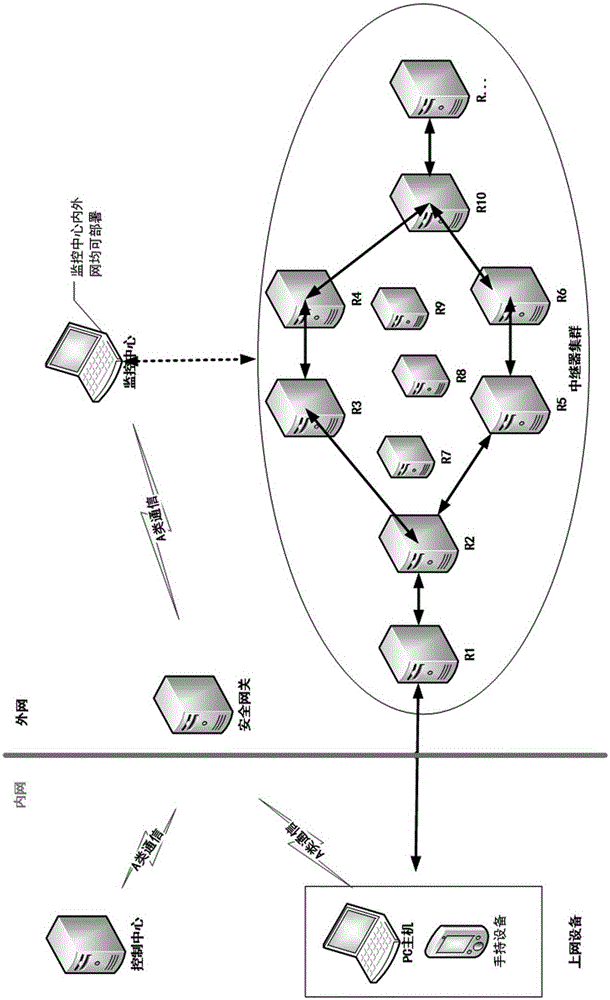
The invention relates to the technology of communication, and discloses a differential relay method and device for a global navigation satellite system. According to the invention, the method comprises the steps: enabling a transmission region of a server to be divided into a plurality of grid units, setting at least one differential relay in each grid unit; calculating a difference correction number of each differential relay through the server, and transmitting the position information of each relay and the difference correction numbers to a user terminal, so that the user terminal employs the position information and the difference correction number of the differential relay nearest to the user terminal for differential positioning, thereby facilitating the use of differential services. Moreover, the server can meet the demands of a large number of users only if the server calculates a fixed number of difference correction numbers, thereby improving the coverage and usability of the differential services. In addition, the user terminal does not need to upload the position information of the user terminal to the server, can carry out differential positioning through obtaining the difference correction number of the nearest differential relay according to the position information of each differential relay, and guarantees the crypticity of a user.
Owner:QIANXUN SPATIAL INTELLIGENCE INC
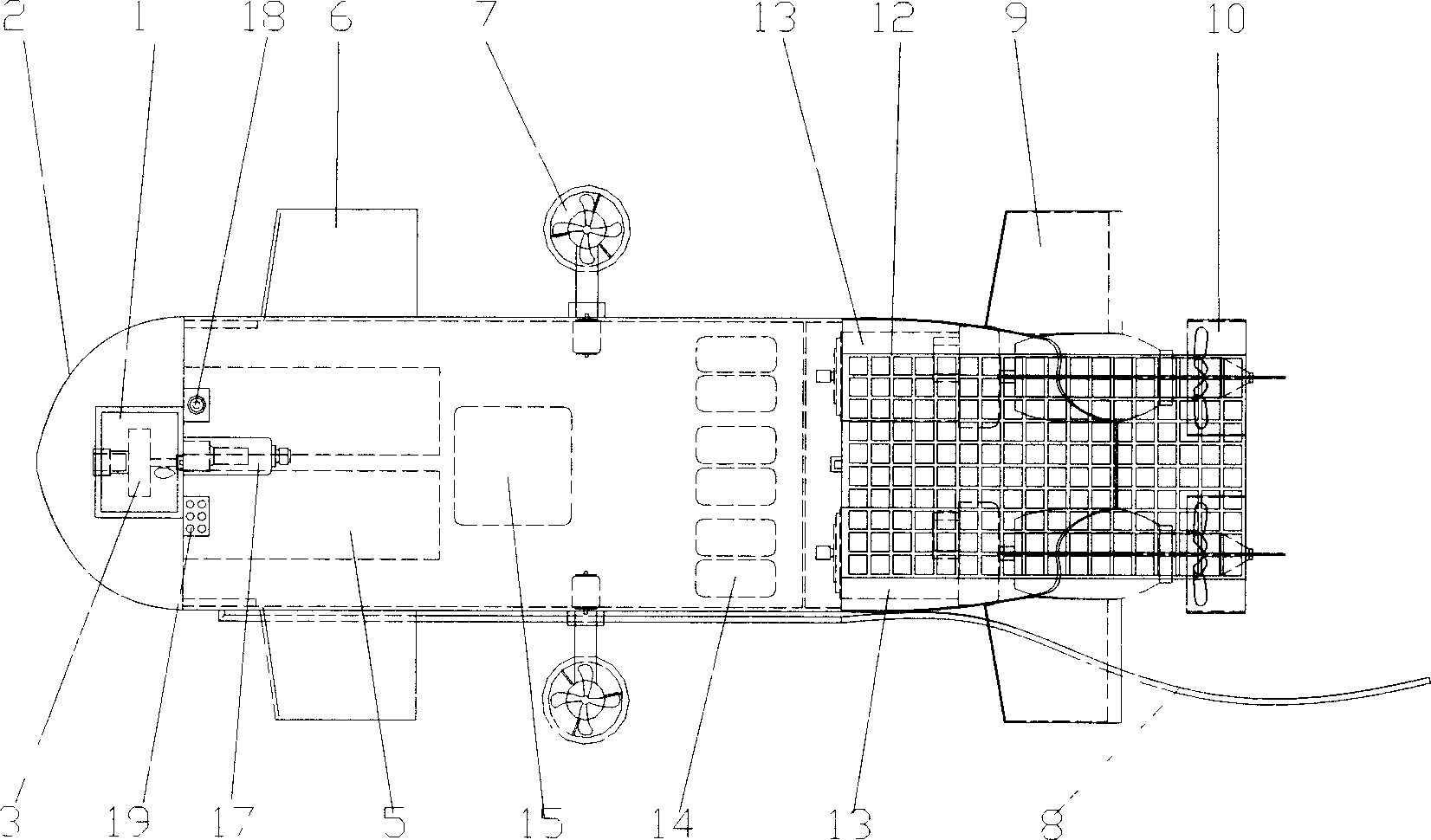
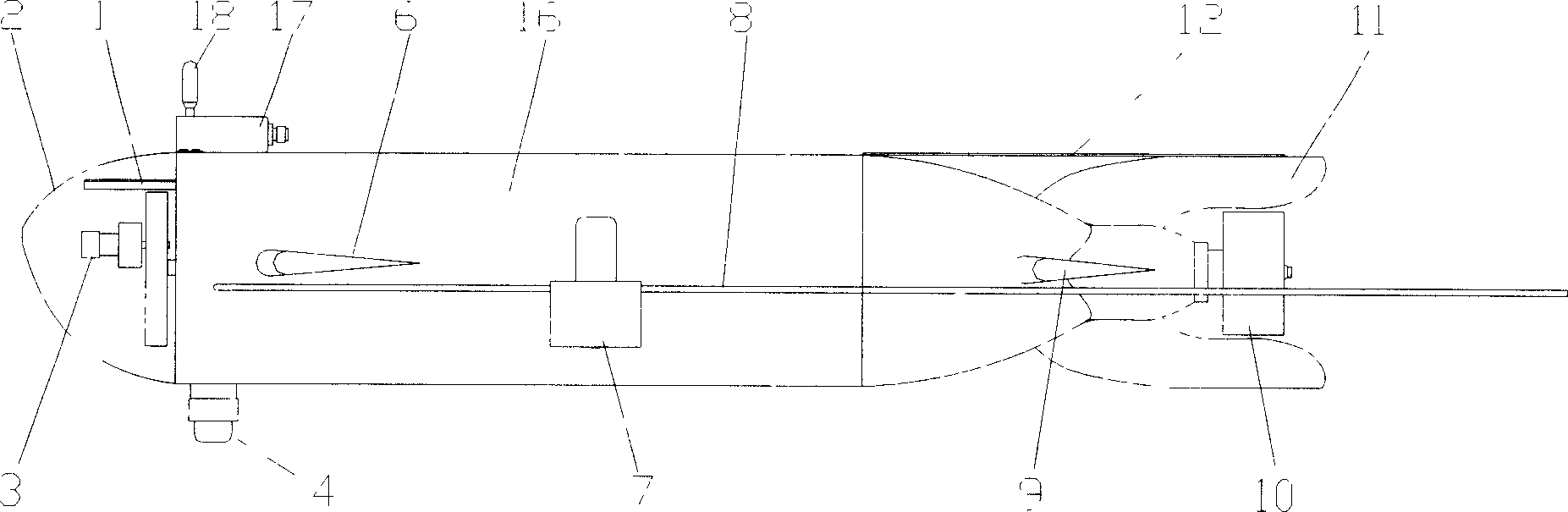
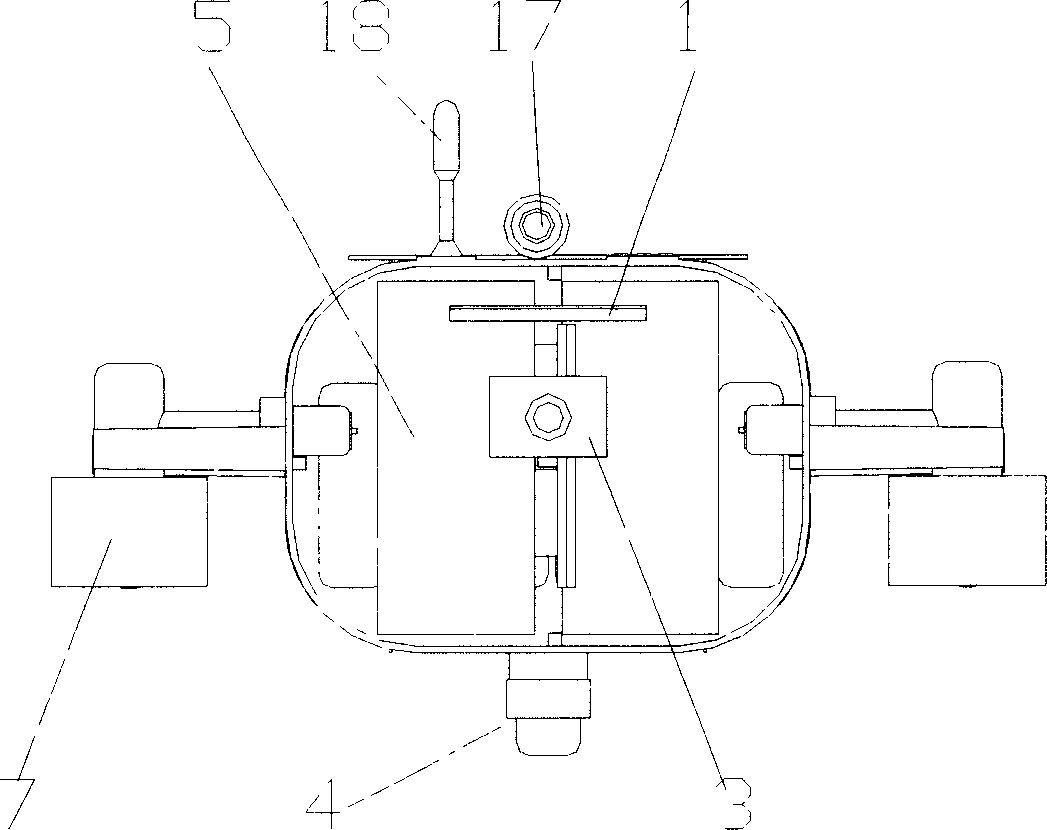
Semi-independent submersible device
InactiveCN1640765AExpand the scope of workGuaranteed real-time and concealmentUnderwater vesselsUnderwater equipmentData transmissionPropeller
The semi-autonomous submarine has water sealed hull comprising transparent pressure-proof glass cover and main hull; video camera capable of rotating in several directions and LCD screen inside the glass cover; underwater video camera, operating handle and keyboard for diver to use; imaging sonar in the bottom for detecting sea bed topography; control computer, gyroscope, cell and driving motor inside the main hull; one pair of stabilizing prow wings and one pair of stern hydroplanes for stabilizing navigation direction and regulating the depth of the submarine separately; one pair of auxiliary propellers capable of rotating in vertical planes to provide the submarine with vertical lift and auxiliary running function and horizontal steering performance; two main propellers and one pair of stern fins for stable navigation; and optical cable for the data transmission between the submarine and the mother ship.
Owner:SHANGHAI JIAO TONG UNIV
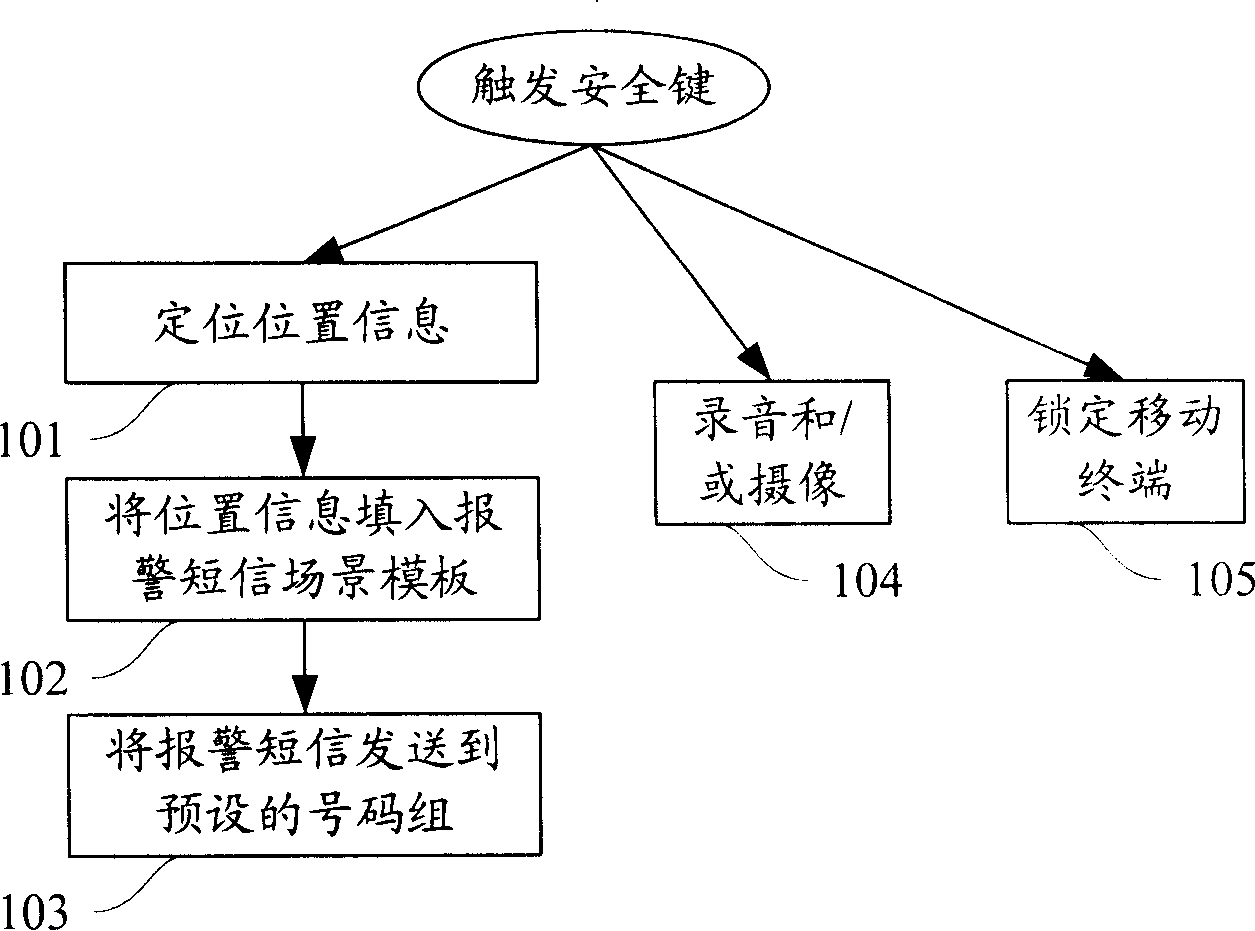
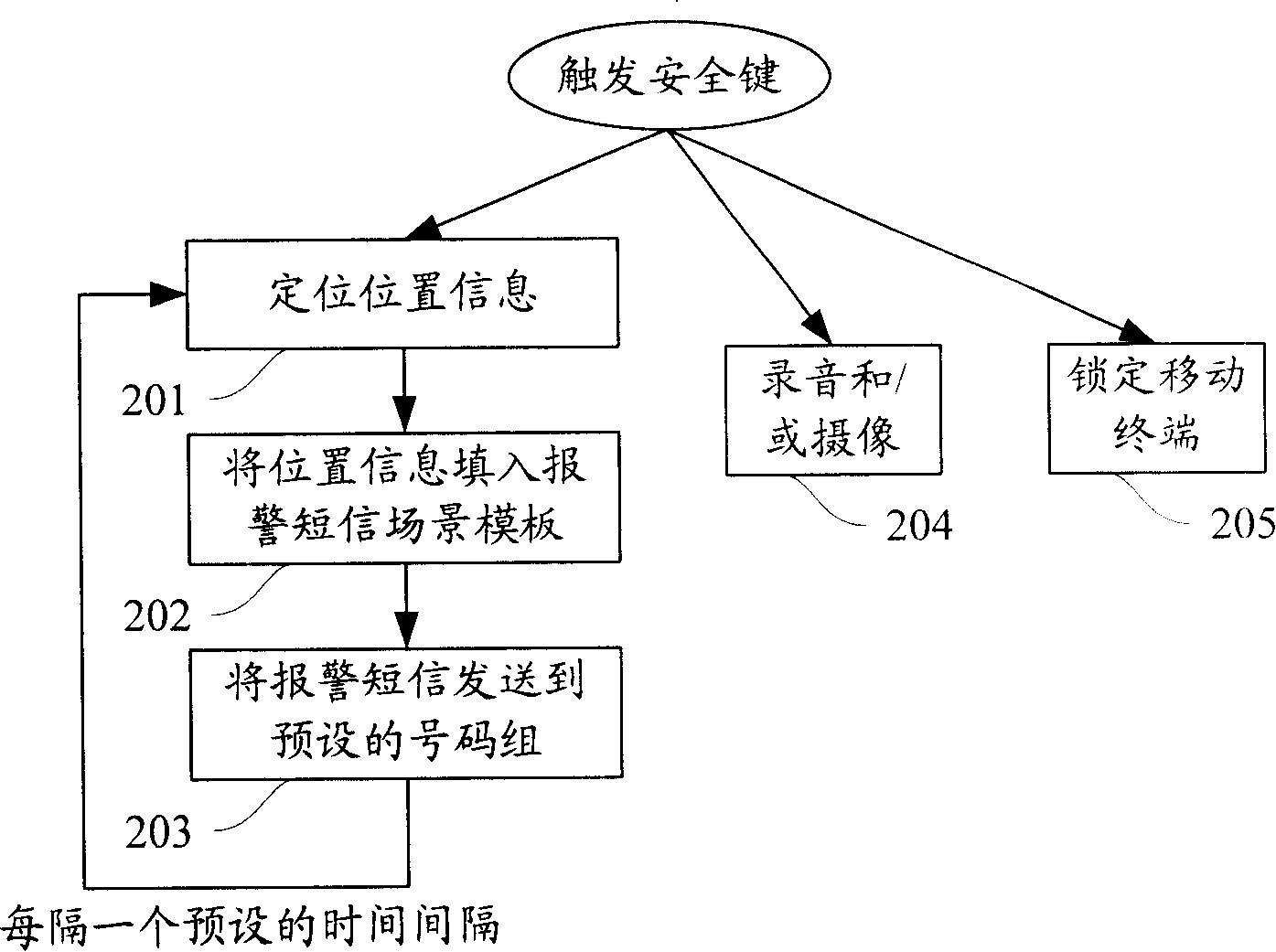
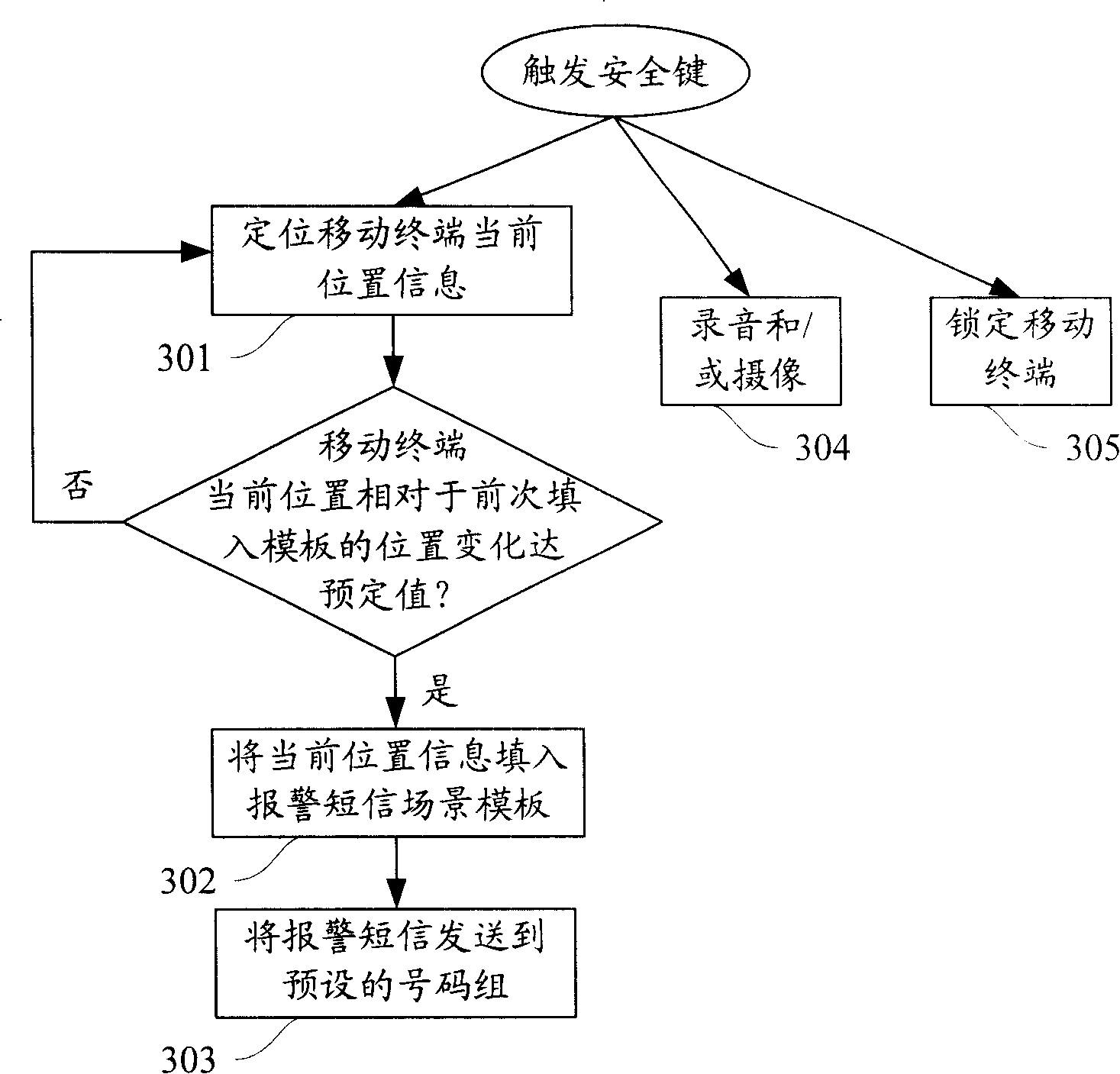
Method and device for implementing automatic alarm from mobile terminal
InactiveCN101212747AReliable alarmGuaranteed concealmentRadio/inductive link selection arrangementsTelephone set constructionsComputer science
Owner:LEADCORE TECH +2
Mixed battery pack comprising lithium power cell and super capacitor
InactiveCN101399452AGood powerExtend cycle lifeElectrical storage systemBatteries circuit arrangementsCharge voltageCapacitance
The invention discloses a mixing battery group consisting of a lithium power battery group and a super capacitor group. The mixing battery group comprises a rectifying circuit, a charging buffer circuit, a lithium power battery group consisting of a plurality of lithium power batteries, a super capacitor group consisting of a plurality of super capacitors, a main circuit of bilateral switch, an output switch and a signal collection and control circuit; the outer current or DC electrical source is connected with the input terminal of the main circuit by the rectifying circuit and the charging buffer circuit, and the output terminal of the main circuit is connected with the electric equipment by the output switch; the signal collection and control circuit comprises a controller, a bus bar voltage transducer, a lithium battery group voltage transducer, a lithium battery electric current transducer and an output current transducer. The invention can provide output of electric energy with high power and high energy stably, guarantee to be effectively connected with 220V effective value of electric equipment, and bear a certain degree of fluctuation of charging voltage and current, and guarantee the stability and convenience for electric energy supply and invisibility of power supply. The mixing battery group is characterized by small volume and convenient carrying.
Owner:刘云海 +2
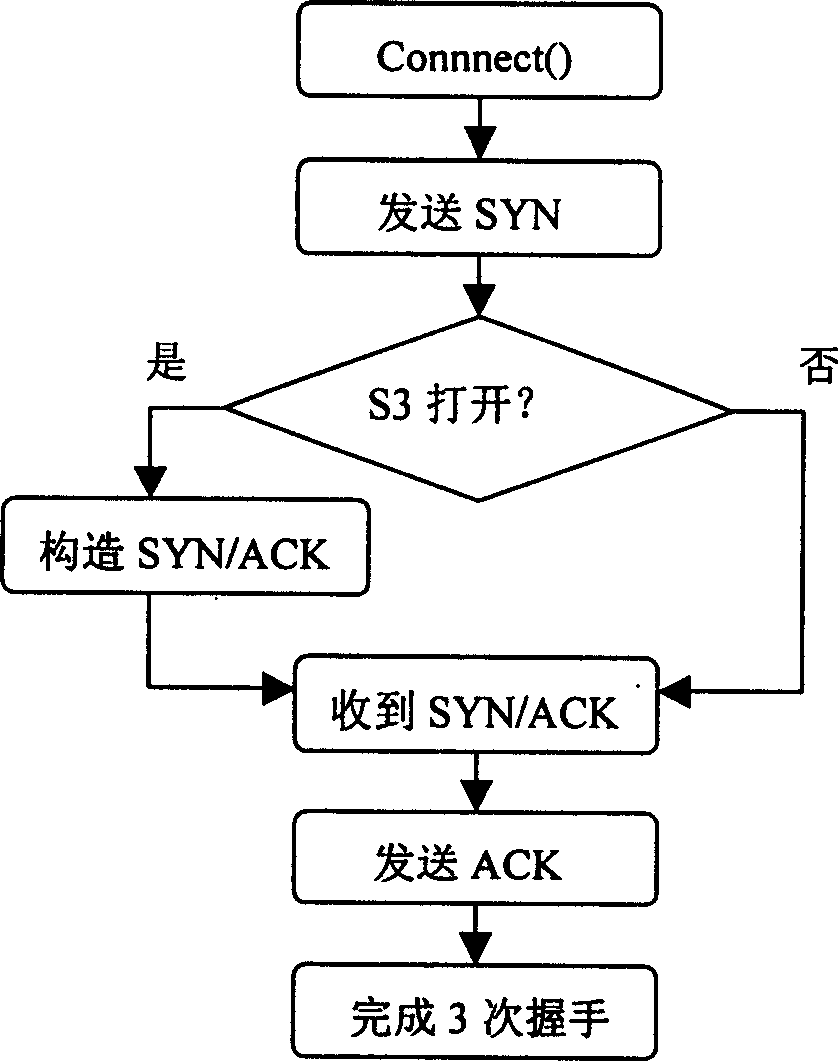
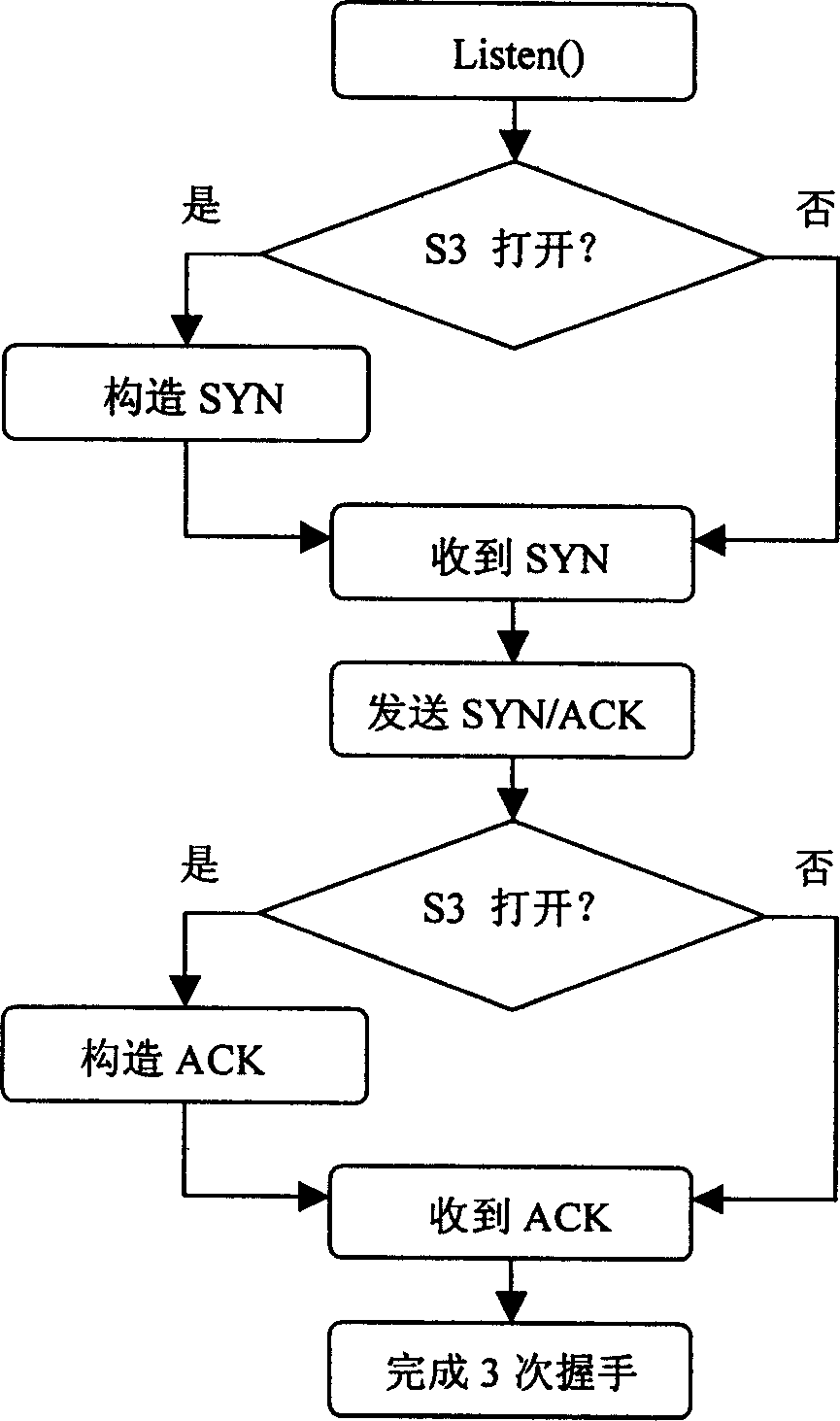
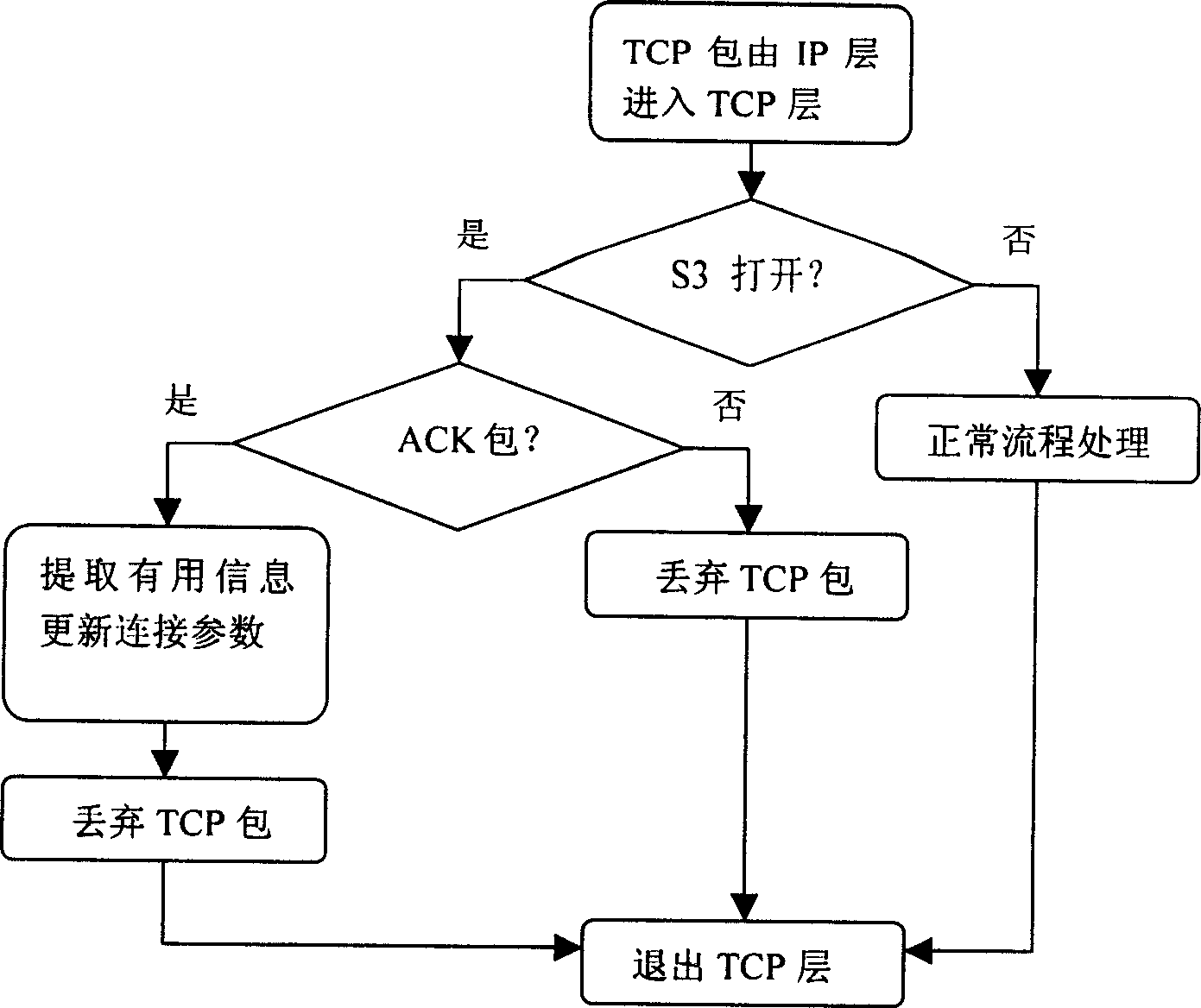
A method for primary and standby machine to take turns on TCP connection
InactiveCN1567919AEnsure continuityGuaranteed concealmentTransmissionNetwork communicationProtocol stack
The invention discloses a method of master and backup machines applies TCP to switch TCP connection as communicating with remote-end machine, thus effectively avoiding the interruption of the TCP connection with remote-end machine as the master and backup machines switch between them, not influencing the continuity of the communication with the remote-end machine and making the remote-end machine not sense the switching course. It makes a certain small-rage reformation on traditional TCP protocol stack to adapt to the requirement of realizing the invention. It can be widely applied to the master-backup machine network communication by TCP.
Owner:XIAN DATANG TELECOM
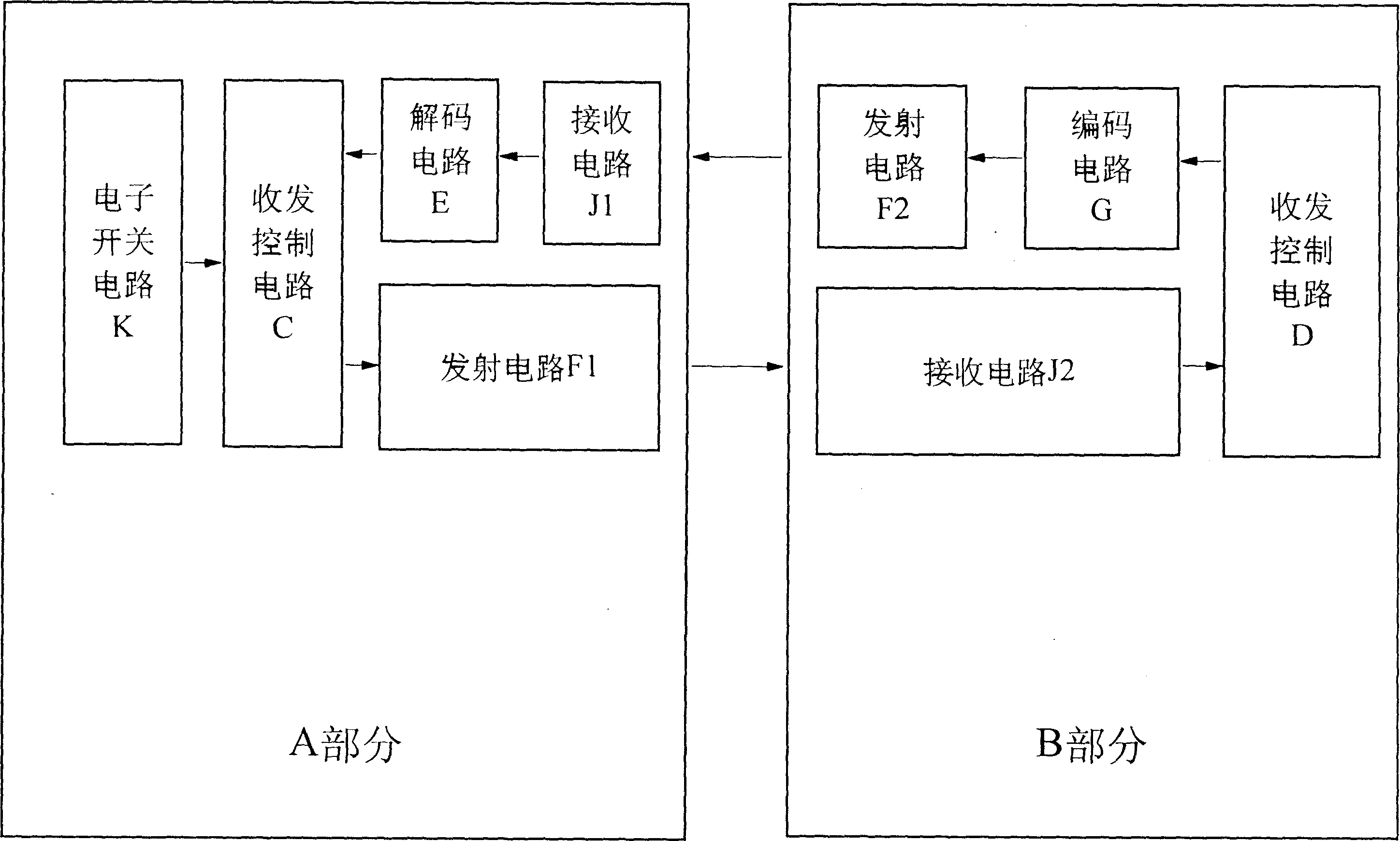
Concealed electronic cipher remote controller
InactiveCN1232936CImprove concealmentGuaranteed concealmentElectric signal transmission systemsSecuring communicationTransceiverRemote control
The invention provides an invisible electronic password remote controller, which belongs to an anti-theft device in the technical field of electronic information. It consists of a host installed on a door or other controlled parts and an electronic key on the user's body. The host includes an electronic switch circuit, a transceiver control circuit, a transmitter circuit, a receiver circuit and a decoding circuit; the electronic key includes a transmitter and receiver control circuit, a transmitter circuit, a receiver circuit and an encoding circuit. The user touches the electronic switch circuit on the host, and its transceiver control circuit controls the transmitting circuit to emit a specific signal. After receiving and confirming the electronic key, another specific password is sent, and the host receives and confirms and then outputs a control signal to open the door lock or other equipment. It has changed the one-way confirmation control mode in which the remote control transmits the password and the host outputs the control signal after receiving it, but the control purpose can only be achieved after the host and the electronic key two-way confirm, which improves the security and concealment of the electronic password remote control. performance, reducing cost and energy consumption.
Owner:舒涛
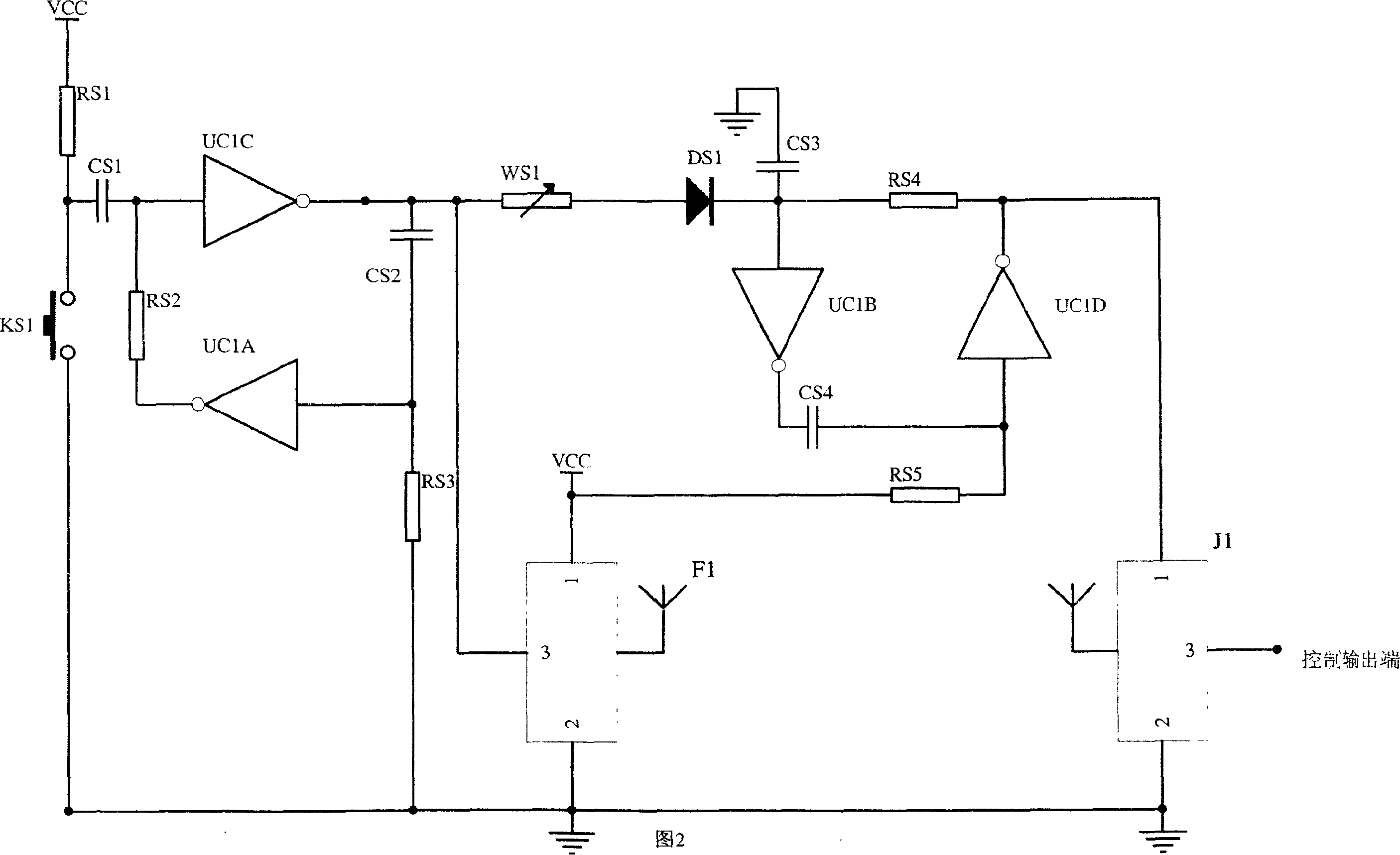
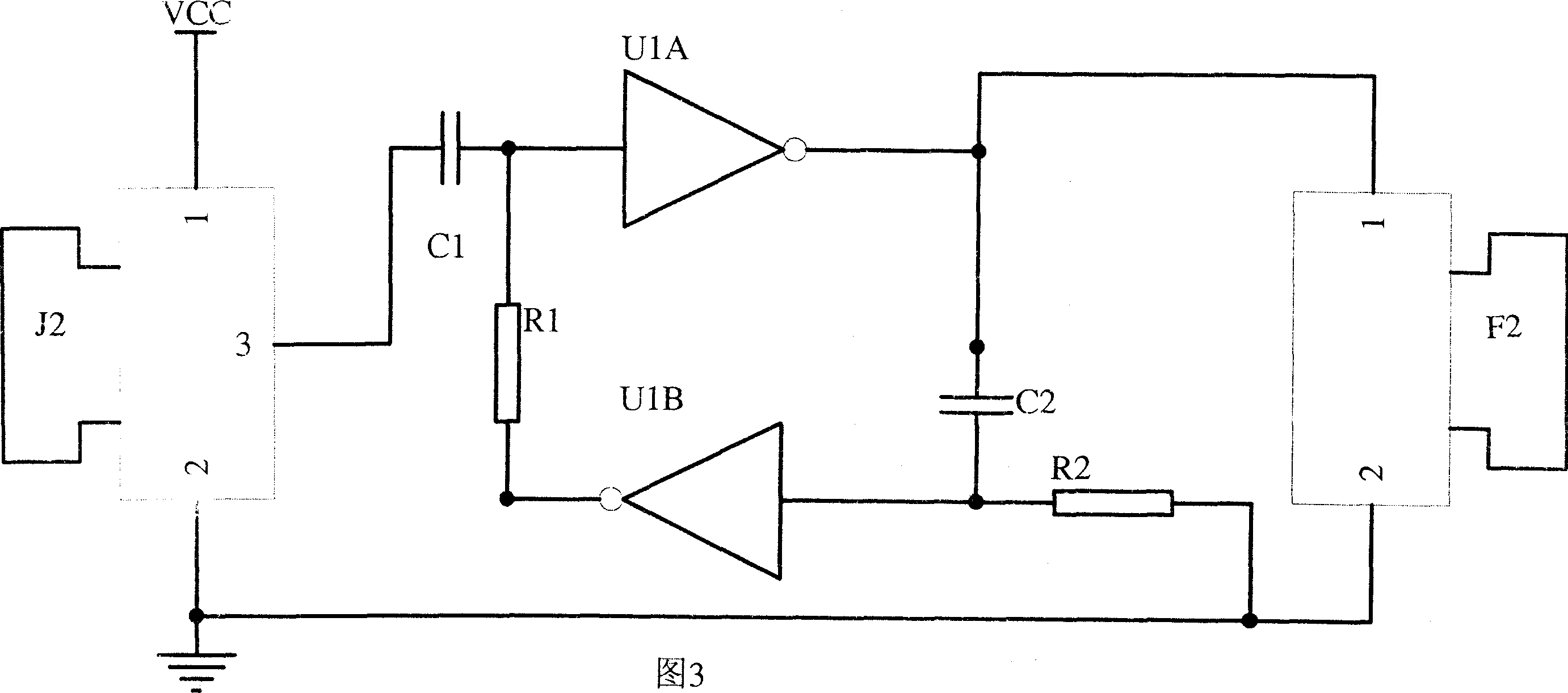
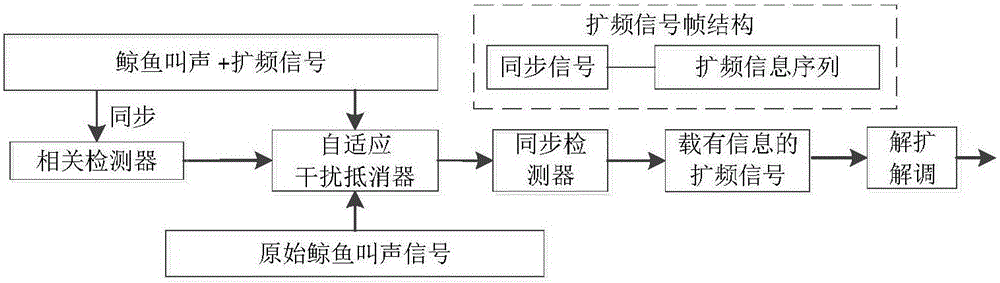
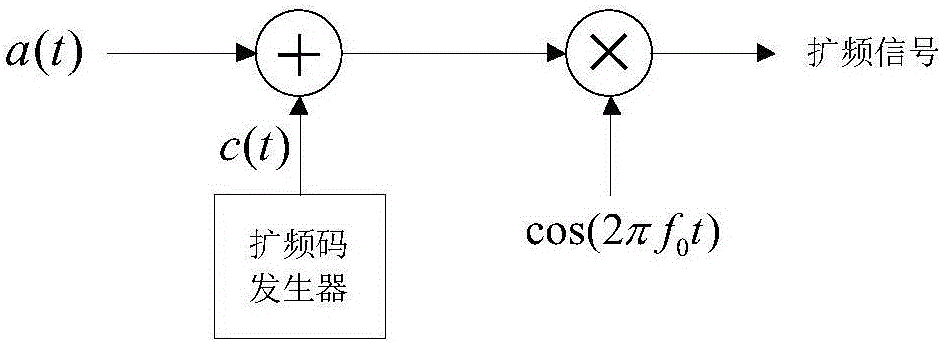
Whale-sound-imitating covert underwater sound communication method based on self-adaptive interference cancellation
ActiveCN105871475AImprove concealmentGuaranteed concealmentSonic/ultrasonic/infrasonic transmissionTransmission noise suppressionCommunications systemDirect-sequence spread spectrum
The invention belongs to the technical field of underwater sound communication and particularly relates to a whale-sound-imitating covert underwater sound communication method based on self-adaptive interference cancellation. The method comprises steps as follows: a proper whale sound signal is selected, the time frequency characteristic of the whale sound signal is analyzed, and a proper time frequency interval is selected for spread spectrum signal concealment; digital information source information is modulated into a direct sequence spread spectrum signal, and the frequency range of the spread spectrum signal is required to be within the frequency band range of the whale sound signal; the spread frequency signal produced in step (2) and the whale sound signal selected in step (1) are summed up to form a bionic communication signal and the like. The whale-sound-imitating covert underwater sound communication method based on self-adaptive interference cancellation is simple, easy to implement, high in reliability and capable of guaranteeing the covert property and safety of communication information and well meeting the requirement of a covert underwater sound communication system.
Owner:HARBIN ENG UNIV
Two-dimensional code information hiding method based on run-length coding
ActiveCN109657769AAvoid the possibility of exposureImprove securityKey distribution for secure communicationRecord carriers used with machinesInformation CardEncoding algorithm
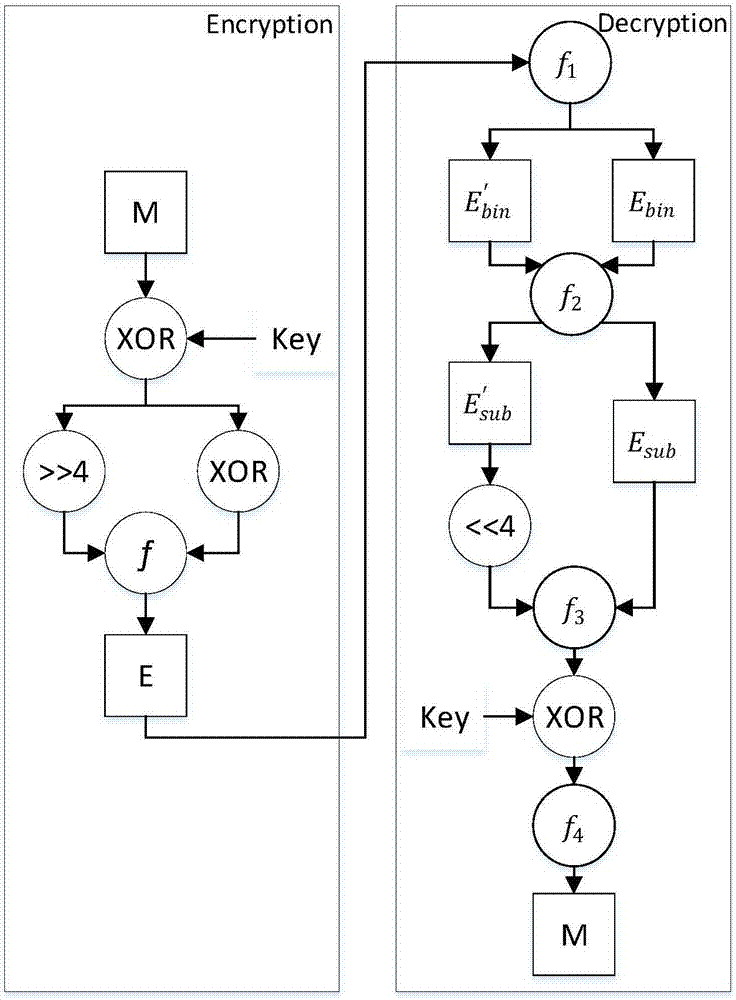
The invention discloses a run length coding-based two-dimensional code information hiding method. The method comprises the following steps of: simultaneously processing carrier information carrier andsecret information set; Before a two-dimensional code is generated, embedding secret information secret to be encrypted into carrier information card through an encryption algorithm, then generatingencrypted information into a two-dimensional code image QR, and genertaing a key Key; enabling The sender to send the two-dimensional code image QR to a receiver; And after receiving the QR of the two-dimensional code image, enabling the receiver to decrypt the QR through a decryption algorithm to obtain carrier information carrier and secret information set. And compressing the text information by adopting a run-length coding algorithm to obtain bits in which information can be embedded, thereby achieving the encryption purpose of the invention. The two-dimensional code information hiding method based on run-length coding has the advantages of being large in transmitted information amount, good in information concealment, high in robustness and compression resistance, high in safety and the like.
Owner:ANHUI UNIVERSITY
Mobile Terminal Capable of Being Tracked and Located and Method for Tracking and Locating
ActiveUS20120040640A1Guaranteed concealmentEfficient solutionEnergy efficient ICTUnauthorised/fraudulent call preventionComputer hardwareElectricity
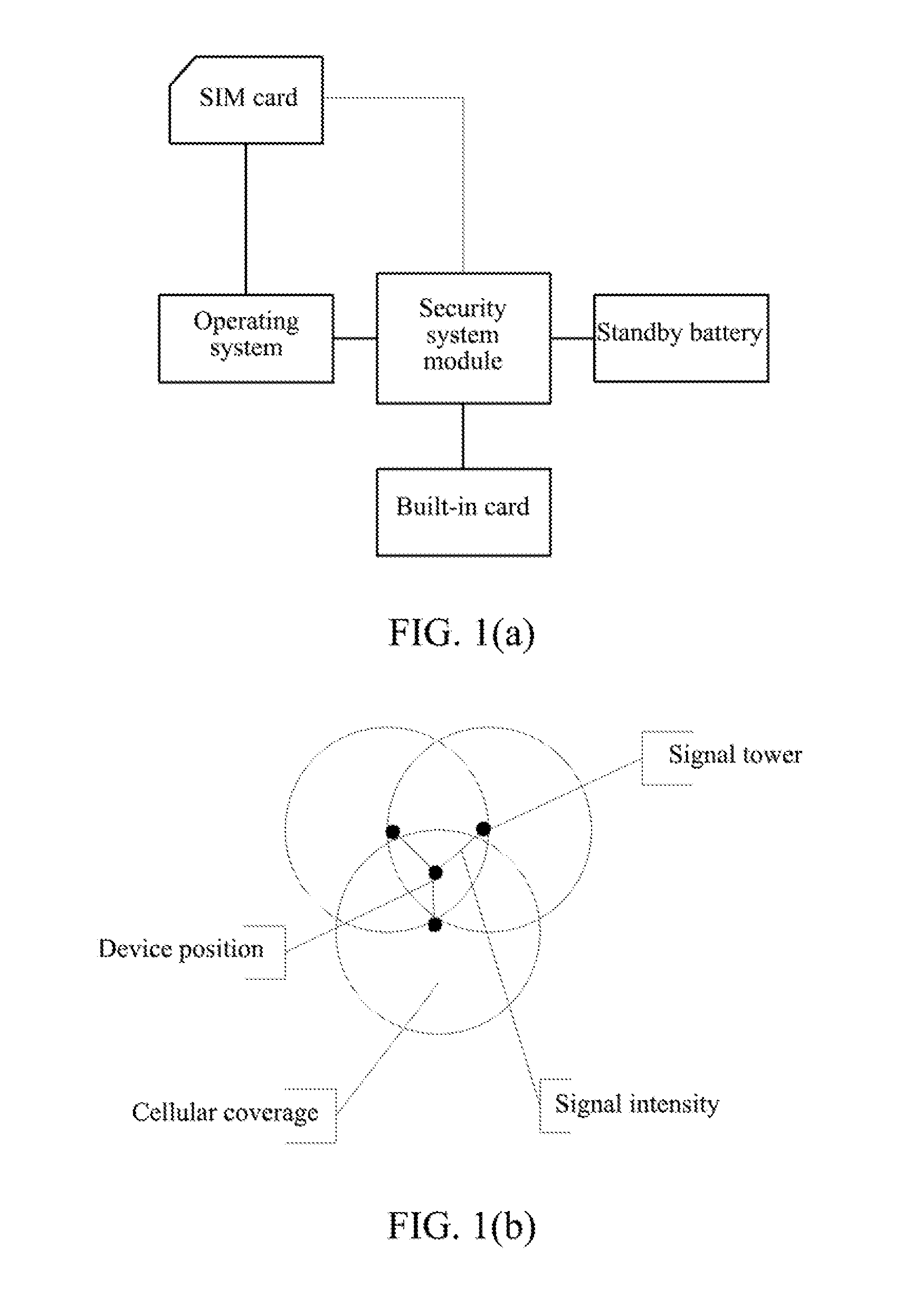
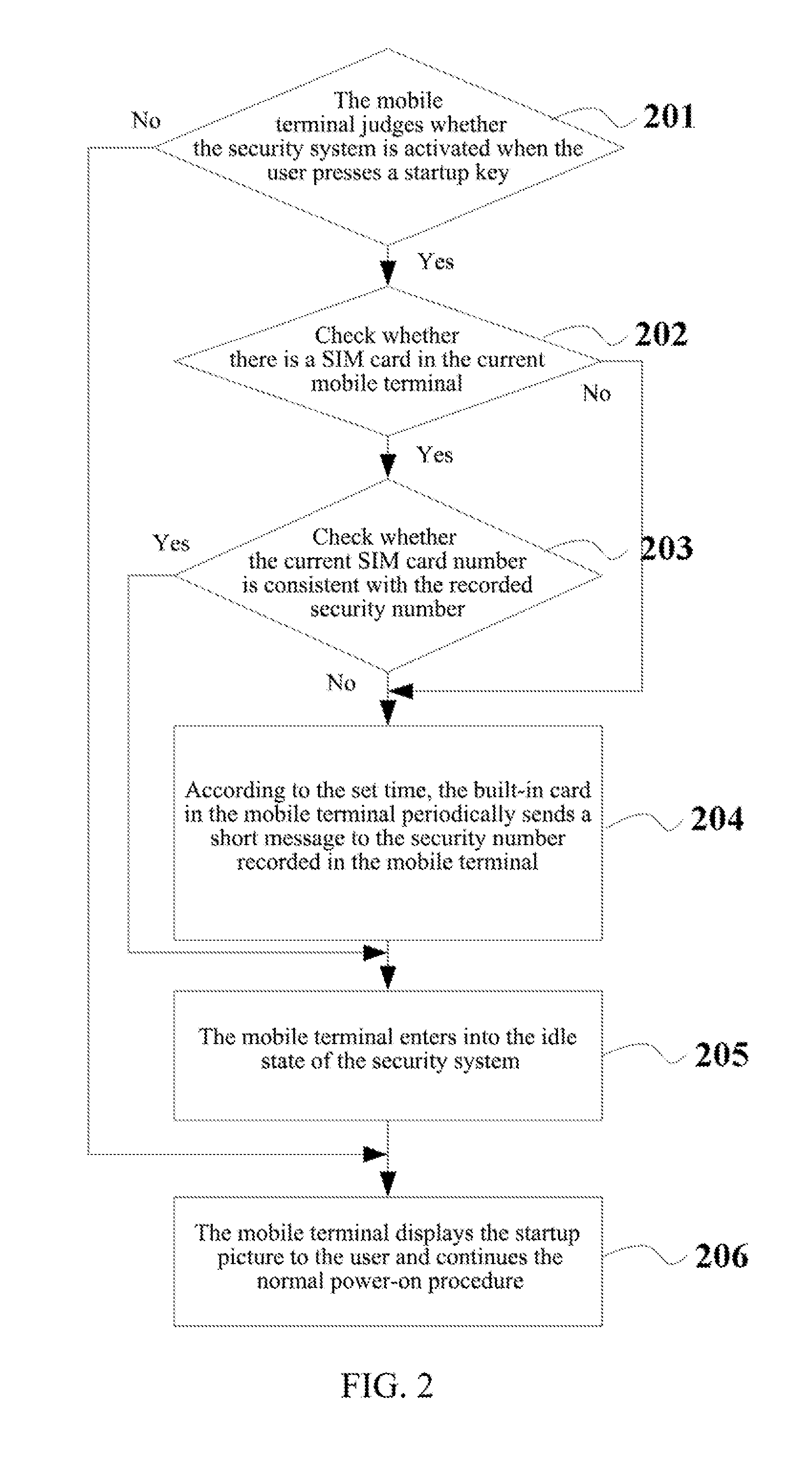
A mobile terminal capable of being tracked and located is disclosed, comprising a built-in card and a security system module which are connected with each other. The security system module generates a short message used for tracking and locating when receiving an incoming call request or a short message sent by the built-in card, wherein the short message at least carries an identification of a cellular tower interacting with the built-in card and information of current signal intensity, and the short message is sent into the built-in card; the built-in card sends the received incoming call request or the short message to the security system module and periodically sends the short message used for tracking and locating generated by the security system module to the set security number. A corresponding method is also provided. The security system is good at cover-up to bring the advantages of security and saving electricity.
Owner:DRNC HLDG INC
Touch panel
InactiveCN105426025AReduce thicknessGuaranteed concealmentInput/output processes for data processingTouch panelMaterials science
The invention relates to a touch panel. The touch panel comprises a touch sensing layer and a cover plate, wherein the touch sensing layer comprises a silver nanowire electrode and a routing region corresponding to the silver nanowire electrode; a routing material of the routing region is a silver nanowire; the cover plate is positioned on the touch sensing layer and comprises a visual region and a coverage region; the coverage region is formed by coating the periphery of at least one edge of the visual region with a color coating; and the thickness of the color coating is less than 10 microns. The color coating of the touch panel can well cover the routing region, so that the touch panel has the characteristic of a colorful appearance.
Owner:TPK TOUCH SOLUTIONS (XIAMEN) INC
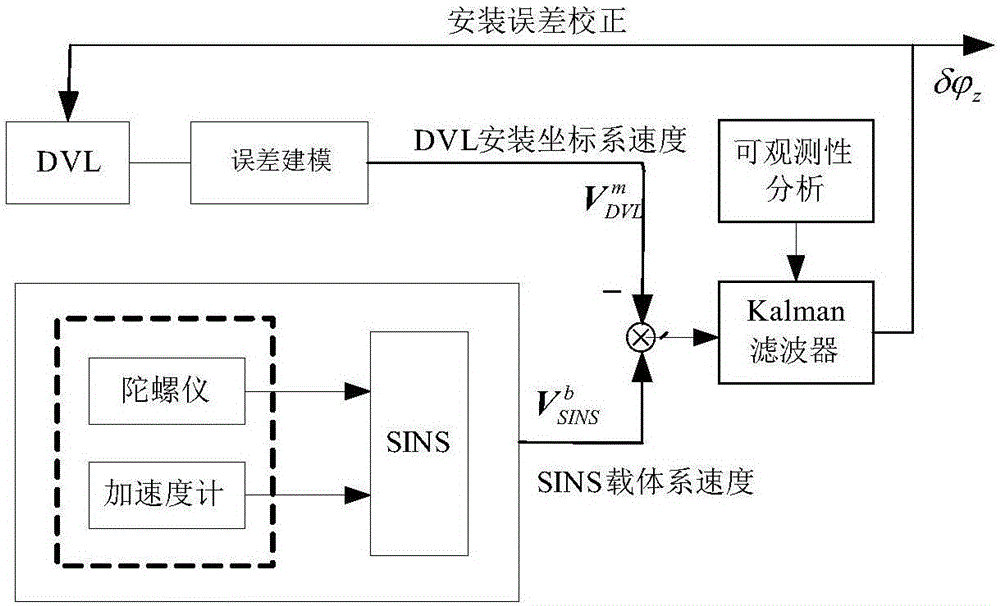
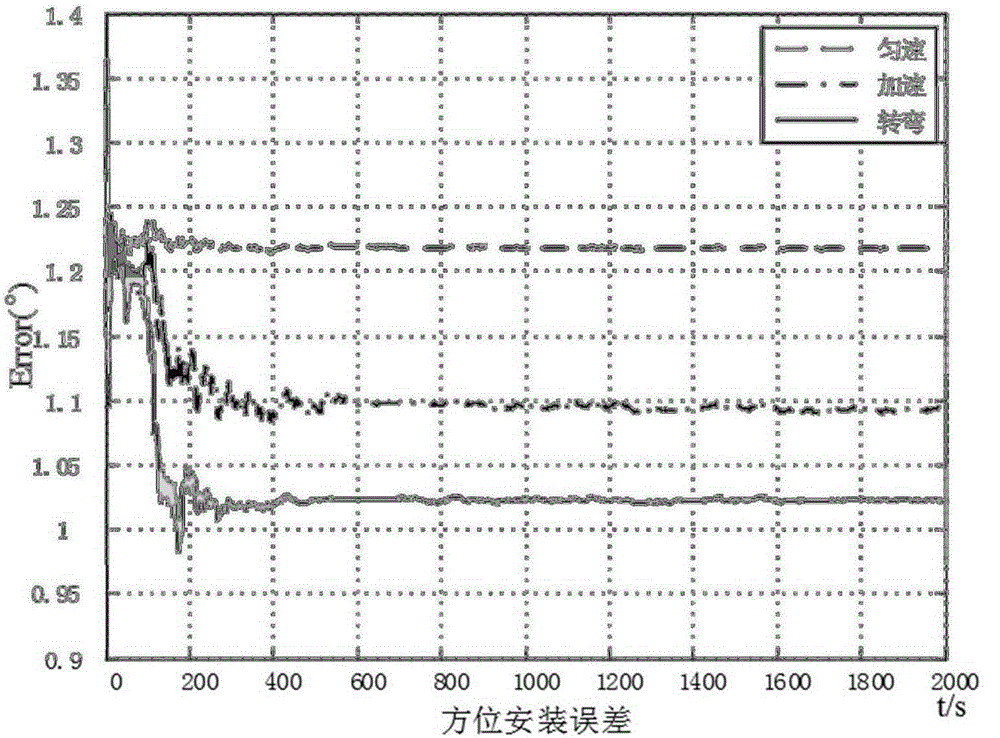
Estimation method of installation error of DVL direction in SINS and DVL combination
ActiveCN105091907AEasy to install errorsGuaranteed concealmentMeasurement devicesGyroscopeAccelerometer
The invention discloses an estimation method of an installation error of a DVL direction in an SINS and DVL combination. The method comprises the steps that an SINS speed error, an attitude error, a position error, an accelerometer null bias, a gyroscope null bias, a DVL scale coefficient error and the installation error of the direction of an IMU in a DVL and an SINS are selected to serve as state vectors, and a system state equation is established; a difference value of the SINS load system speed and the DVL installation coordinate system speed is selected to serve as a measurement vector, and a system measurement equation is established; a Kalman filter serves as an SINS and DVL information fusion filter; turning motion is selected to obtain the best observable degree of the SINS and DVL direction installation error, thus, the best estimation effect is achieved. According to the estimation method of the installation error of the DVL direction in the SINS and DVL combination, an external GPS is not needed for reference to assist in navigation information, the DVL speed does not need to be converted to a navigation coordinate, and the feasible plan of improving the direction installation error estimation performance can be selected according to the observability analysis results.
Owner:SOUTHEAST UNIV
Safe and rapid anonymous network communication method and system
ActiveCN105306483AEnsure safetyGuaranteed concealmentTransmissionTelecommunications linkNetwork communication
The invention belongs to the technical field of network security communications, and particularly relates to a safe and rapid anonymous network communication method and system. According to the method, random change of a communication port and branching and converging functions of a communication link are realized according to a thought based on UDP (User Datagram Protocol) penetration, so that a large confusion flow can be generated in a small system; a function similar to a P2P acceleration function is realized; and a one-way transmission can be performed. In the system, uniform centralized authorization management is adopted for all system network resources, so that access of illegal third-party resources is prevented. A type A communication is adopted between a control center and Internet access equipment, so that the security of the control center is ensured effectively. A mobile monitoring center is deployed movably, and actively detects a state of a relay server, so that large-area node exposure caused by malicious node exposure is effectively avoided.
Owner:XIAMEN ANSCEN NETWORK TECH CO LTD
Agent-free client process protection method based on virtualization technology
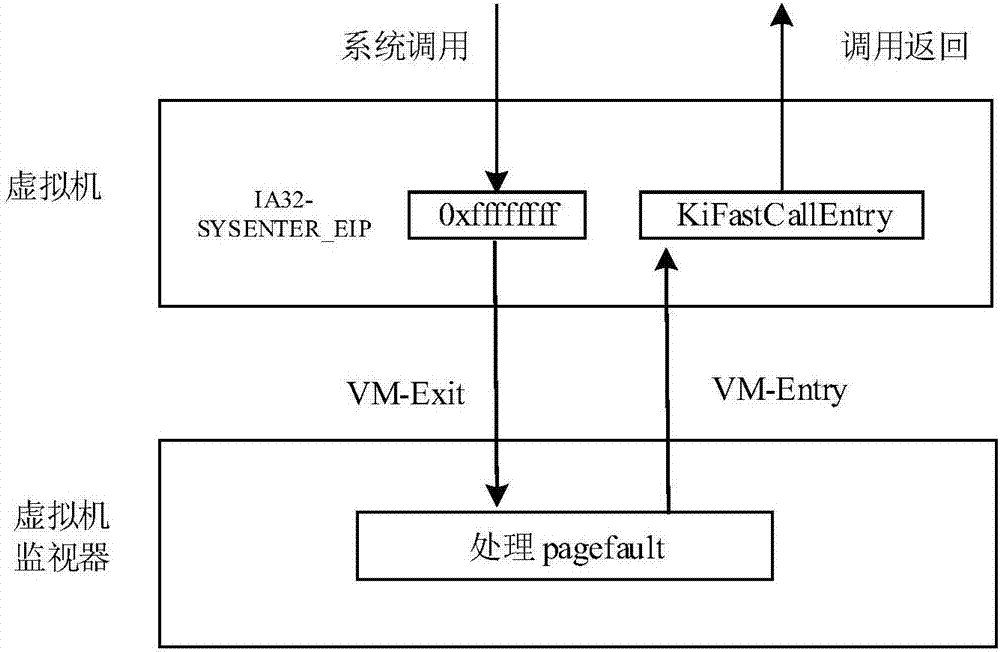
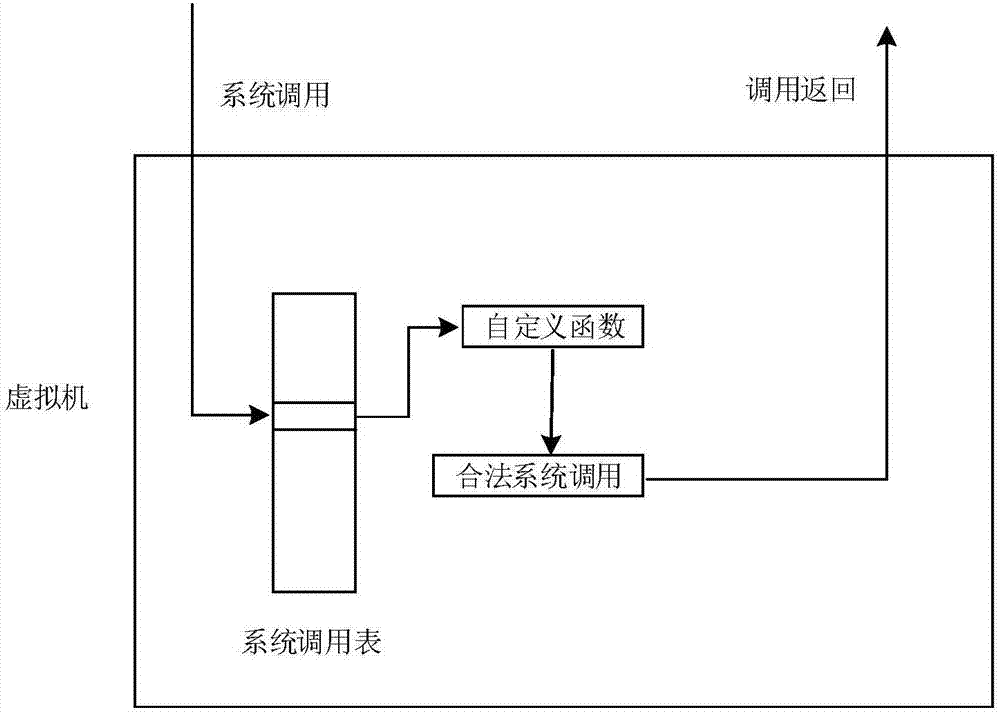
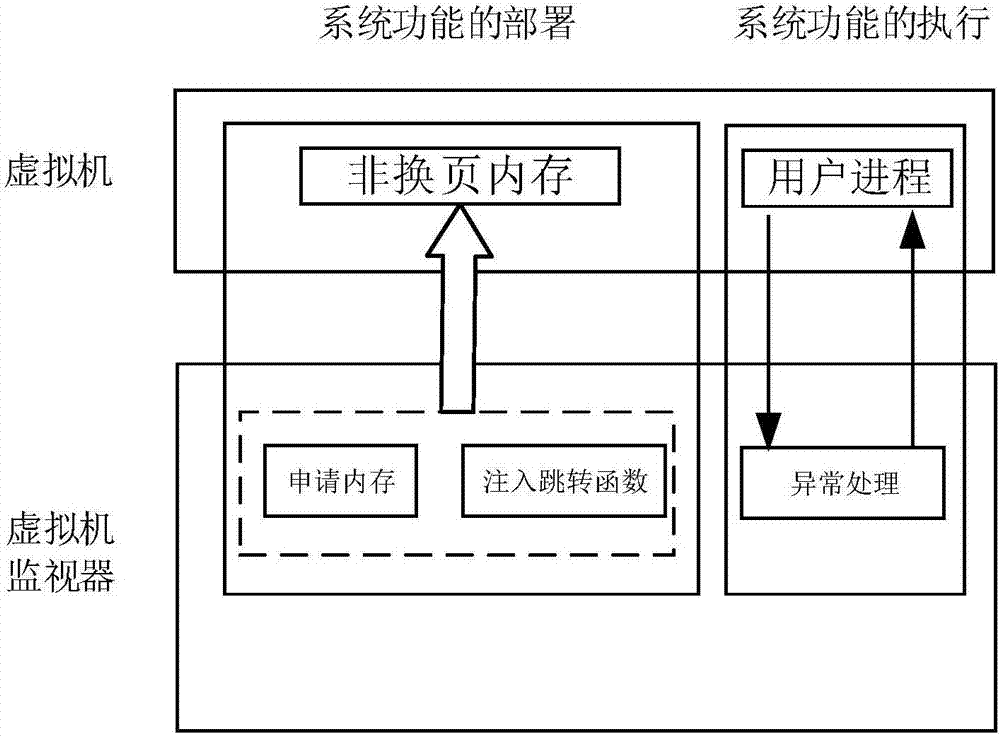
ActiveCN106897121AGuaranteed concealmentHigh performance advantagePlatform integrity maintainanceSoftware simulation/interpretation/emulationVirtualizationStructure of Management Information
The invention discloses an agent-free client process protection method based on a virtualization technology. The method comprises the steps of transparently obtaining a windows non-paging memory page in a KVM, and recording an initial address of the memory page to a KVM structure body corresponding to a virtual machine; injecting virtual machine information; setting an IA32-SYSENTER-EIP register as a newly injected KiFastCallEntry function address, and conducting hook on a KiSystemService function; conducting clearing on original SSDT contents; setting VMCS structure relevant fields, and setting read-write sinking of the IA32-SYSENTER-EIP register and pagefault abnormal sinking of an instruction fetching type; intercepting instruction fetching pagefault abnormality of a client by a virtual machine monitor, analyzing a current operation, feeding a result back to the client, and finishing one-time accessing processing. According to the agent-free client process protection method based on the virtualization technology, the safe execution of system functions is ensured, there is no need to install an agent drive inside the client, there is no need to consider the security of the agent drive, and the influence on the performance of the virtual machine is reduced to the minimum.
Owner:SICHUAN UNIV
Digital alarm receiving system
InactiveCN101771979ACovert alarm signalReal-time acquisitionSpecial service provision for substationTelephonic communicationThe InternetUser authentication
The invention discloses a digital alarm receiving system, which comprises a communication network, the Internet connected with the communication network, an alarm receiving server connected with the Internet, an alarm receiving terminal connected with the alarm receiving server and a communication terminal performing alarming communication with the alarm receiving server through the communication network, wherein the alarm receiving server verifies user identity by resolving an alarming data packet from the communication terminal and forwards the alarming data packet passing the user identity verification to the alarm receiving terminal.
Owner:卢中江
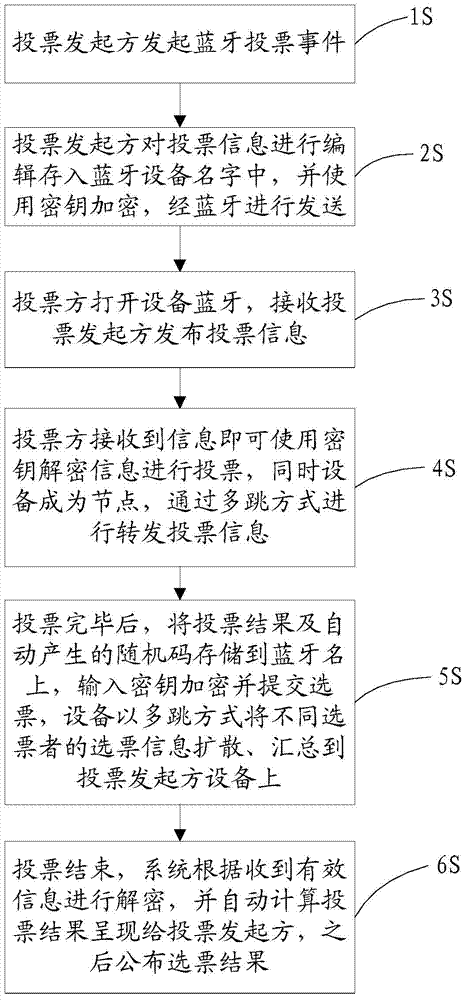
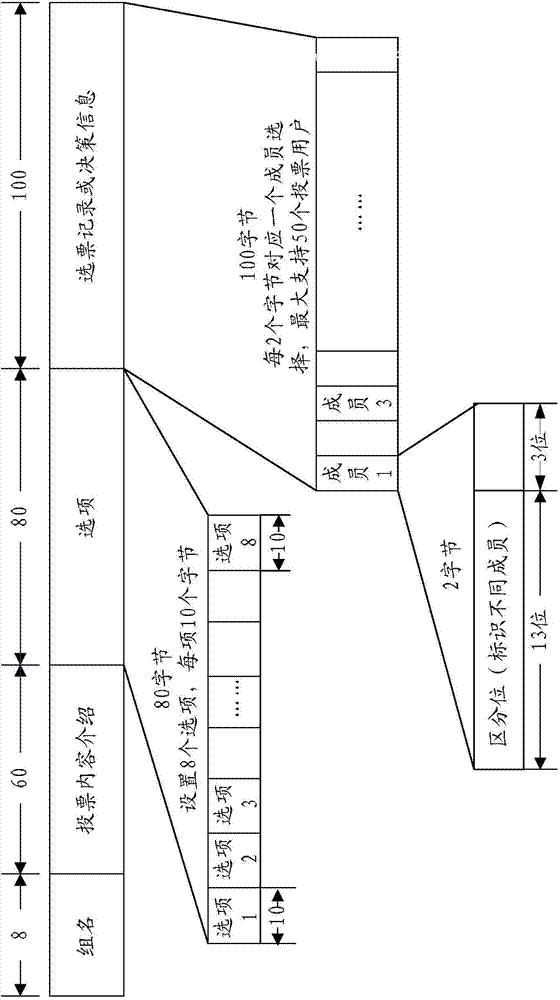
Anonymous group voting method based on bluetooth
The invention provides an anonymous group voting method based on Bluetooth. The method includes: initiating a bluetooth voting event by a voting initiator; editing voting information and storing the information into a bluetooth device name by the voting initiator, performing secret key encryption, and carrying out bluetooth transmission; letting a voting party open the bluetooth device to receive the voting information issued by the voting initiator; making the voting party use a secret key to decode the information so as to vote after receiving the information, at the same time forwarding the voting information by multihop with the device as a node; at the end of voting, storing the voting result and an automatically generated random code into the mobile phone bluetooth device name, inputting the secret key, performing encryption and submitting the vote, diffusing the vote information of different voters and gathering the information on voting initiator equipment through multihop; when voting is finished, conducting decryption by the system according to the received effective information, automatic calculating the voting result and presenting the result to the voting initiator, and announcing the vote result. With the method, the cost is reduced, and the flexibility, efficiency, security and reliability are enhanced.
Owner:HUAQIAO UNIVERSITY
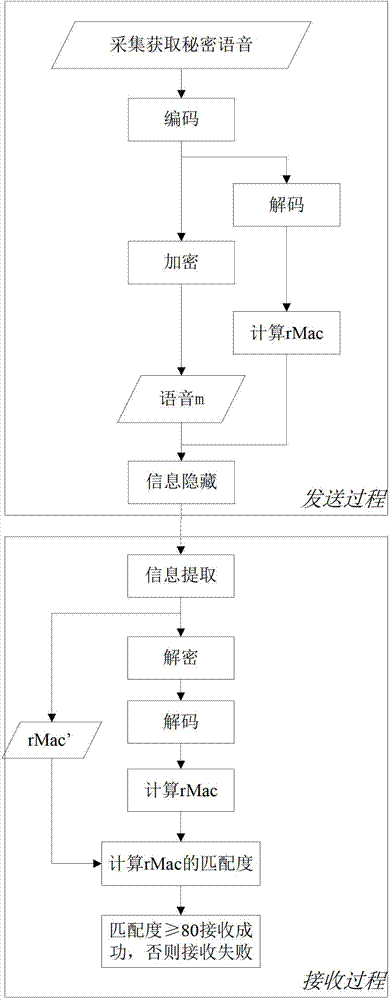
Safety communication method for voice information
InactiveCN102737639AGuaranteed concealmentGuaranteed confidentialitySpeech analysisSecuring communicationComputer hardwareSecure communication
The invention discloses a safety communication method for voice information. The hiddenness of communication is guaranteed through a discrete cosine transform domain embedding algorithm based on coefficient quantization. A secret voice is encrypted through a selective chaotic encryption algorithm, and only few key bits in audio frequency are encrypted in the encryption process, so that the encryption efficiency is greatly improved, and the confidentiality of the content in the secret voice is guaranteed. The completeness of the content in the secret voice is judged by calculating and comparing a robust message authentication code of the secret voice. While the hiddenness of voice communication is guaranteed, the confidentiality and the completeness of the voice communication content are ensured, and the safe voice communication is realized.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Method for hiding contact person information on intelligent device
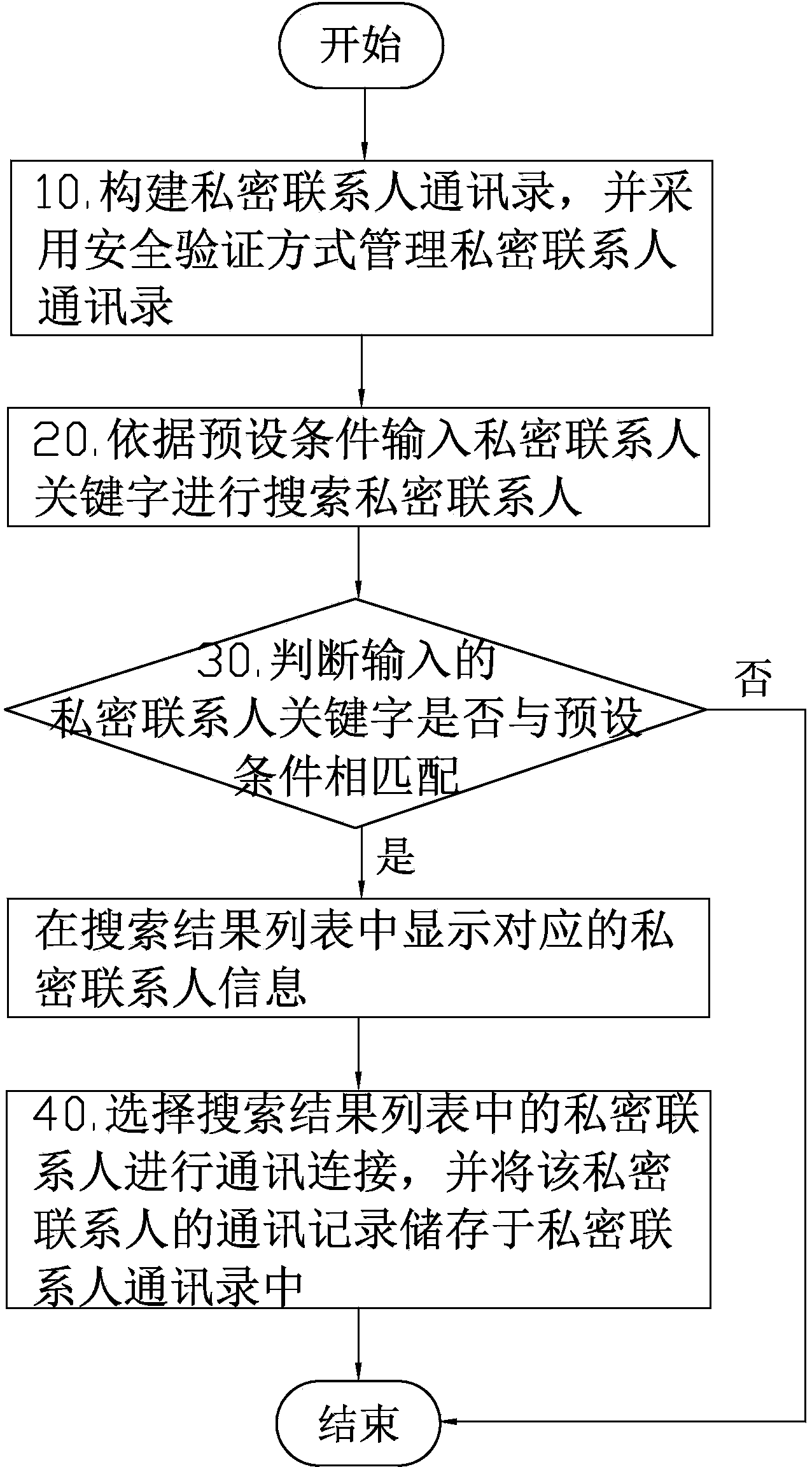
InactiveCN104284024AGuaranteed concealment and securityGuaranteed concealmentSubstation equipmentResult listSmart device
The invention discloses a method for hiding contact person information on an intelligent device. The method comprises the steps that a private contact person list is built and is managed by the adoption of a safety verification mode; when the contact person list is used, a private contact person keyword is input according to a preset condition so as to search for a private contact person, when a system judges that the input private contact person keyword is matched with the preset condition, the corresponding private contact person information is displayed in a search result list, communication logs of the private contact person are stored into the private contact person list through communication connection, and therefore the privacy and safety of the private contact person are ensured. A user can conveniently check the private contact person in the contact person list and a dialing interface and does not need to worry that the private contact person information is utilized by criminals.
Owner:XIAMEN MEITU MOBILE TECH CO LTD
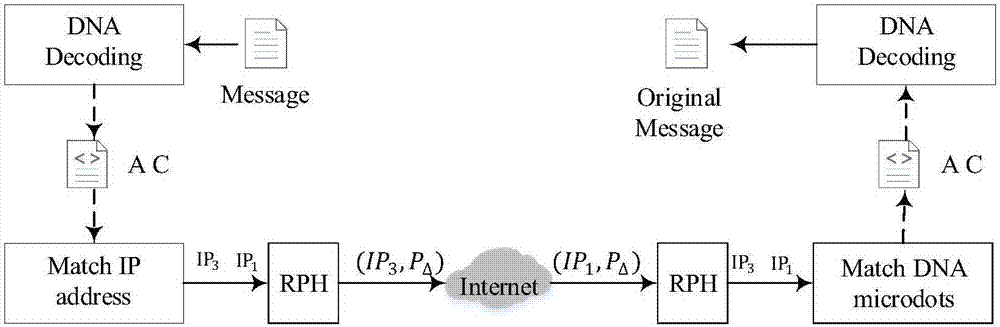
Covert hopping communication method based on DNA encryption
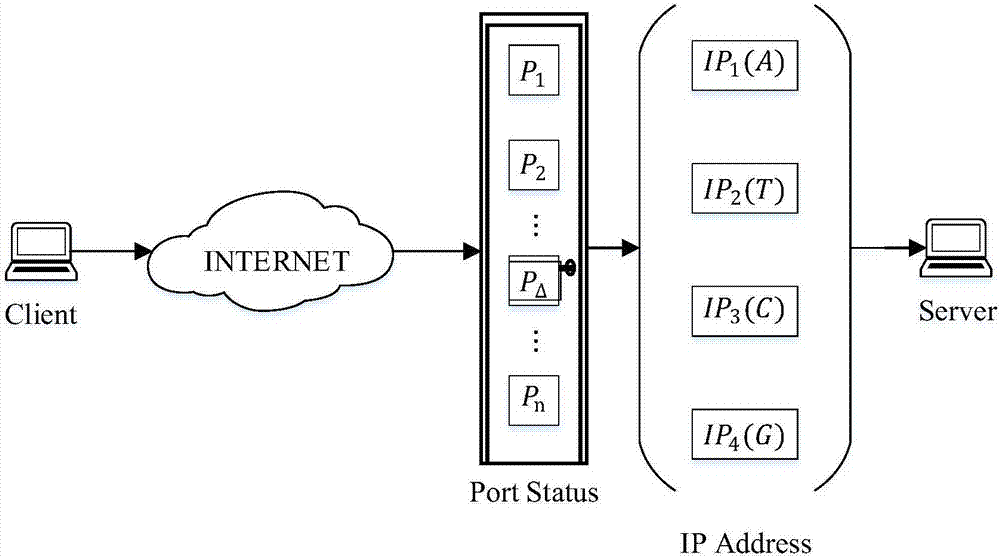
The invention provides a covert hopping communication method based on DNA encryption. The method comprises the following steps: a message server and a client are deployed; the client encrypts text contents into a letter A-P text sequence; the client carries out the DNA encryption on the text sequence with letter A-P ciphertext; the server configures four IP addresses which are respectively corresponding to four basic groups of DNA, and the client sequentially accesses the corresponding IPs on the server according to the encrypted DNA sequence for DNA encrypted sequence sending; when accessing the IPs on the server, the client calculates service port numbers based on time stamps, and makes access requests according to the target IPs and ports; the server obtains a letter A-P plaintext encrypted sequence through conversion according to rules; and the server recovers the original contents from the encrypted sequence. The method provided by the invention has the advantage that DOS attacks and eavesdropping attacks during communication can be effectively resisted.
Owner:CHINA UNIV OF PETROLEUM (EAST CHINA)
Movable type safety inspection device based on X-ray
ActiveCN103257365ASocial securityImprove security screening resultsMaterial analysis by transmitting radiationNuclear radiation detectionReciprocating motionMovable type
The invention provides a movable type safety inspection device based on X-ray. The movable type safety inspection device based on the X-ray comprises a ray launcher and a ray receiving device. The ray launcher and the ray receiving device are fixedly arranged at two ends of a source detecting frame respectively. A sliding block is fixedly arranged at the bottom end of the source detecting frame. The sliding block is matched with a guide rail which is fixedly arranged at the upper end of a base to slide. The source detecting frame is driven by a transmission mechanism and conducts reciprocating motion along the guide rail through the sliding block. The transmission mechanism is fixedly arranged on the base. The source detecting frame which is provided with the ray launcher and the ray receiving device conducts wholly and transversely reciprocating motion in hidden space which is formed by an inner frame and an outer frame to achieve the detection to people and objects. The safety inspection device is driven through the transmission mechanism, reciprocating type moving scanning imaging detection is achieved, the result of the detection is improved, and the device is high in invisibility and strong in operability.
Owner:ANHUI QILOOTECH PHOTOELECTRIC TECH
Hybrid light supplement control method and system for face snapshot camera, medium and terminal
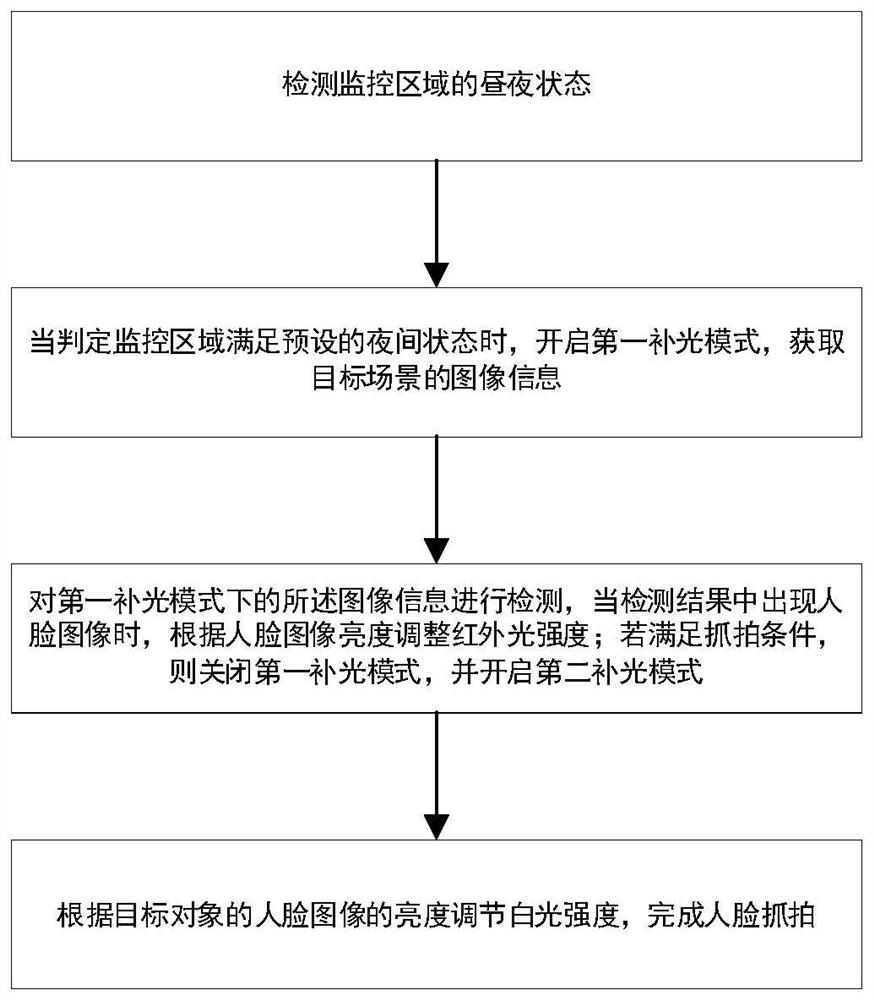
ActiveCN112040108AGuaranteed concealmentMeet the needs of supplementary lightTelevision system detailsColor television detailsWhite lightImaging quality
The invention provides a self-adaptive hybrid light supplement control method and system for a face snapshot camera, a medium and a terminal. The method comprises the steps that the day and night state of a monitoring area is detected; when the monitoring area meets the preset night state, a first light supplementing mode is started, image information of the target scene is obtained, and the firstlight supplementing mode comprises infrared light supplementing; the image information in the first light supplementing mode is detected, and when a face image appears in a detection result, the infrared light intensity is adjusted according to the brightness of the face image; if the snapshot condition is met, the first light supplementing mode is closed, a second light supplementing mode is started, and the second light supplementing mode comprises white light supplementing; the white light intensity is adjusted according to the brightness of the face image of the target object to completeface snapshot. According to the invention, a mode of combining infrared light supplement and white light supplement is adopted, the problem that a single light supplement lamp cannot give consideration to camera concealment and snapshot image quality is solved, and the snapshot quality of face images at night is improved on the premise of ensuring the camera concealment.
Owner:重庆紫光华山智安科技有限公司
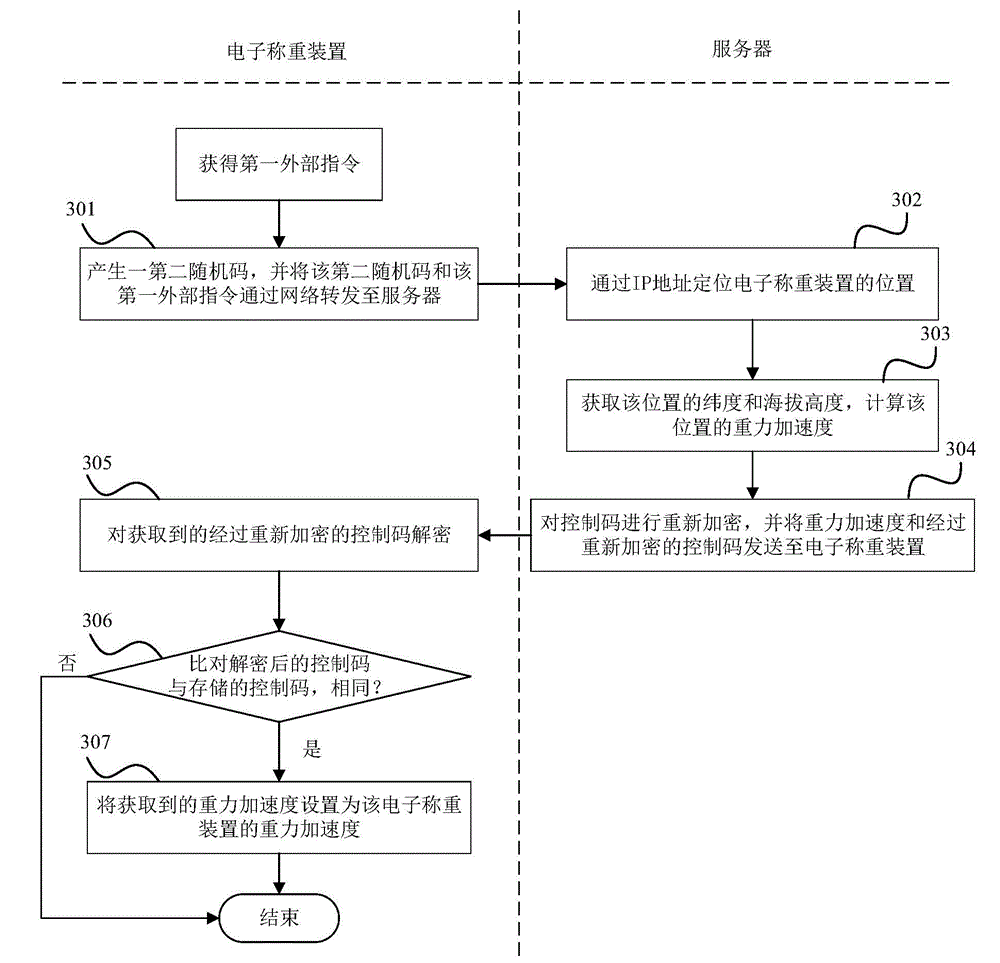
Gravitational acceleration correcting method and system
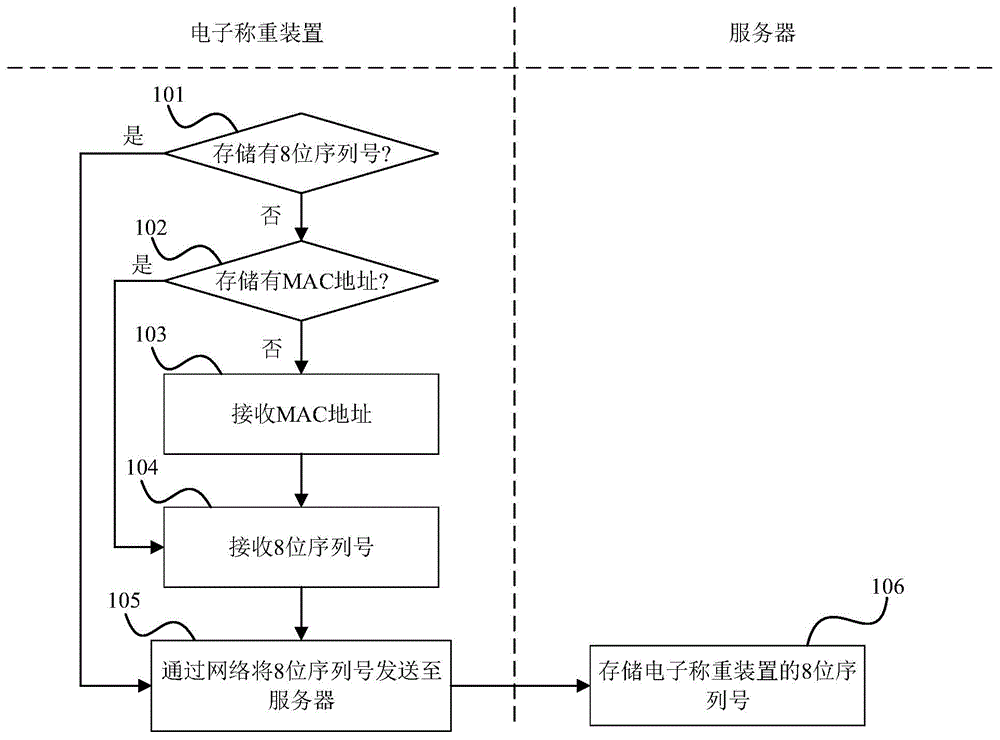
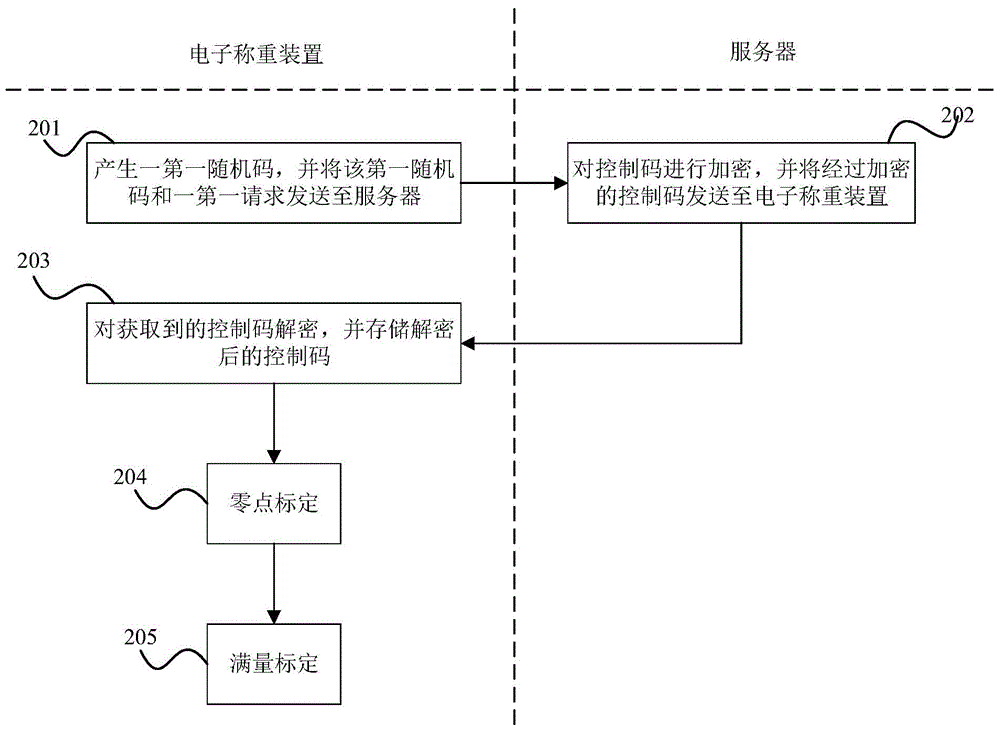
InactiveCN105222877AGuaranteed concealmentGuaranteed accuracyWeighing apparatus testing/calibrationSecuring communicationComputer hardwareData transmission
The present invention discloses a gravitational acceleration correcting method and system. The method comprises the steps that when gravitational acceleration is demarcated for the first time, a first request is sent to a server, the server sends an encrypted control code back, and an electronic weighing device decrypts and stores the control code; after obtaining a first external command, the electronic weighing device transmits the first external command to the server, the server positions and sends the gravitational acceleration and an encrypted control code back, and the electronic weighing device decrypts the control code and compares the decrypted control code with the stored control code to see if they are the same; if yes, setting the gravitational acceleration as that of the electronic weighing device, and if not, finishing. With adoption of the method, the gravitational acceleration can be automatically set according to the position where the electronic weighing device is, thereby ensuring weighing accuracy, preventing other servers from tampering the gravitational acceleration of the electronic weighing device, and effectively ensuring correcting security and data transmission concealment.
Owner:SHANGHAI SIGANG ELECTRONICS
Air-ground amphibious robot
ActiveCN104442248AOvercoming obstaclesSolve smoothnessAircraft convertible vehiclesSimulationMechanical design
The invention relates to an air-ground amphibious robot, belongs to a bionic shape air-ground amphibious robot device. A ground walking device is fixedly connected with a flight device. The air-ground amphibious robot has the benefits that the air-ground amphibious robot has high obstacle crossing capacity and through capacity, meanwhile, has flight capacity, and mainly comprises the advantages that firstly, bionic platform design is adopted, the stealthiness of the robot is convenient to guarantee when the robot carries out a task, the overall mechanical design size is small, and the appearance of the robot achieves bionic camouflage; secondly, an incomplete wheel structure with a bionic structure is adopted, and the through capacity of the structure is higher than that of wheel type and crawler type structures under the condition of light weight and the same size; thirdly, an automatic inclinator and coaxal sculls are simplified, the mechanical structure is simple and compact, the size is small, the weight is light, and the control is simple.
Owner:CHANGCHUN UNIV OF TECH +3
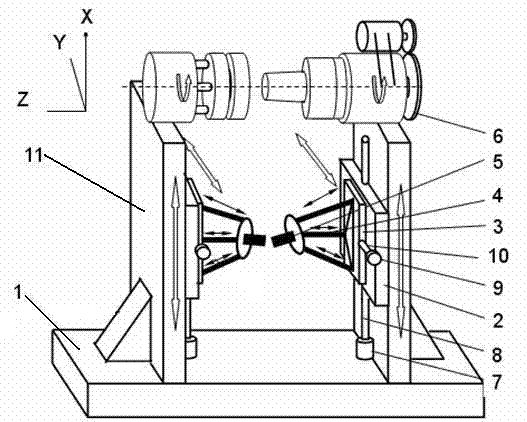
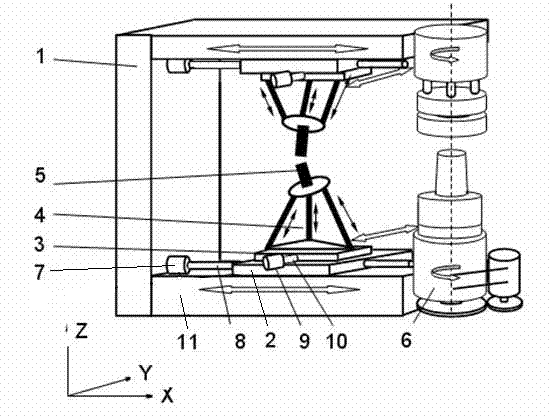
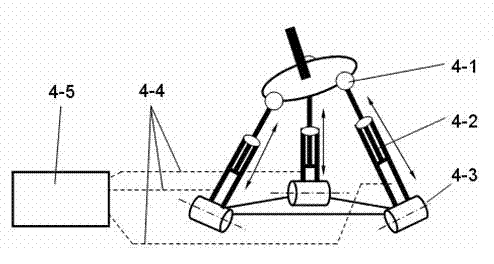
Double-blade and double-faced symmetric machining device of large propellers
InactiveCN102896375AStrong rigidityImprove stiffness performancePrecision positioning equipmentFeeding apparatusPropellerDrive motor
The invention discloses a double-blade and double-faced symmetric machining device of large propellers, and relates to propeller machining devices. The device is provided with a fixed seat; a pair of symmetric propeller machining devices are arranged on the fixed seat; each propeller machining device comprises a supporting frame, an X-direction sliding seat, an X-direction driving screw rod, and a machining power device consisting of an X-direction driving motor, a Y-direction sliding seat, a Y-direction driving screw rod and a Y-direction driving motor; a small-free-degree parallel mechanism is arranged on the Y-direction sliding seat; a machining tool is arranged at the executing end of the small-free-degree parallel mechanism; and dividing mechanisms matched with the propeller machining devices and used for clamping propellers are arranged on the two supporting frames. The device can symmetrically machine the pressure surface and a suction surface of a paddle of the propeller, double-faced symmetric machining can effectively eliminate cantilever beam effect generated during the machining process, simultaneously reduce vibration, and improve the rigidity performance of the machining device, the machining efficiency and the machining accuracy of the propeller are high, and the invisibility and the safety of military submarines are guaranteed.
Owner:HARBIN INST OF TECH AT WEIHAI
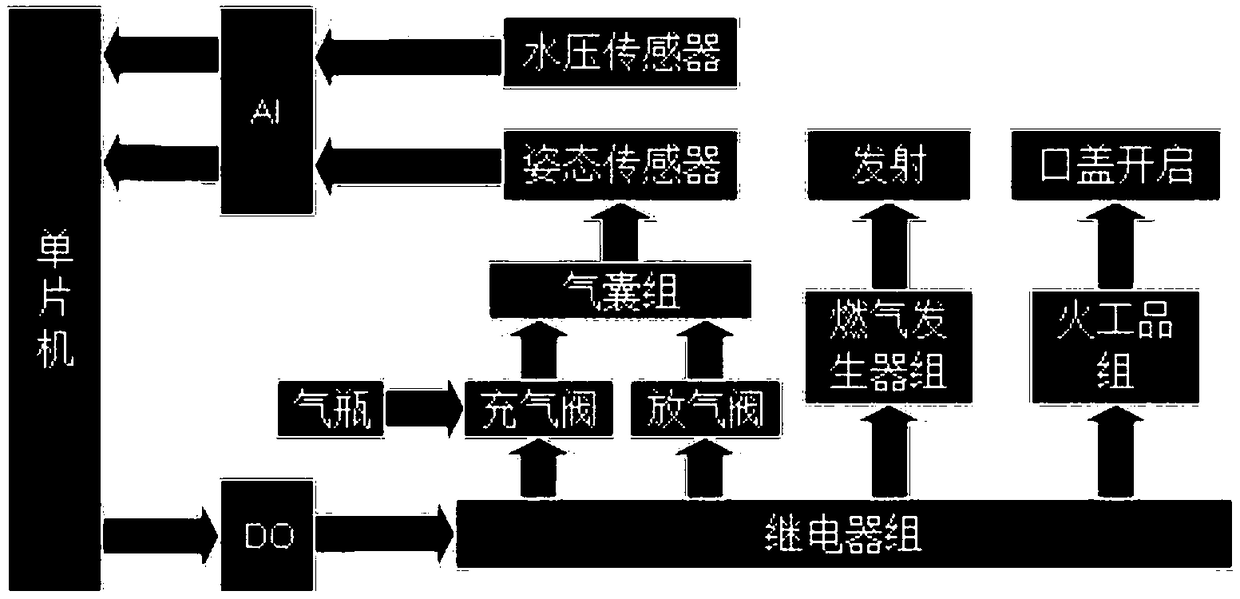
A launching vehicle of a multi-task unmanned aerial vehicle for a submarine and a carrying method thereof
The invention provides a launching vehicle of a multi-task unmanned aerial vehicle for a submarine, comprising a launching vehicle main body, a plurality of attitude adjusting airbags, an upfloating airbag and a suspension airbag. A plurality of unmanned aerial vehicles (UAVs) are uniformly arranged in the launch vehicle main body, a plurality of attitude adjustment airbags are uniformly arrangedalong the circumferential direction of the outer wall of the launch vehicle main body end, the upfloating airbag is arranged along the circumferential direction of the outer wall of the front end of the launch vehicle main body, and the suspension airbag is arranged along the circumferential direction of the outer wall of the front end of the launch vehicle main body; the upfloating air bag and the suspension air bag are free of air initially and are inflated under certain conditions; the attitude adjustment airbags and corresponding UAVs are located in the same position inside and outside thelaunch vehicle body, and the inflation time of each attitude adjustment airbag is not the same and the airbags are deflated after a period of time after inflation.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS +2
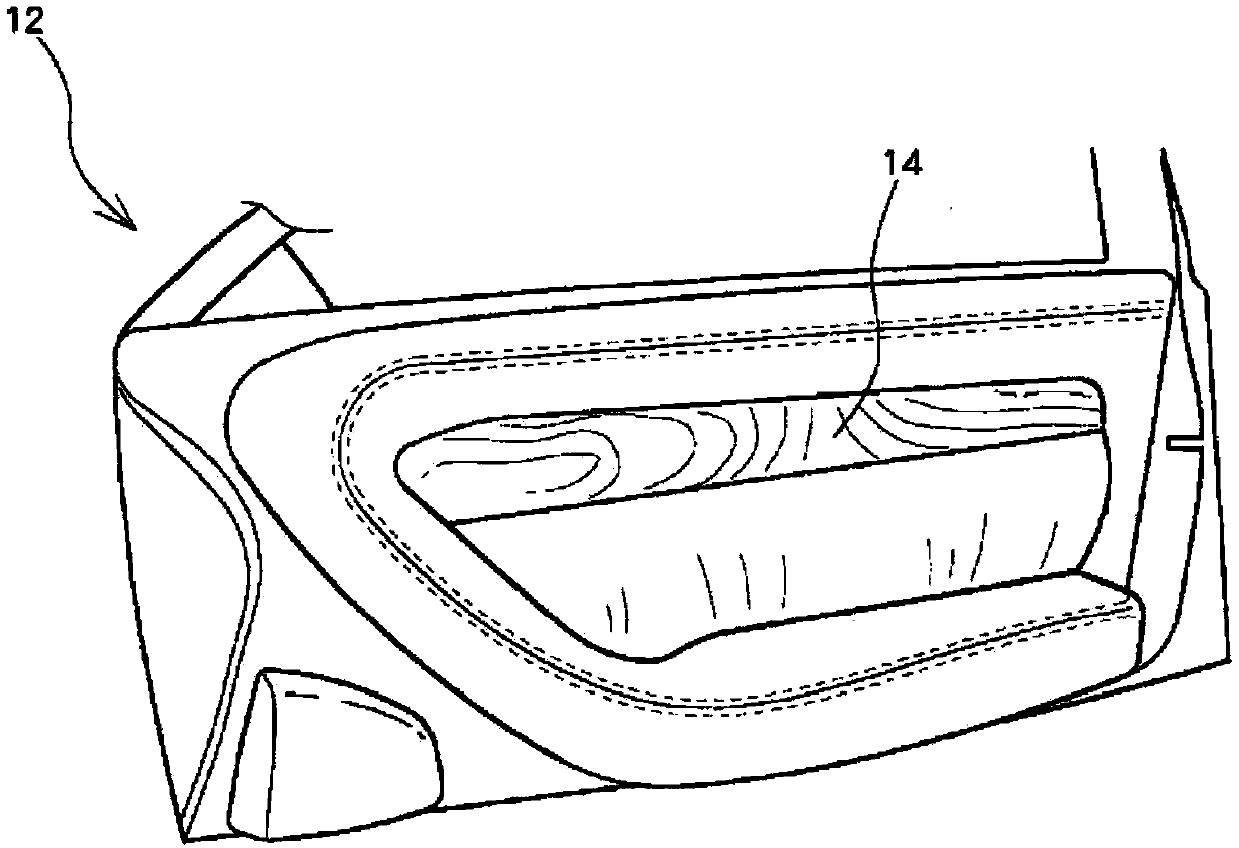
Soft door upper trim of vehicle for switch assembly and method of producing same
ActiveCN110239454ASimple processGuaranteed visibilityButtonsLegendsElectrical and Electronics engineeringCar door
The present invention relates to a soft upper trim of a laminated vehicle door of an upper substrate, foam and a permeable skin, and especially, to a soft door upper trim of a vehicle for switch assembly, in which a switch displaying a symbol such as a locking / unlocking of a door on a transparent skin while preserving the continuity of the permeable skin is easily assembled to the upper substrate, and to a mass production method thereof.
Owner:SEOYON E HWA CO LTD +1
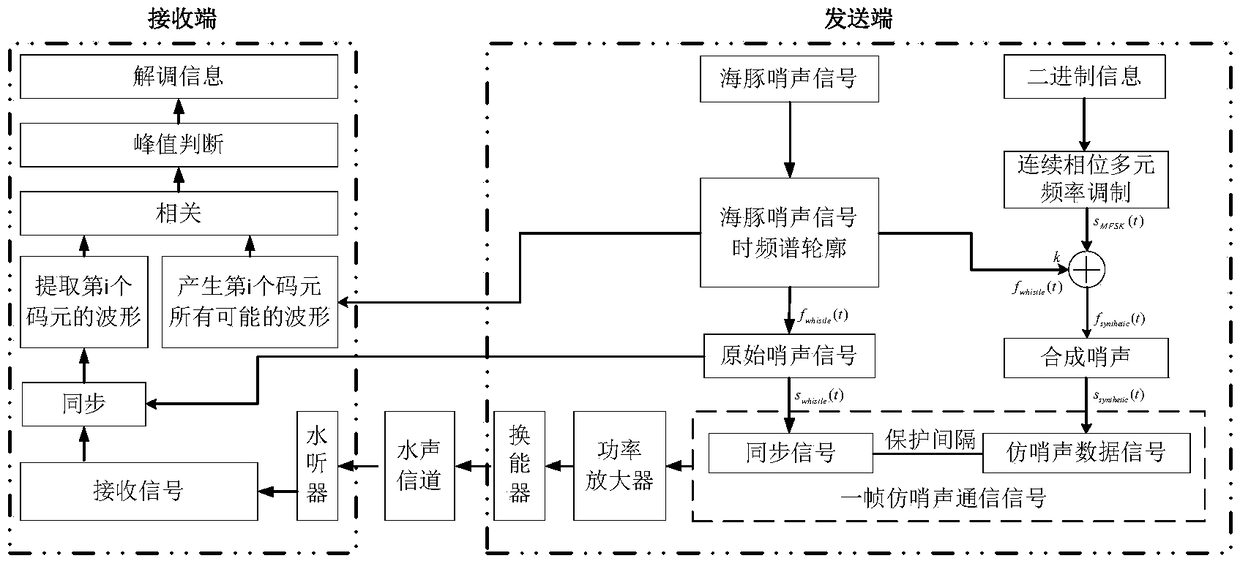
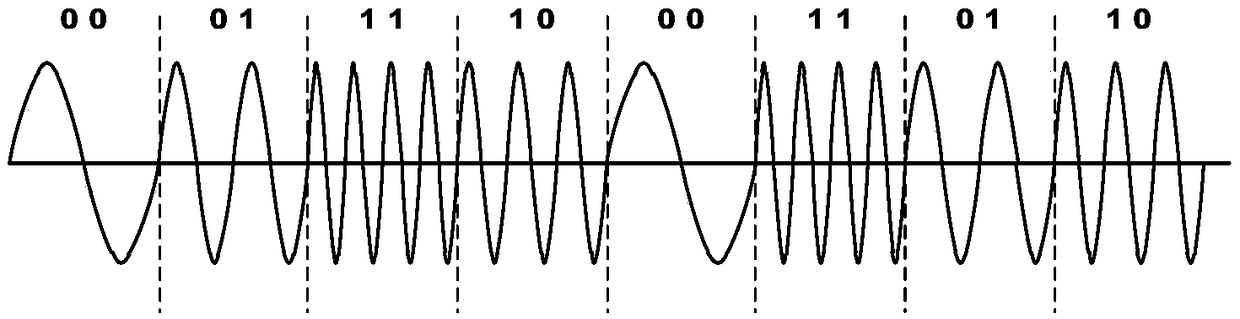
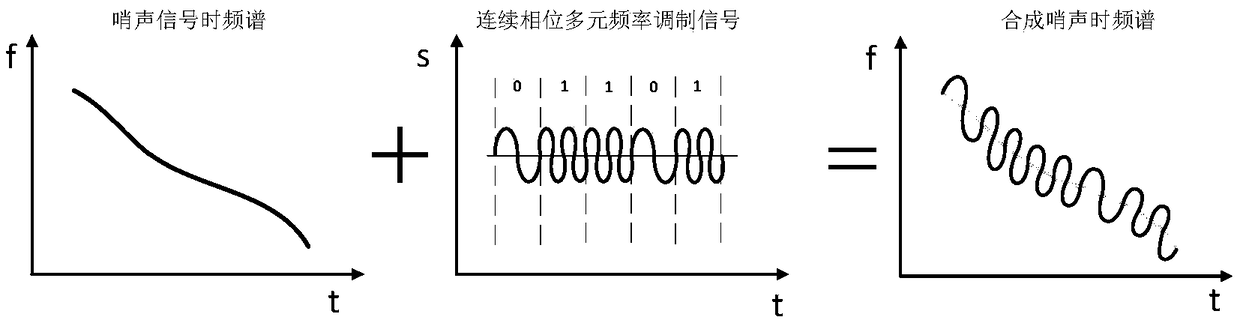
Simulated dolphin whistle continuous phase multivariate frequency modulation underwater acoustic communication method
ActiveCN109347568AGuaranteed continuityGuaranteed continuous changeSonic/ultrasonic/infrasonic transmissionFrequency spectrumCorrelation function
The invention belongs to the technical field of underwater acoustic communication, and particularly relates to a simulated dolphin whistle continuous phase multivariate frequency modulation underwateracoustic communication method. The method of the invention includes the following steps: performing continuous phase multivariate frequency modulation on information by a sending end; adding the modulated signal with a time-frequency spectrum profile of an extracted dolphin whistle signal in a certain proportion to generate a synthesized whistle, and further obtaining a simulated whistle data signal; adding an original whistle signal before the simulated whistle data signal to serve as a synchronization signal, and forming a frame of transmission signal; after a receiving end performs synchronization, extracting each symbol waveform; and calculating correlation functions between each symbol waveform and all possible signal waveforms of the symbol, and judging a maximum correlation peak toimplement demodulation. According to the simulated dolphin whistle continuous phase multivariate frequency modulation underwater acoustic communication method, provided by the invention, each symbolcan modulate a plurality of pieces of bit information, the communication rate is high, the similarity between the synthesized whistle signal and a real whistle signal is high, and the underwater acoustic communication method has strong concealment and can meet the requirements of underwater covert acoustic communication.
Owner:HARBIN ENG UNIV
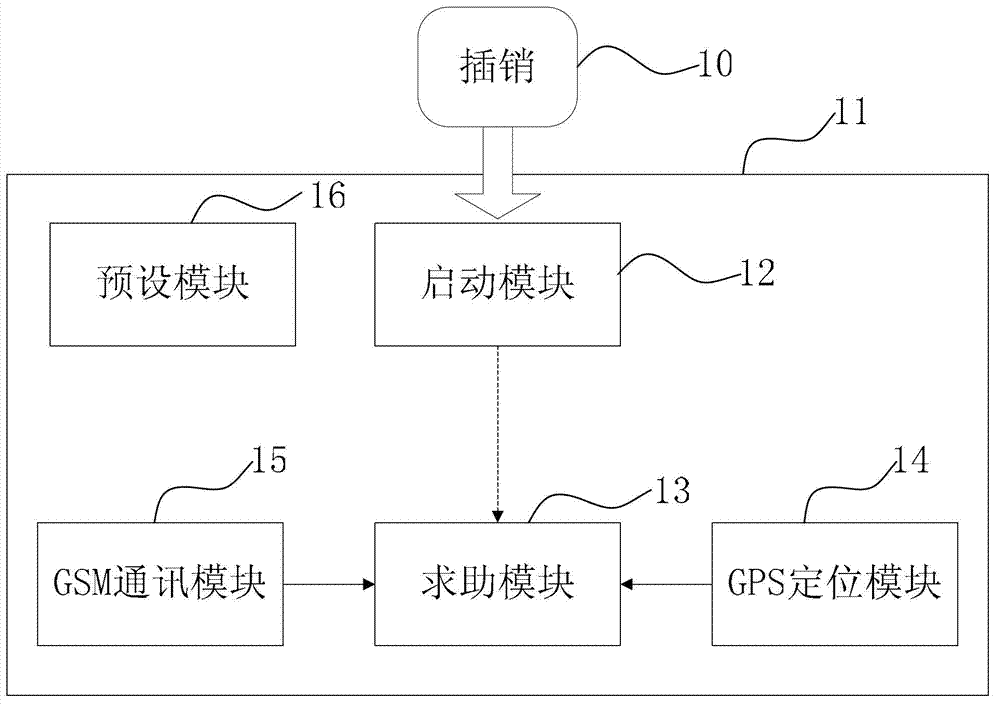
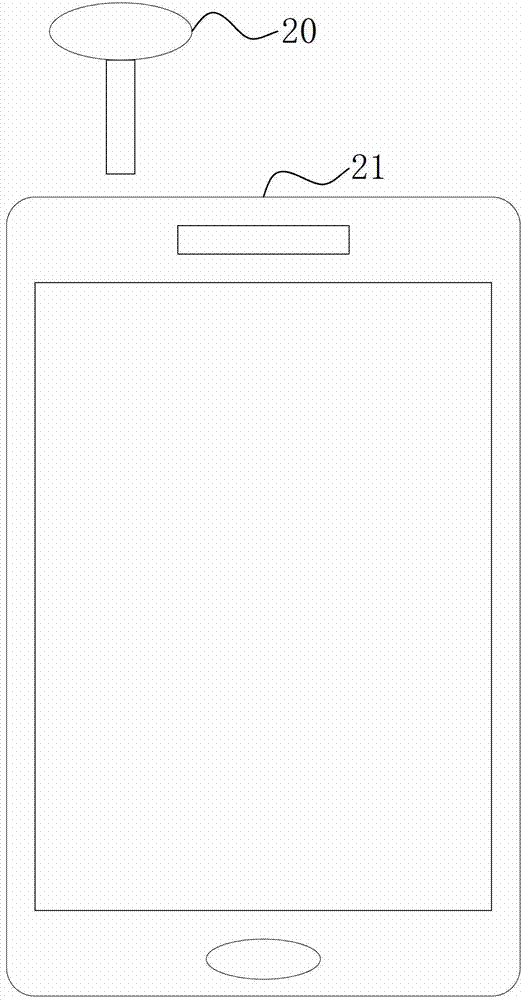
Emergency calling method and system for mobile device
InactiveCN103209264AAsk for help promptly and covertlyImprove effectivenessSubstation equipmentComputer terminalMobile device
The invention provides an emergency calling method for a mobile terminal. The method is used for the mobile terminal with a communication function, and the mobile terminal comprises a bolt with an emergency trigger function and a jack with an emergency detection function. The emergency calling method comprises the following steps of: when the bolt is inserted into the jack, starting an emergency calling system of the mobile terminal; and when the bolt is pulled out of the jack, performing automatic calling by the emergency calling system of the mobile terminal, wherein the automatic calling comprises the following steps of: automatically starting the communication function of the mobile terminal, automatically dialing a calling telephone, turning on a microphone unit of the mobile terminal when the calling telephone is answered, and turning off a receiver unit of the mobile terminal. By adopting the method, a user can ask for help in a timely and concealed mode through the mobile terminal.
Owner:QISDA SUZHOU +1
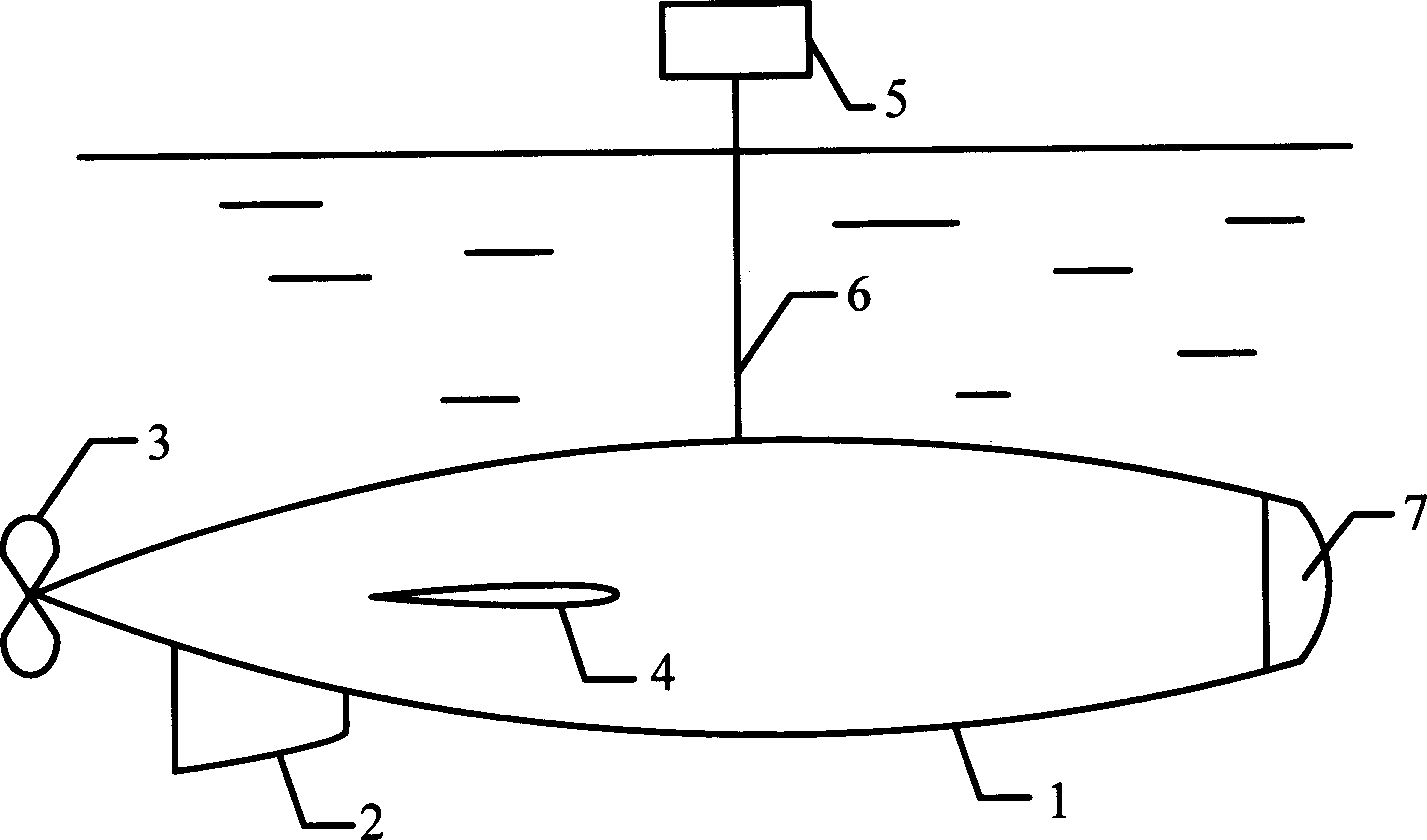
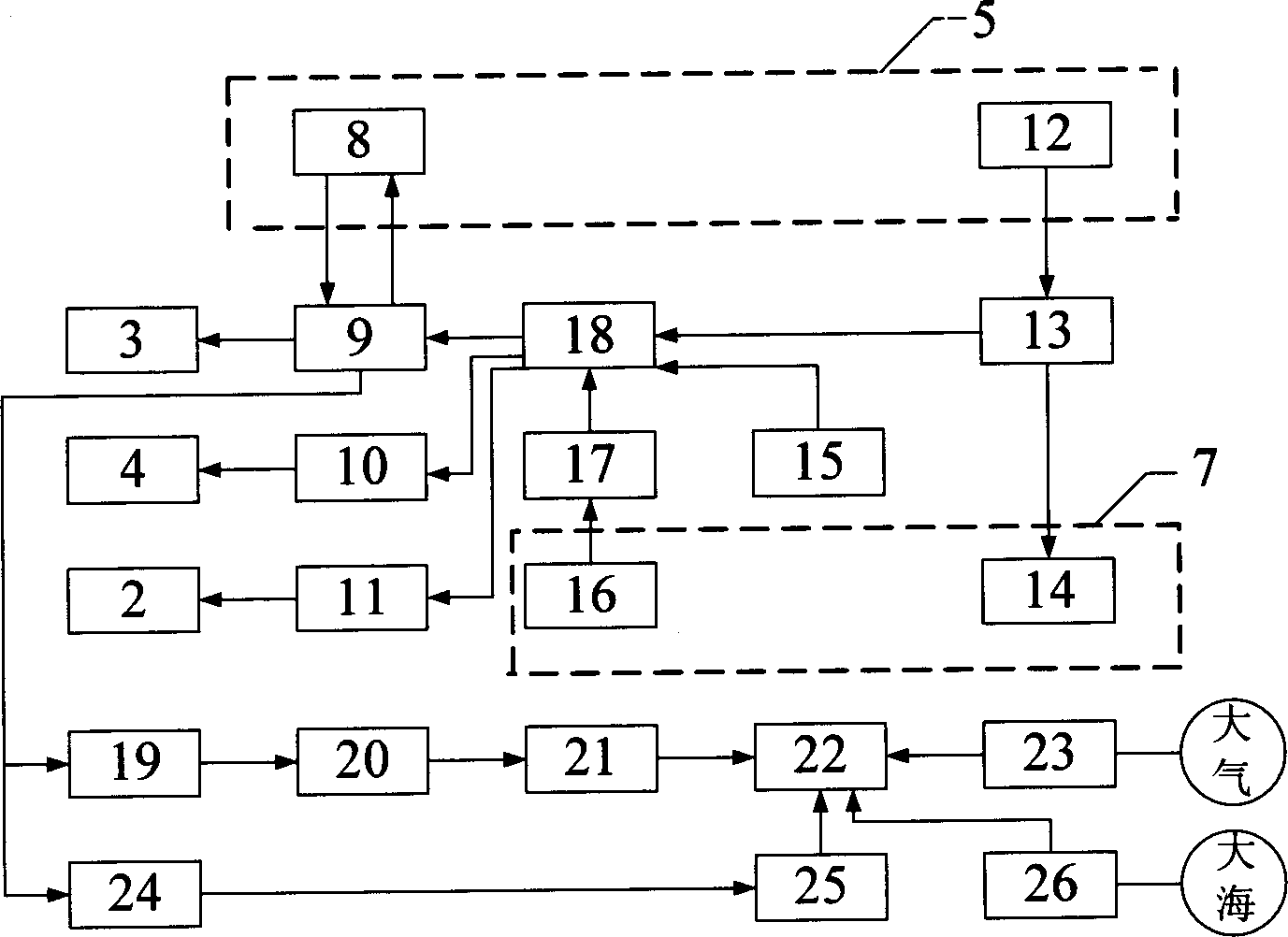
Optronic two-channel auto-observation following semi-submerged device
InactiveCN1775623AImprove concealmentGuaranteed concealmentUnderwater vesselsUnderwater equipmentEngineeringActuator
The invention relates to a photoelectric double-channel automatic watching following semi- diving device, belonging to ship engineering technical field, comprising a casing, vertical and horizontal tail fins, reversible screw propeller, top frame, connection pipe, vent-pipe, power system, vertical and horizontal tail fin executer, photoelectric periscopic window, signal processing encryption and decryption machine, transmitting and receiving energy exchange base array, hydraulic sensor, control system, air compressing bottle, rapid blow valve, ballast tank, water injection system, and water injection valve. The semi-diving device can be completely hidden underwater and can only expose the periscopic window for detecting and encrypts the detected image signal and transmits it in form of water sound wireless signal to the underwater mother boat. The encrypted control instructions emitted by the underwater mother boat are transmitted to the semi-diving device in the data transmission form of water sound digital communication and command the semi-diving device to work after decrypted. The encrypted water sound wireless signal is unable to be modified, broken down, intercepted or utilized by the enemy and can be widely applied to military and civil occasions and the others.
Owner:SHANGHAI JIAO TONG UNIV
Laminating film for liquid crystal display and backlight module of liquid crystal display
PendingCN110928053AImprove stiffnessSolve the problem of coiling exceptionNon-linear opticsLiquid-crystal displayDisplay device
The invention discloses a laminating film for a liquid crystal display. The laminating film comprises an atomization layer film, a base film, a first prism layer film, a second prism layer film and athird prism layer film from top to bottom, and the atomization layer film, the base film, the first prism layer film, the second prism layer film and the third prism layer film are sequentially attached to one another through attaching glue. Moreover, the invention further discloses a backlight module of the liquid crystal display, and the backlight module comprises the laminating film for the liquid crystal display. According to the laminating film for the liquid crystal display, the brightness reaches the effect of two brightness enhancement films and two diffusion films, and the shielding property can also meet the requirements of the liquid crystal display module; and the laminating film can be in direct contact with glass of the liquid crystal display panel, it is guaranteed that interference and glare are avoided, the visual effect reaches the standard, the scratch resistance meets the assembly requirement, and the stiffness of a final product can meet the requirement of a large-size module.
Owner:CCS (SHANGHAI) FUNCTIONAL FILMS IND CO LTD
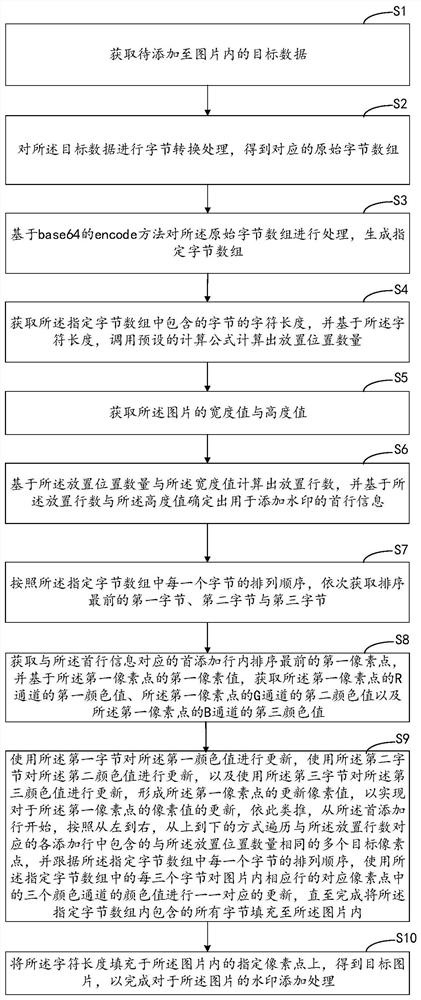
Watermark adding method and device, computer equipment and storage medium
The invention relates to the field of data processing, and provides a watermark adding method and device, computer equipment and a storage medium. The method comprises the following steps of acquiring target data to be added into a picture, performing byte conversion on the target data to obtain an original byte array; processing the original byte array based on an encode method of base64 to generate a specified byte array; according to a preset updating rule, sequentially using every three bytes in the specified byte array to perform one-to-one correspondence updating processing on the color values of the three color channels in the corresponding pixel points of the corresponding row in the picture; and filling the specified pixel points in the picture with the character length to obtain a target picture so as to complete watermark adding processing of the picture. The target data is added into the picture in an implicit manner, so that the sharing safety and concealment of the target data are ensured. The invention can also be applied to the field of block chains, and the target pictures and other data can be stored on the block chains.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com