Protection method permitted by webmaster and device therefor
A protection device and network management technology, applied in the field of communication, can solve problems such as low security, and achieve the effect of enhancing security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
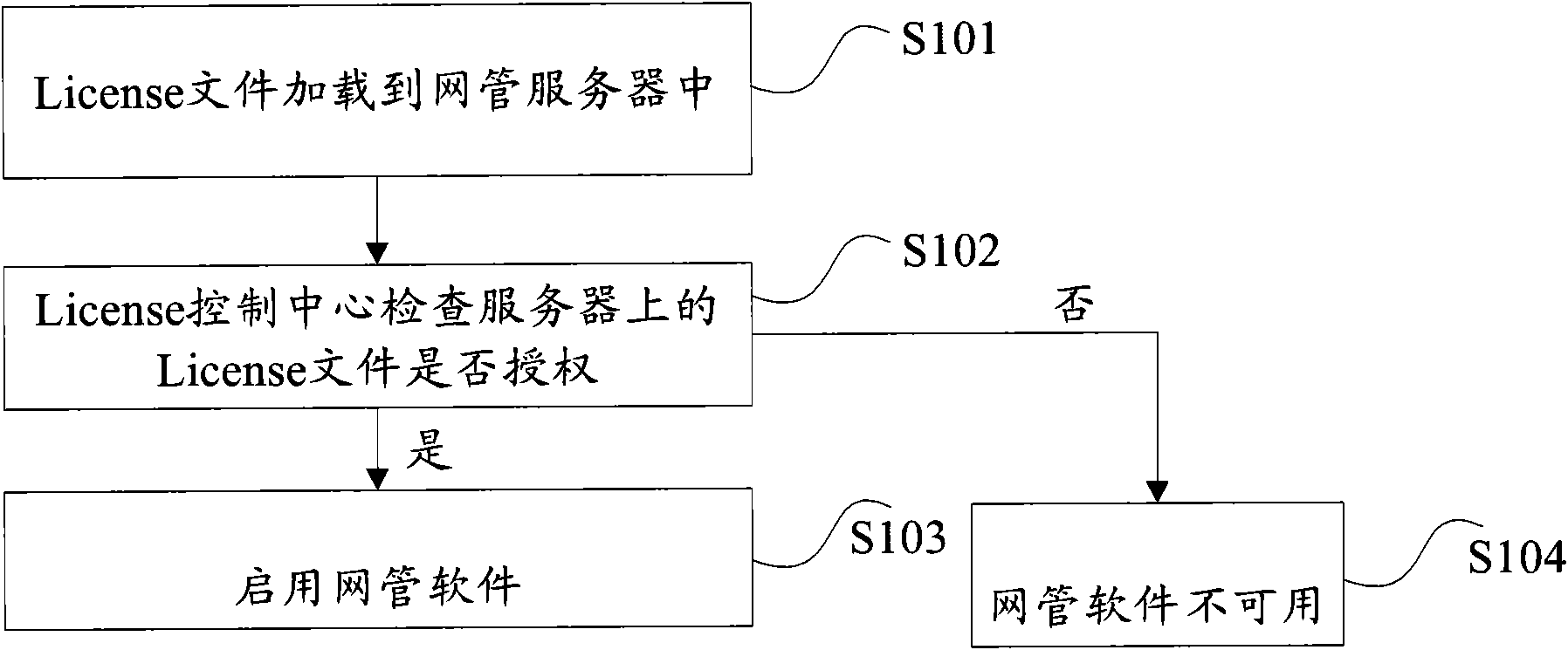
[0053] Embodiment 1: The license control center detects a security assurance scheme when the server is started for the first time.
[0054] When the server is started for the first time, the License control center detects whether the dongle is inserted into the server, if not, the server will stop starting, otherwise continue to check whether the license file is authorized, if there is, the server will start normally, otherwise the server will stop starting. Figure 4 is a flow chart of the server's initial start-up process according to an embodiment of the present invention, such as Figure 4 As shown, it specifically includes the following steps S401 to S404.
[0055] Step S401, determine whether the dongle exists, if yes, proceed to step S402, otherwise, proceed to step S404.
[0056] Step S402, judging whether the license file is authorized, if the judging result is yes, go to step S403, otherwise, go to step S404.
[0057] Step S403, judging whether the authorization co...
Embodiment 2
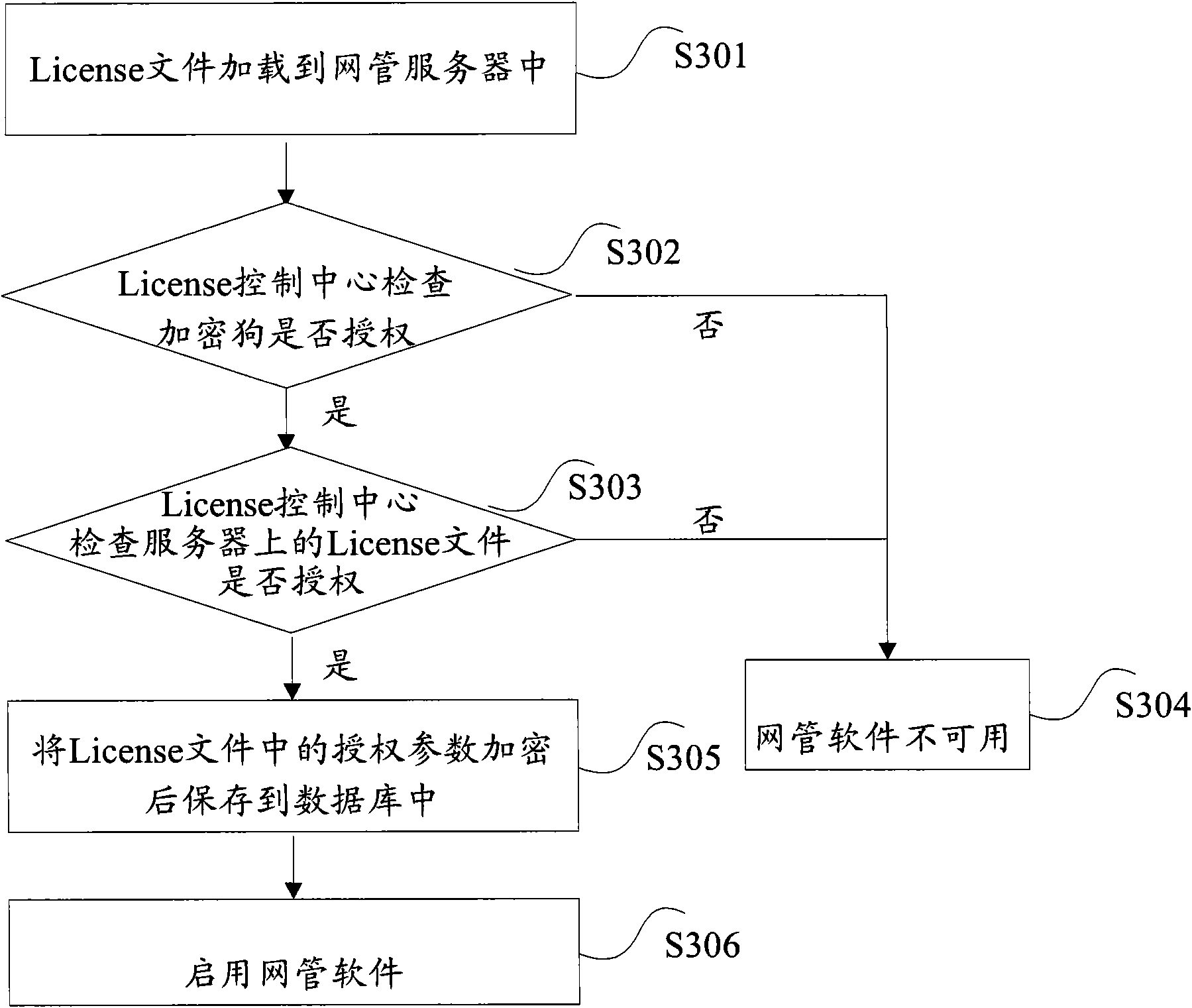
[0060] Embodiment 2: The license control center detects the security guarantee scheme when the server is not started for the first time.
[0061] When the server is not started for the first time, the License control center checks whether the dongle is inserted into the server and whether the dog is authorized. If not, it will send an alarm to the server. If yes, it will continue to check whether the license file is authorized. If it is, it will check whether the validity period of the file has expired. If yes, send an alarm to the server, otherwise end, see attached Figure 5 (Similar to the cycle detection process)
Embodiment 3
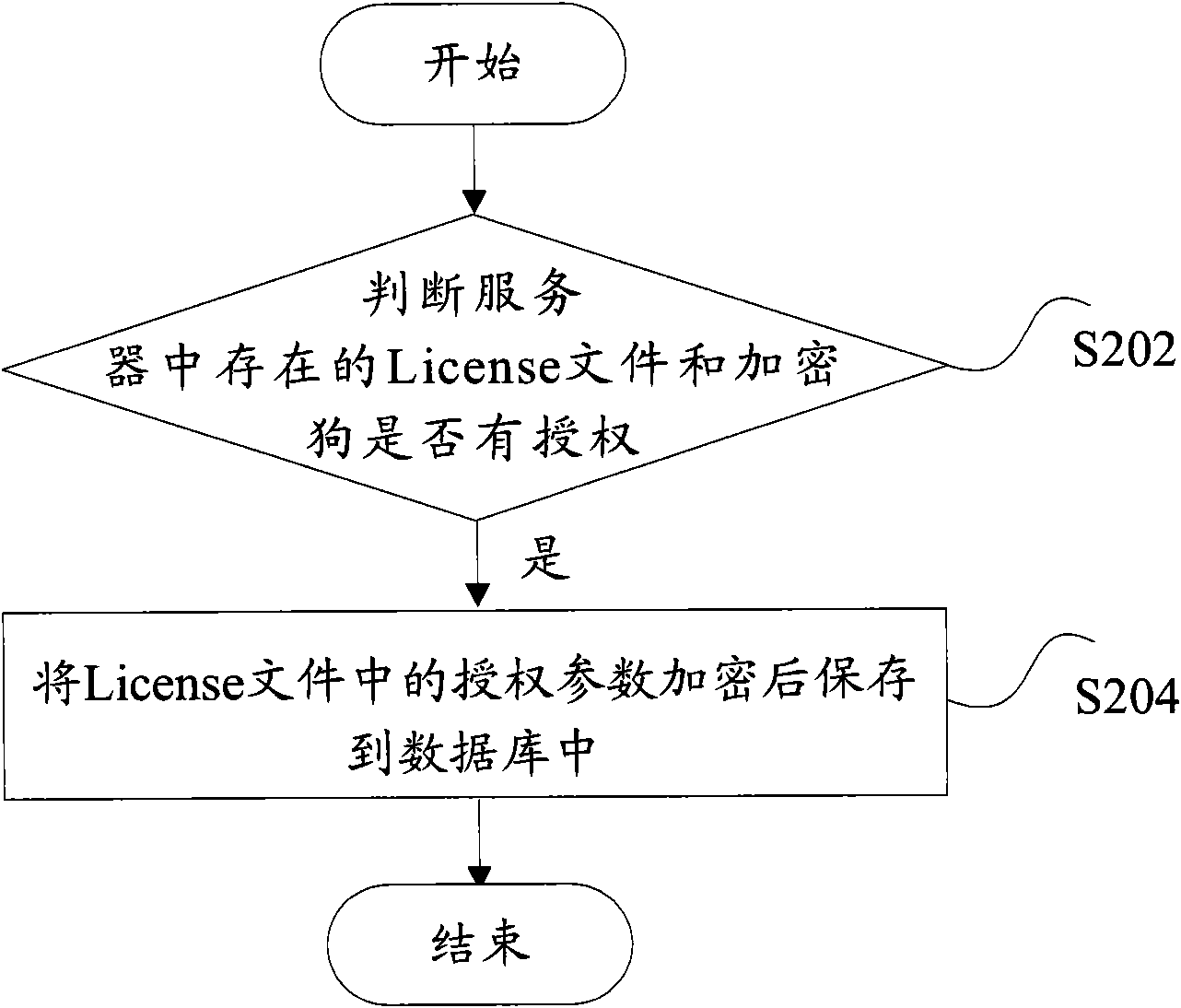
[0062] Embodiment 3: A guarantee scheme for regularly checking the security of the server for the License control center.
[0063] Figure 5 is a flowchart of server timing detection processing according to an embodiment of the present invention, such as Figure 5 As shown, it specifically includes the following steps S501 to S507.
[0064] Step S501, after the timing detection time arrives, judge whether the dongle exists, if the judgment result is yes, go to step S502, if the judgment result is no, go to step S507.
[0065] Step S502, judging whether the dongle is authorized according to the authorization parameters stored in the database, if the judging result is yes, go to step S503, if the judging result is no, go to step S507.
[0066] Step S503, judging whether the license file exists, if the judging result is yes, go to step S504, if the judging result is no, go to step S507.
[0067] Step S504, judging whether the license file is authorized according to the authori...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com