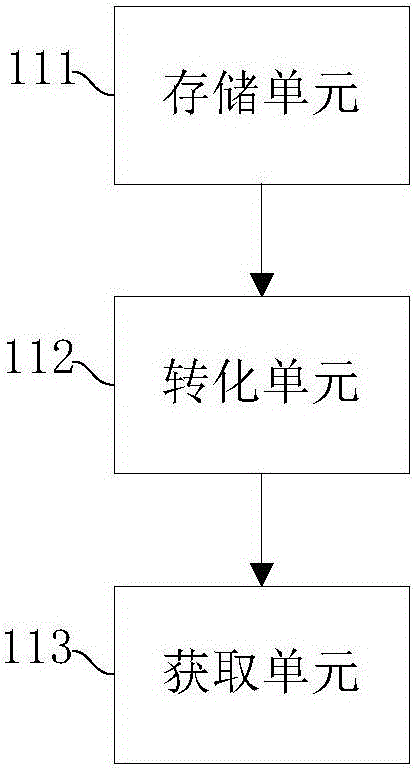
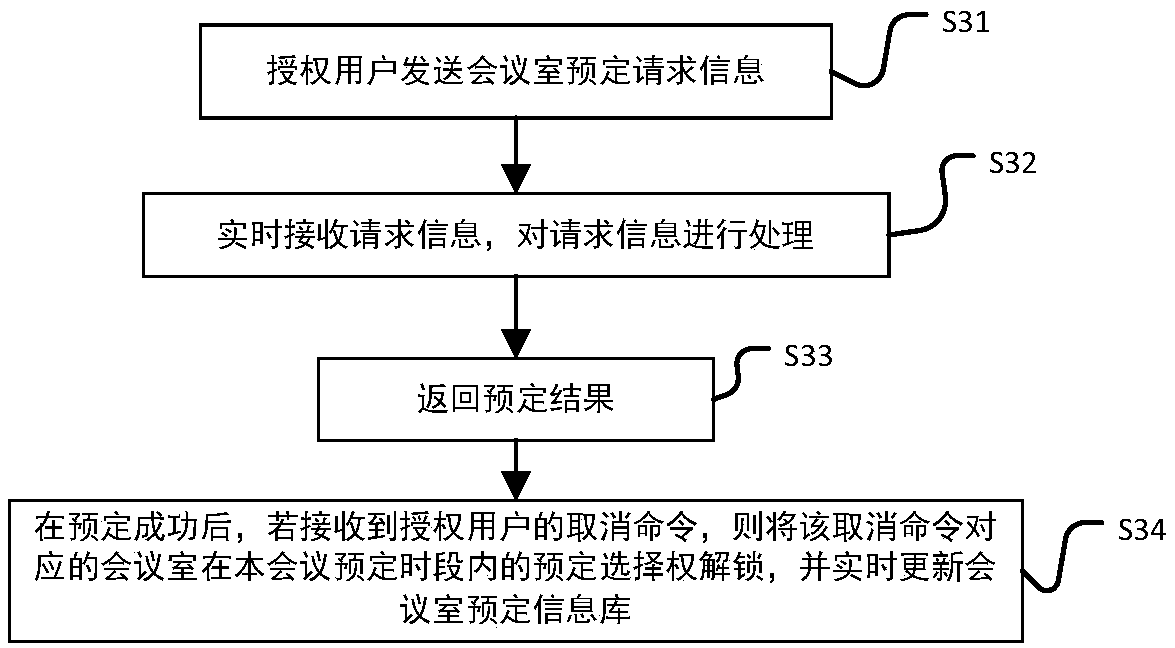
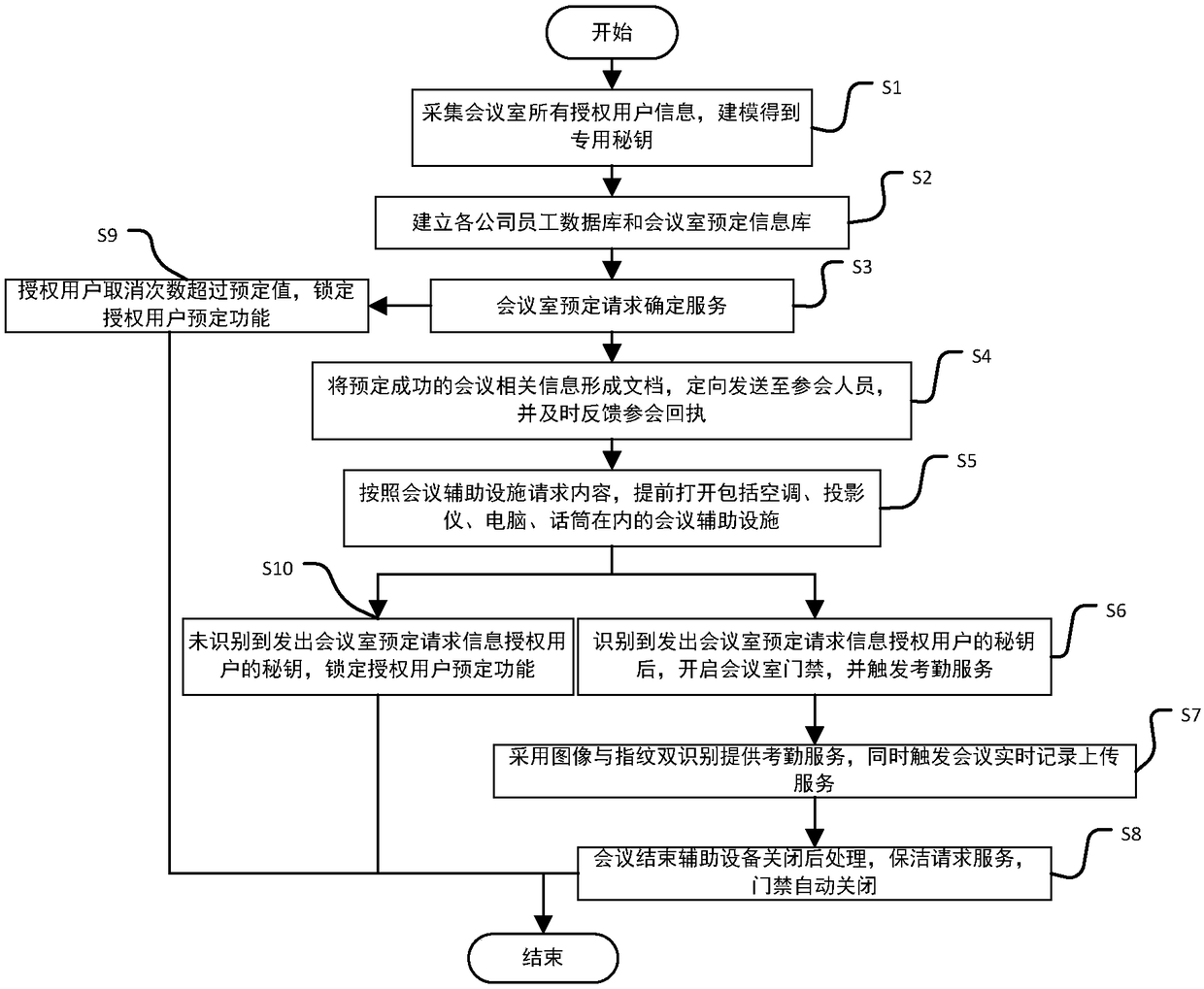
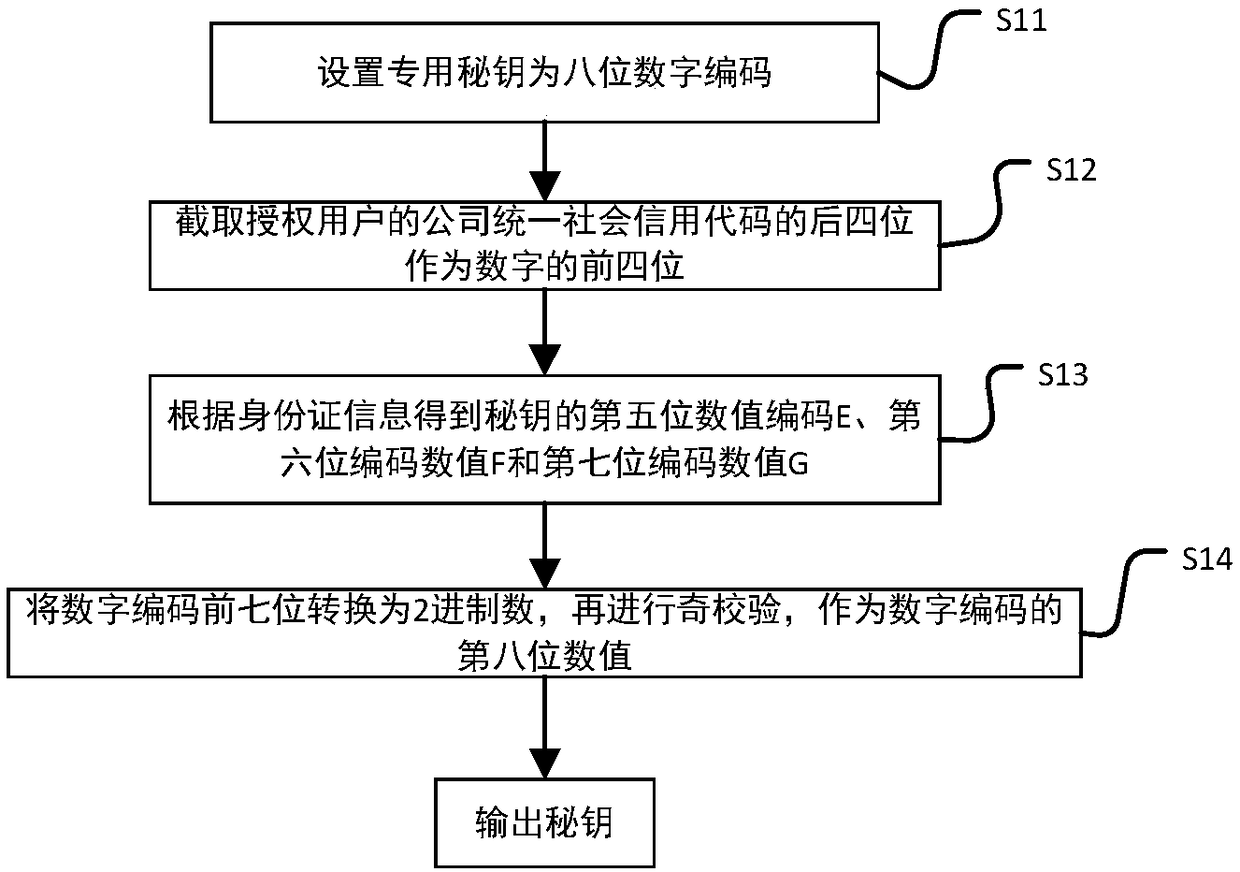
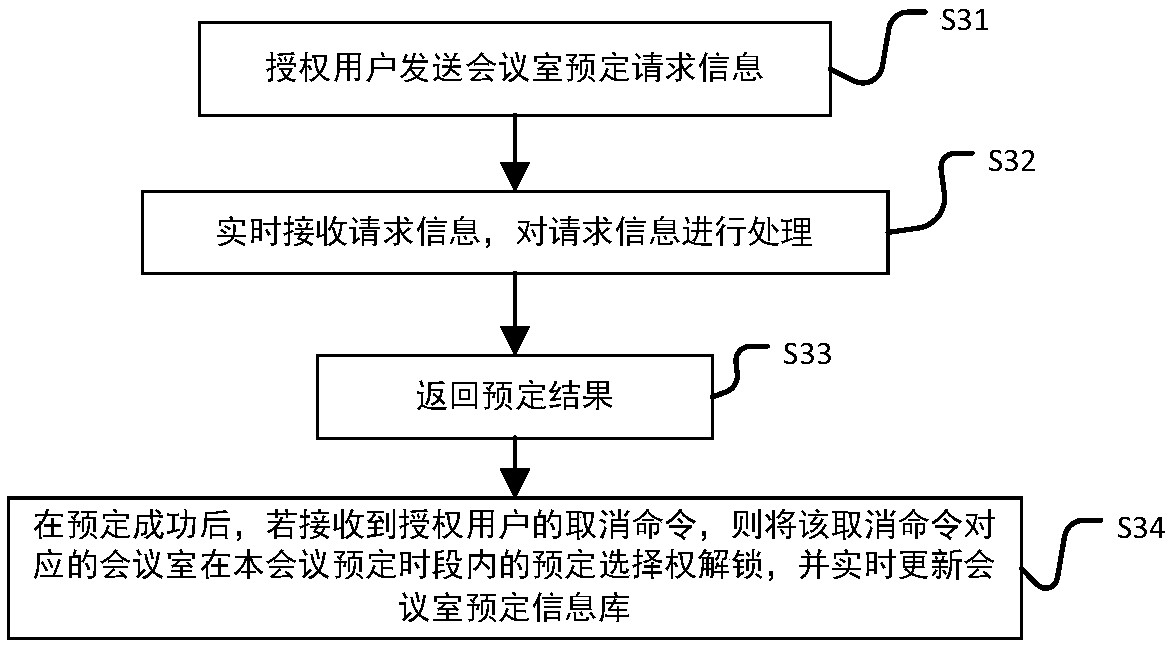
Patents
Literature
38results about How to "Realize unified authentication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
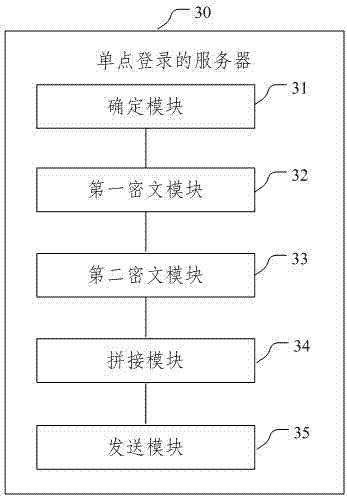
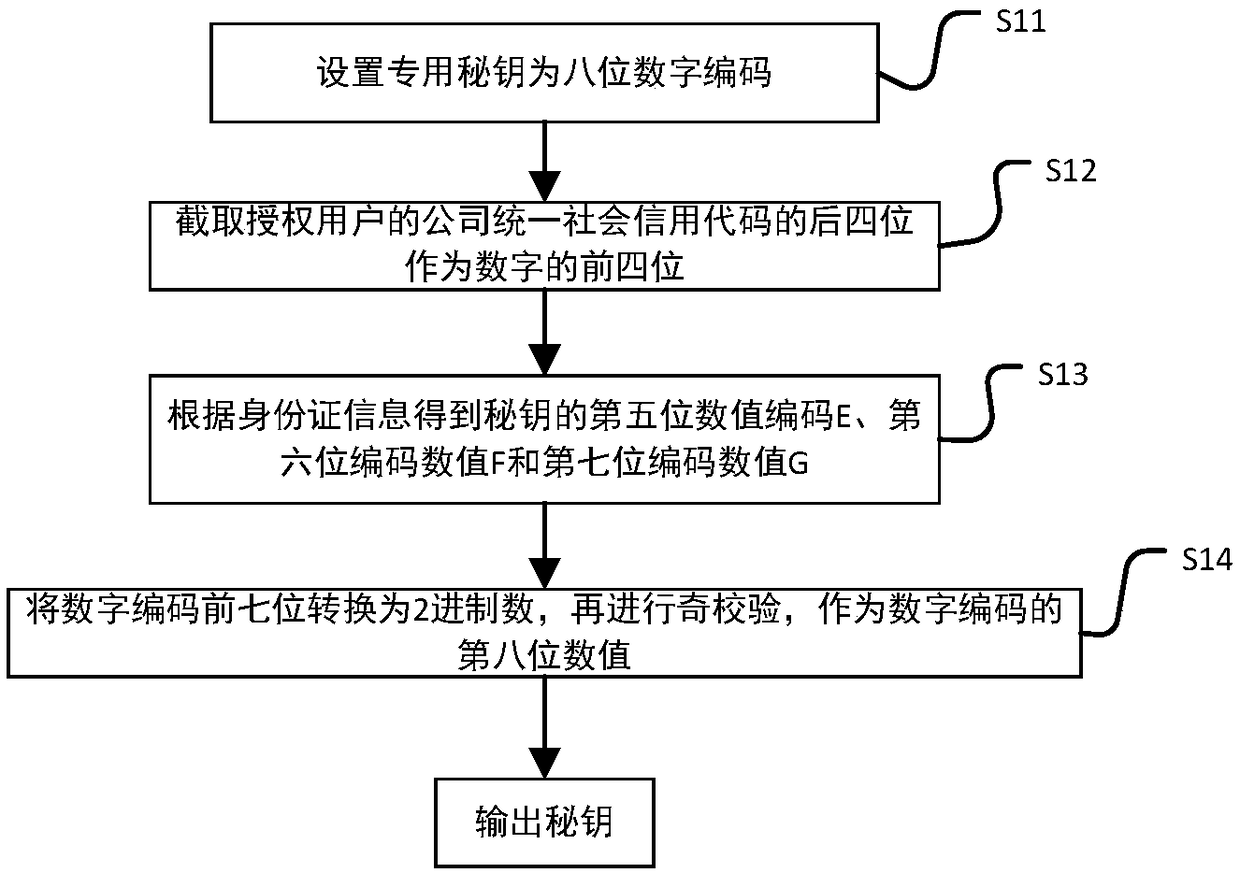
Single sign-on method, server and client
InactiveCN106936759AProtect data securityImprove user experienceTransmissionClient-sideData security
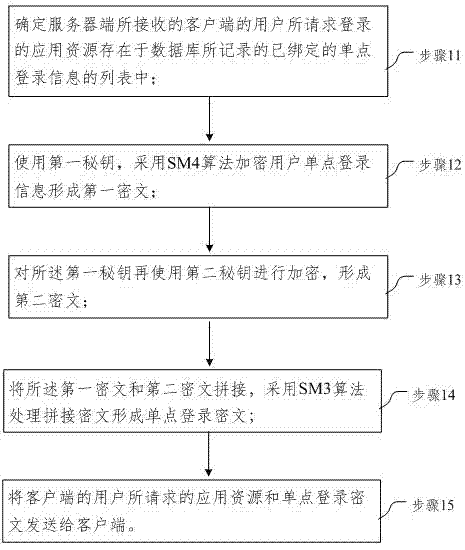
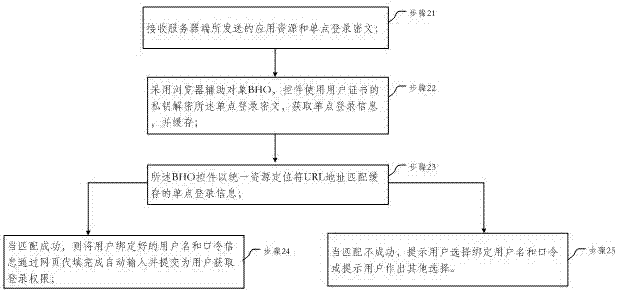
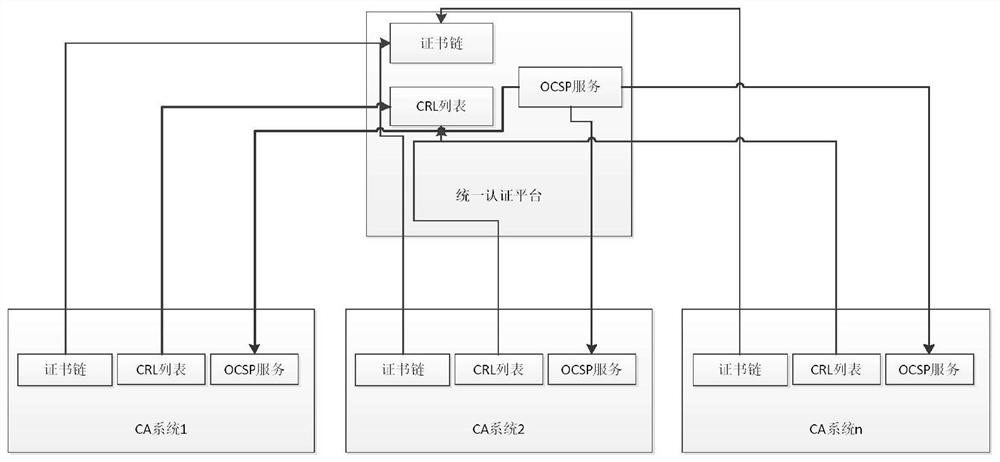
The embodiment of the invention provides a single sign-on method, server and client. In the embodiment of the invention, the method comprises the following steps: determining that application resources on which a user of a client requests to sign received by a server side exist in a list of bound single sign-on information recorded in a database; encrypting single sign-on information of the user by a first key through an SM4 algorithm to form a first ciphertext; encrypting the first key with a second key to form a second ciphertext; splicing the first ciphertext and the second ciphertext, and processing a spliced ciphertext through an SM3 algorithm to form a single sign-on ciphertext; and transmitting the application resources requested by the user of the client and the single sign-on ciphertext to the client. Through adoption of the single sign-on method, server and client, data security is protected through a GMB algorithm; the identity of the user is identified by taking a digital certificate as a carrier; uniform authentication is realized; a plurality of independent application systems can be used in single sign-on; and the user experience is improved.
Owner:AEROSPACE INFORMATION
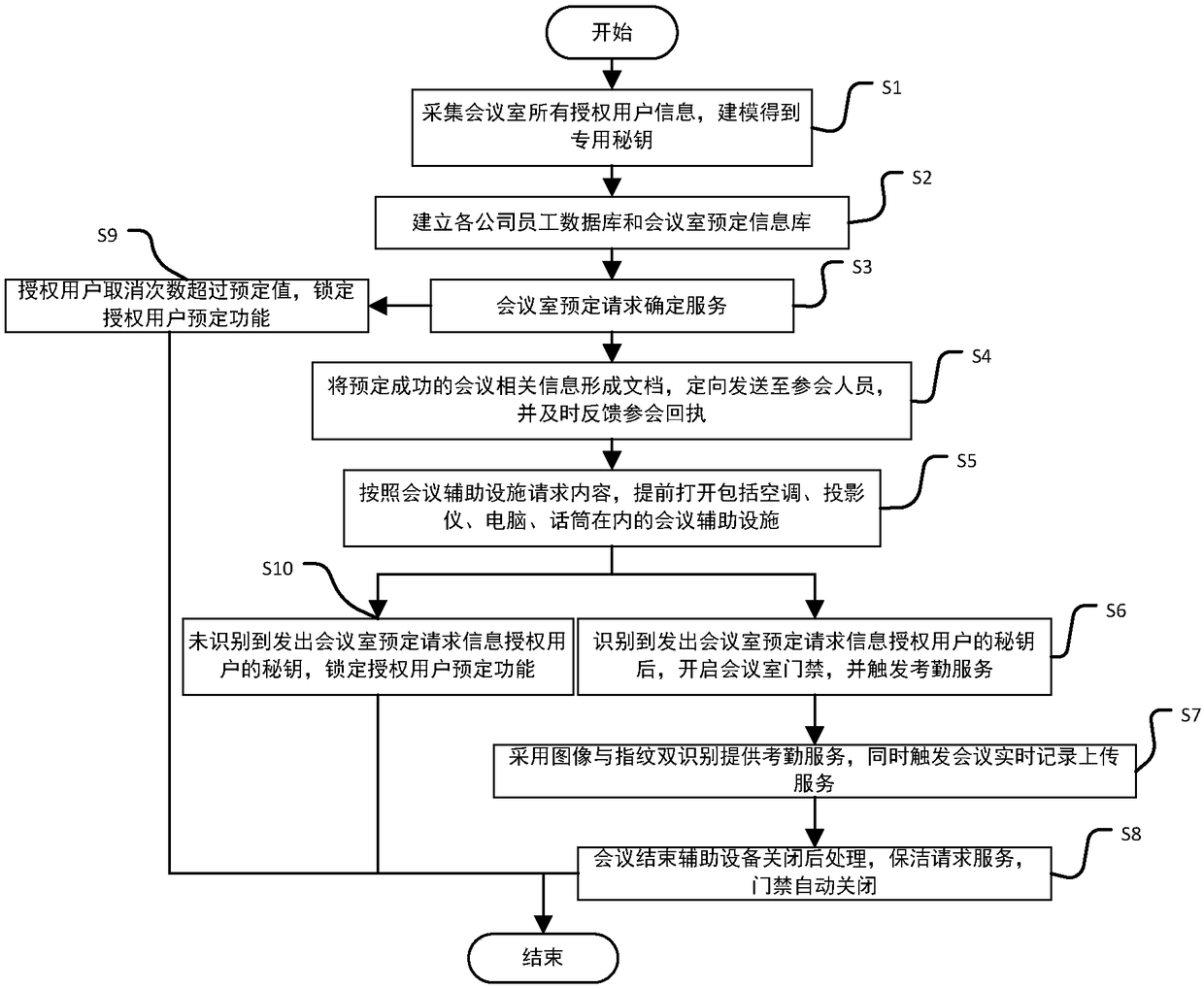
Intelligent conference control method and system
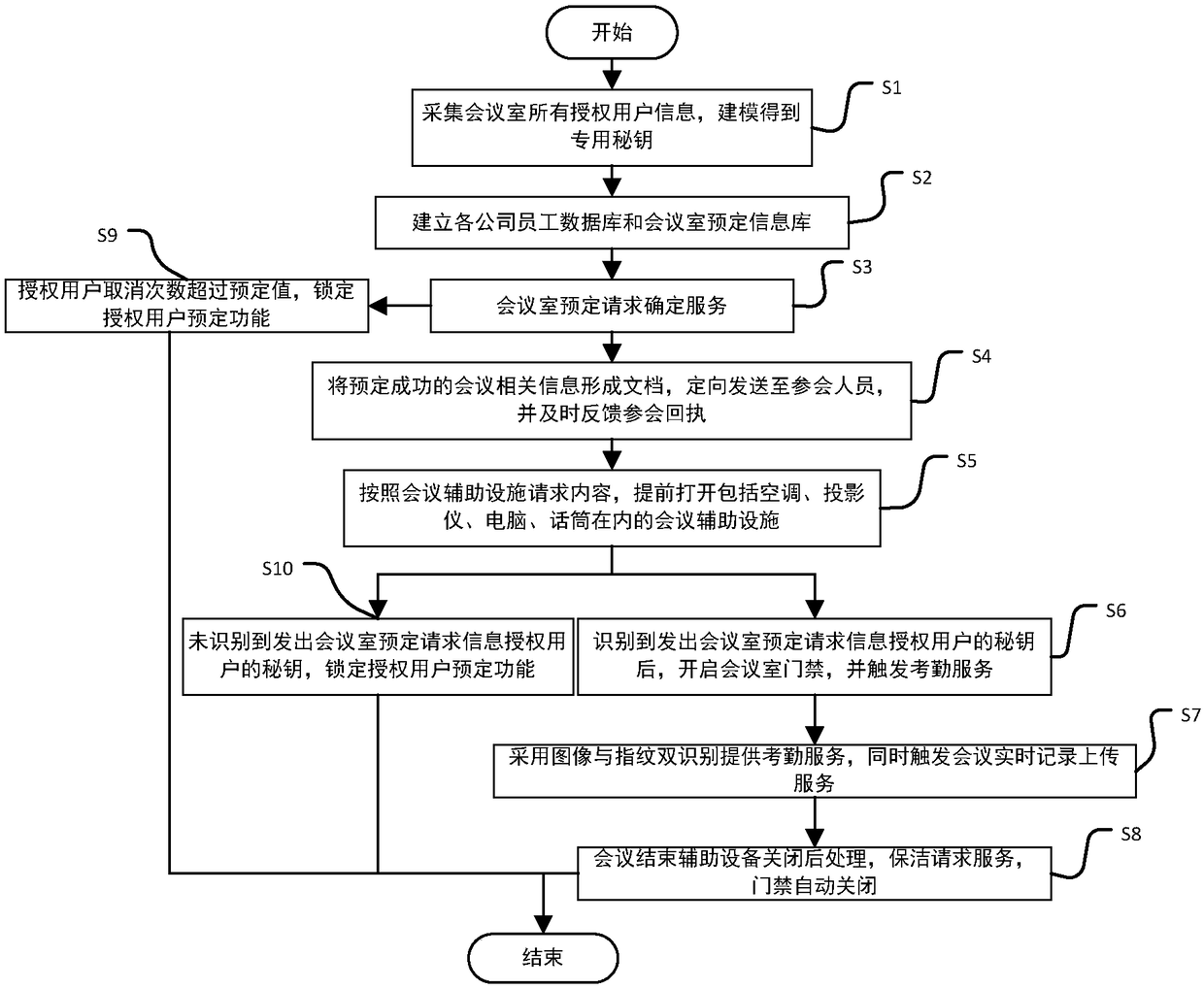
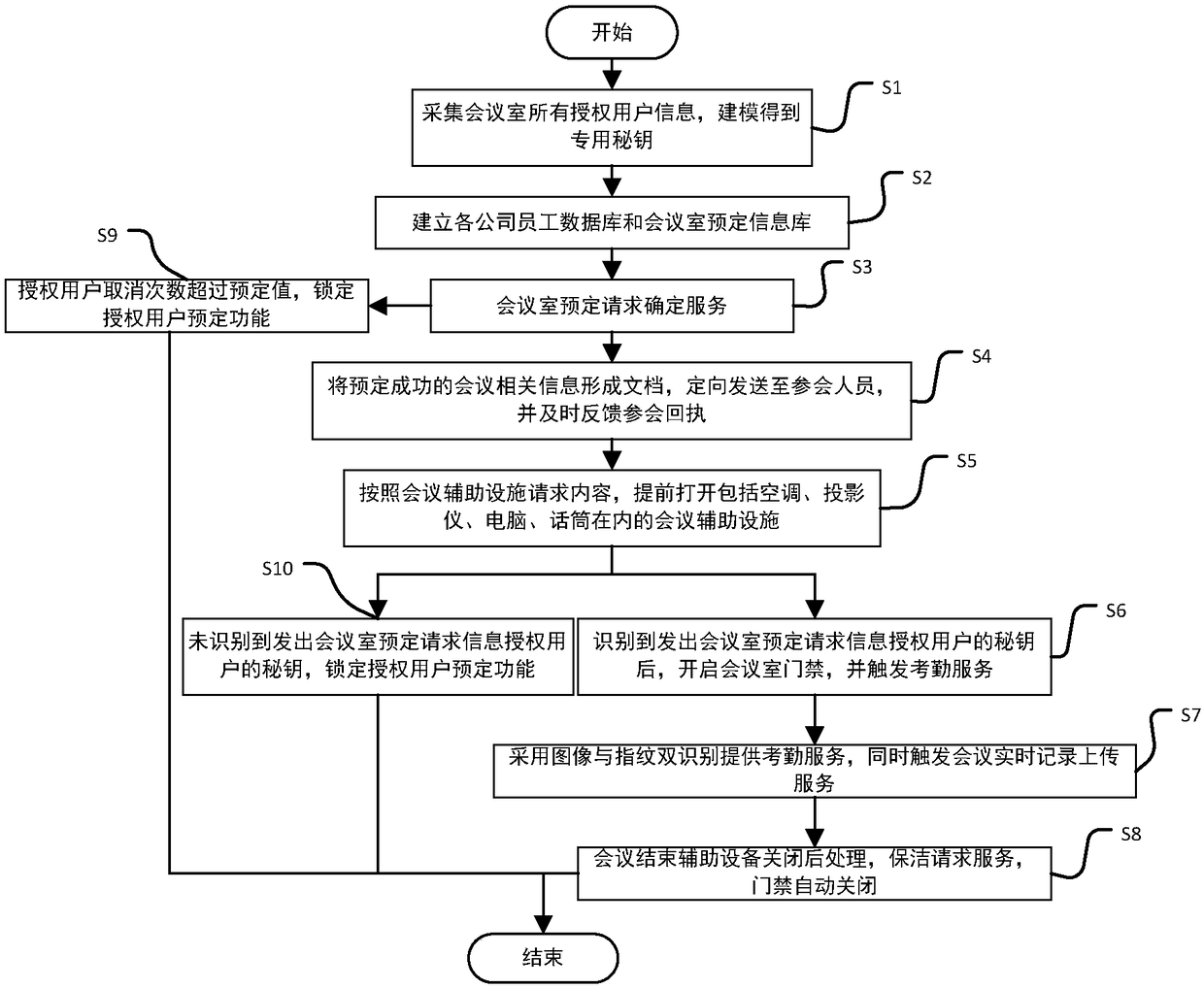
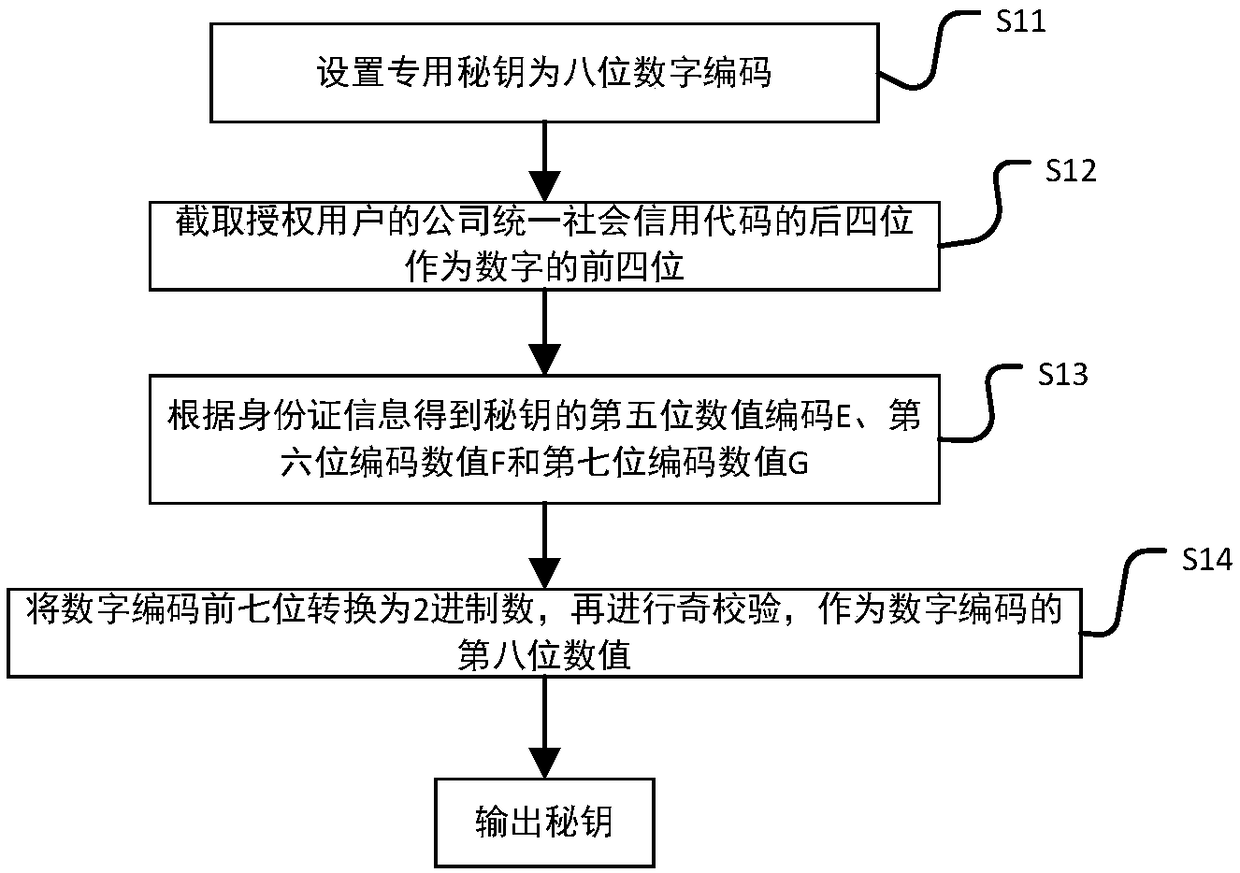
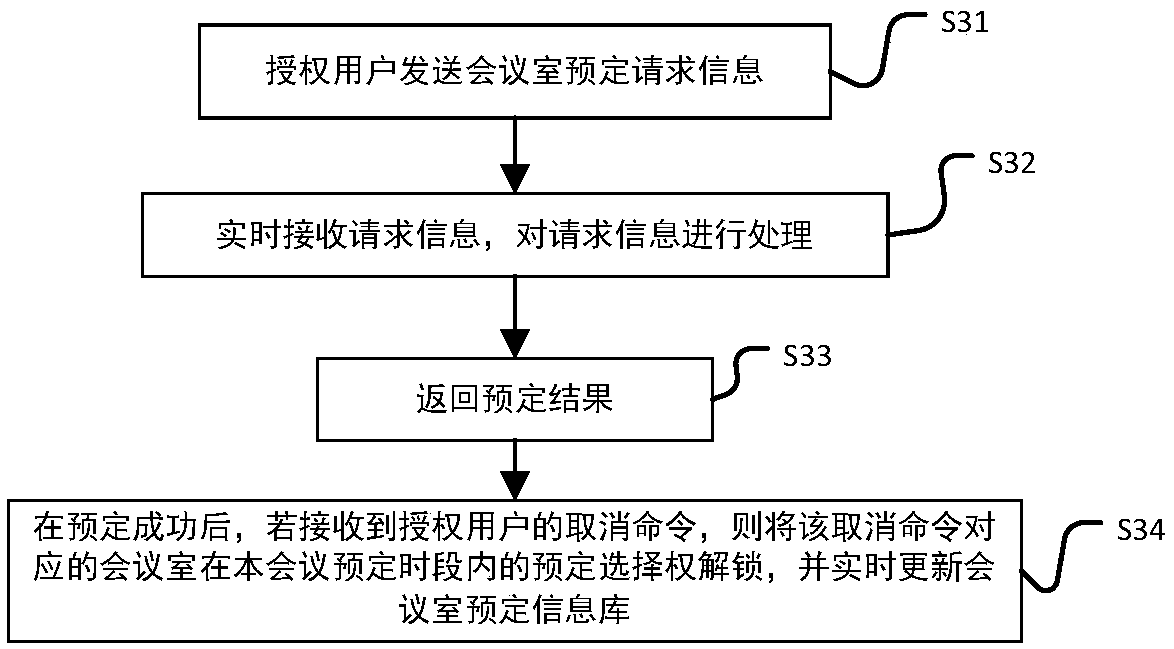
InactiveCN108846647AConvenient and fast bookingThe process is convenient and fastOffice automationData acquisitionComputer module
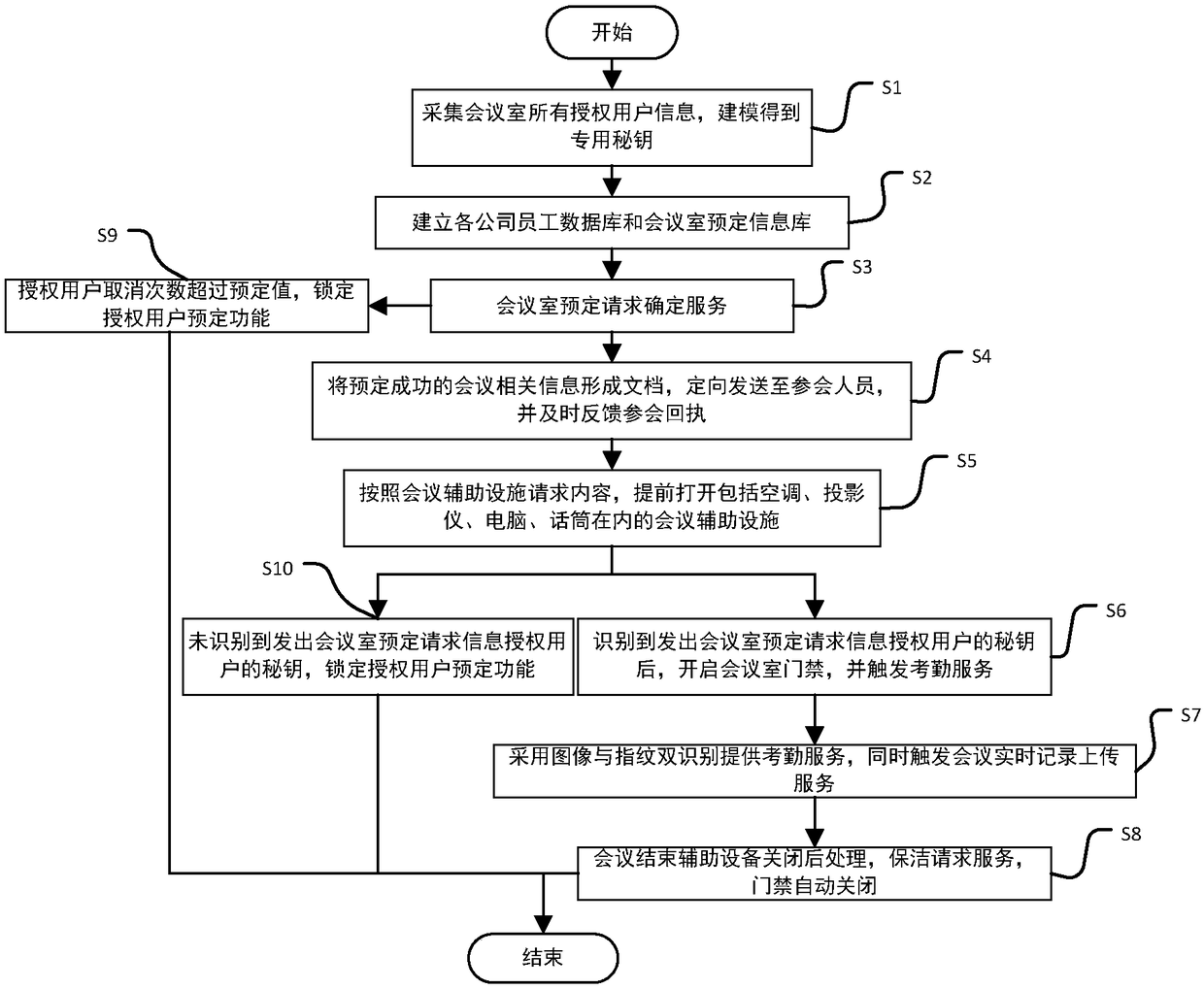
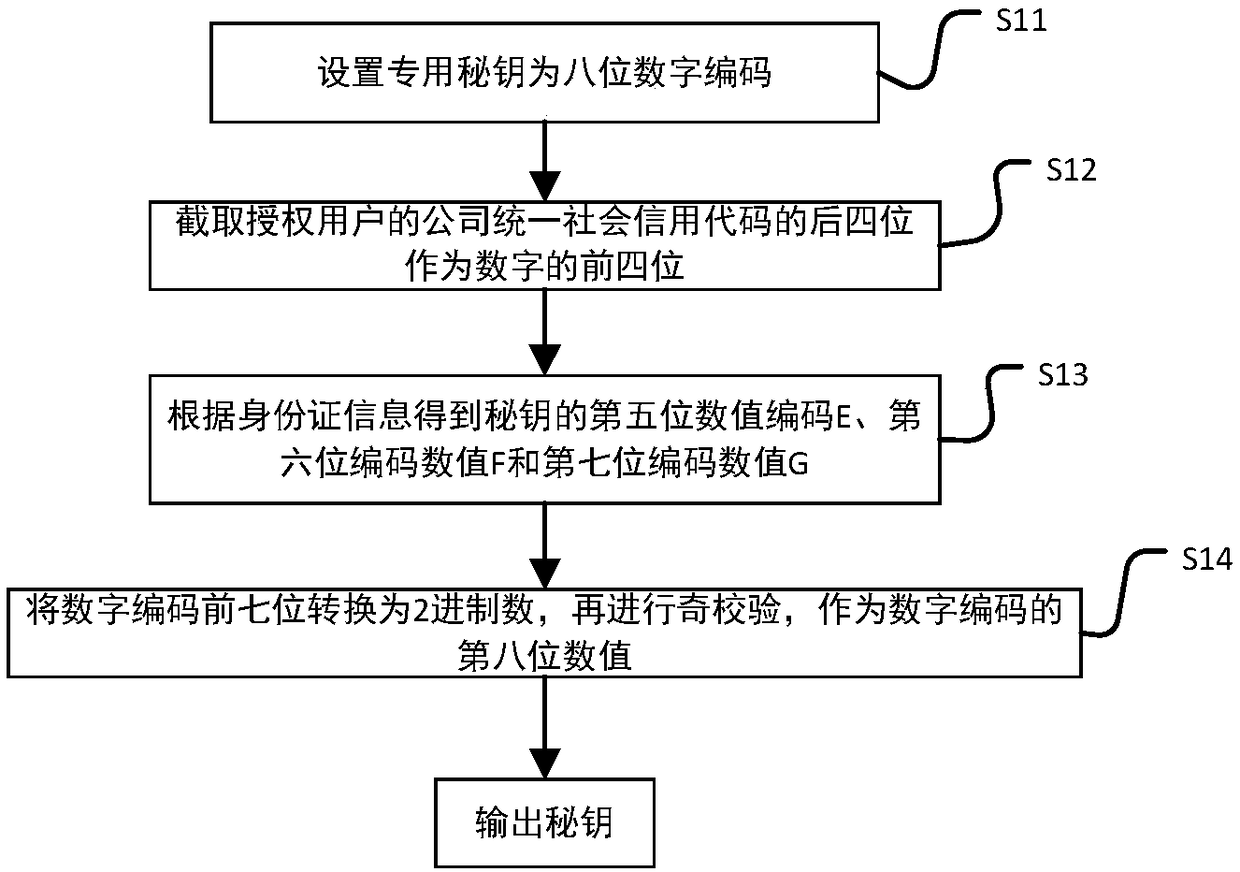
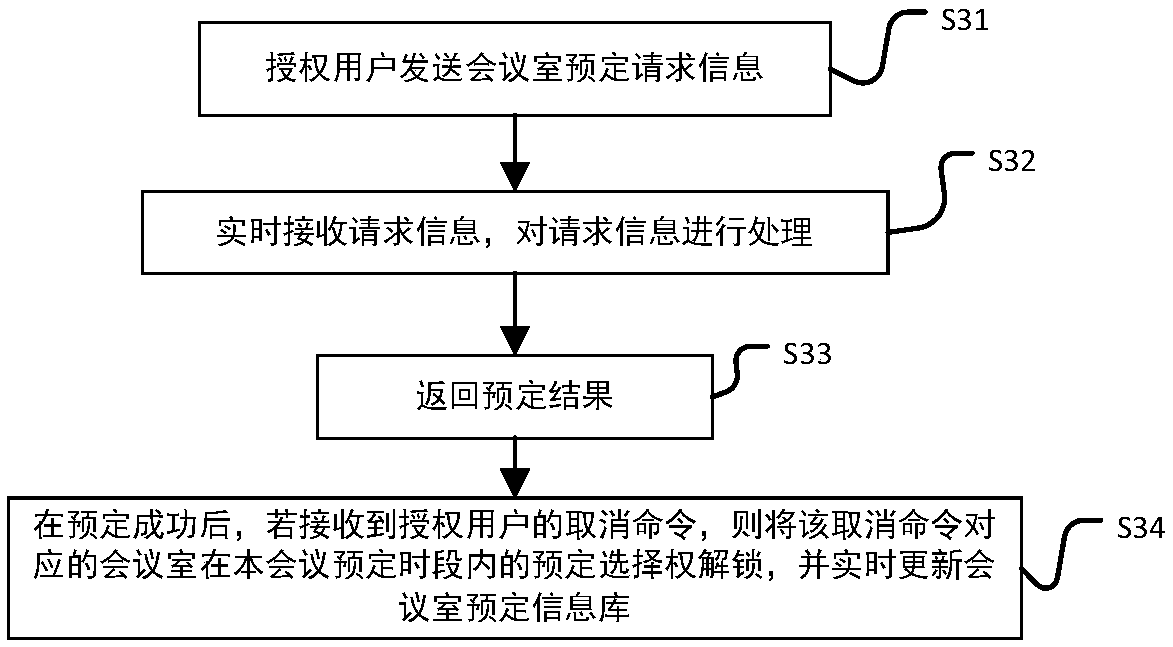
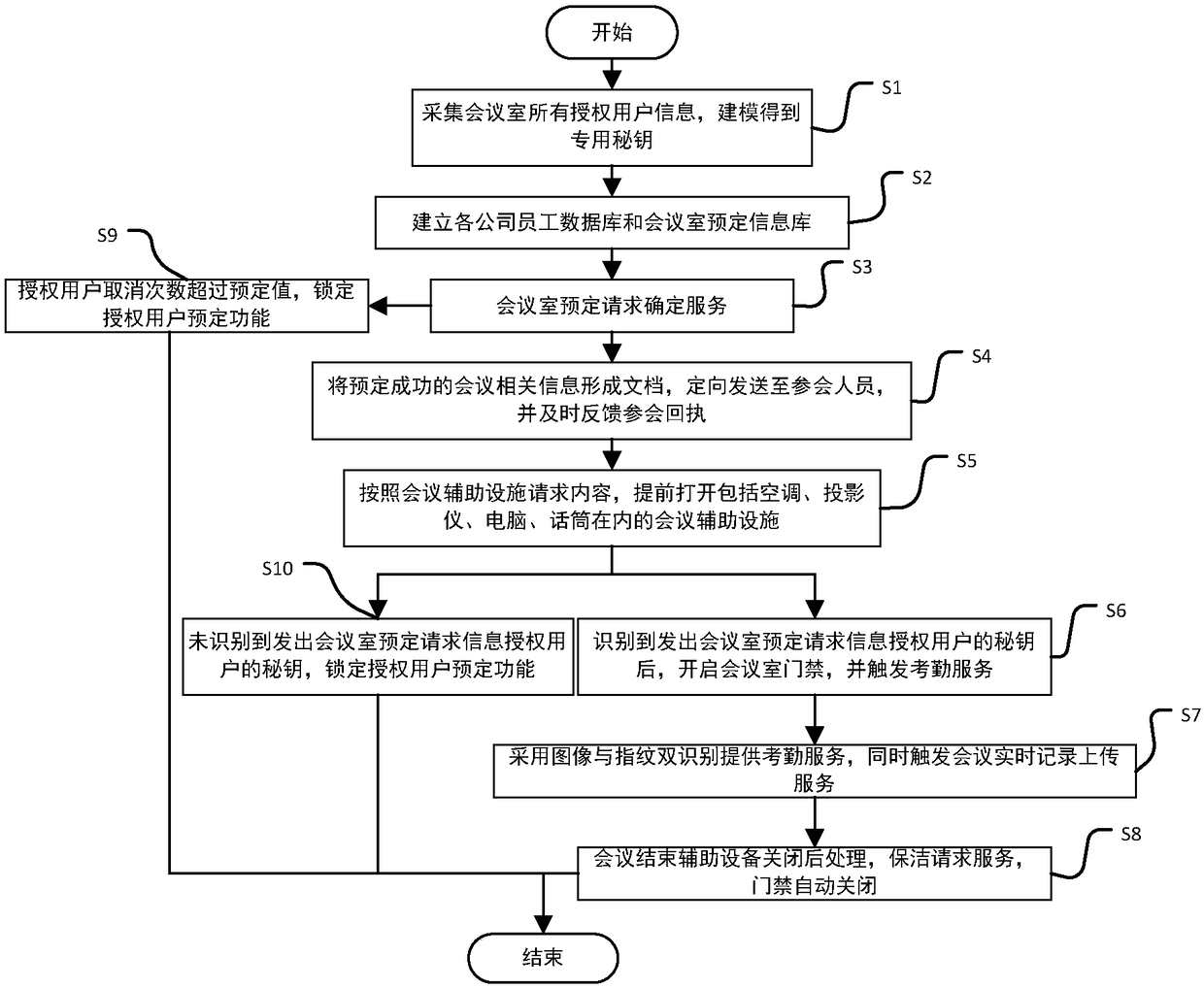
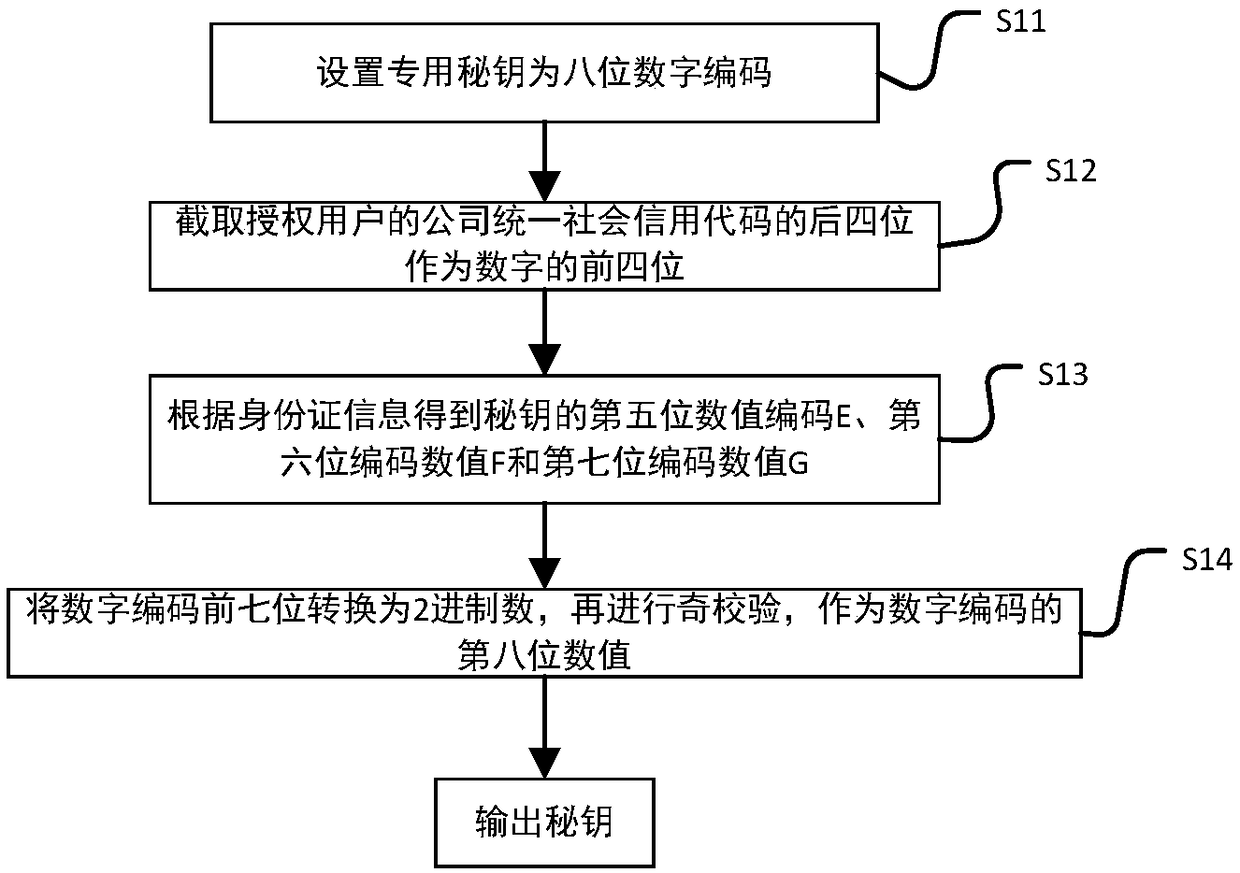
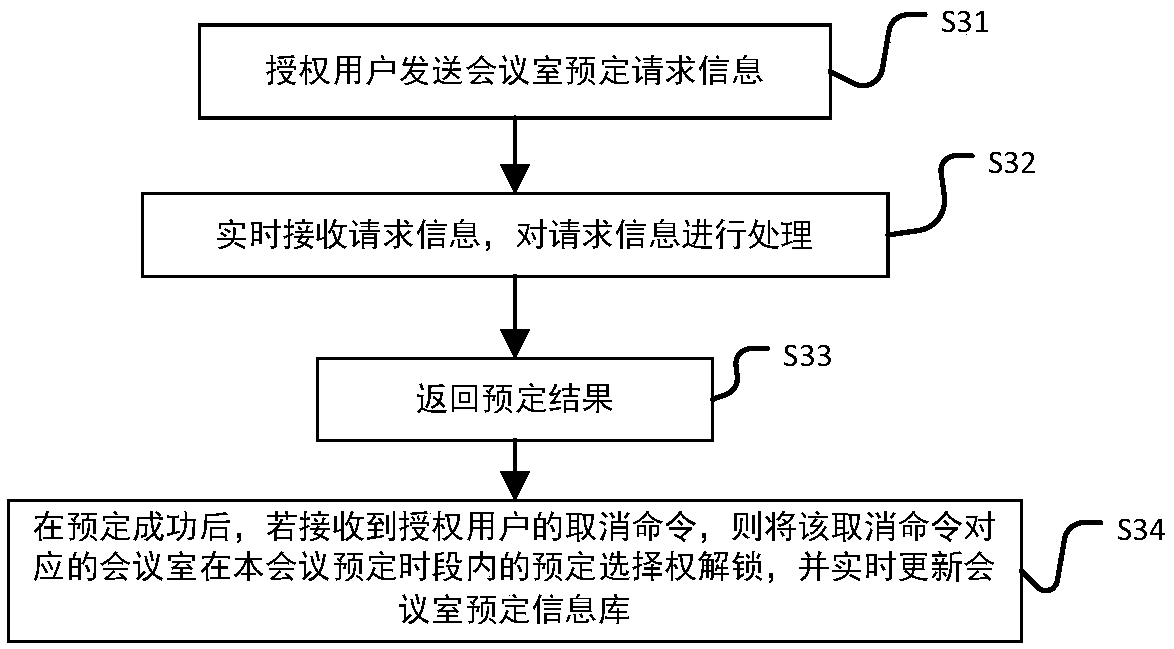
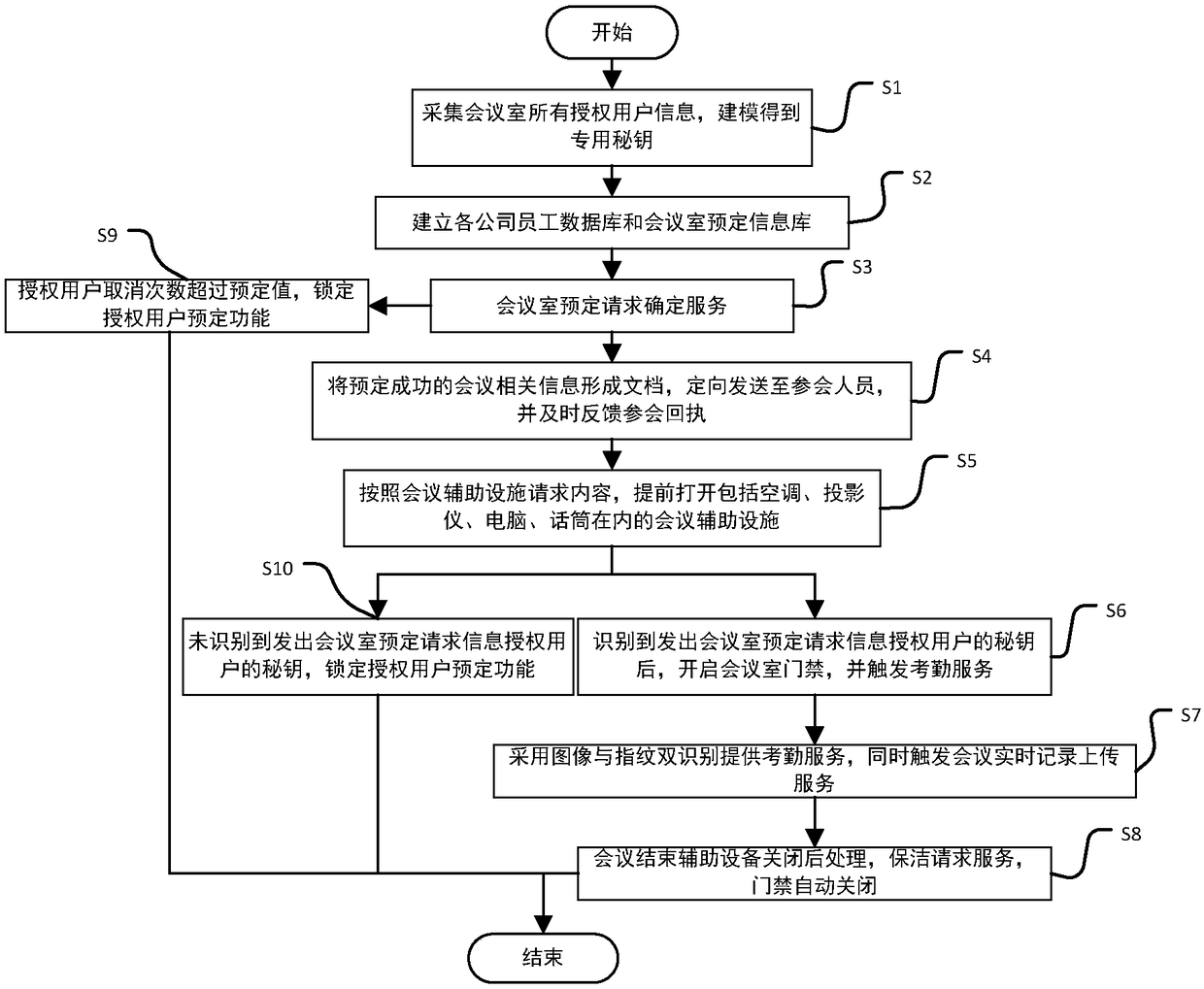
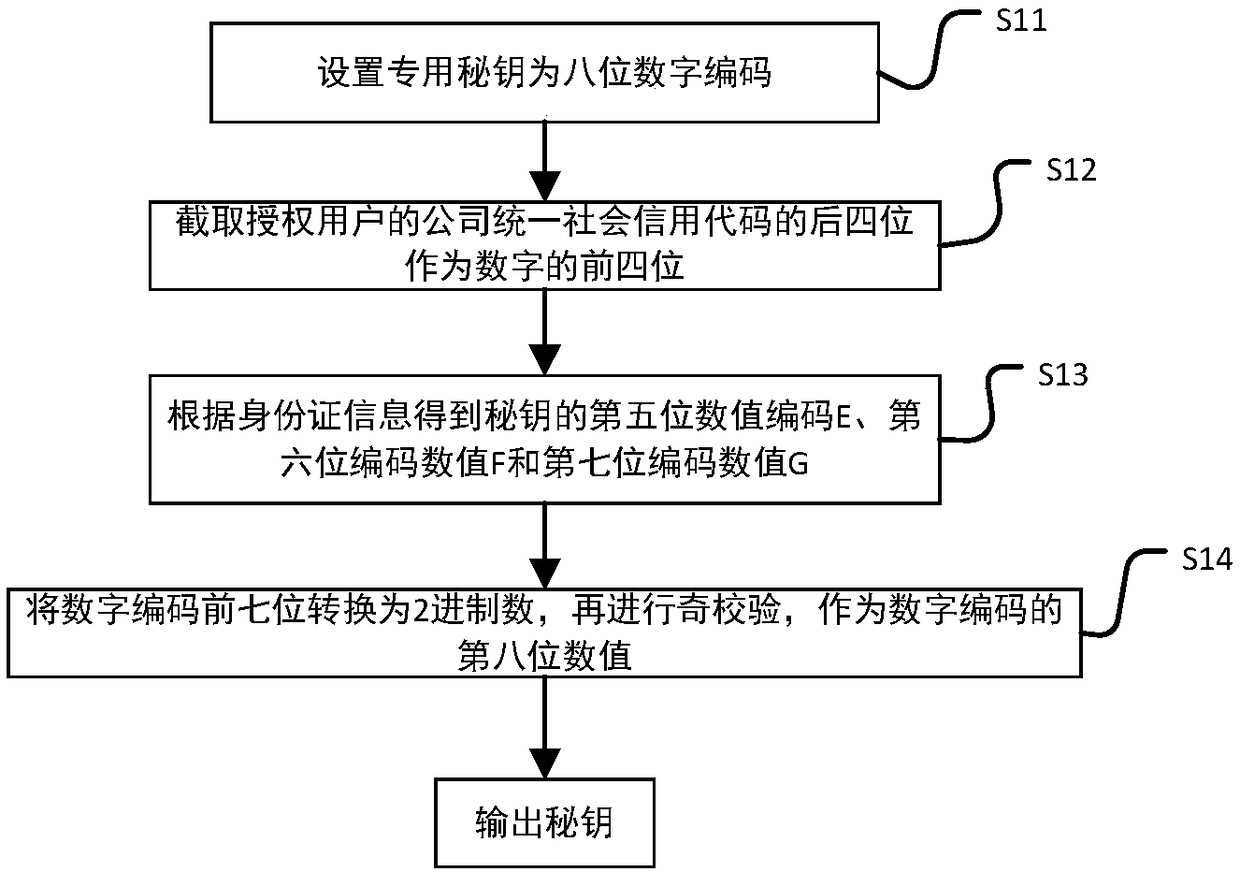
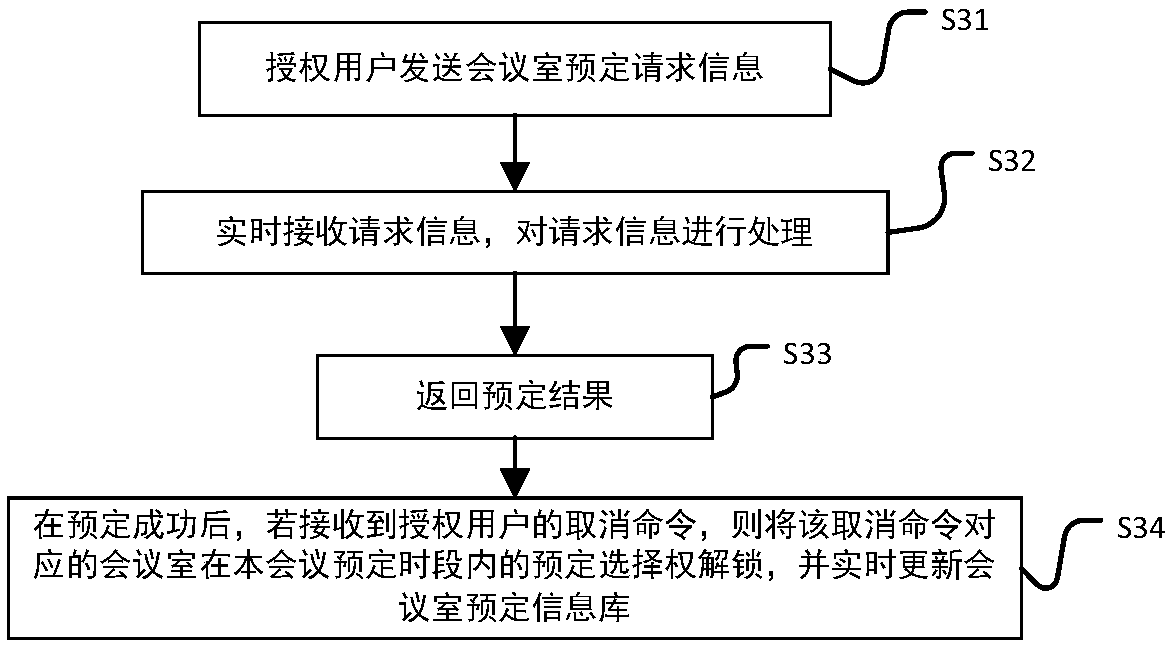
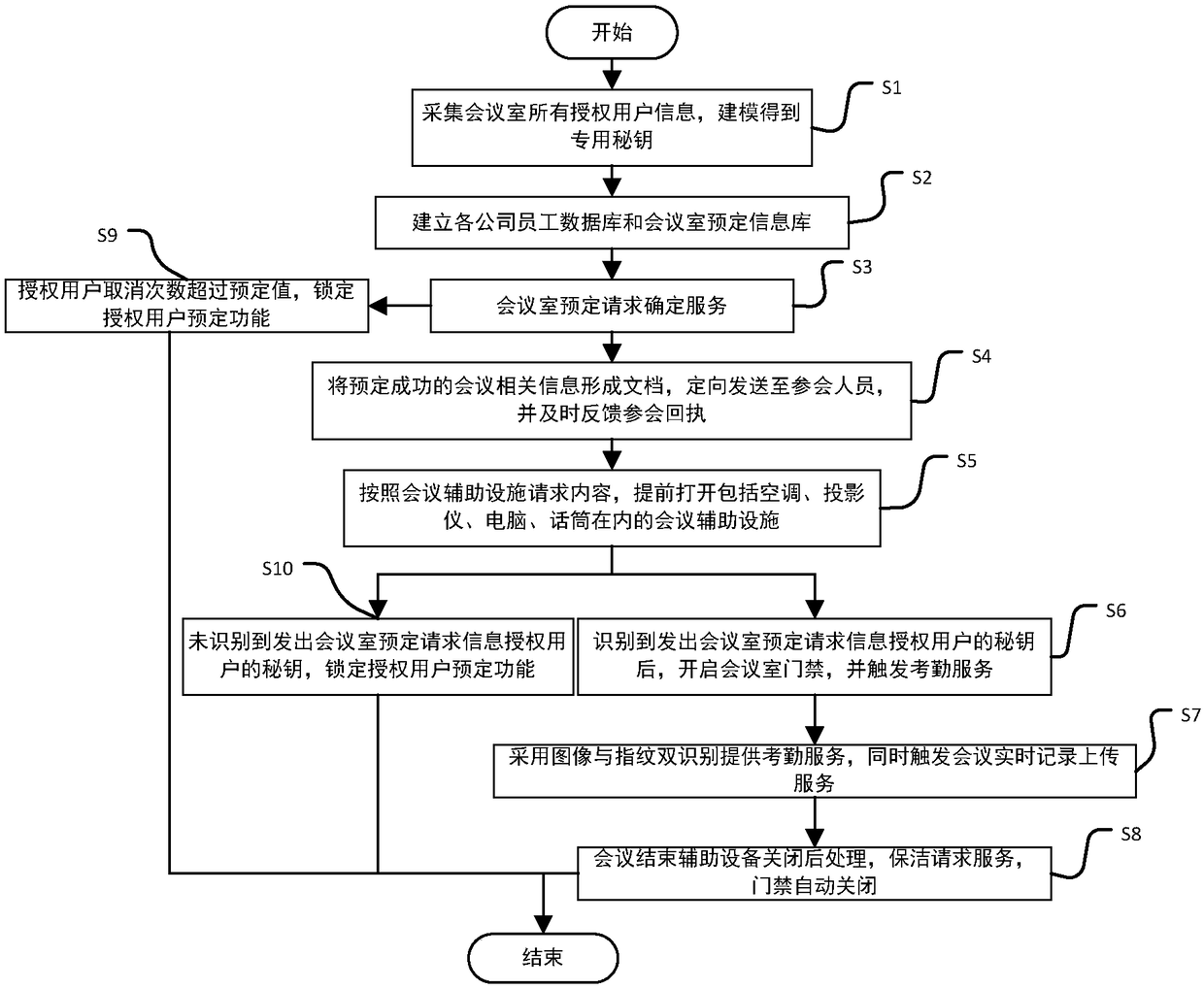
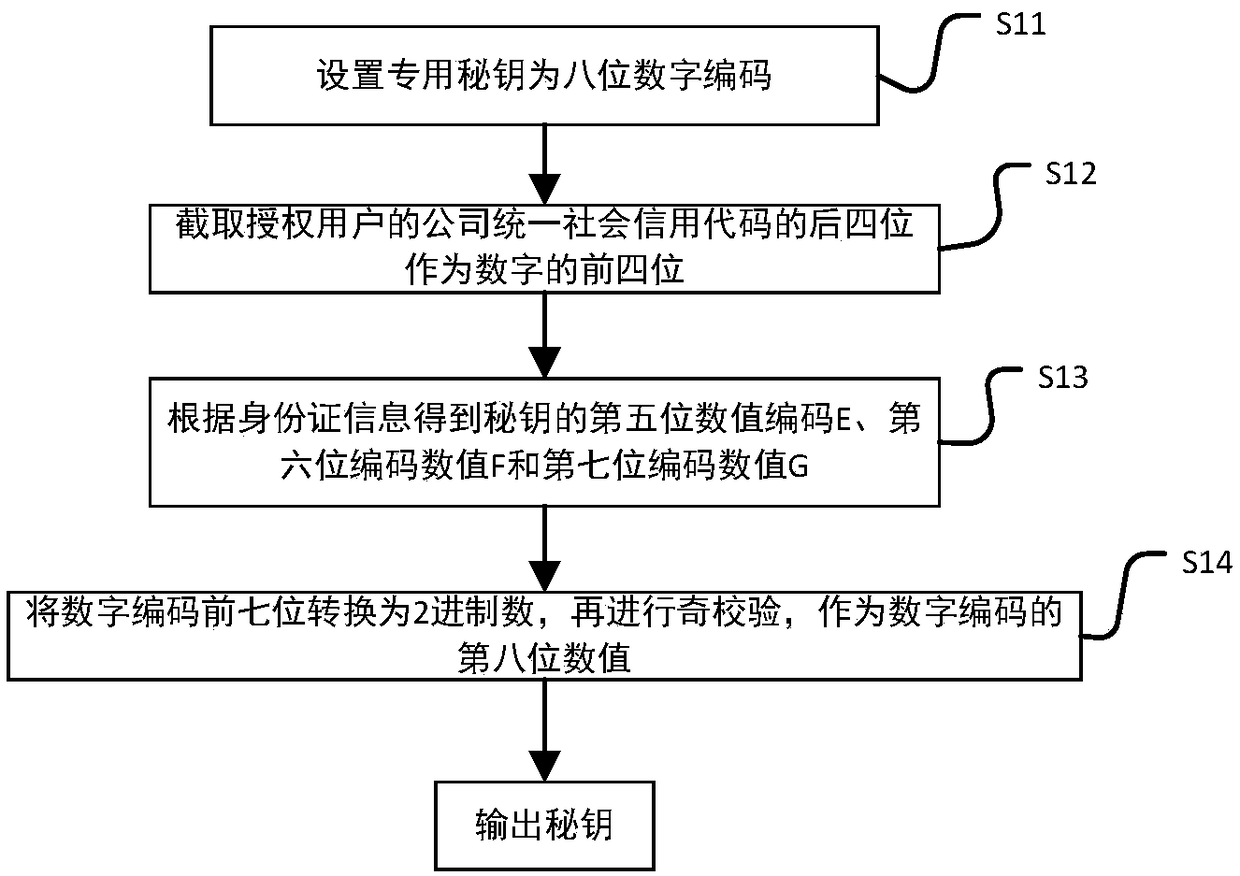
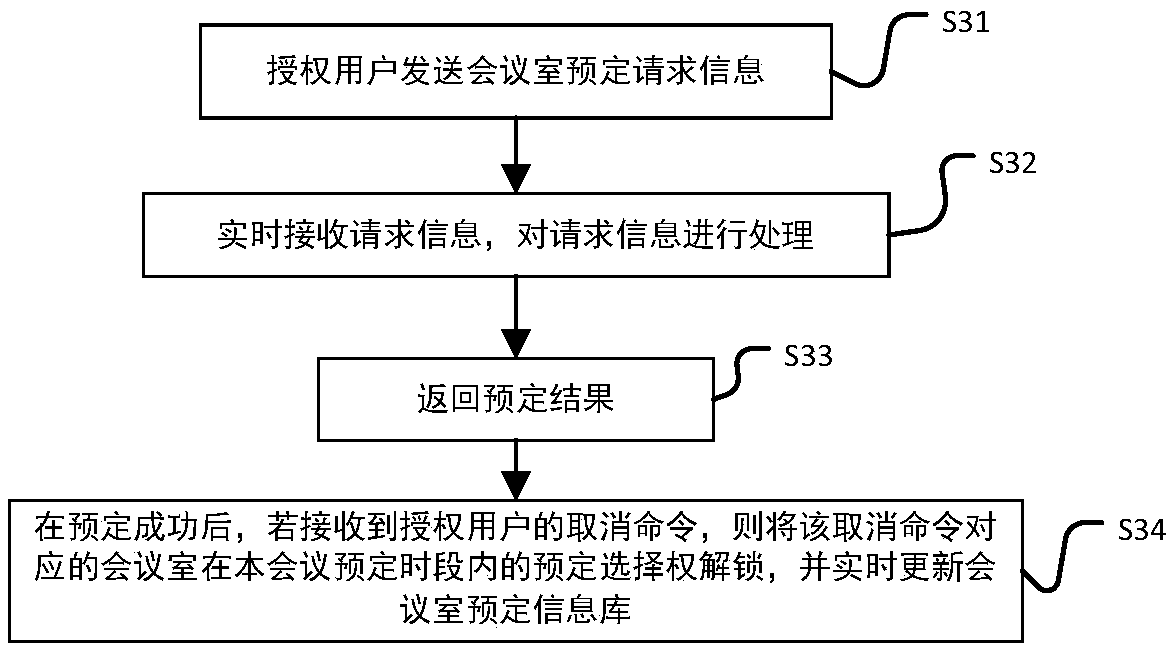
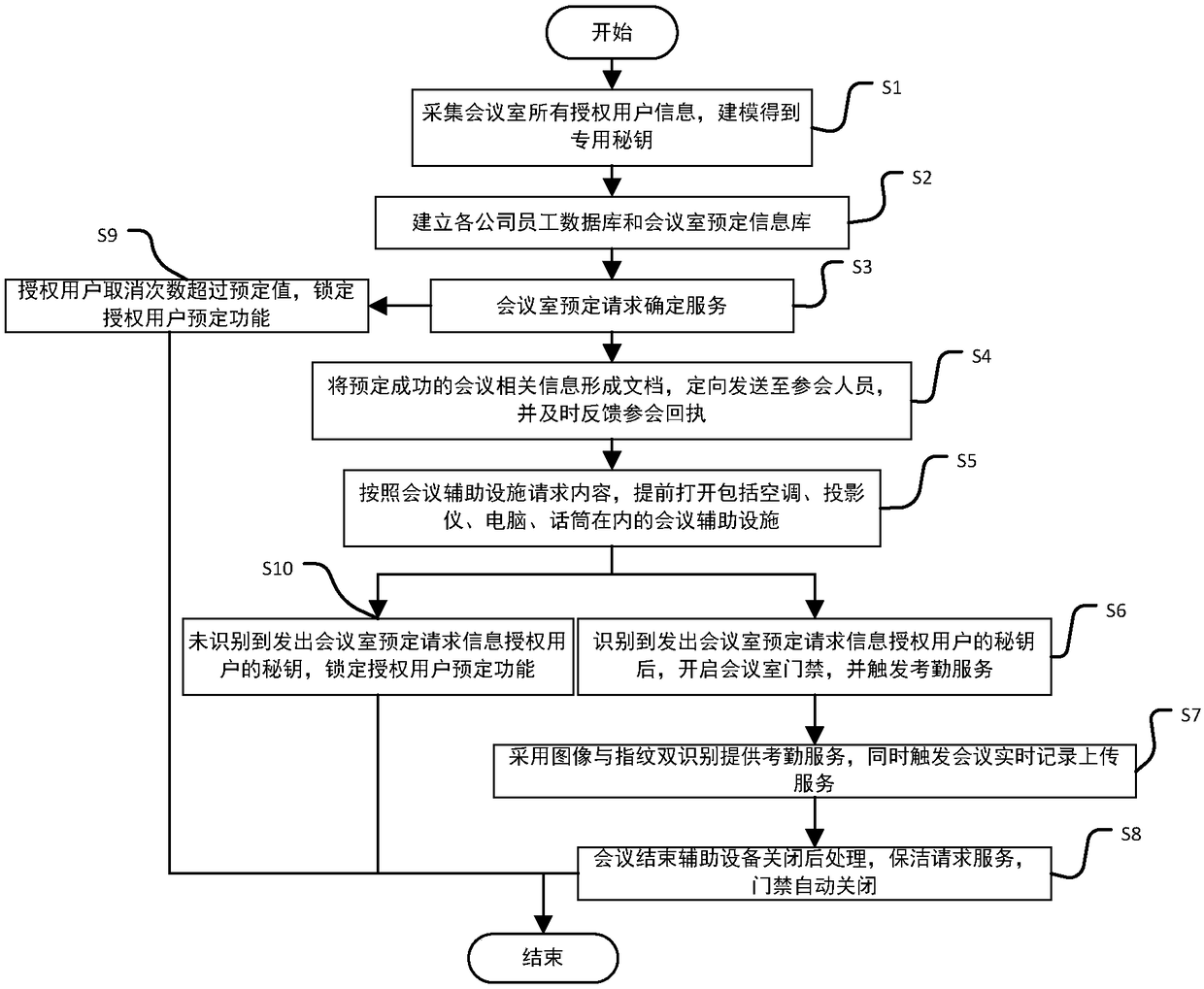
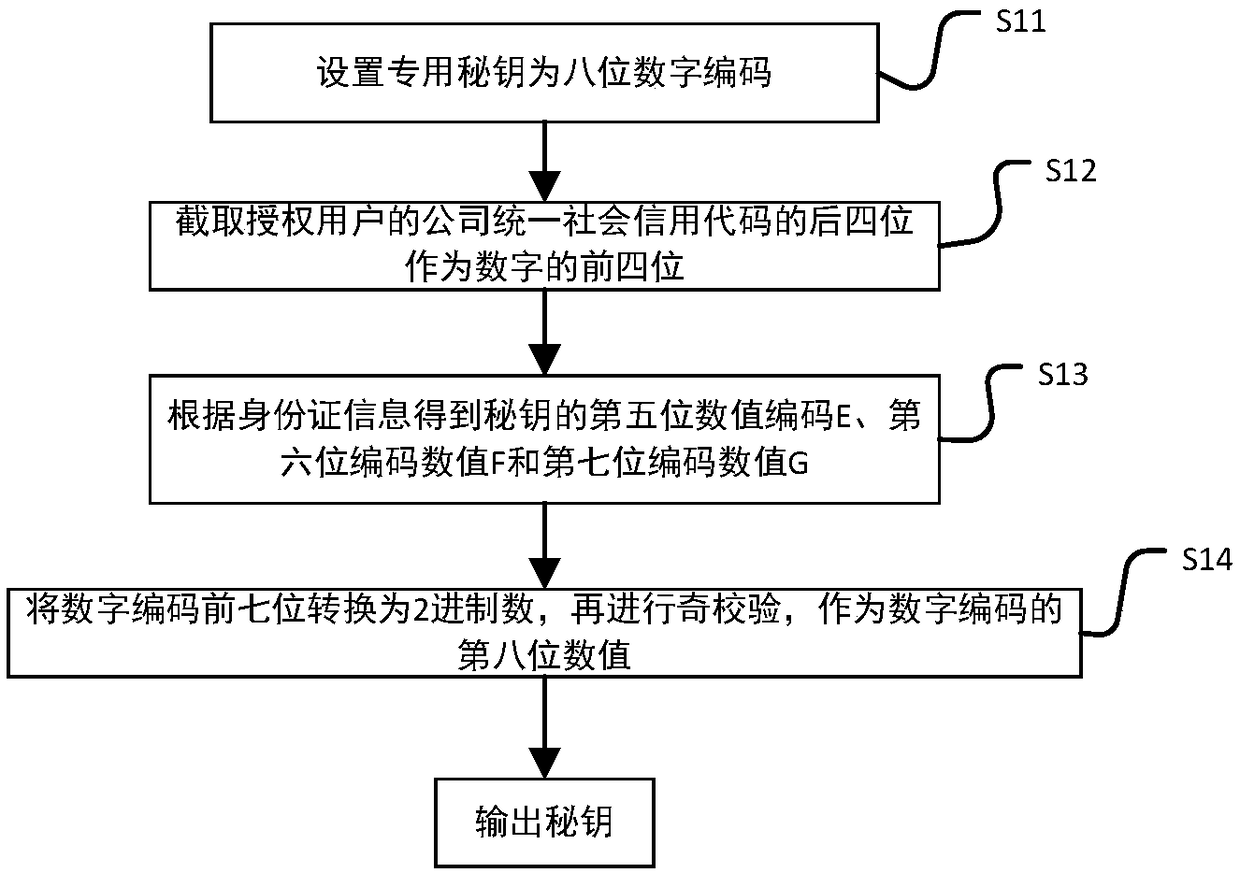
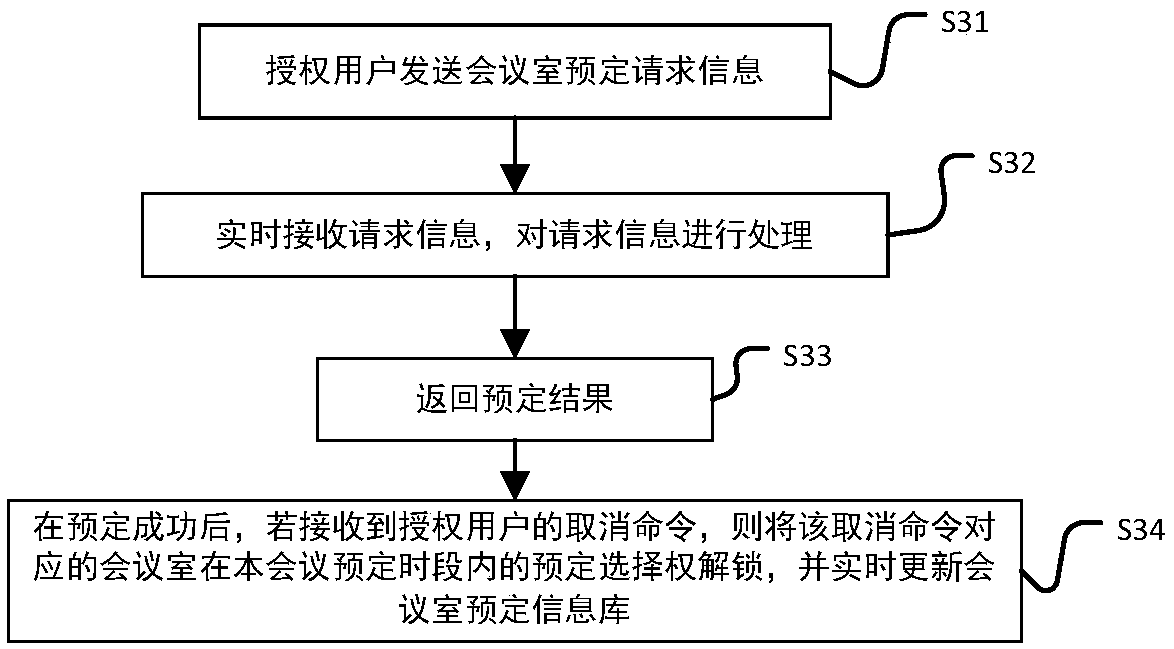
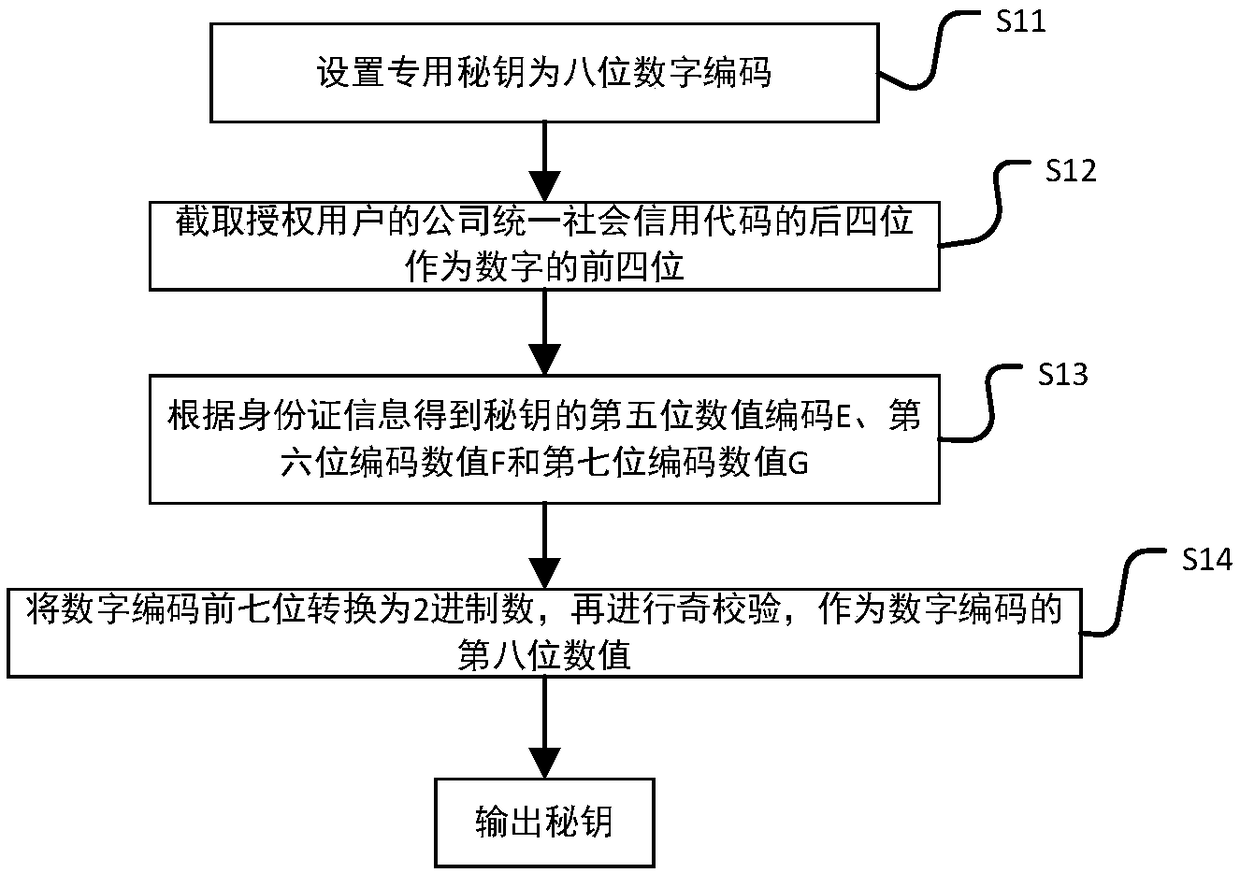
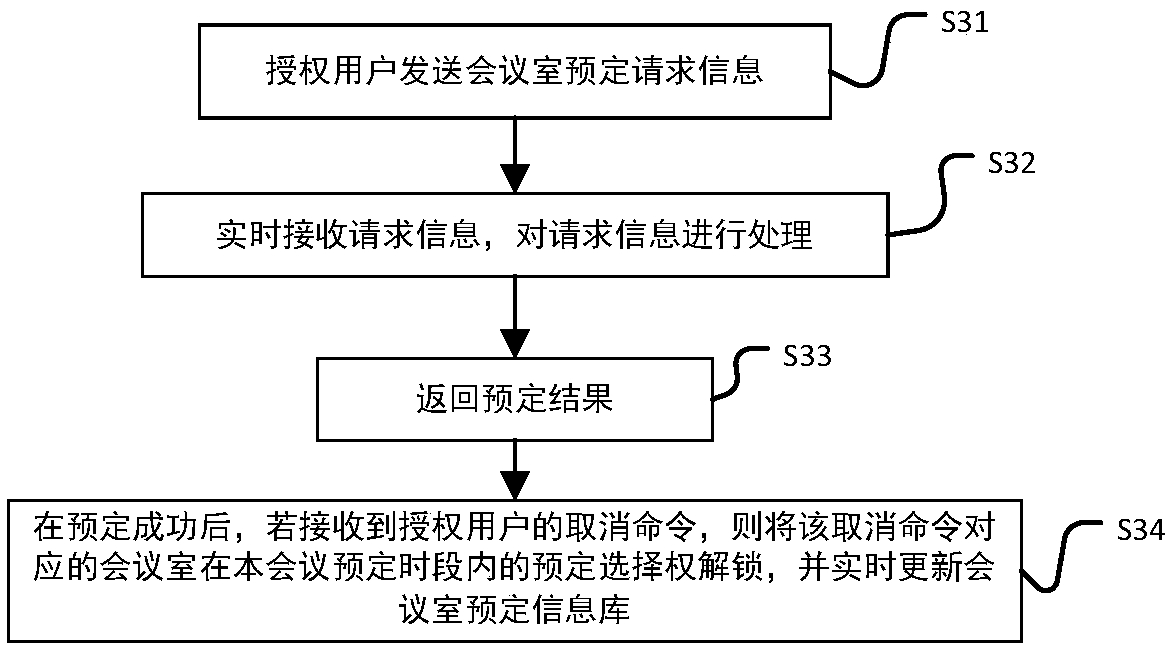
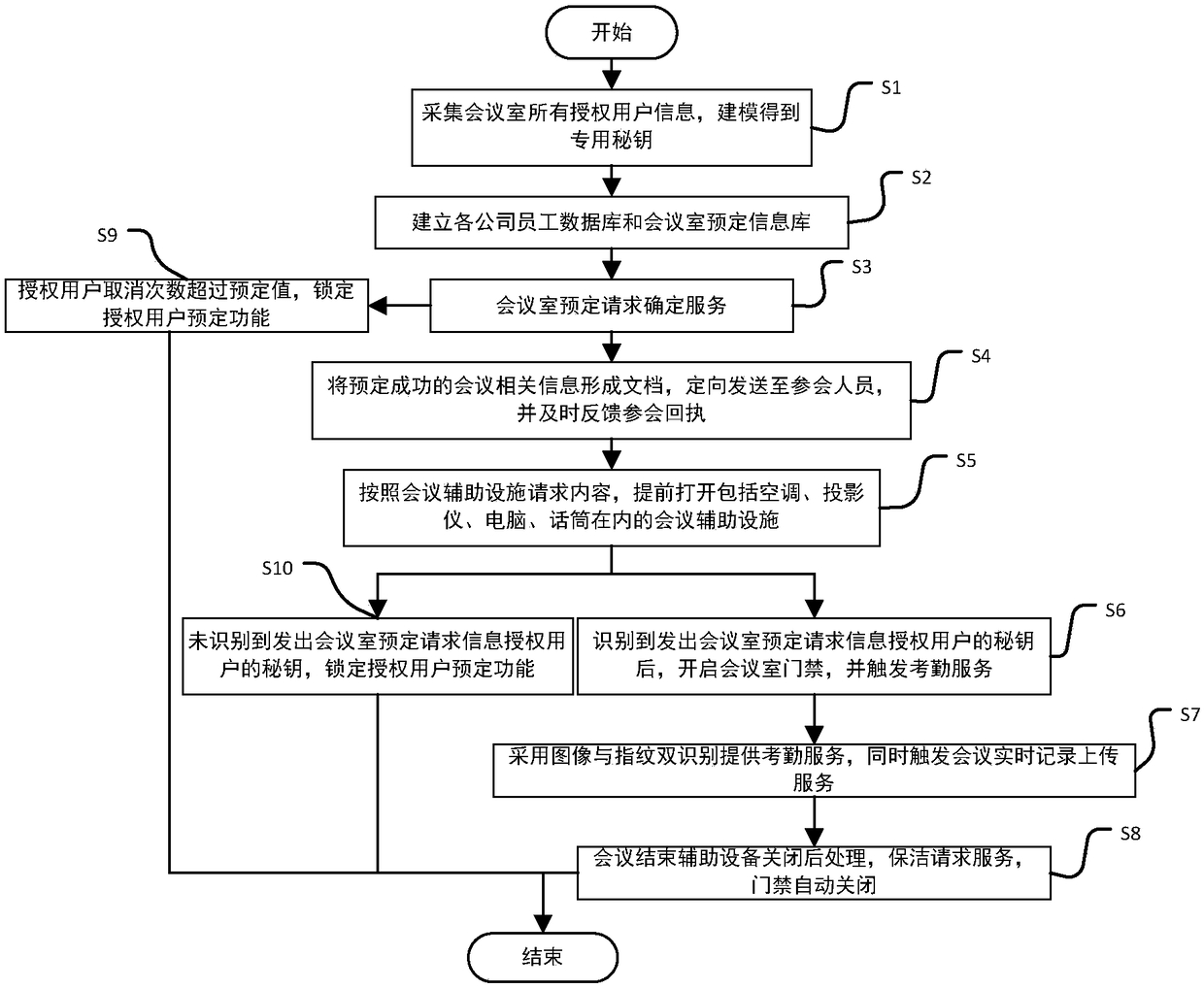
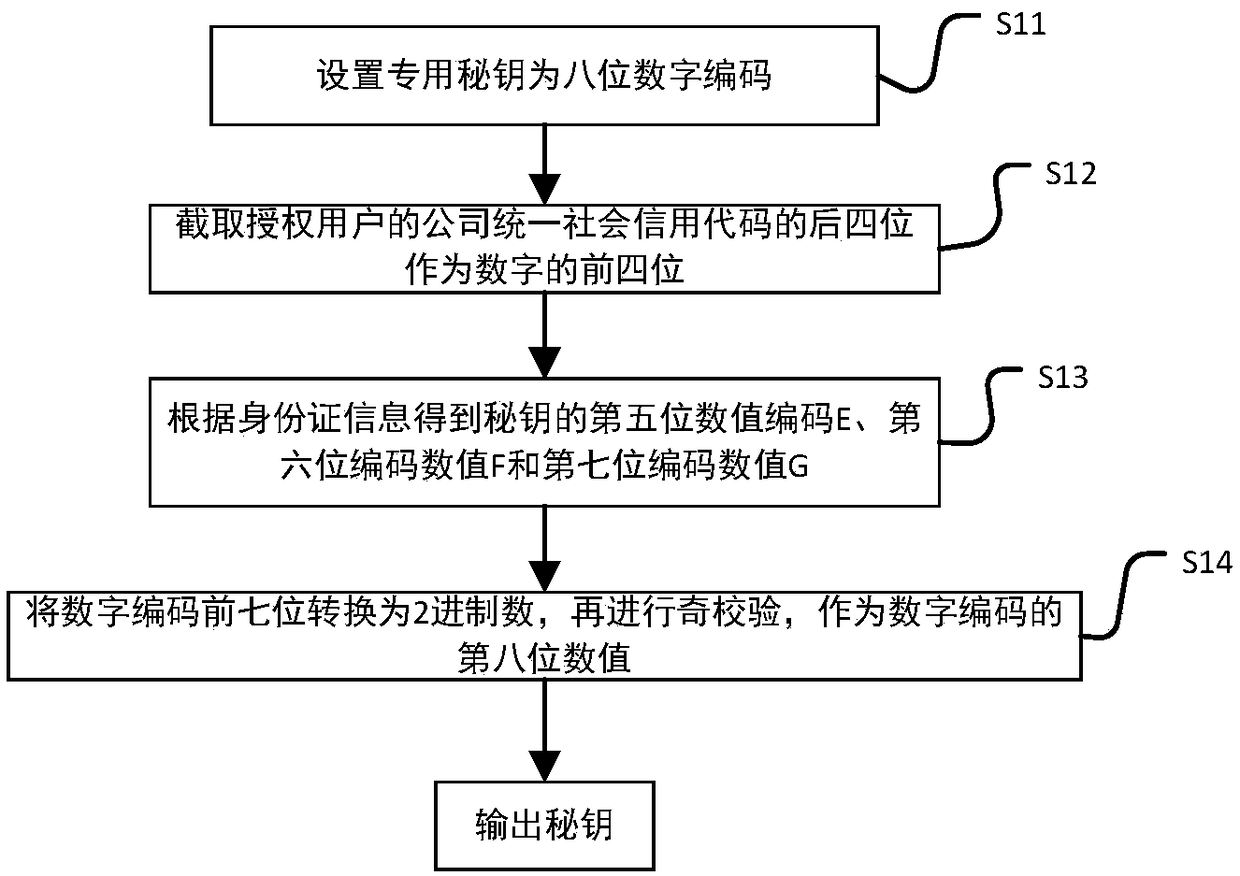
The invention discloses an intelligent conference control method and system. The method comprises acquisition of authorized user information, key generation, database establishment, conference room reservation request determination service, directional transmission of participant information, turn-on of conference auxiliary equipment, attendance service and conference end processing. The system comprises an authorized user data acquisition module, a key generation module, an employee data acquisition module, a conference room information acquisition module, a storage module, a conference roomreservation request determination service module, a conference determination information generation and transmission module, a conference room internal control module, a conference room access identification module, an attendance service module and a communication module. The method and the system can arrange conference proceedings accurately and efficiently, maximize the use of a conference room,reduce the labor intensity of manual registration schedules, conveniently and quickly handle the reservation and proceeding of various conferences, achieve automation and intelligence, realize the goal of unmanned management of the conference room, and have high practical value.
Owner:HEFEI ANLI ELECTRIC POWER ENG CO LTD
Authentication method and device
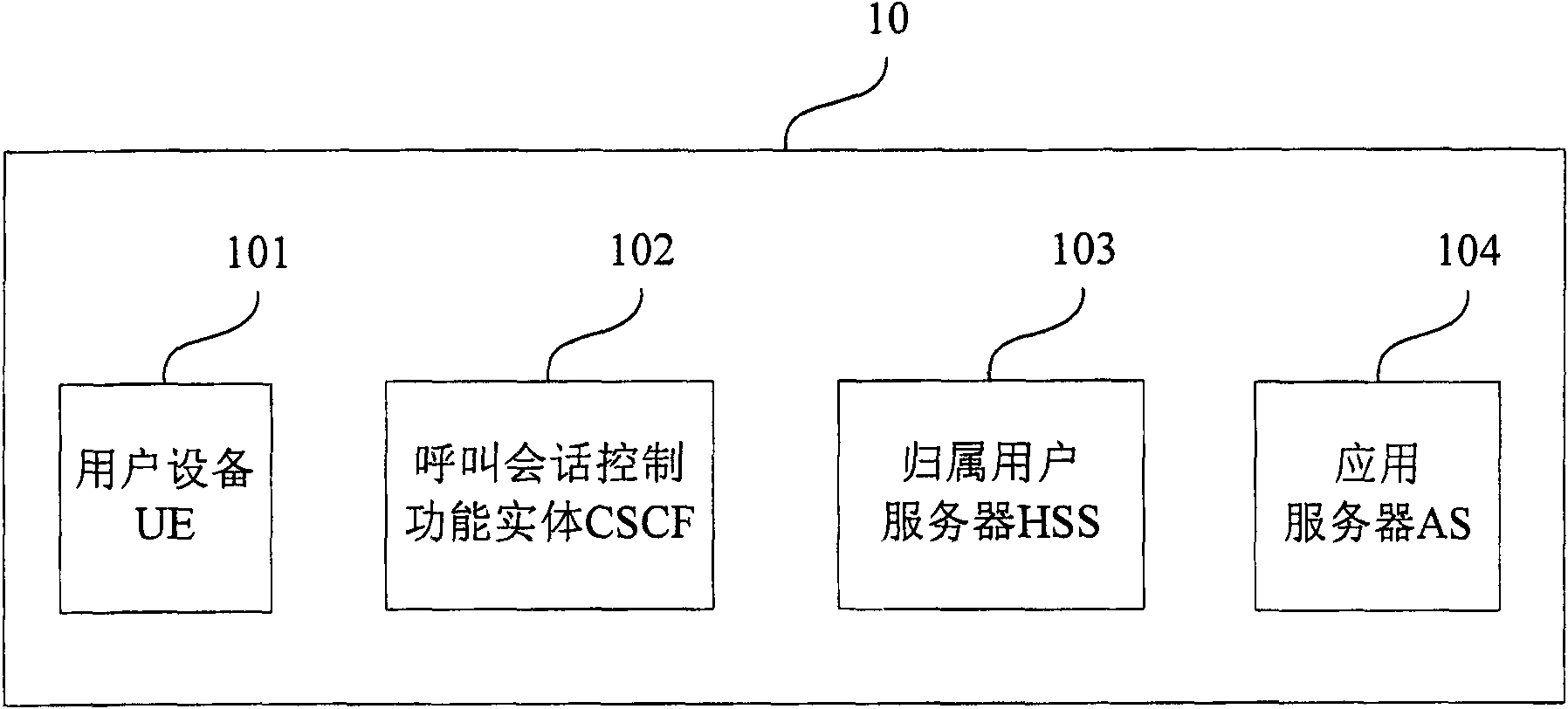
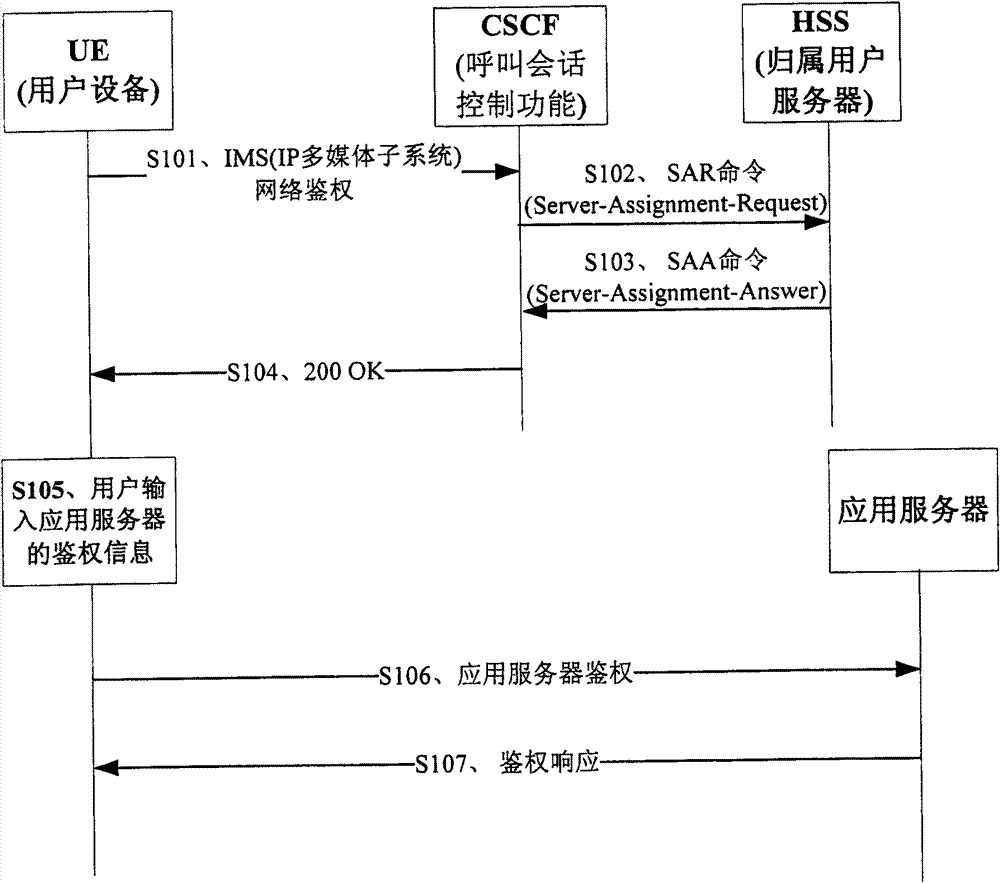
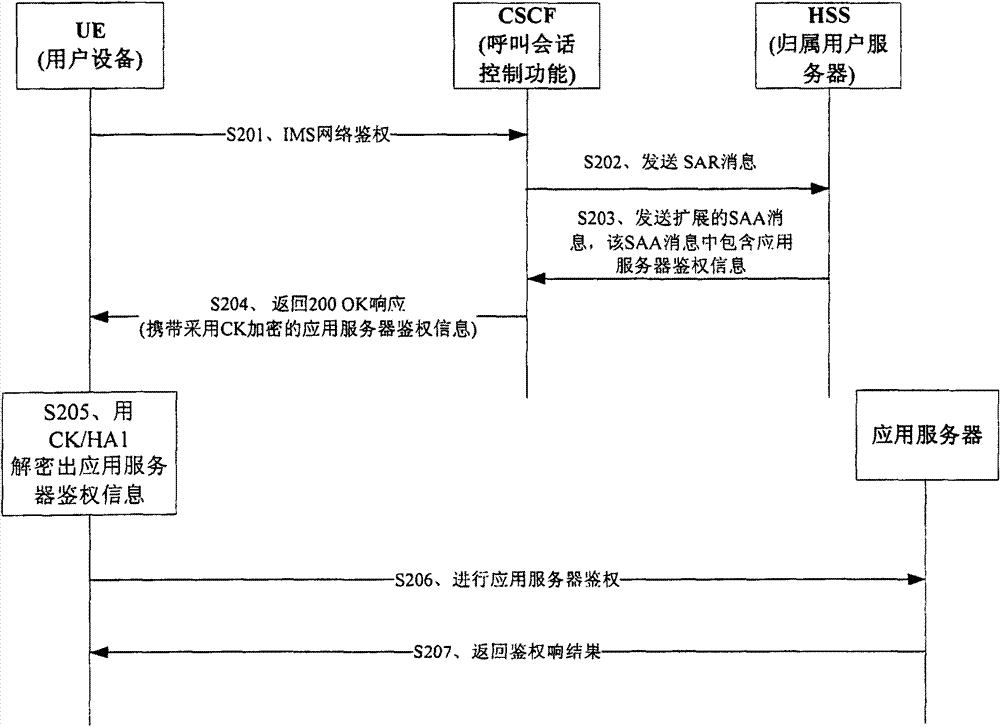
ActiveCN101668016AUser-friendly and operator-friendly managementEasy to implementTransmissionSecurity arrangementHome subscriber serverApplication server
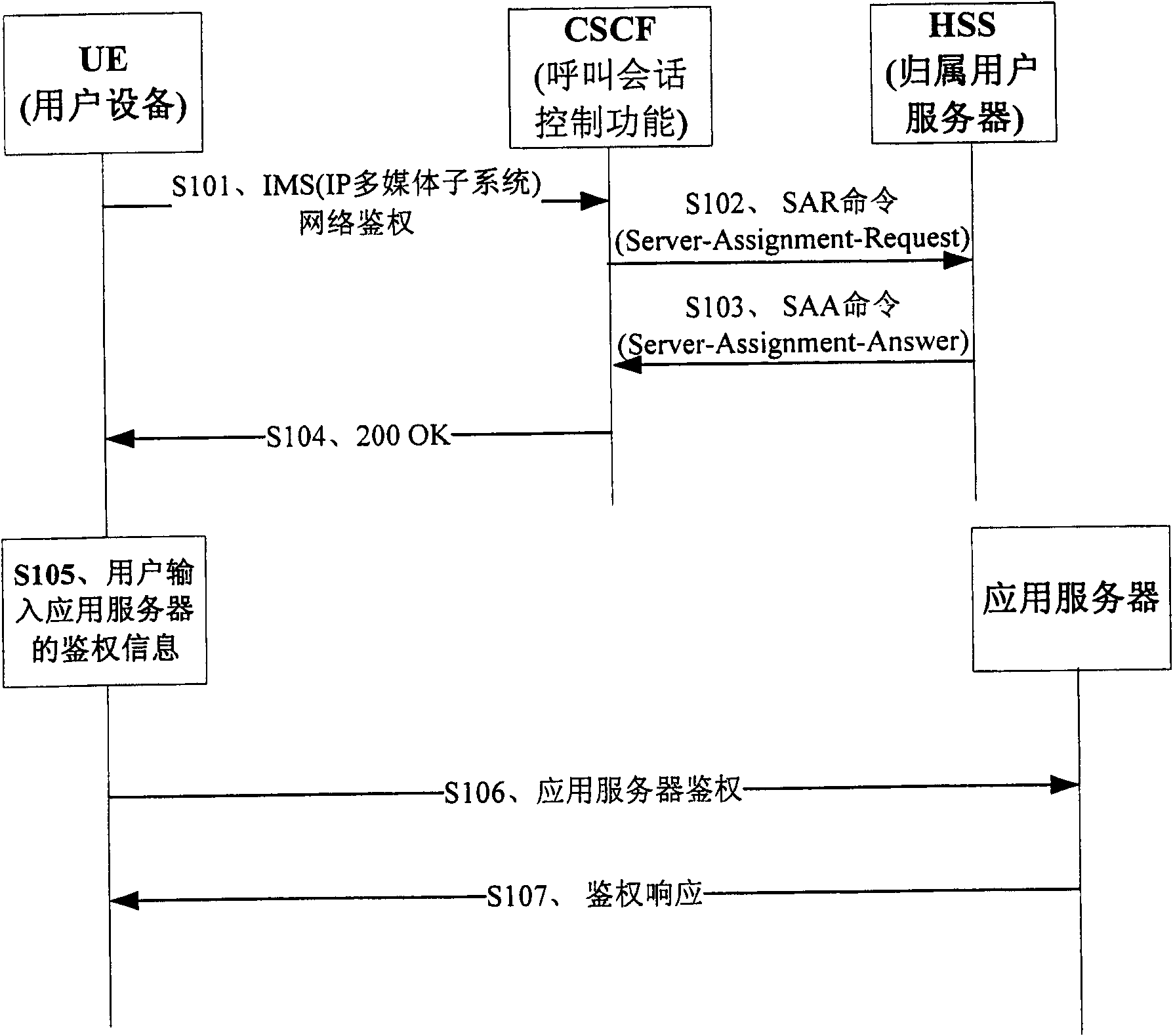
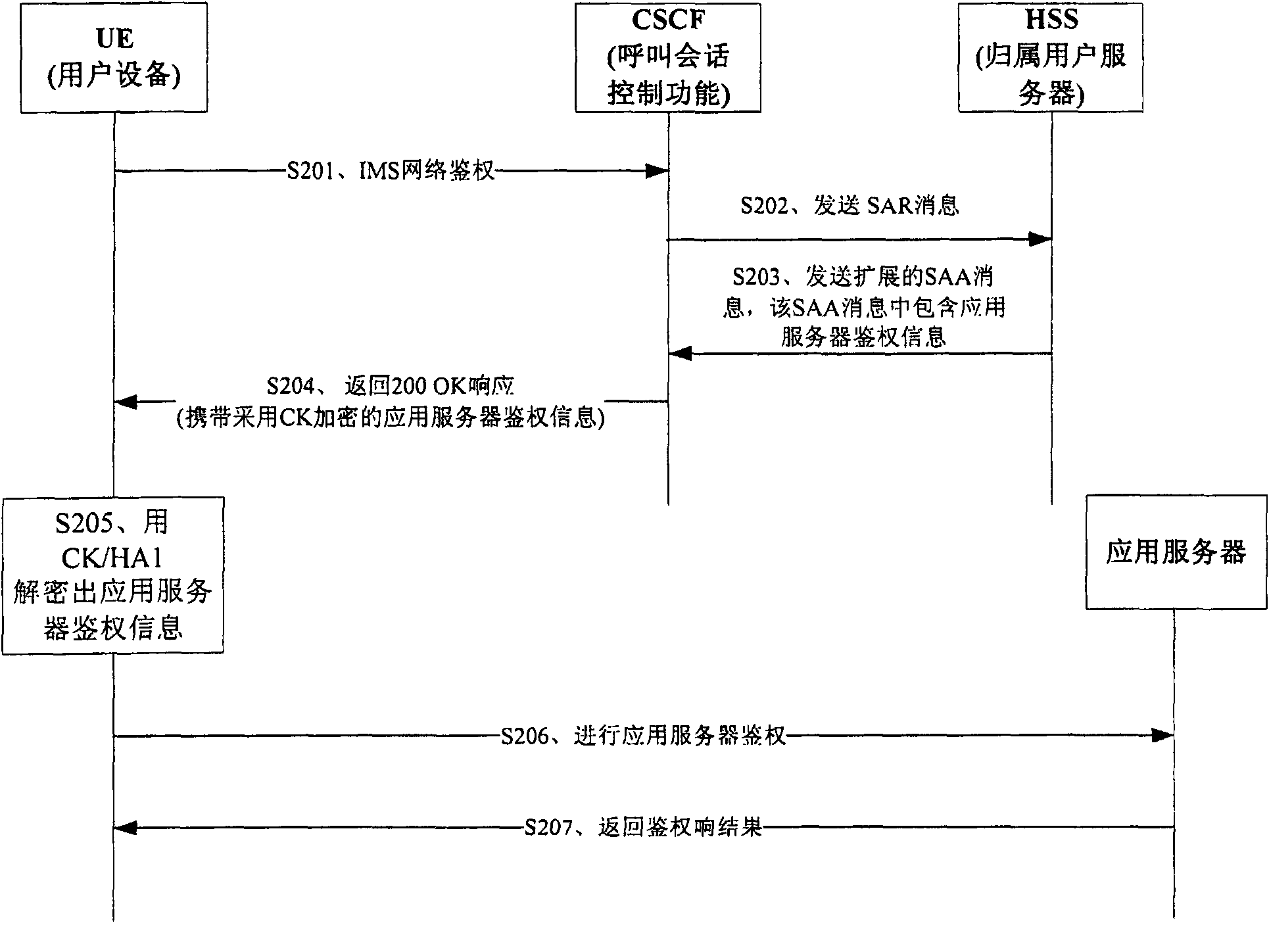
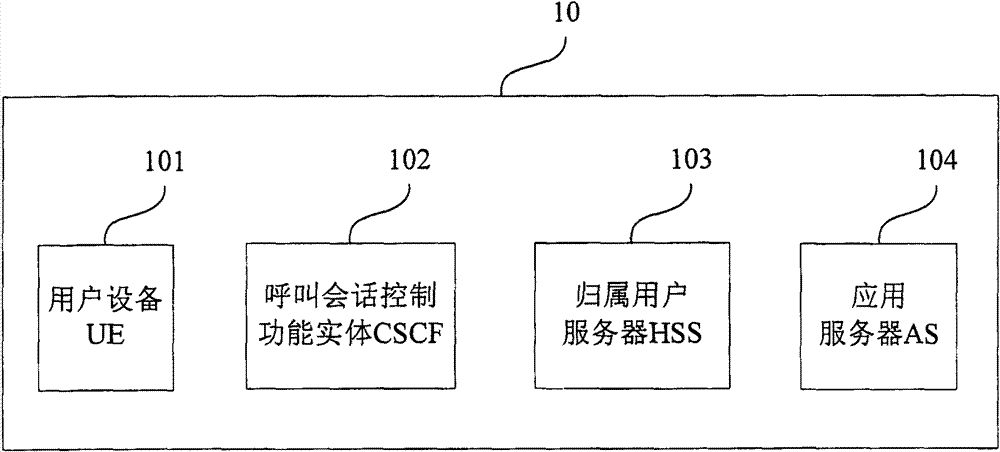
The embodiment of the invention provides an authentication method and a device; the device comprises the following steps: a network authentication request of an IP multimedia subsystem IMS, which is sent by user equipment, is received; according to the IMS network authentication request, authentication information of an application server is obtained from a home subscriber server HSS; an IMS network authentication respond message containing the authentication information of the application server is transmitted to the UE, so as to trigger the UE to utilize the authentication information of theapplication server to carry out authentication in the application server. In the method of the embodiment of the invention, uniform authentication of IMS and the application server is realized by carrying the authentication information of the application server in the returned result of the IMS network authentication without mutually intervening the authentication process of the application server by the user. The method brings great convenience to the usage of the user and the management of operators; in addition, the existing IMS authentication flow is fully utilized to realize simpleness.
Owner:HUAWEI TECH CO LTD
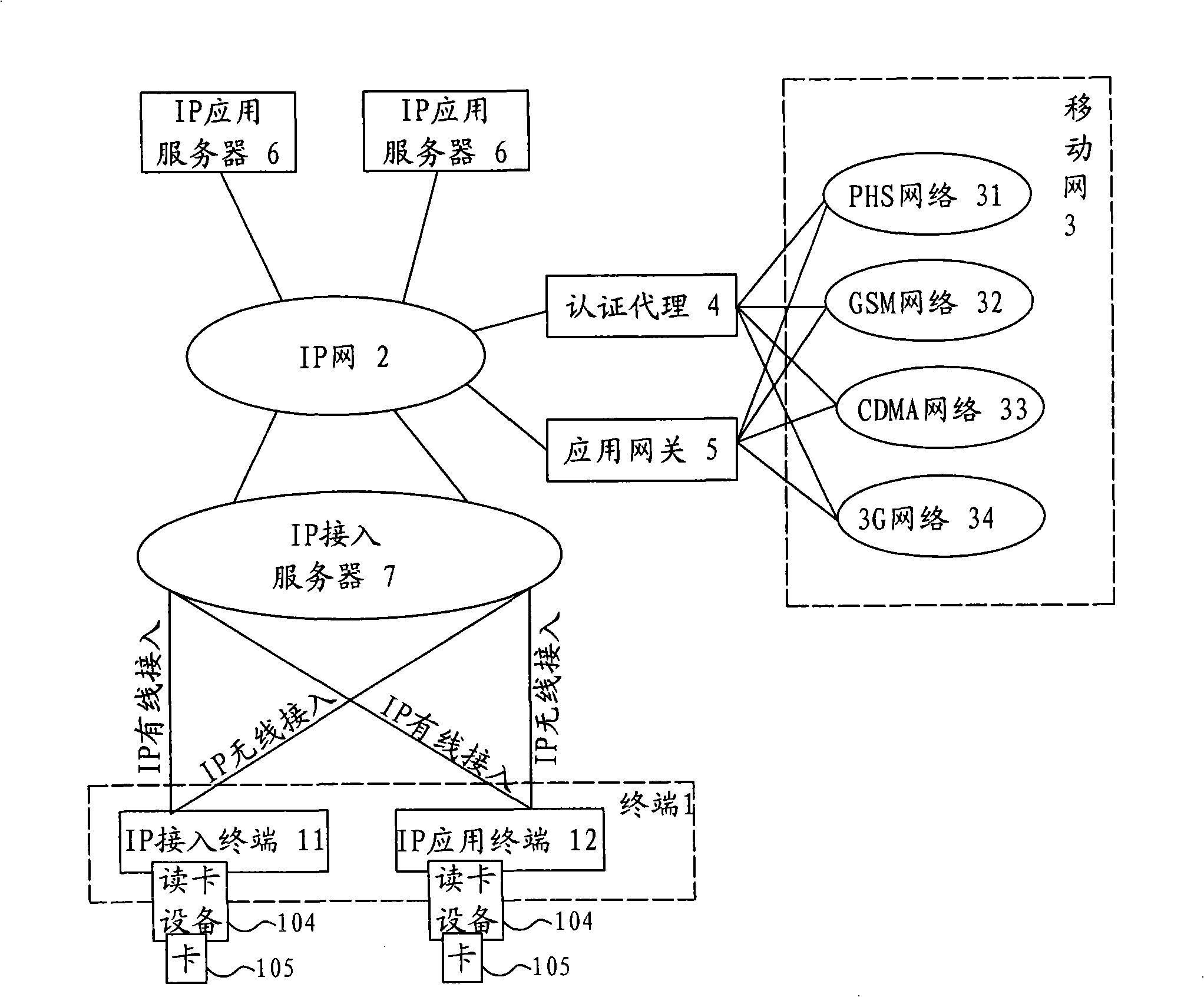
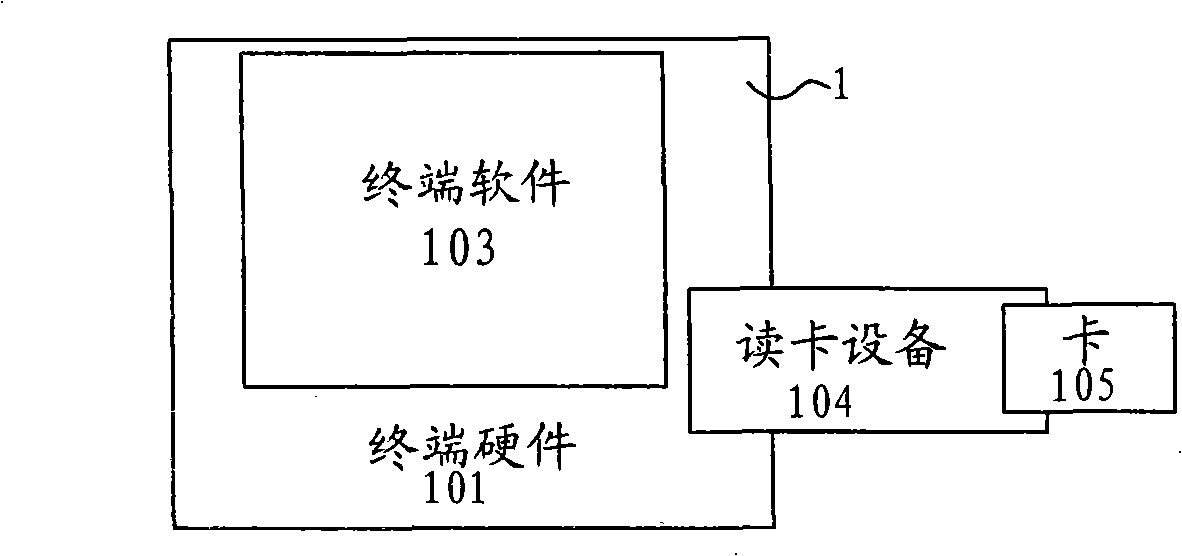
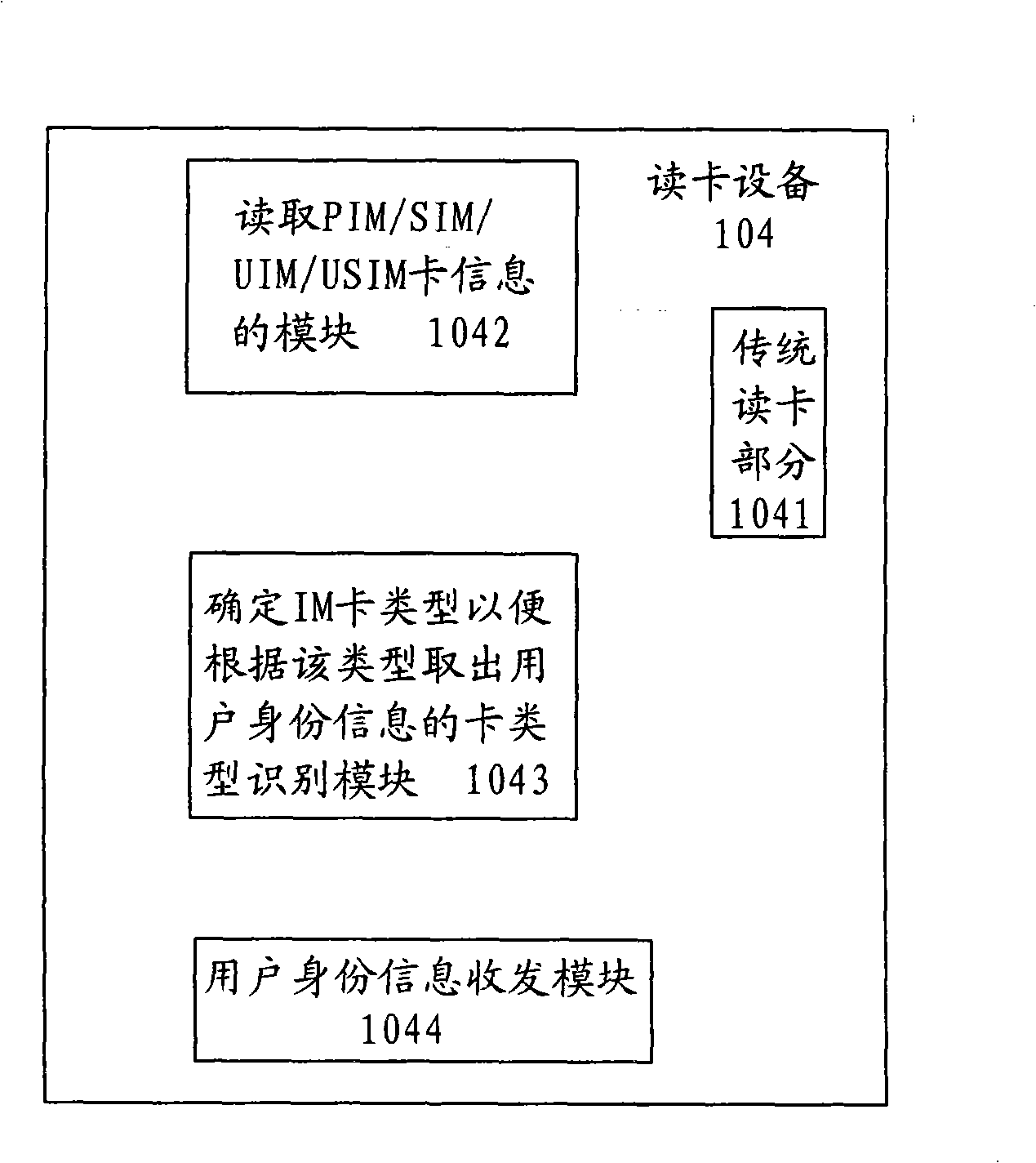
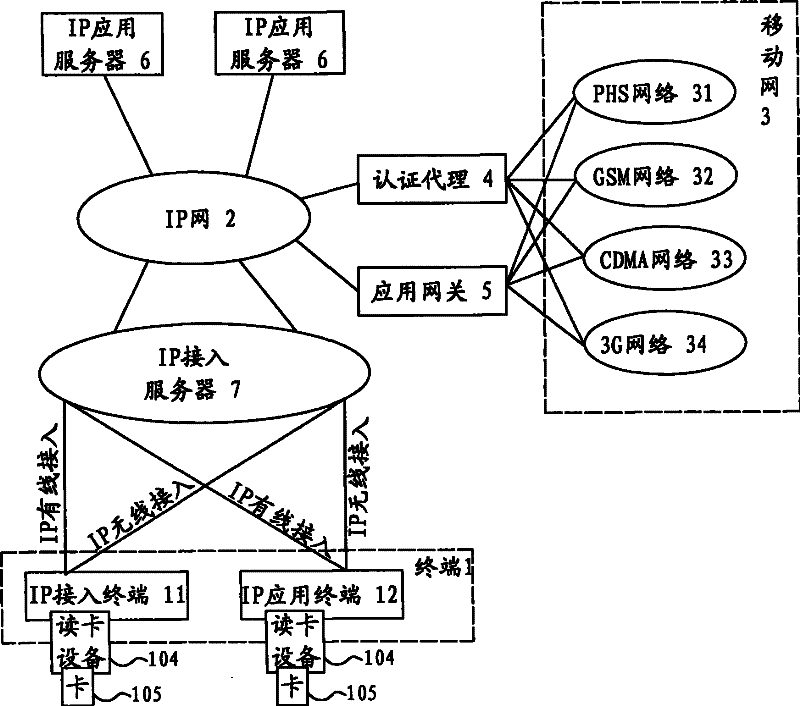
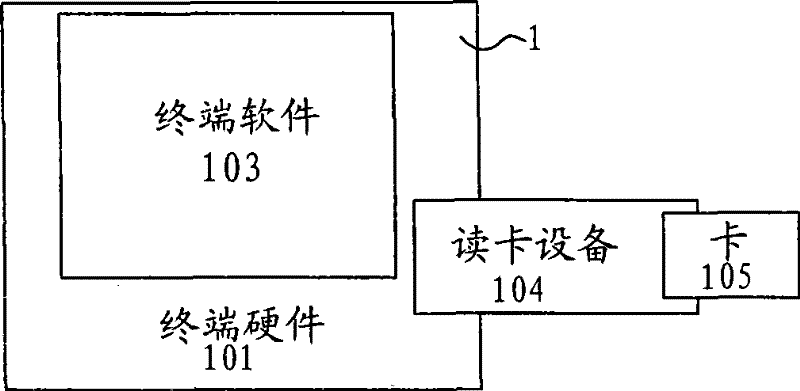
System, application and method for IP network access authentication based on personal identification module IM
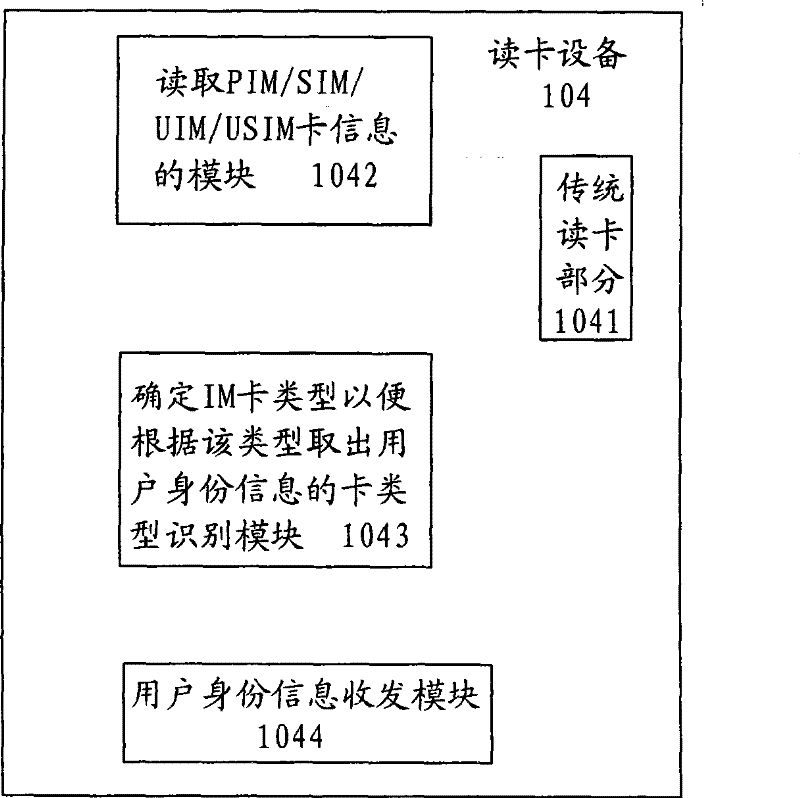
ActiveCN101282259AImprove securityImprove controllabilityUser identity/authority verificationData switching by path configurationAuthentication systemCard reader
An IP access authentication system based on an identity identification module IM is disclosed, comprising an IP network coupled to each IP terminal, a mobile network and an application gateway, the system also comprises an authentication proxy between the IP network and the mobile network, the authentication proxy can launch an authentication request to the corresponding mobile network for user identity information; a card reader is arranged at the IP terminal and able to read the user identity information in the IM card; the information is sent to the authentication proxy via the IP network. The invention also provides an application and a method thereof. The invention improves security of the authentication for user identity, expands usage range of smart cards like PIM, SIM, UIM and USIM, and achieves united authentication for users.
Owner:CHINA TELECOM CORP LTD
Uniform authentication system and method of multiple WiFi networks based on cloud platform
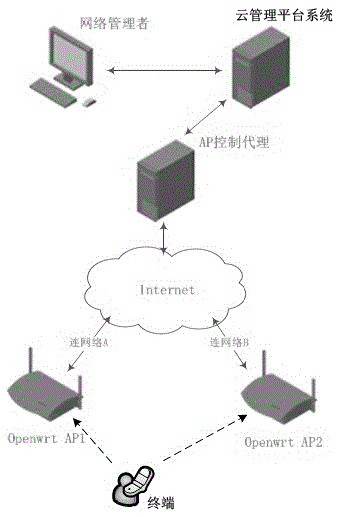
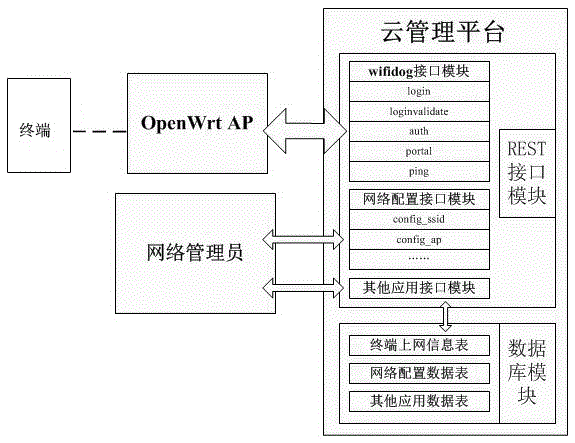
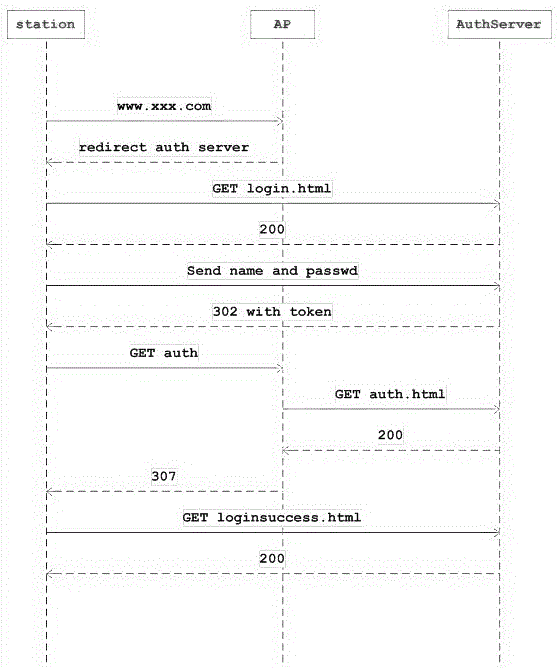
InactiveCN105554758AImprove management efficiencyRealize unified authenticationAssess restrictionNetwork topologiesWifi networkNetwork management
The invention discloses a uniform authentication system of multiple WiFi networks based on a cloud platform, comprising a cloud management platform system for recording the network information of a terminal and judges whether authentication is successful according to the network information; and an interface module for providing the authentication of the terminal and management operation of a network manager. The management operation of the network manager at least comprises: building an SSID, configuring valid authentication time, configuring an AP and dynamically binding the AP and the SSID; the AP is connected to the cloud management platform system through a network and is used for providing an open wireless network; an AP control agent is connected between the cloud management platform system and the AP and is used for forwarding the configuration of the cloud management platform system to the AP. According to the system and the method of the invention, multiple networks can be uniformly authenticated; once the authentication is passed in certain network, the authentication can be passed in all networks configured with the same SSIDs; the authentication efficiency is improved; a great deal of construction cost can be saved; the history information is recorded; therefore maintenance is convenient.
Owner:苏州云融信息技术有限公司 +1
Method for performing cross-platform unified management on users of cluster storage system
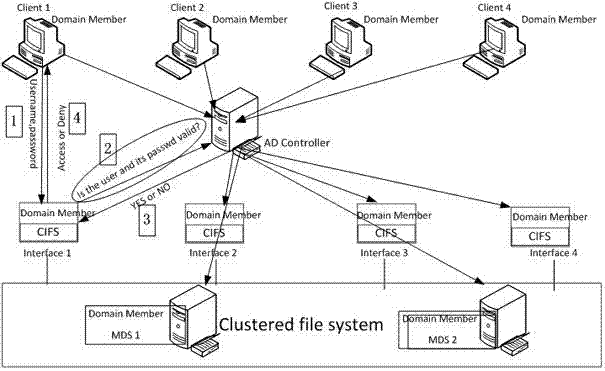
InactiveCN104754047ARealize unified managementSimplify the troubleshooting processTransmissionDomain controllerCluster systems
The invention specially relates to a method for performing cross-platform unified management on users of a cluster storage system. The method for performing the cross-platform unified management on the users of the cluster storage system includes: uniformly storing all the cluster storage users on an external AD (active directory) domain controller, and simultaneously using SAMBA software to add cluster storage nodes in a Windows AD domain, wherein a storage node SAMBA server is used as a member of the Windows AD domain, and an AD domain controller node provides SAMBA user unified management services to the cluster storage system. According to the method for performing the cross-platform unified management on the users of the cluster storage system, all user management operations are completed through the AD domain controller, unified authentication of the cross-platform users, Windows users and Linux users is achieved, and simultaneously user information is stored on an AD domain service node except the nodes of the cluster storage system, influences of breakdowns of the cluster storage nodes on user access are further avoided, and furthermore not only is the unified management of the cross-platform users achieved, but also an elimination process of system breakdowns is greatly simplified.
Owner:INSPUR GROUP CO LTD
Intelligent construction processing method and system for live conference
InactiveCN108875990AAccurate and efficient arrangementMaximize utilizationReservationsIndividual entry/exit registersKey generationService module
The present invention discloses an intelligent construction processing method and system for live conference, which comprises the steps of: Collecting information of authorized users, generating a secret key, building a database, determining reservation request of meeting room, directly sending meeting information, turning on conference equipment, serving of check on work attendance and end process of the conference. The system comprises an authorized users data collection module, a secret key generation module, an employee data collection module, a conference room information collection module, a storage module, a reservation request of meeting room determining module, a conference determination information generation transmission module, a conference room internal control module, a conference room entrance guard identity module, an check on work attendance service module and a communication module. The intelligent construction processing method and system for live conference can schedule meeting matters accurately and efficiently, maximize the use of conference rooms, reduce labor intensity of manual table registration, conveniently and rapidly processed reservation and progressof various conferences, achieves automation, intelligence and realize objective of unmanned management of the conference room, has high practical value.
Owner:HEFEI DONGHENGRUI ELECTRONICS TECH CO LTD
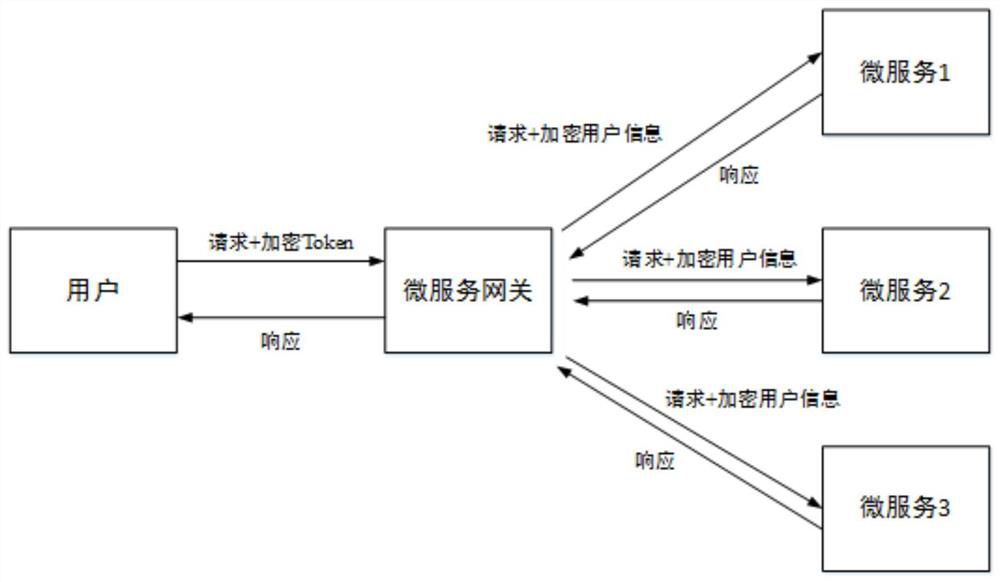
Stateless authentication method for micro-service system
InactiveCN111865984ARelieve pressureGuaranteed uptimeUser identity/authority verificationInternet privacyEngineering
The invention discloses a stateless authentication method for a micro-service system, and relates to the technical field of data authentication. The method comprises the steps of: obtaining a token authenticated by a user; sending the token to a micro-service gateway; enabling the micro-service gateway to perform unified authentication through the token and acquire user information; packaging userinformation through the micro-service gateway based on a JWT protocol, and generating and forwarding a stateless JWT token to a target micro-service; and checking and analyzing the JWT token based onthe JWT protocol for the target micro-service to obtain user information, and after performing service logic processing, feeding back a result to the user to complete stateless authentication.
Owner:SHANDONG LANGCHAO YUNTOU INFORMATION TECH CO LTD
Authentication method, device and system
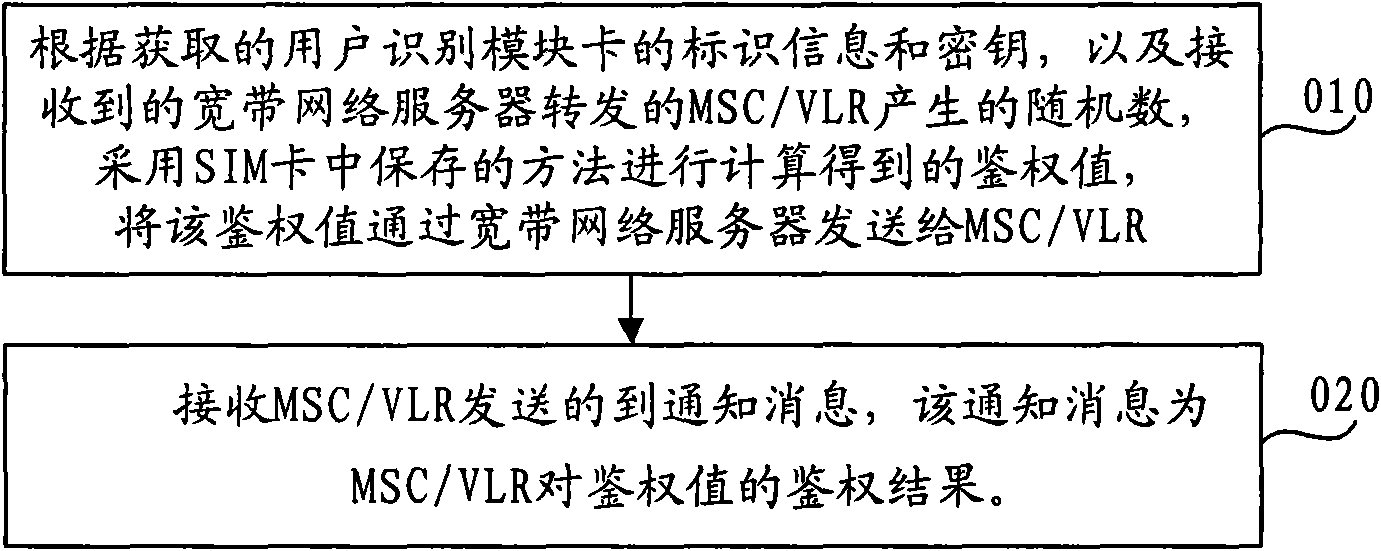
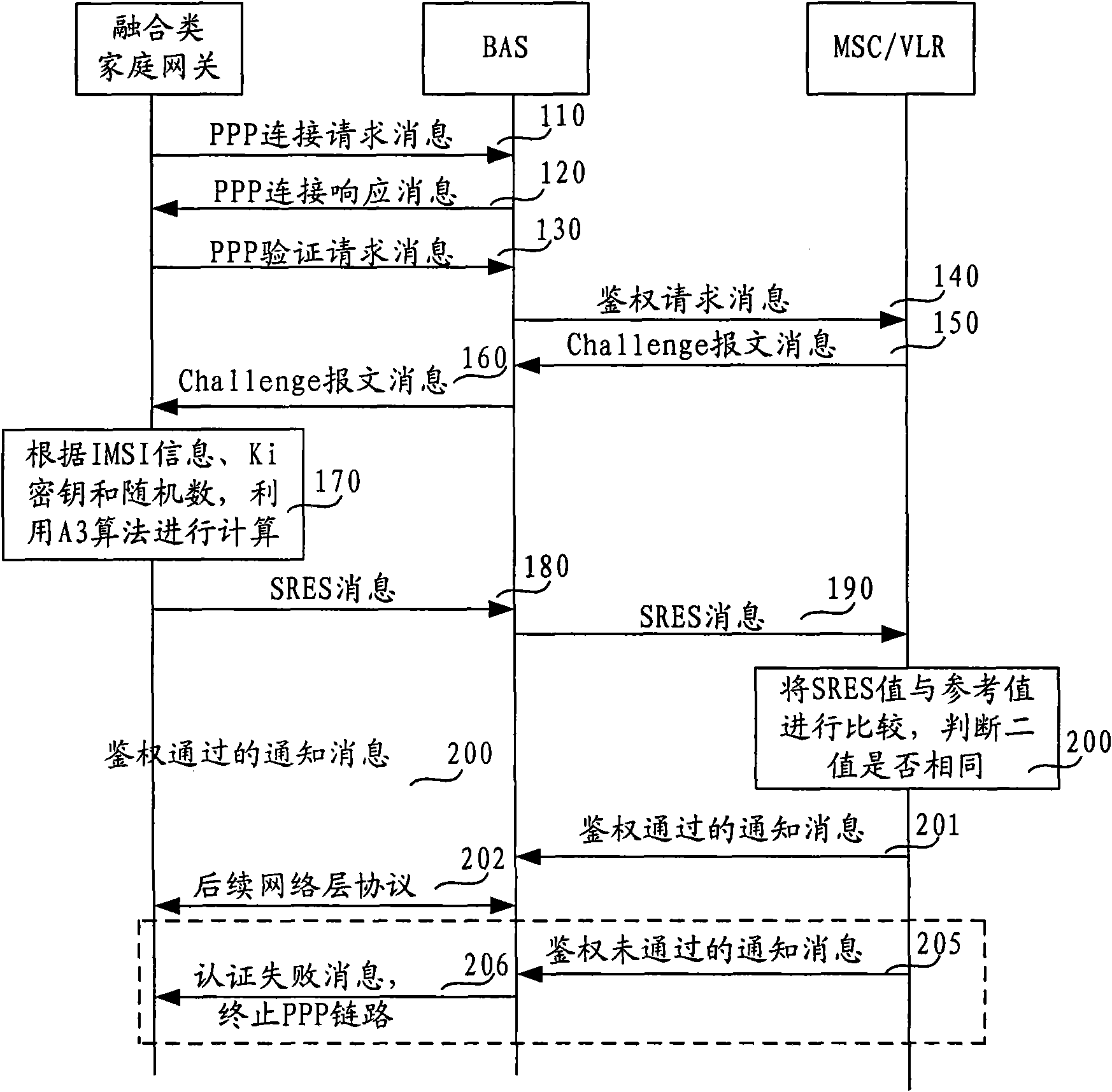
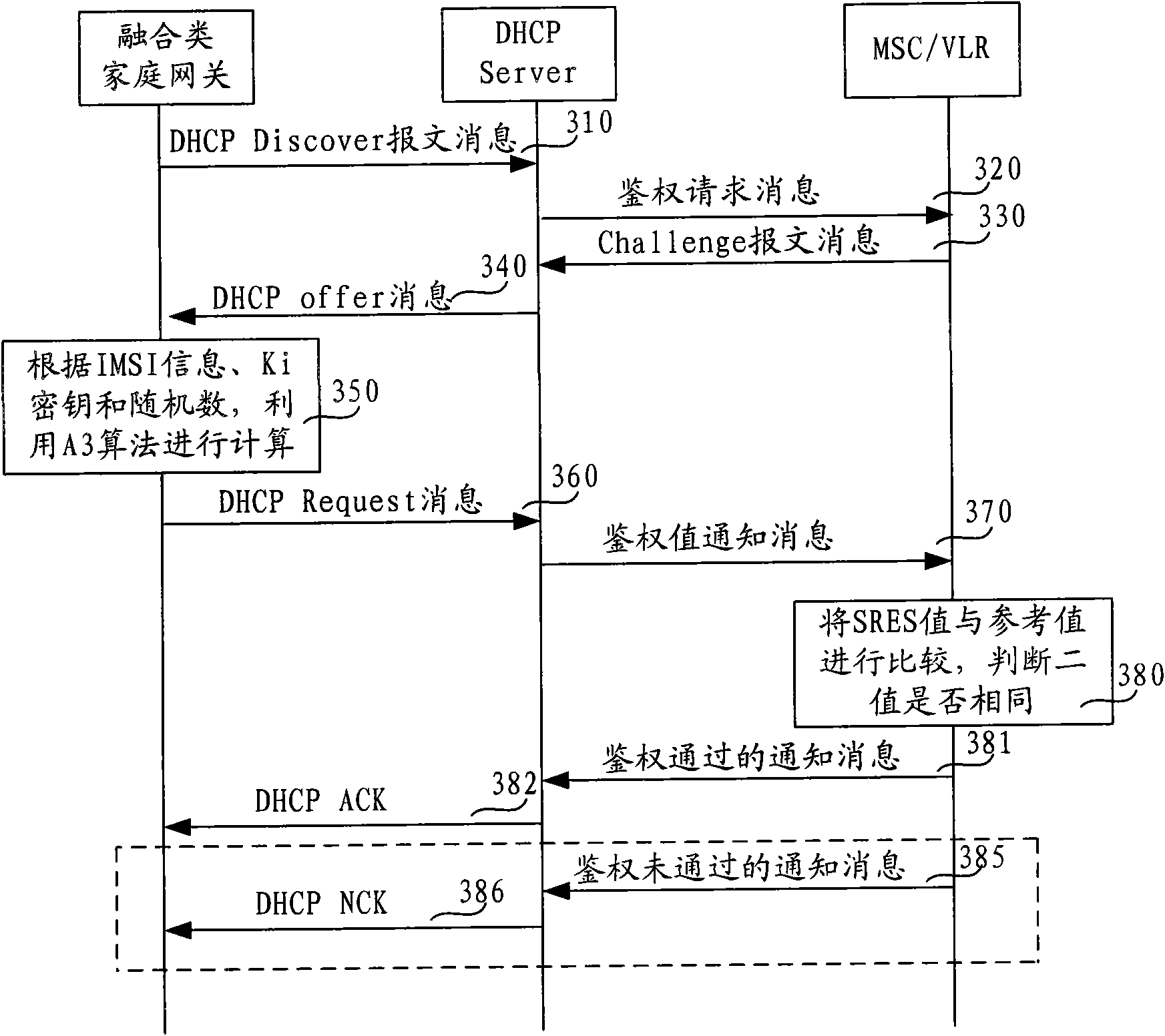
InactiveCN101645774ARealize unified authenticationUser identity/authority verificationAuthentication systemBroadband networks
The embodiment of the invention discloses an authentication method, an authentication device and an authentication system. The method comprises the steps of: according to acquired identification information and a key of a user identification module card, and a received random number generated by a mobile switching centre / visited location register MSC / VLR and forwarded by a broadband network server, adopting a method saved in an SIM card to perform computation to obtain an authentication value, and transmitting the authentication value to the MSC / VLR through the broadband network server; and receiving a notification message, wherein the notification message is transmitted according to an authentication result obtained by comparing a reference value and the authentication value. The embodiment of the invention can realize uniform authentication and authorization on a home fusion gateway so as to effectively solve the problems such as charging, management and the like.
Owner:HUAWEI DEVICE (SHENZHEN) CO LTD
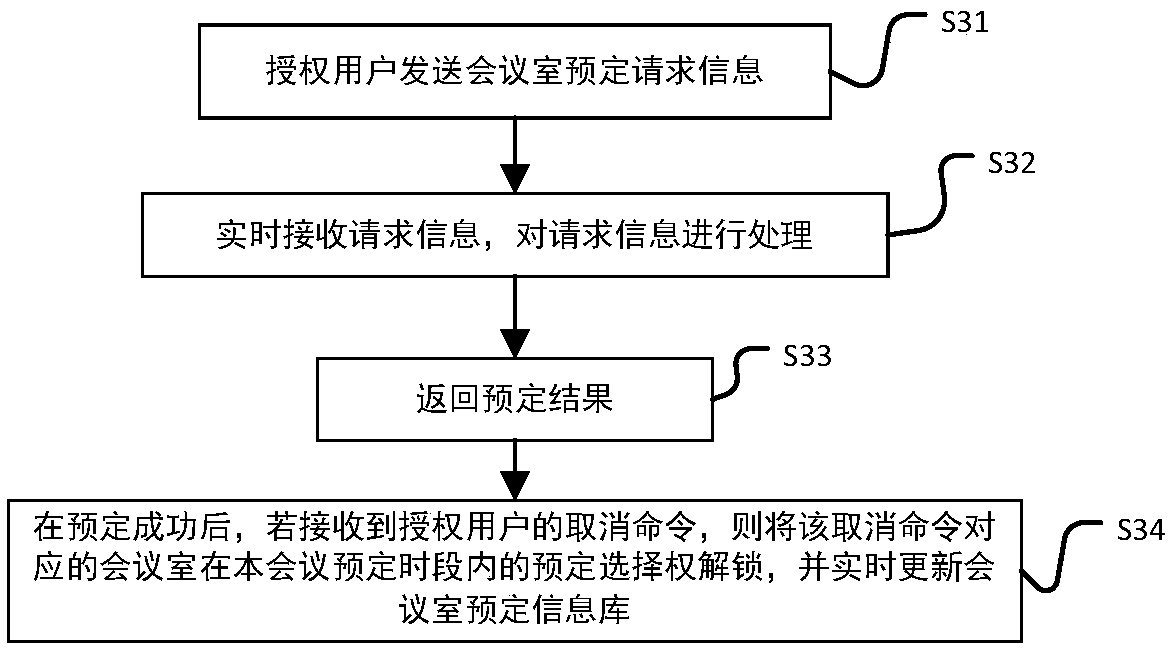
An efficient and safe conference room reservation management method and system
InactiveCN109034431AMaximize utilizationRealize unmanned managementKey distribution for secure communicationRegistering/indicating time of eventsInternal managementData acquisition
The invention discloses an efficient and safe conference room reservation management method and system. The method includes collecting authorized user information, secret key generation, database establishment, conference room reservation request confirmation service, meeting information directional transmission, meeting auxiliary equipment opening, attendance service and meeting end processing. The system includes an authorized user data acquisition module, a secret key generation module, an employee data acquisition module, a meeting room information acquisition module, a storage module, a meeting room reservation request determination service module, a meeting determination information generation transmission module, a meeting room internal management and control module, a meeting roomaccess control identification module, an attendance service module and a communication module. The invention can precisely and efficiently arrange meeting matters, maximizes the utilization of the conference room, reduces the labor intensity of manual registration and scheduling, conveniently and quickly processes the reservation and carrying out of various meetings, achieves automation and intelligence, realizes the goal of unmanned management of the conference room, and has high practical value.
Owner:HEFEI KANGZHIHENG MACHINERY TECH CO LTD
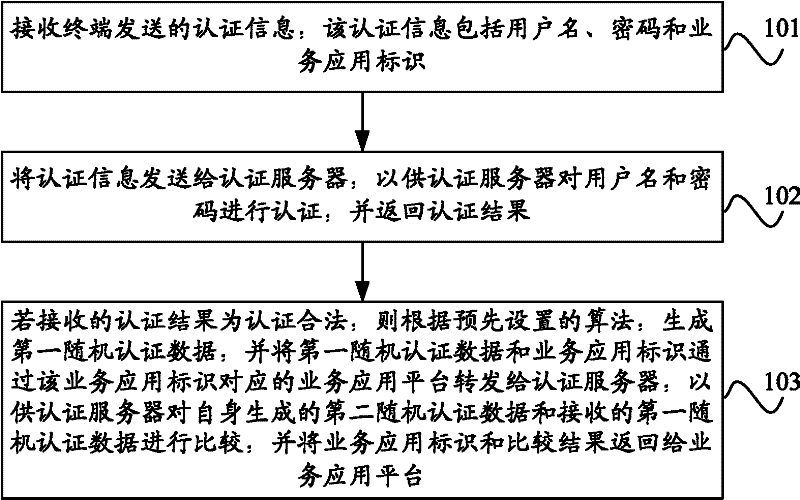
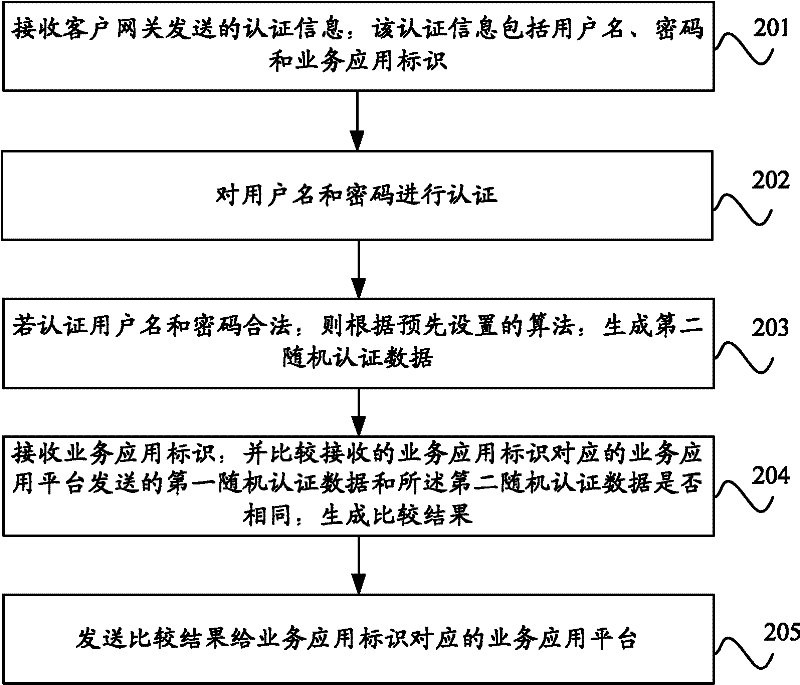
Authentication method, equipment and system
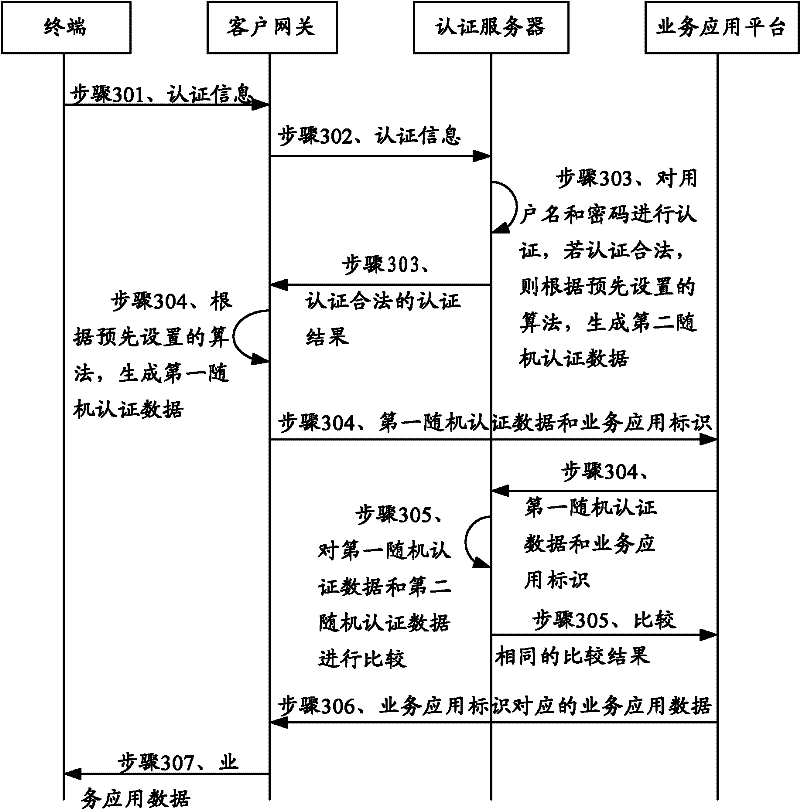
ActiveCN102546552AMeet high security requirementsRealize unified authenticationUser identity/authority verificationPasswordComputer terminal
The invention provides an authentication method, equipment and system. The method comprises the following steps of: receiving authentication information sent by a terminal, wherein the authentication information comprises a user name, a password and a business application identifier; sending the authentication information to an authentication server to carry out authentication on the user name and the password by the authentication server, and returning back the authentication result; if the received authentication result is legally authenticated, generating first random authentication data according to a pre-set algorithm; forwarding the first random authentication data and the business application identifier to the authentication server through a business application platform corresponding to the business application identifier, so as to compare second random authentication data generated by the authentication server with the received first random authentication data by the authentication server; and returning the business application identifier and the comparison result back to the business application platform. According to the authentication method, equipment and system provided by the invention, the uniform authentication is realized and the safety of the authentication is effectively improved.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Conference room reservation method and system
InactiveCN108921316AMaximize utilizationRealize the goal of unmanned managementRegistering/indicating time of eventsReservationsData acquisitionHuman–computer interaction
The invention discloses a conference room reservation method and system. The method comprises the following steps of: acquiring authorized user information; generating a secret key; establishing a database; determining a conference room reservation request; directionally sending conference attending information; starting conference auxiliary equipment; carrying out an attendance check service; andcarrying out conference ending processing. The system comprises an authorized user data acquisition module, a secret key generation module, a staff data acquisition module, a conference room information acquisition module, a storage module, a conference room reservation request determination service module, a conference determination information generation and transmission module, a conference room interior control module, a conference room entrance guard recognition module, an attendance checking service module and a communication module. The method and system are capable of accurately and efficiently arranging conference proceedings so as to maximally utilize conference rooms and decrease the labor intensity of manual login and table arrangement, and conveniently and rapidly processingreservation and proceeding of various conferences so as to achieve automation and intelligence and realize the aim of unmanned conference room management, and has a relatively high practical value.
Owner:HEFEI XINYADA INTELLIGENT TECH CO LTD
Conference rapid establishing and efficient implementation method and system
InactiveCN108960781AConvenient and fast bookingThe process is convenient and fastOffice automationKey generationAuthorization
The present invention discloses a conference rapid establishing and efficient implementation method and system. The method comprises the steps of: collection of authorization user information, generation of secret keys, establishing of a database, conference room reservation request determination service, conference attending orienteering sending, conference auxiliary device turning-on, attendanceservice and conference ending processing. The system comprises an authorization user data collection module, a secret key generation module, a staff data collection module, a conference room information collection module, a storage module, a conference room reservation request determination service module, a conference determination information generation and transmission module, a conference room internal control module, a conference room gate control identification module, an attendance service module and a communication module. The conference rapid establishing and efficient implementationmethod and system can accurately and effectively arrange an agenda, can maximally utilize the conference room, can reduce the labour intensity of manual registration and list arrangement, can conveniently and rapidly handle with reservation and proceeding of various conferences, is automatic and intelligent, can achieve the target of unmanned management of the conference, and has a high practicalvalue.
Owner:HEFEI SIBOT SOFTWARE DEV CO LTD
Cross-system trust management system suitable for electric power internet of things
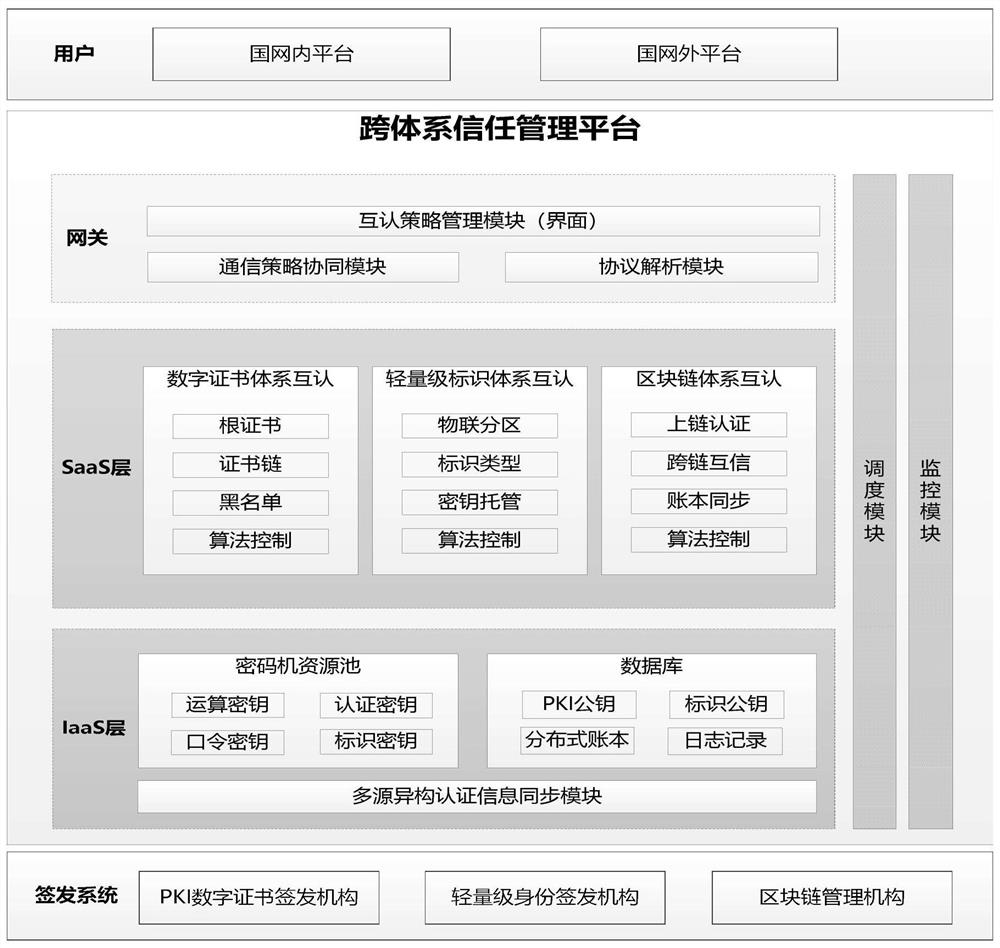
ActiveCN112217793ABreak through technical barriersRealize unified authenticationResourcesTransmissionAuthentication systemDatabase query
The invention discloses a cross-system trust management system suitable for the power Internet of Things, and the system comprises a gateway which is used for determining an authentication system to which the identity authentication of a user belongs according to an identity authentication request of the user; a service module which is used for determining a corresponding authentication processingunit according to the authentication system to which the identity authentication of the user belongs, calling the infrastructure module to authenticate the identity of the user by utilizing the determined authentication processing unit, determining an identity authentication result, and feeding back the identity authentication result to the user side; an infrastructure module which is used for supporting a cryptographic operation function and a database query function involved in the service module, and synchronously signing and issuing authentication data of the signing and issuing system inreal time; a monitoring module which is used for monitoring the running state of the system, acquiring resource bearing information and sending the resource bearing information to the scheduling module; and a scheduling module which is used for carrying out unified allocation and control on the service module and the infrastructure module according to the resource bearing information.
Owner:CHINA ELECTRIC POWER RES INST
A method and system for unmanned service in a conference room
InactiveCN109087059AMaximize utilizationRealize the goal of unmanned managementOffice automationKey generationData acquisition module
The invention discloses a method and a system for unmanned service in a conference room. The method comprises the following steps: collecting authorized user information, generating secret keys, establishing a database, confirming service of a reservation request of the conference room, directional transmission of attendance information, opening auxiliary equipment of the conference, attendance service and end-of-meeting processing. The system includes an authorized user data acquisition module, a secret key generation module, an employee data acquisition module, a meeting room information acquisition module, a storage module, a meeting room reservation request determination service module, a meeting determination information generation transmission module, a meeting room internal management and control module, a meeting room access control identification module, an attendance service module and a communication module. The invention can precisely and efficiently arrange meeting matters, maximizes the utilization of the conference room, reduces the labor intensity of manual registration and scheduling, conveniently and quickly processes the reservation and carrying out of various meetings, achieves automation and intelligence, realizes the goal of unmanned management of the conference room, and has high practical value.
Owner:HEBEI JIASHICHENG ENERGY TECH CO LTD
Unified authentication system and method for realizing authentication of multiple WIFI networks
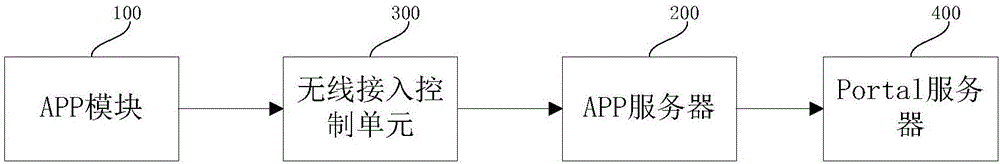
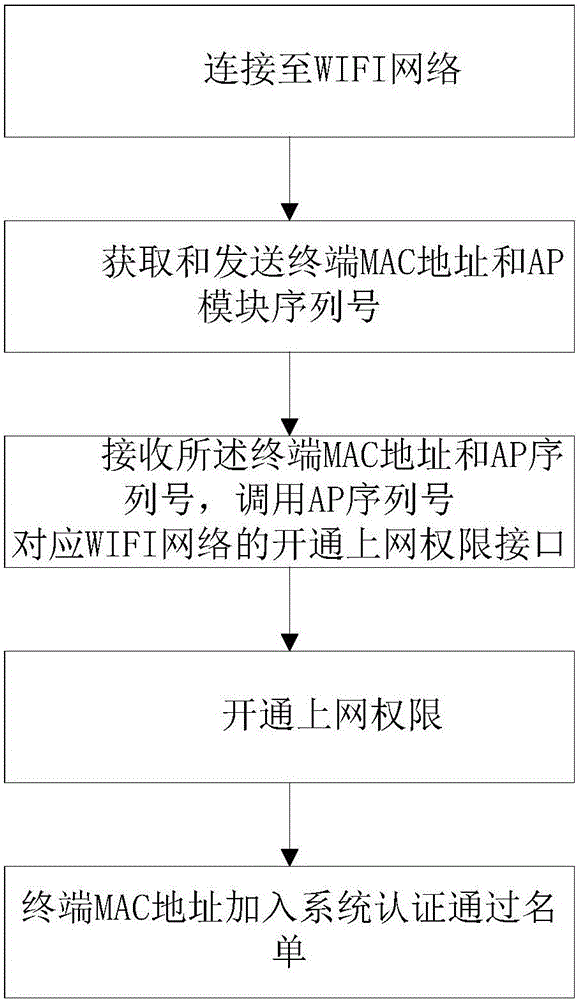
InactiveCN106851641ARealize unified authenticationAdd authentication functionNetwork topologiesTransmissionWifi networkInternet access
The invention provides a unified authentication system and method for realizing authentication of multiple WIFI networks. The system comprises an APP module and an APP server, wherein the APP module contains an AP serial number acquisition device for acquiring and sending a terminal MAC address and an APP serial number; the APP server is used for storing the AP serial number stored in each WIFI network, querying the WIFI network corresponding to the AP serial number, and calling an internet access privilege opening interface. The AP serial number acquisition device reads and searches the authentication page information in a text way to find the needed key field, and then acquires the AP serial number. The invention further provides an APP unified authentication method and system butted with multiple existing commercial WIFI networks, thereby fast increasing the APP authentication function, and performing the authentication in multiple independent WIFI system in the unified way.
Owner:PHICOMM (SHANGHAI) CO LTD
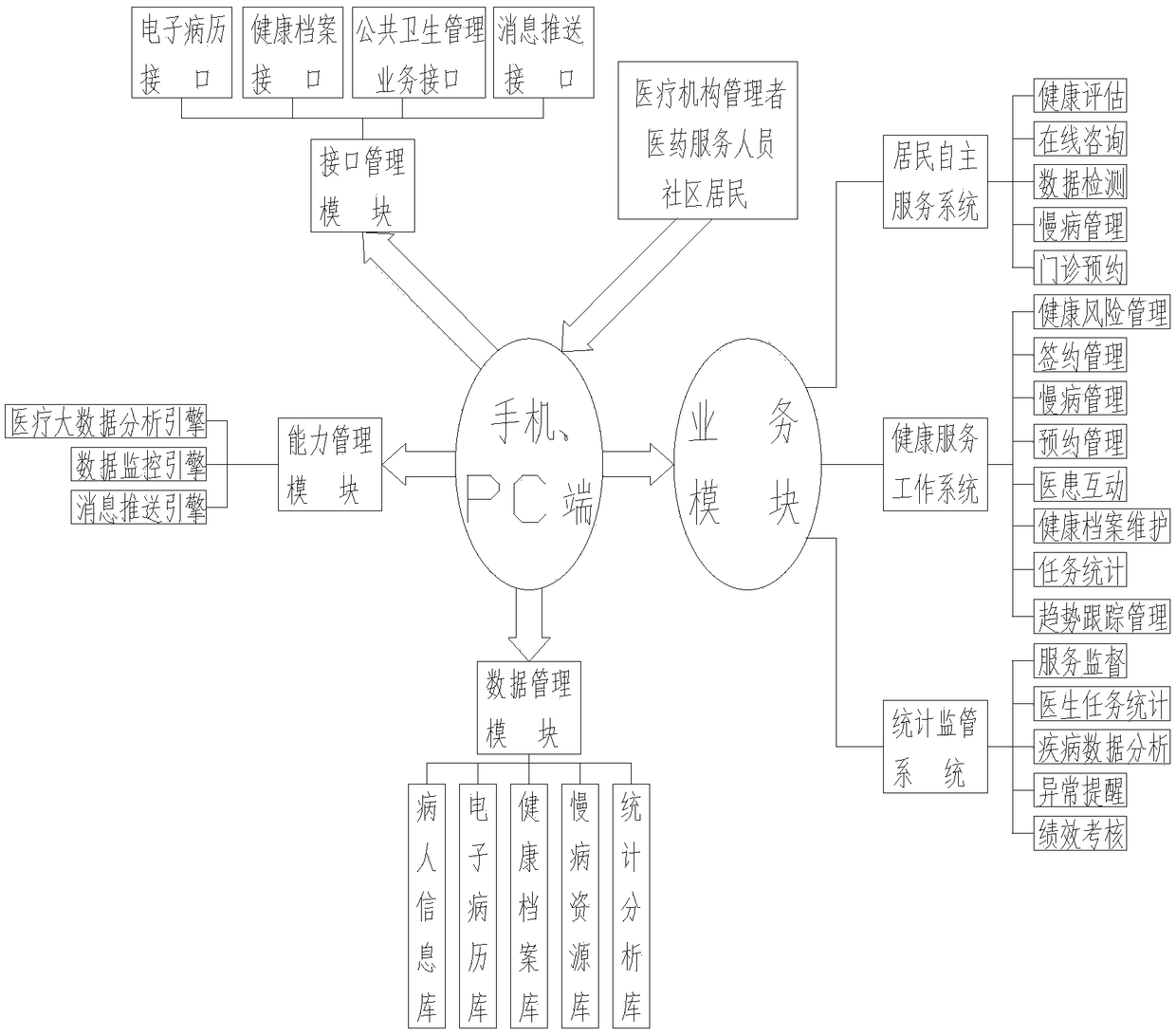
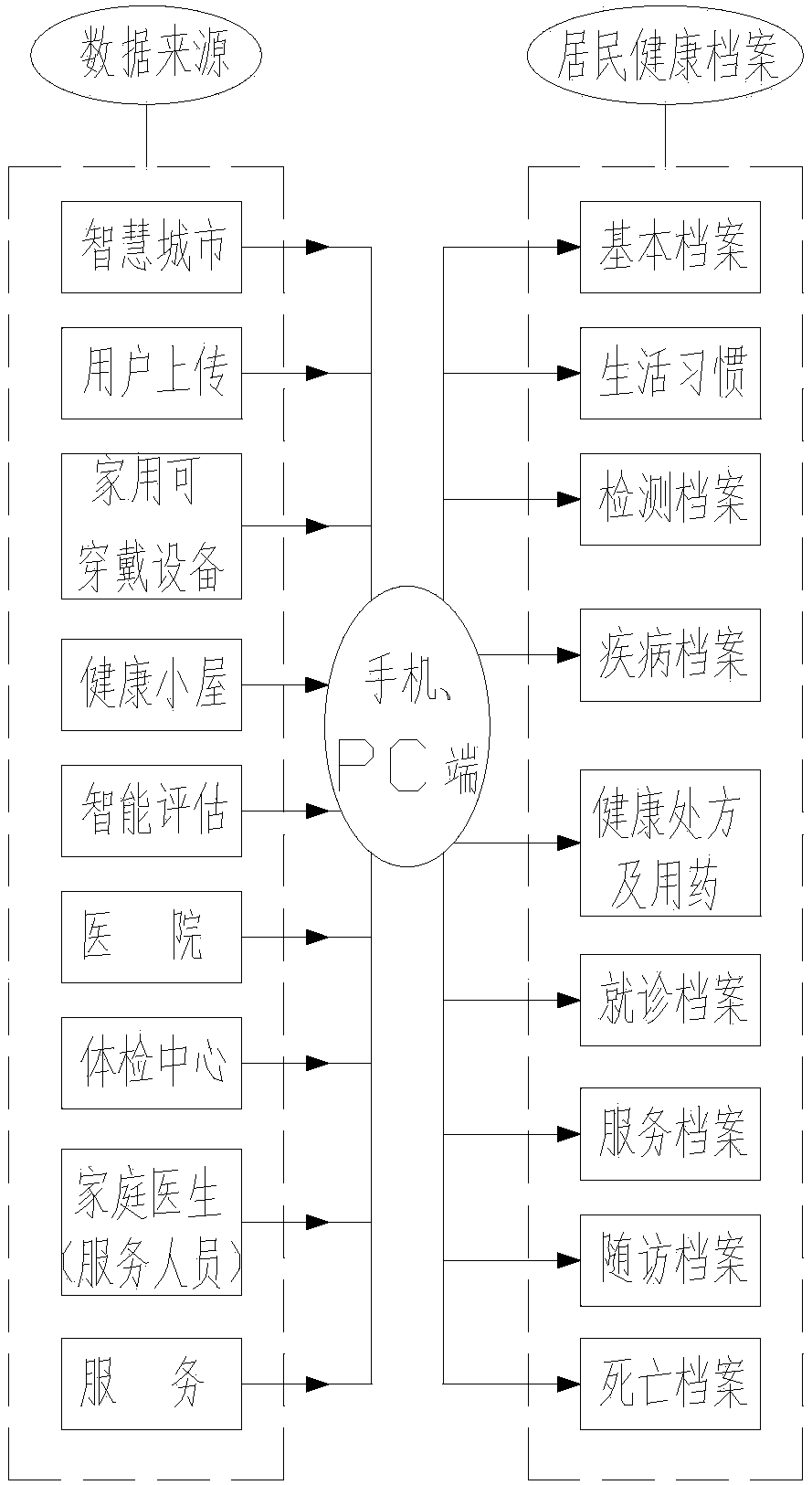
Elderly sports risk evaluation method
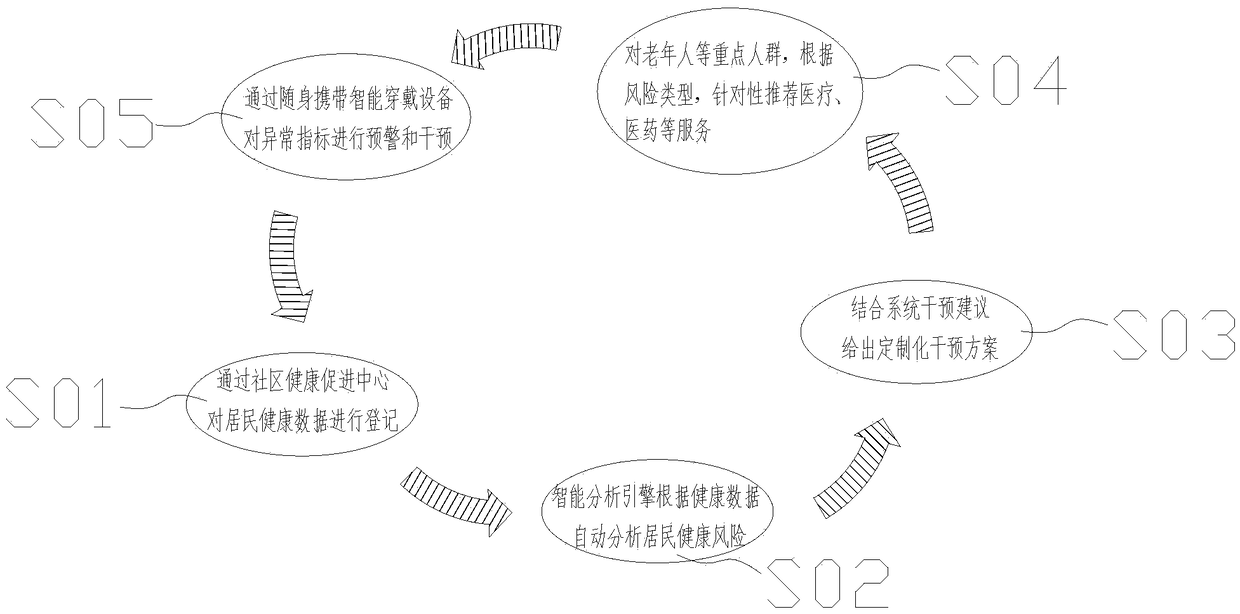
InactiveCN109065167AReasonable designBreak through information barriersHealth-index calculationIndustrial systemsRisk evaluation
The invention mainly provides an elderly sports risk evaluation method, the method is reasonable in design, breaks through information barriers, establishes a comprehensive health archive, forms long-term tracking health promotion for residents and can integrate and apply comprehensive life cycle health data of the residents. The information barriers between medical institutions at all levels needto be broken, unified certification of resident identity across the institutions is achieved, uniform services are provided for the residents, the health tracking base is unified, and high-quality health management service resources are integrated to form a comprehensive service system; public health, basic medical care, top three hospitals, chain pharmacies and other high-quality resources are integrated to form a health joint body, and the synergistic effect, accurate intelligent health risk prediction and accurate early warning capabilities are played to drive integration of services; through application of the big data analysis technology, data-based risk accurate prediction and early warning are achieved, and building an industrial system is driven for construction on the basis.
Owner:芜湖云枫信息技术有限公司
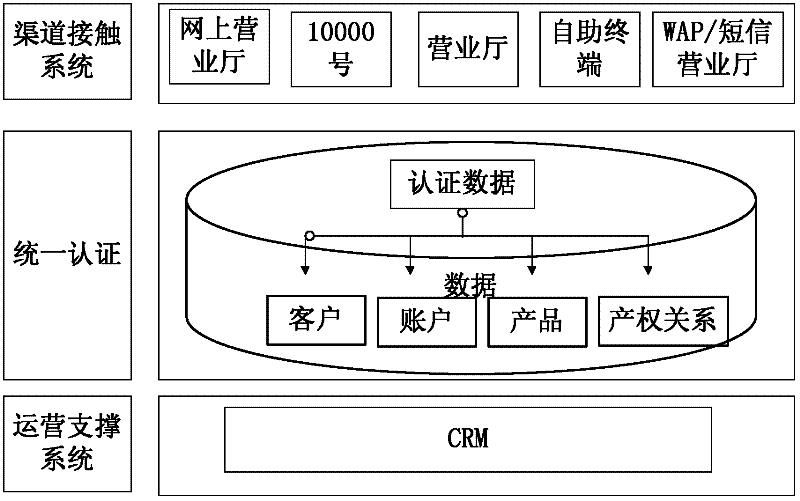
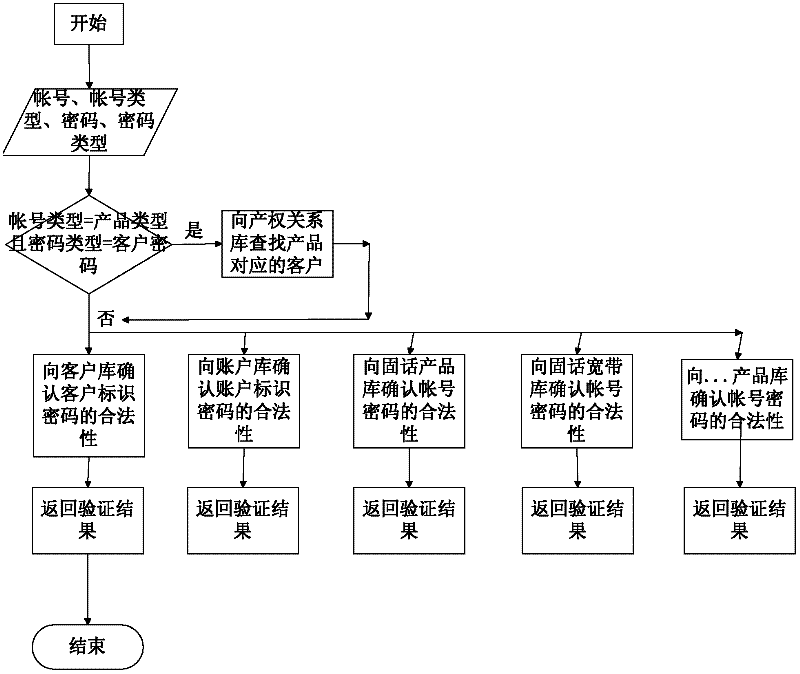
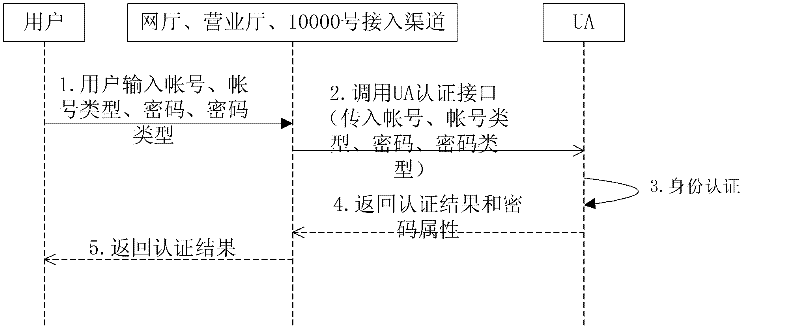
A Method of Realizing Centralized Authentication in Telecommunication Supporting System
InactiveCN102291258AOptimize IT architectureLow costData switching networksTelecommunicationsCustomer centric
A method for realizing centralized authentication in a telecommunications support system: a telecommunications user inputs one or more of the three household information through a telecommunications access channel; each channel contact system sends the three household information and user requests to The unified authentication platform UA performs authentication; the unified authentication platform UA compares the information in the received user's three-account information with the three-account information stored in the UAM, and performs identity authentication; the unified authentication platform UA returns the authentication information to the user. The present invention can promote customer-centered account management: with the rapid development of telecommunication value-added services, customer-centered account management has become a development trend, and it is necessary to integrate multiple account systems; it is also necessary to improve the efficiency of customer-oriented online business halls. Portal status drives the integration of business resources, realizes unified authentication across systems and platforms, and meets the requirements for integration of service interfaces and consistency of customer experience.
Owner:WHALE CLOUD TECH CO LTD
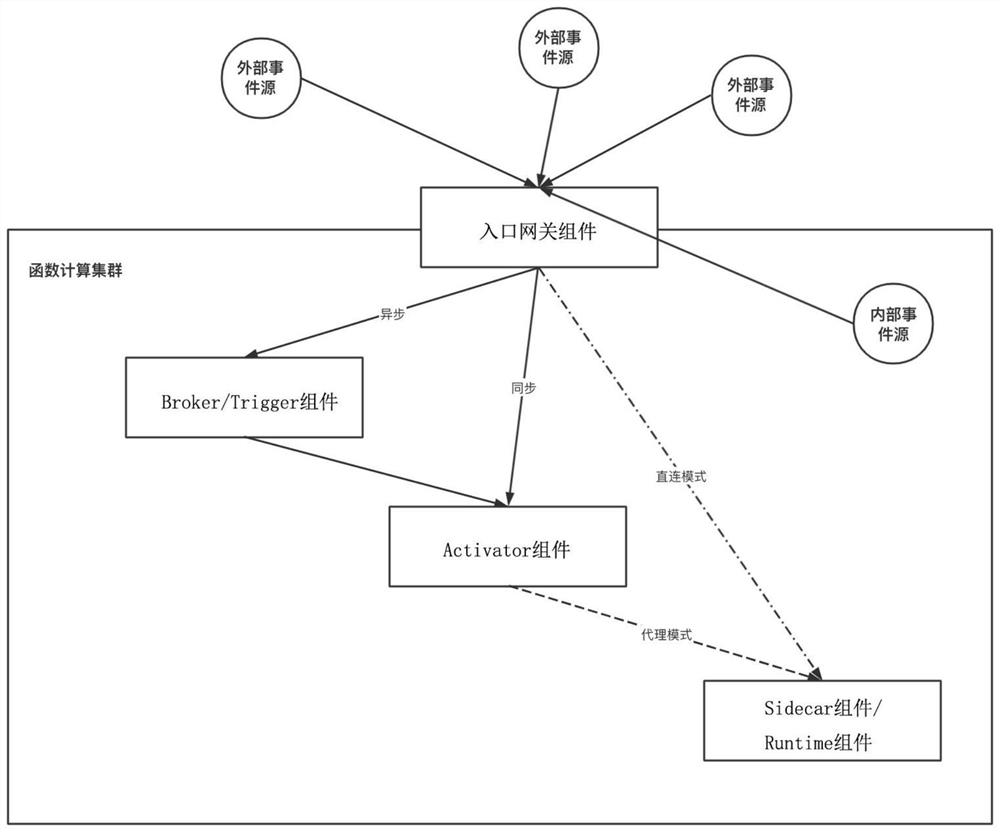
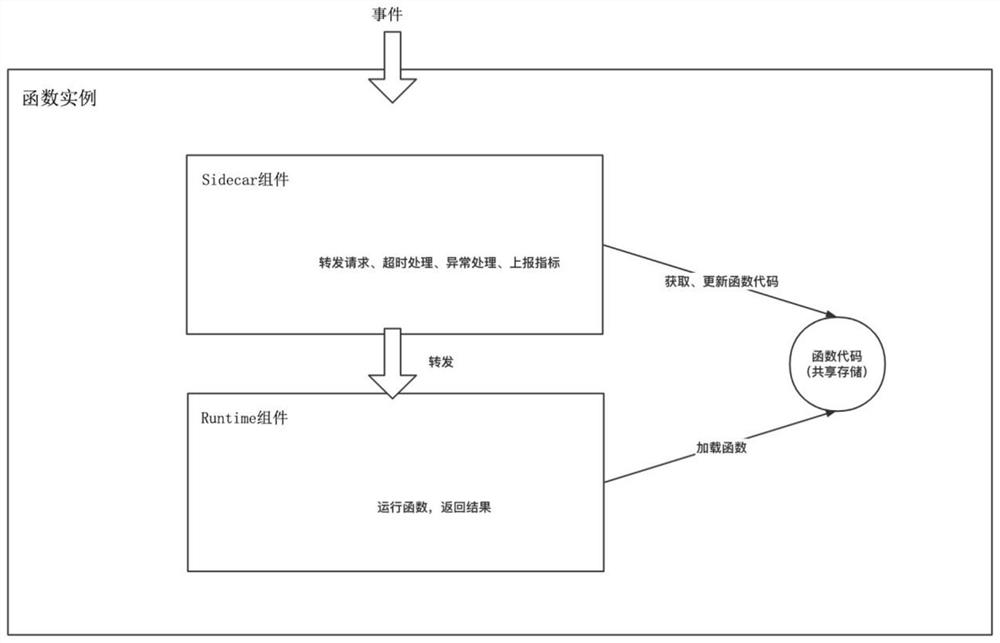
Method for realizing function computing service based on container technology
ActiveCN112328362AImprove availabilityRealize unified managementProgram loading/initiatingSoftware simulation/interpretation/emulationEngineeringMultitenancy
The invention discloses a method for realizing a function computing service based on a container technology, which relates to the technical field of server-free computing, is based on an entrance gateway component, a Broker / Trigger component, an Activer component and a Sidecar component, and comprises the following steps of: constructing the function computing service in a multi-tenant scene by using the container technology; receiving an event request of an external execution function by using an entrance gateway component, forwarding the request according to a specific rule, receiving and forwarding a function event by using a Broker / Trigger component to achieve an asynchronous processing function, controlling a request mode by using an Activer component, and selecting an agent mode to process the event request when a function instance is not completely started, when a function can normally provide service, selecting a direct connection mode to directly guide a request to a functioninstance, using a Sidecar assembly for monitoring and managing a single function instance so that finally event-driven, on-demand paid, high-availability and automatic extended multi-tenant function computing service is achieved. The cold start of the function can be optimized, and rapid capacity expansion and shrinkage and response are achieved.
Owner:SHANDONG LANGCHAO YUNTOU INFORMATION TECH CO LTD
A method and a system for improving the use efficiency of a conference room
InactiveCN108985479AMaximize utilizationRealize unmanned managementRegistering/indicating time of eventsReservationsInternal managementData acquisition
The invention discloses a method and a system for improving the use efficiency of a conference room. The method comprises the following steps: collection of authorized user information, secret key generation, database establishment, conference room reservation request confirmation service, directional transmission of attendance information, opening of conference auxiliary equipment, attendance service and end-of-meeting processing. The system includes an authorized user data acquisition module, a secret key generation module, an employee data acquisition module, a meeting room information acquisition module, a storage module, a meeting room reservation request determination service module, a meeting determination information generation transmission module, a meeting room internal management and control module, a meeting room access control identification module, an attendance service module and a communication module. The invention can precisely and efficiently arrange meeting matters,maximizes the utilization of the conference room, reduces the labor intensity of manual registration and scheduling, conveniently and quickly processes the reservation and carrying out of various meetings, achieves automation and intelligence, realizes the goal of unmanned management of the conference room, and has high practical value.
Owner:HEFEI DAHU ELECTRIC WIRE & CABLE TECH CO LTD
A conference room service method and system based on unmanned management
InactiveCN109034432ARealize unmanned managementMaximize utilizationRegistering/indicating time of eventsTelevision conference systemsInternal managementData acquisition
The invention discloses a conference room service method and system based on unmanned management. The method includes collecting authorized user information, generating secret key, establishing database, confirming service of conference room reservation request, directional sending of meeting information, opening of conference auxiliary equipment, attendance service and end-of-meeting processing.The system includes an authorized user data acquisition module, a secret key generation module, an employee data acquisition module, a meeting room information acquisition module, a storage module, ameeting room reservation request determination service module, a meeting determination information generation transmission module, a meeting room internal management and control module, a meeting roomaccess control identification module, an attendance service module and a communication module. The invention can precisely and efficiently arrange meeting matters, maximizes the utilization of the conference room, reduces the labor intensity of manual registration and scheduling, conveniently and quickly processes the reservation and carrying out of various meetings, achieves automation and intelligence, realizes the goal of unmanned management of the conference room, and has high practical value.
Owner:HEFEI DAZHUO ELECTRIC POWER CO LTD
A whole-process unmanned management method and system of a conference room
InactiveCN109033870ARealize unmanned managementMaximize utilizationReservationsDigital data protectionInternal managementData acquisition
The invention discloses a whole-process unmanned management method and system of a conference room. The method comprises the following steps: collecting authorized user information, generating secretkey, establishing database, confirming service of conference room reservation request, directional sending of attendance information, turning on of conference auxiliary equipment, attendance service and end-of-meeting processing. The system includes an authorized user data acquisition module, a secret key generation module, an employee data acquisition module, a meeting room information acquisition module, a storage module, a meeting room reservation request determination service module, a meeting determination information generation transmission module, a meeting room internal management andcontrol module, a meeting room access control identification module, an attendance service module and a communication module. The invention can precisely and efficiently arrange meeting matters, maximizes the utilization of the conference room, reduces the labor intensity of manual registration and scheduling, conveniently and quickly processes the reservation and carrying out of various meetings,achieves automation and intelligence, realizes the goal of unmanned management of the conference room, and has high practical value.
Owner:HEFEI SHANGQIANG ELECTRIC TECH CO LTD
Intelligent project data management method and system
PendingCN113392420AImprove securityAvoid unusual loginsDigital data protectionDigital data authenticationPasswordData access
The invention provides an intelligent project data management method and system. The method comprises the steps of obtaining a request for logging in a project data center; carrying out the unified identity verification on the login request, and when the identity verification is passed, allowing the data access; wherein the unified identity verification comprises the steps of obtaining identity information of a login object, taking out a user password in the login object, adding a timestamp to form a new character string, encrypting the new character string, matching an encryption result with the user password, taking a difference value between current server time and the timestamp, if the difference value is within a fixed range and the user password can be matched, successfully verifying the identity of the login user. According to the invention, through the unified identity authentication method and the unified authority management strategy based on the timestamp, the security of identity authentication and authority management is greatly improved, the abnormal login of the project data center library is effectively avoided, and the security of the project data is improved.
Owner:SHANDONG ELECTRIC POWER ENG CONSULTING INST CORP
IMS-based flow media network system
ActiveCN101026615BAchieve authenticationRealize billingAutomatic exchangesTwo-way working systemsApplication serverNetworked system
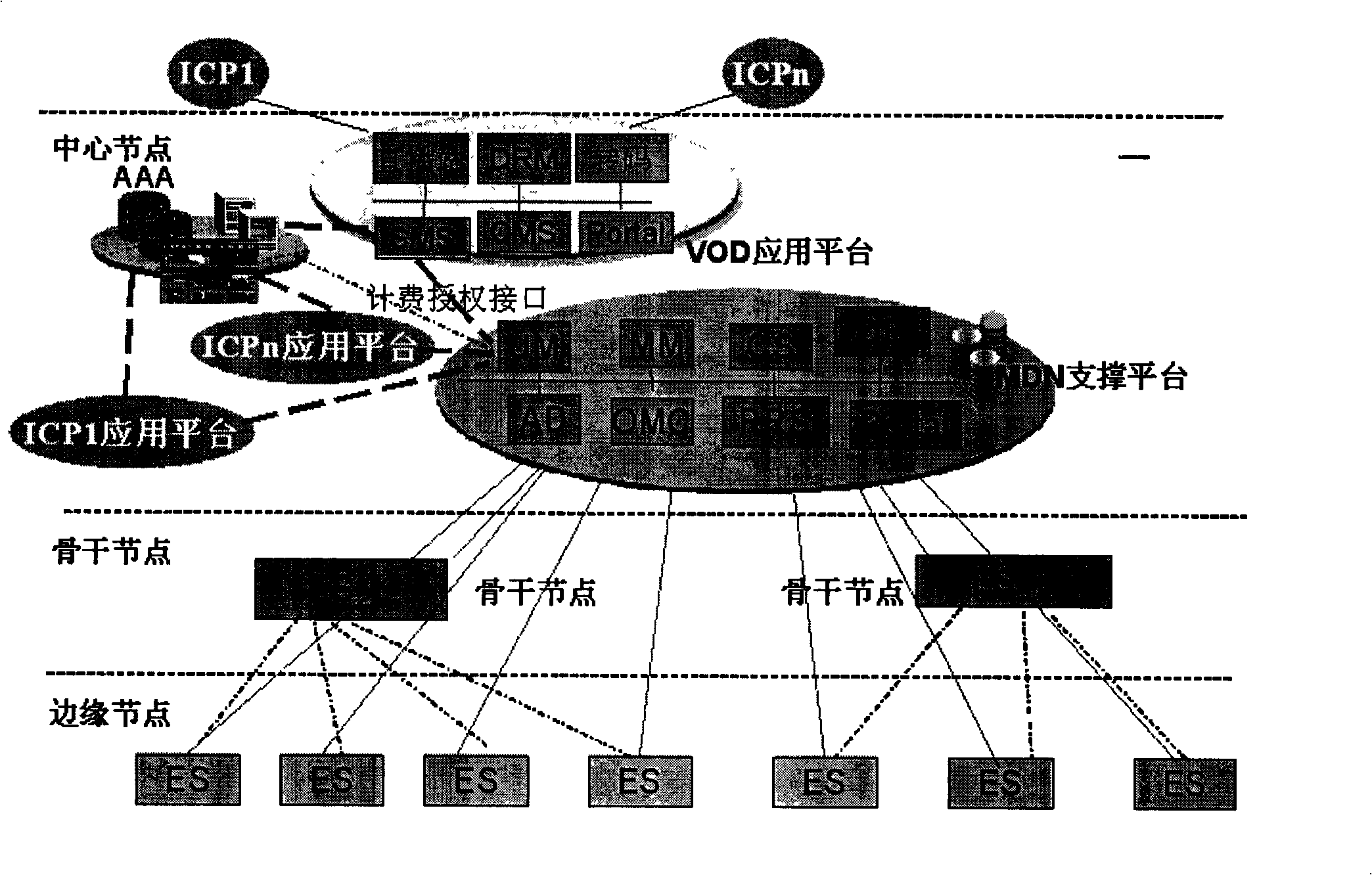
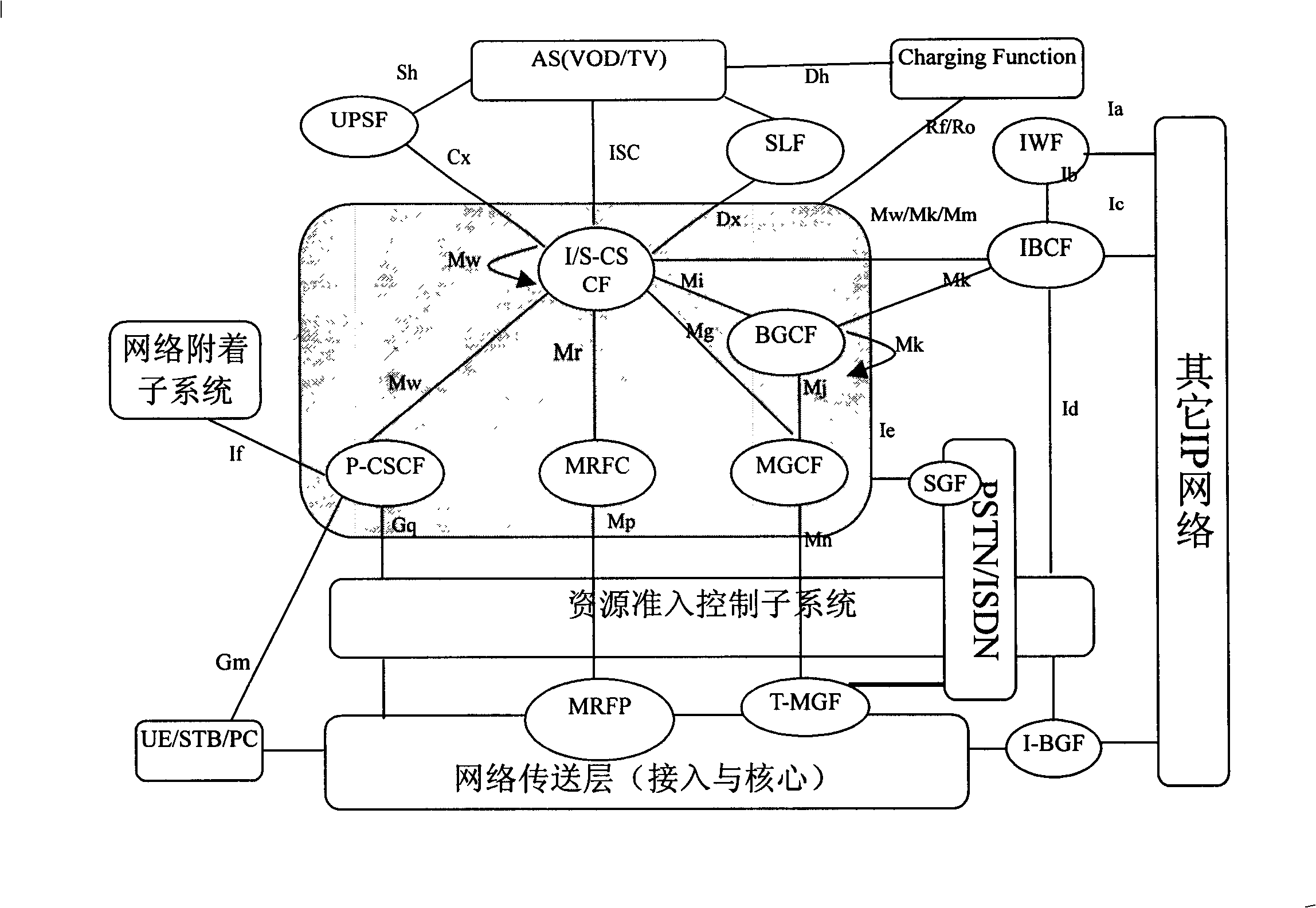
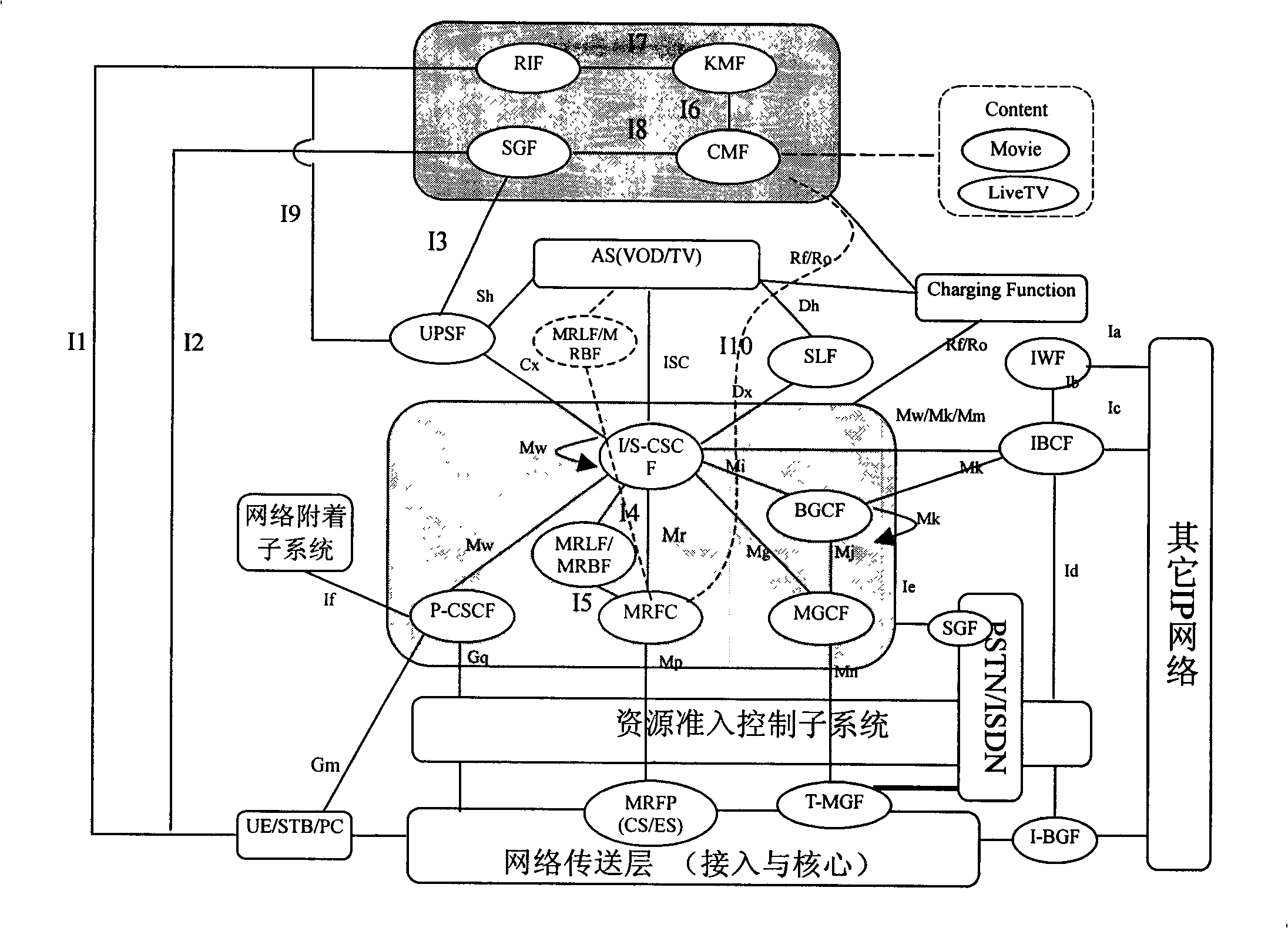
The system includes following parts: P-CSCF, S-CSCF, and I-CSCF in use for implementing controlling session, routing, and service triggering functions; entity for enabling stream media service (SMS) is in use for implementing supporting function needed by SMS; media resources functional (MRF) entity is in use for implementing function of media server; media resources locating function (MRLF) entity, or media resources broker function (MRBF) entity is in use for implementing function of distributing and dispatching media resource; application server AS is in use for implementing function of logic controlling SMS; user signed data service function (UPSF) is in use for saving user information of signed stream media user, authority information, and selectable SMS information; and user equipment UE. Comparing prior art, the invention realizes united authentication, charging, managing supporting functions for users, and guarantees QoS.
Owner:HUAWEI TECH CO LTD
Efficient management method and system for a public meeting room
InactiveCN109063868AMaximize utilizationRealize unmanned managementKey distribution for secure communicationReservationsInternal managementData acquisition
The invention discloses an efficient management method and a system for a public meeting room. The method comprises the following steps: collecting authorized user information, generating secret key,establishing database, meeting room reservation request confirmation service, directional transmission of attendance information, opening conference auxiliary equipment, attendance service and meetingend processing. The system includes authorized user data acquisition module, secret key generation module, employee data acquisition module, meeting room information acquisition module, storage module, meeting room reservation request determination service module, meeting determination information generation transmission module, meeting room internal management and control module, meeting room access control identification module, attendance service module and communication module. The invention can precisely and efficiently arrange meeting matters, maximizes the utilization of the conferenceroom, reduces the labor intensity of manual registration and scheduling, conveniently and quickly processes the reservation and carrying out of various meetings, achieves automation and intelligence,realizes the goal of unmanned management of the conference room, and has high practical value.
Owner:HEFEI FANTENG ENVIRONMENTAL PROTECTION TECH CO LTD
Token-based authentication method and device, equipment and storage medium
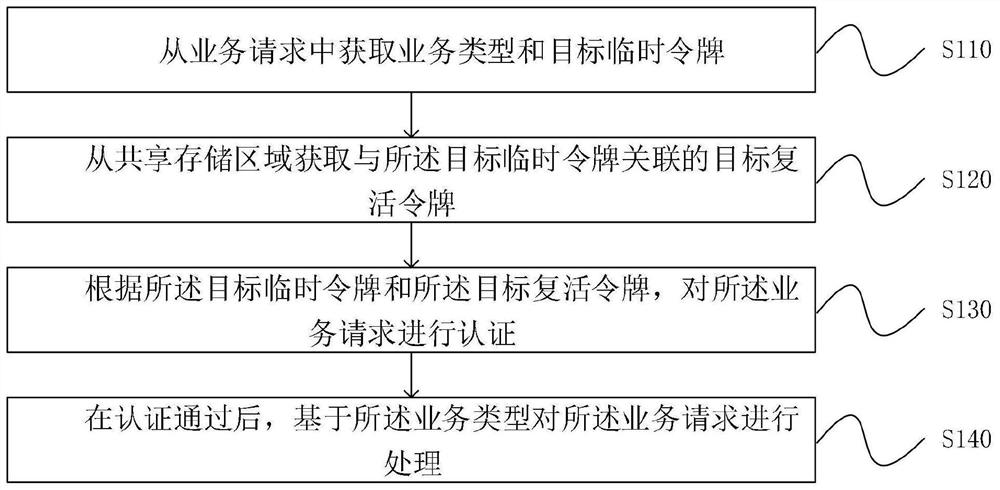
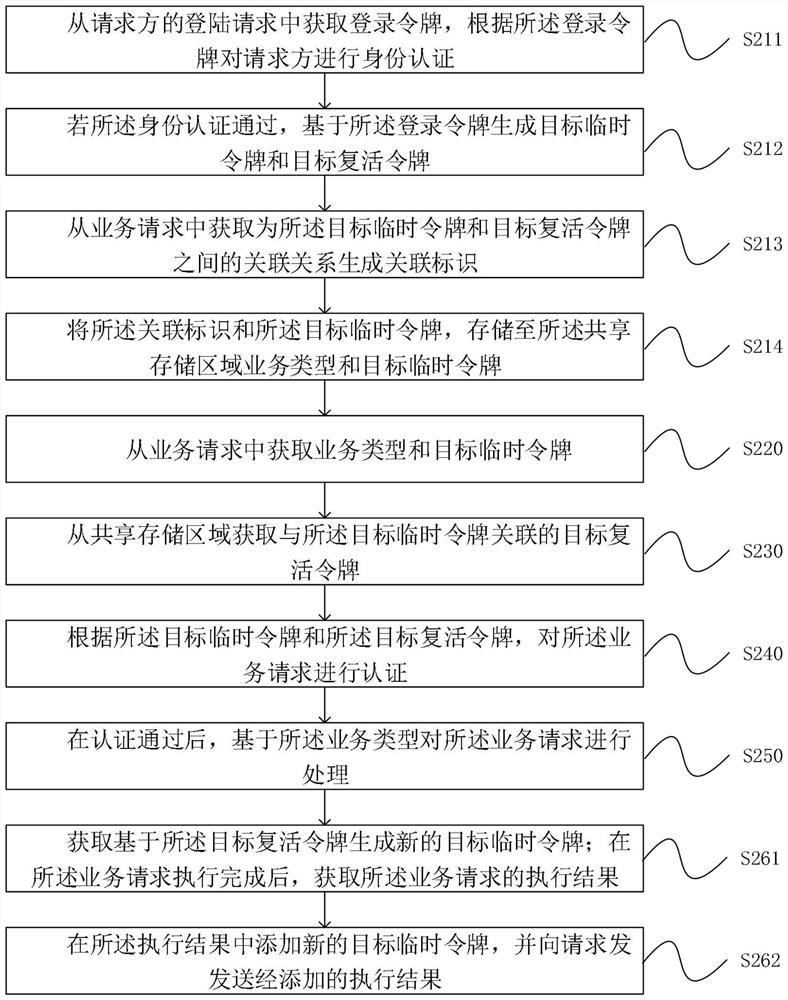
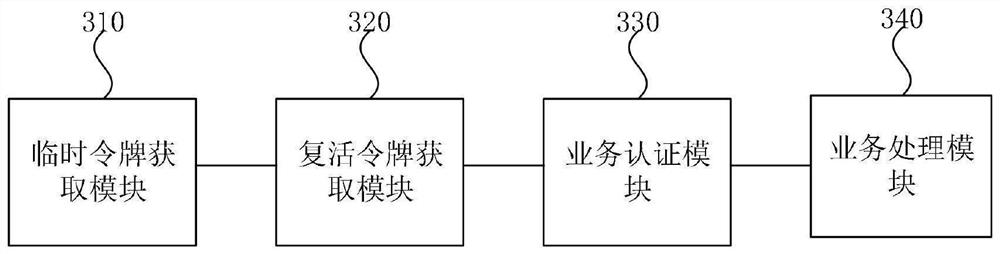
PendingCN114448715ARetrofit needs are smallRealize unified authenticationUser identity/authority verificationEngineeringAuthentication
The invention discloses a token-based authentication method and device, equipment and a storage medium. The method comprises the following steps: acquiring a service type and a target temporary token from a service request; obtaining a target reviving token associated with the target temporary token from a shared storage area; according to the target temporary token and the target reactivation token, authenticating the service request; and after the authentication is passed, processing the service request based on the service type. According to the embodiment of the invention, unified authentication and authentication of the requester can be realized, and the authentication efficiency is improved.
Owner:AGRICULTURAL BANK OF CHINA
System, application and method for IP network access authentication based on personal identification module IM
ActiveCN101282259BImprove securityImprove controllabilityUser identity/authority verificationData switching by path configurationInternet privacyIdentity recognition
An IP access authentication system based on an identity identification module IM is disclosed, comprising an IP network coupled to each IP terminal, a mobile network and an application gateway, the system also comprises an authentication proxy between the IP network and the mobile network, the authentication proxy can launch an authentication request to the corresponding mobile network for user identity information; a card reader is arranged at the IP terminal and able to read the user identity information in the IM card; the information is sent to the authentication proxy via the IP network.The invention also provides an application and a method thereof. The invention improves security of the authentication for user identity, expands usage range of smart cards like PIM, SIM, UIM and USIM, and achieves united authentication for users.
Owner:CHINA TELECOM CORP LTD
Multi-tenant authority authentication method based on operation and maintenance auditing system
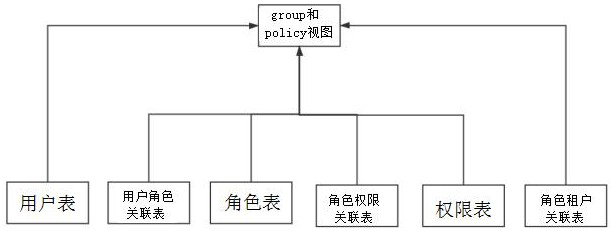
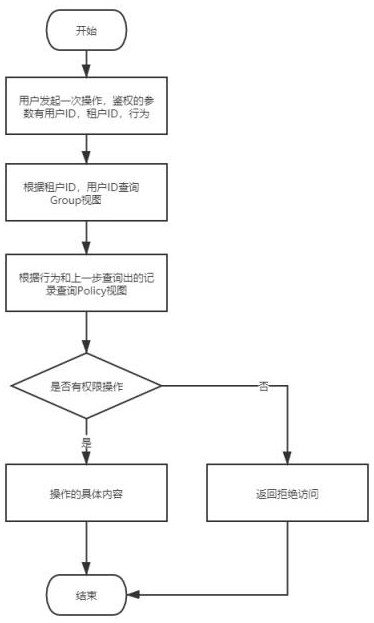
ActiveCN111984977ARealize unified authenticationReduce maintenance costsDigital data protectionEngineeringMultitenancy
The invention discloses a multi-tenant authority authentication method based on an operation and maintenance auditing system, which comprises a group view and a poly view, and the policy view is usedfor storing the relationship among roles, tenants and authorities; the group view is used for storing association relationships between user inheritance roles and tenant inheritance tenants. Aiming atusers, roles, authorities and relations of the users, roles and authorities in an operation and maintenance auditing system, related authorized behaviors are converted into a specific structure by using a database materialized view, so that the unified authentication of the users, user groups and behaviors under multiple tenants can be realized, and the key point is that the authorized query andauthentication are unified through the materialized view and a specific storage structure. According to the invention, the logic of unified system permission judgment is realized, the maintenance costof the system is reduced, the complexity of the system is reduced, and the permission authentication performance is improved.
Owner:CHENGDU DBAPP SECURITY
A method and system for realizing multi-terminal unified authentication
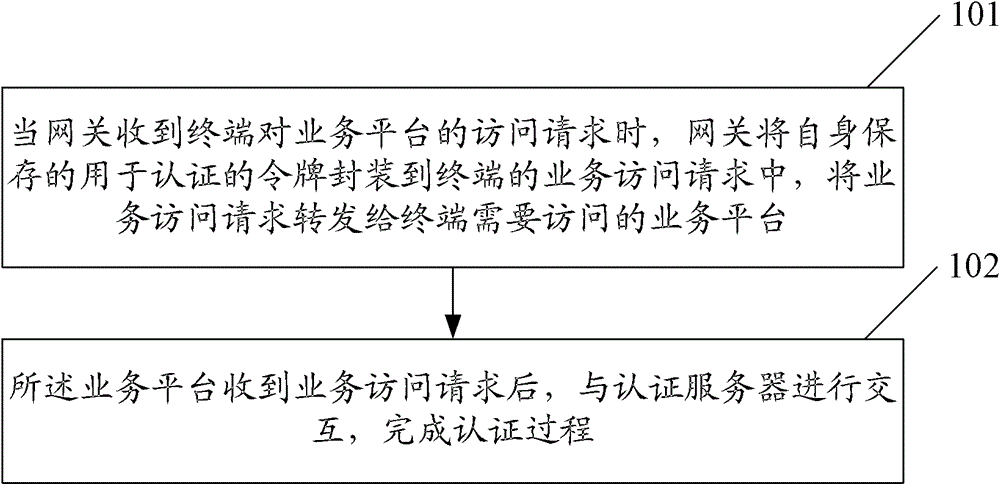
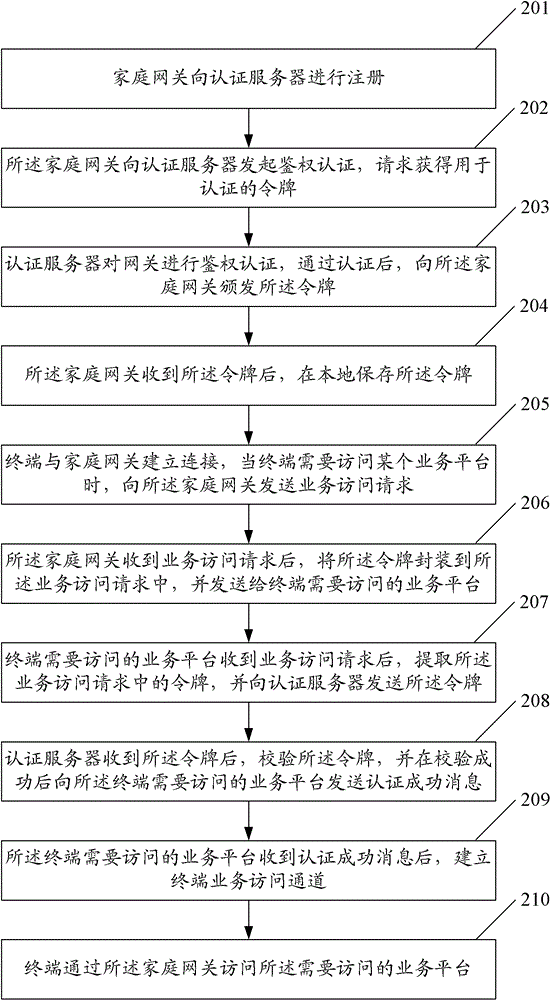
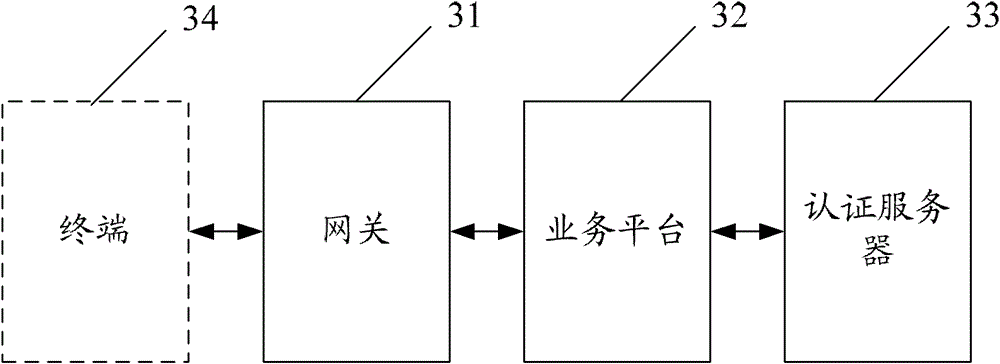
ActiveCN103188076BEasy to operateImprove experienceUser identity/authority verificationNetwork connectionsAuthentication serverComputer science
The invention discloses a method for achieving multi-terminal unified authentication, which comprises the steps that when a gateway receives an access request of a terminal on a service platform, the gateway packages a token stored by the gateway and used for authentication into the service access request of the terminal, and forwards the service access request to the service platform required to be accessed by the terminal; the service platform interacts with an authentication server after receiving the service access request; and the authentication is accomplished. The invention further discloses the gateway and a system for achieving the multi-terminal unified authentication. With the adoption of the method, the gateway and the system, the unified authentication can be achieved effectively, and the operation process of the terminal is simplified.
Owner:CHINA MOBILE GROUP JIANGSU
Authentication method and device
ActiveCN101668016BRealize automatic authenticationRealize unified authenticationTransmissionSecurity arrangementApplication serverComputer science
The embodiment of the invention provides an authentication method and a device; the device comprises the following steps: a network authentication request of an IP multimedia subsystem IMS, which is sent by user equipment, is received; according to the IMS network authentication request, authentication information of an application server is obtained from a home subscriber server HSS; an IMS network authentication respond message containing the authentication information of the application server is transmitted to the UE, so as to trigger the UE to utilize the authentication information of the application server to carry out authentication in the application server. In the method of the embodiment of the invention, uniform authentication of IMS and the application server is realized by carrying the authentication information of the application server in the returned result of the IMS network authentication without mutually intervening the authentication process of the application server by the user. The method brings great convenience to the usage of the user and the management of operators; in addition, the existing IMS authentication flow is fully utilized to realize simpleness.
Owner:HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com