Safety communication method for voice information
A technology for secure communication and voice information, applied in the field of communication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
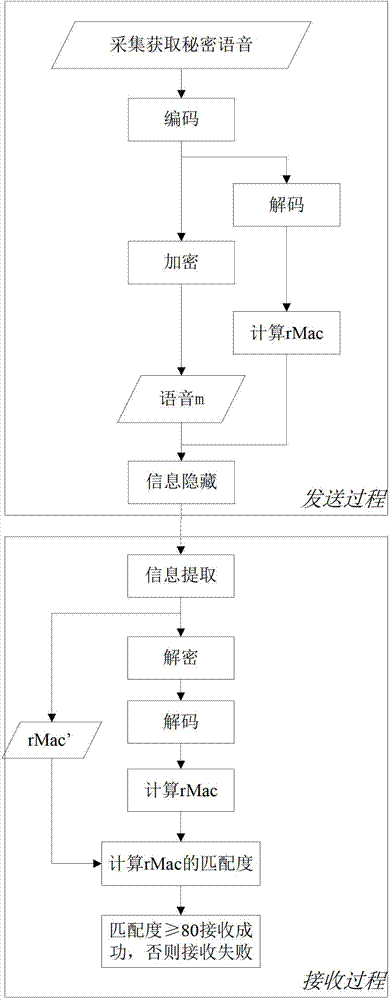
[0067] A method for safe communication of voice information, including two parts: a voice sending process and a voice receiving process, and its realization process is as follows: figure 1 shown. In the method, unless otherwise specified, "n-bit" represents n binary digits.
[0068] Step 1. The sending end obtains the voice to be sent and processes the audio file to generate the audio file of the voice to be sent embedded with the secret voice. details as follows:
[0069] Step 1.1: Collect voice
[0070] This step may be to obtain the existing voice and audio files of the system, or to record the user's voice and audio to obtain the recorded audio files. The acquired audio files are called Secret Voices. For example, we collected the 341KB WAV format audio file info.wav.
[0071] Step 1.2: Encode the secret voice info.wav for compressing the secret voice to save subsequent communication overhead. The encoding process is as follows:
[0072] Step (1): For the secret vo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com