Safe and rapid anonymous network communication method and system
An anonymous network and communication system technology, applied in the field of safe and fast anonymous network communication methods and systems, can solve problems such as poor stability of communication links, weak security, and reduced availability of anonymous communication systems, so as to ensure legitimacy and improve security. sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] To further illustrate the various embodiments, the present invention is provided with accompanying drawings. These drawings are a part of the disclosure of the present invention, which are mainly used to illustrate the embodiments, and can be combined with related descriptions in the specification to explain the operating principles of the embodiments. With reference to these contents, those skilled in the art should understand other possible implementations and advantages of the present invention. Components in the figures are not drawn to scale, and similar component symbols are generally used to denote similar components.
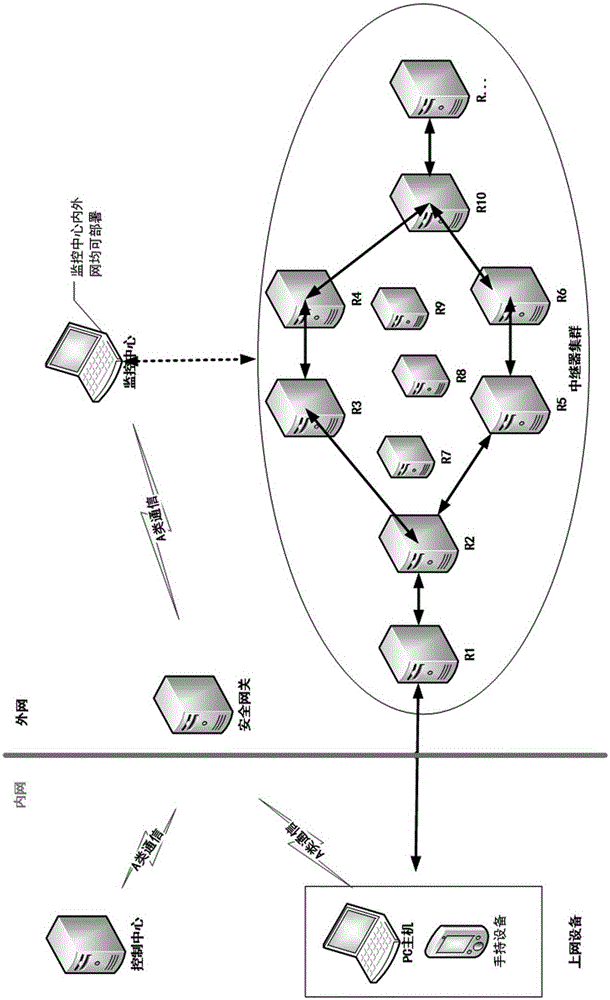
[0031] Now in conjunction with accompanying drawing and specific embodiment the present invention is further described, as figure 1 As shown, a safe and fast anonymous network communication system of the present invention includes a control center, a monitoring center, a security gateway, an Internet access device and a cluster of repeaters. The...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com