Authentication method and device
A technology of authentication and authentication information, applied in the field of communication, can solve problems such as inconvenient use for users, failure to realize automatic authentication, and unified authentication of IMS network and application server, etc., to achieve simple implementation, user use and operation The effect of convenient business management
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
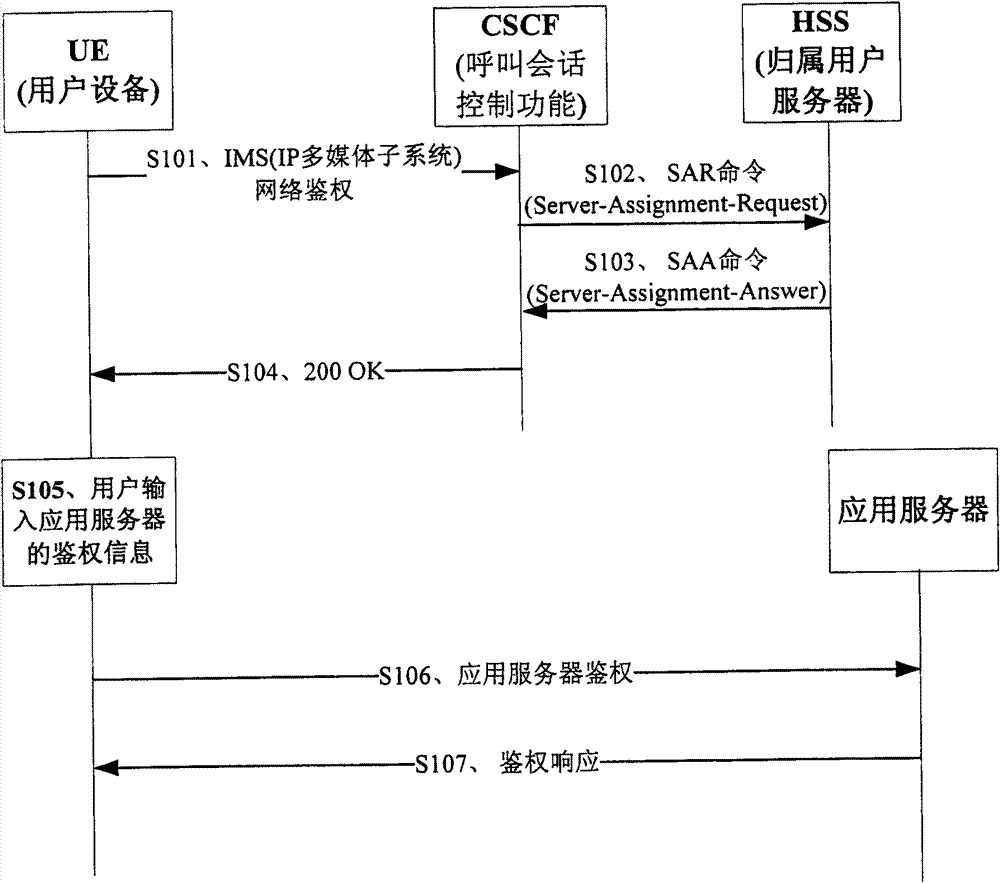
Embodiment 1
[0040] Embodiment 1 of the present invention provides a unified authentication method and system for an IP multimedia subsystem IMS network and an application server.
[0041] Embodiment 1 of the present invention utilizes the existing IMS equipment and flow, appropriately expands, and supports unified authentication of the IMS network and the application server. That is, after passing the IMS network authentication, the UE uses the authentication information acquired during the IMS network authentication process to automatically authenticate other application servers used by the authorized UE, without user intervention.
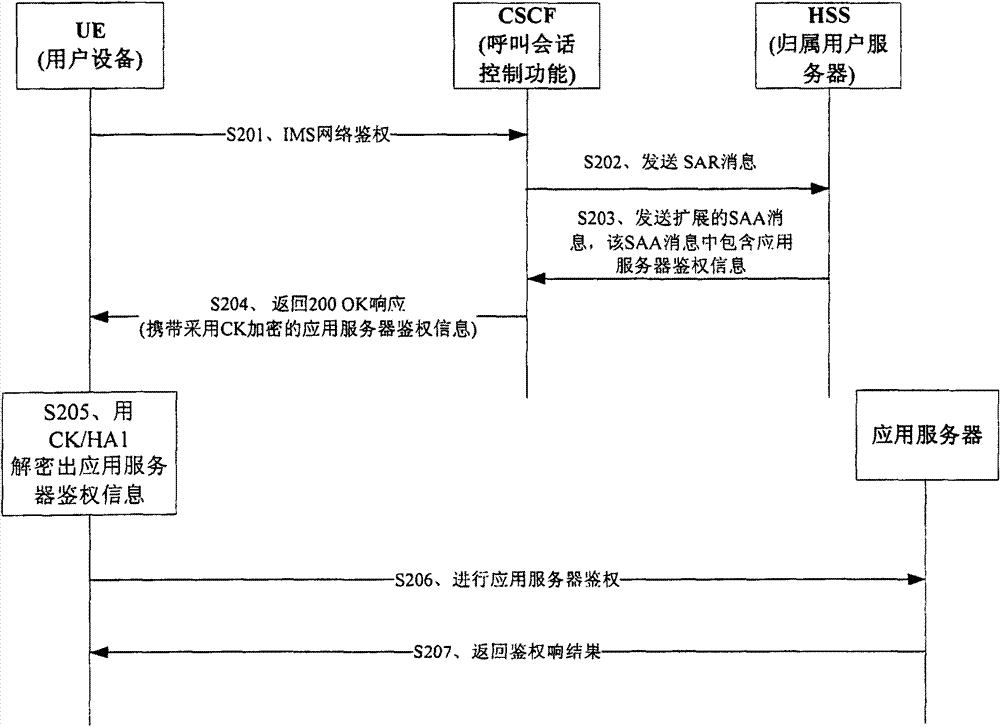
[0042] figure 2 It is a flowchart of signaling interaction of the system according to Embodiment 1 of the present invention. Such as figure 2 As shown, the signaling interaction process includes:
[0043] S201. The user equipment UE performs IP multimedia subsystem IMS network authentication, and the UE sends an IMS network authentication request to the...
Embodiment 2
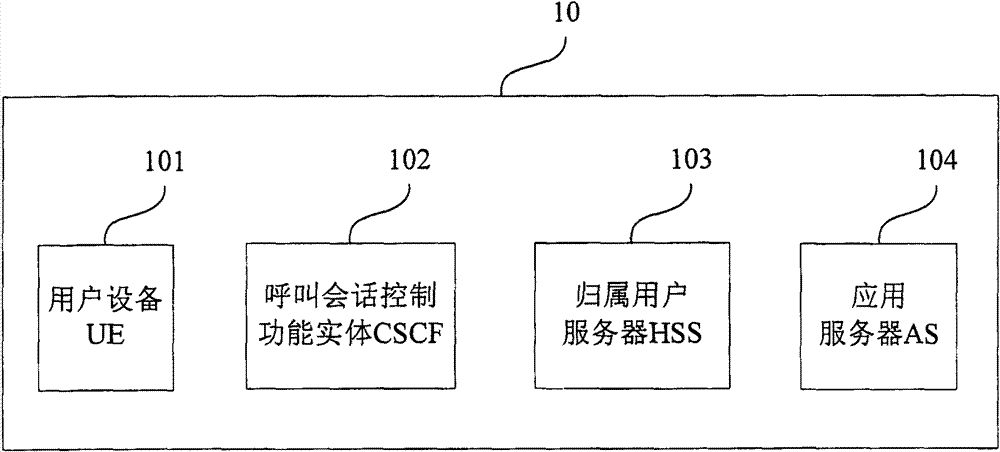
[0065] Embodiment 2 of the present invention provides an authentication method, which is a unified authentication method for an IP multimedia subsystem IMS network and an application server, and the executing subject of the method may be a CSCF.
[0066] Figure 4 It is an overall flow chart of the method in Embodiment 2 of the present invention. Such as Figure 4 As shown, the method includes:
[0067] S401. Receive an IP Multimedia Subsystem IMS network authentication request sent by a user equipment UE;
[0068] S402. Obtain application server authentication information from the home subscriber server HSS according to the IMS network authentication request;
[0069] Specifically, the above application server authentication information includes: application server authentication user name HTTP-Username, application server authentication password (can be extended to authentication certificate) HTTP-Token, application server additional parameter Add-ons (such as IP address...
Embodiment 3
[0116] Embodiment 3 of the present invention provides a method for transmitting authentication information of an application server, and the subject of execution of the method may be the HSS.
[0117] Figure 5 It is a flow chart of the method of Embodiment 3 of the present invention. Such as Figure 5 As shown, the method includes:
[0118] S501. Receive a first message sent by a call session control function entity CSCF, where the first message includes an identifier of a UE requesting IMS network authentication;
[0119] S502. According to the first message, determine whether there is application server authentication information corresponding to the UE;
[0120] S503. When there is application server authentication information corresponding to the UE, send a second message including the application server authentication information corresponding to the UE to the CSCF.
[0121] Optionally, the first message may be a SAR message, the second message may be an SAA message,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com