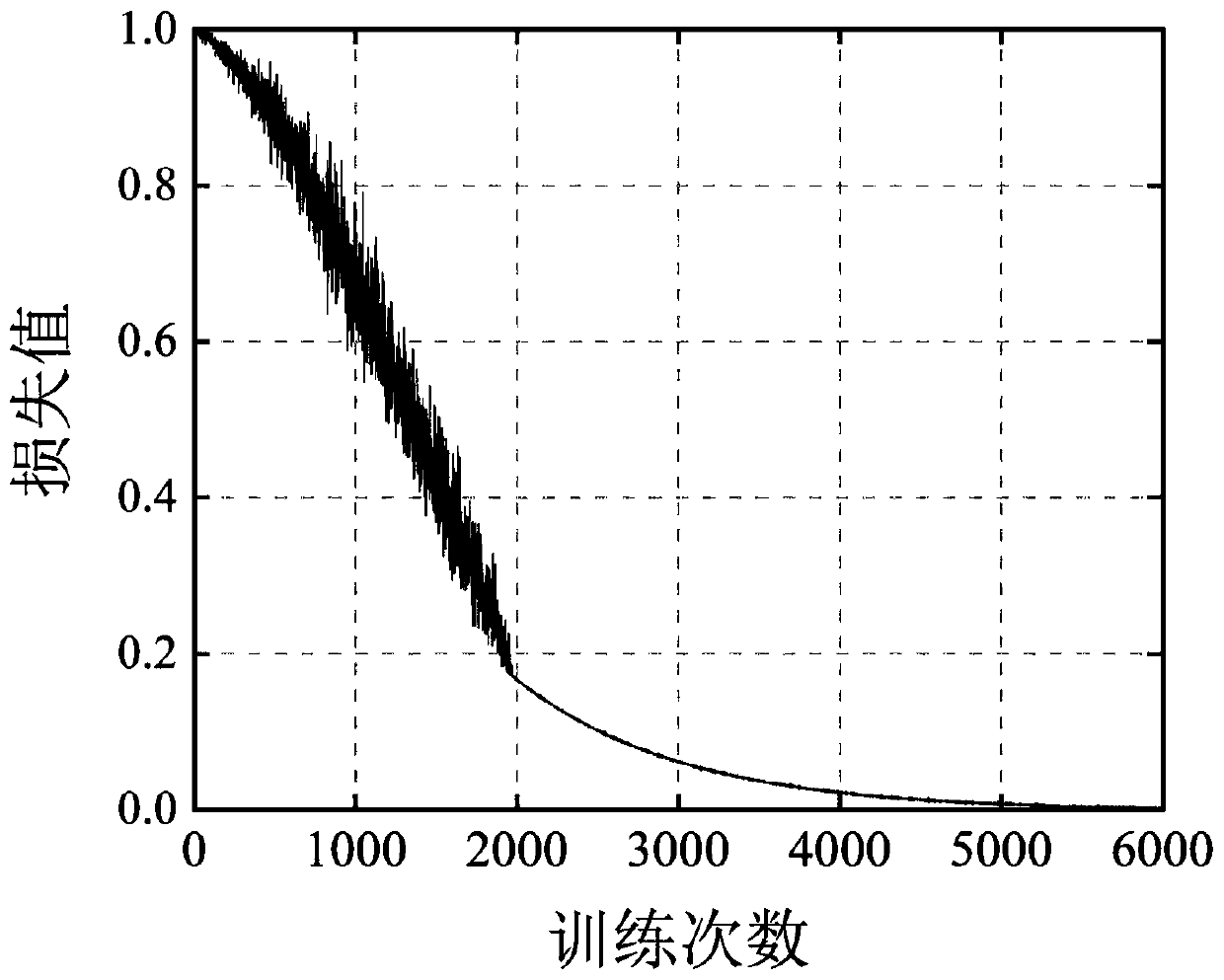
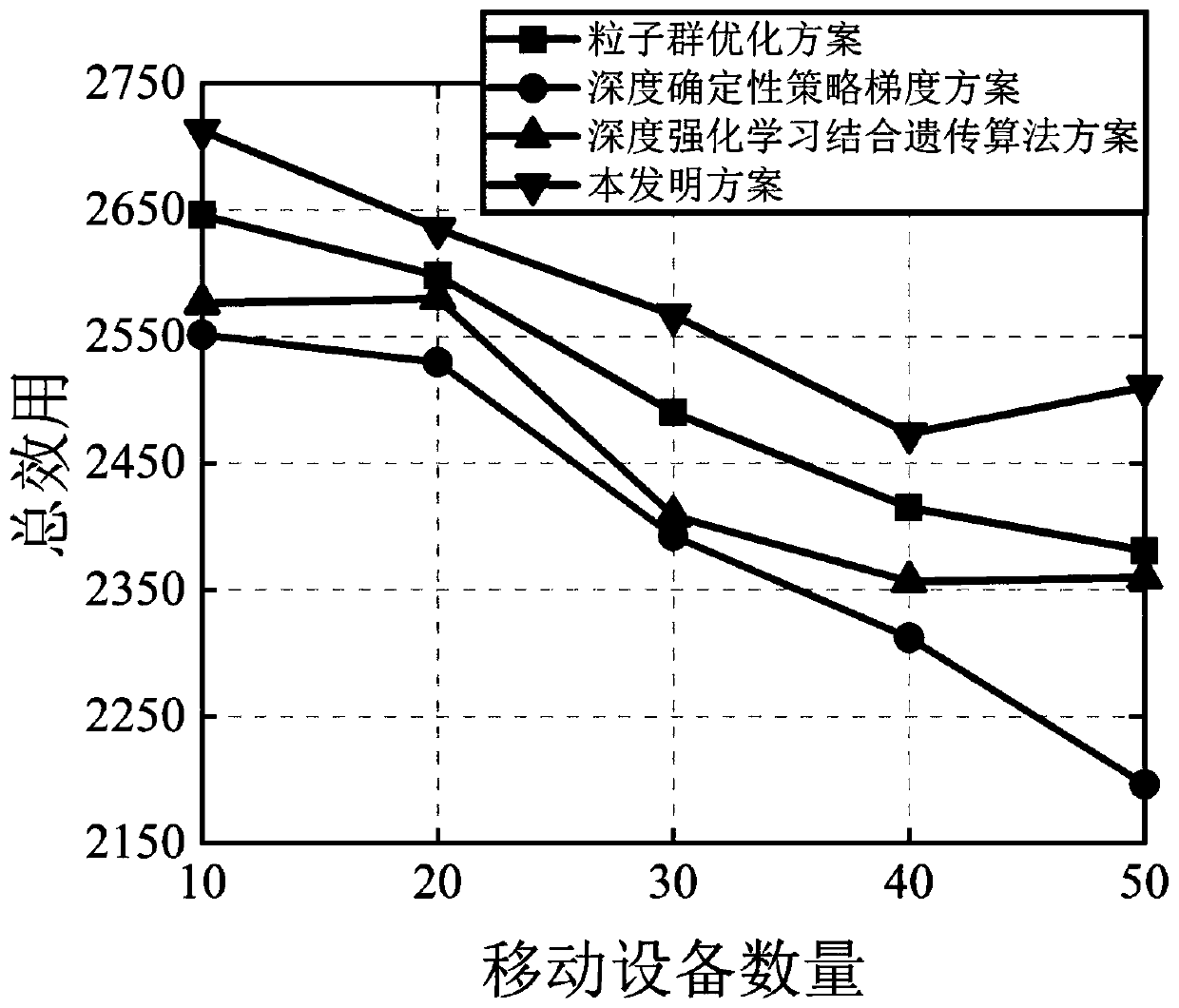
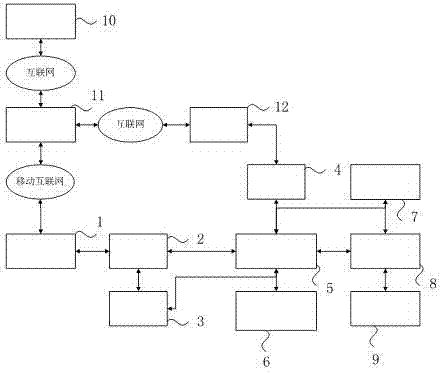
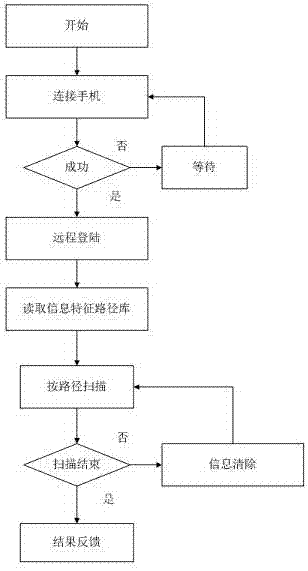
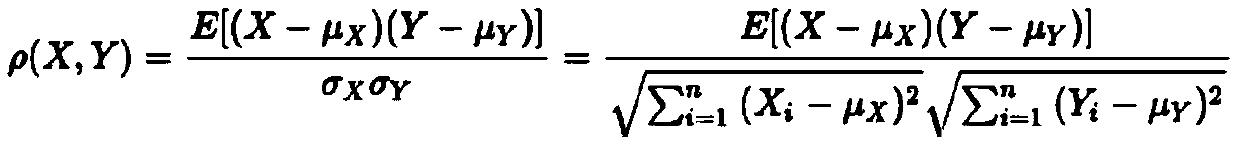Patents
Literature
94results about How to "Protect data security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
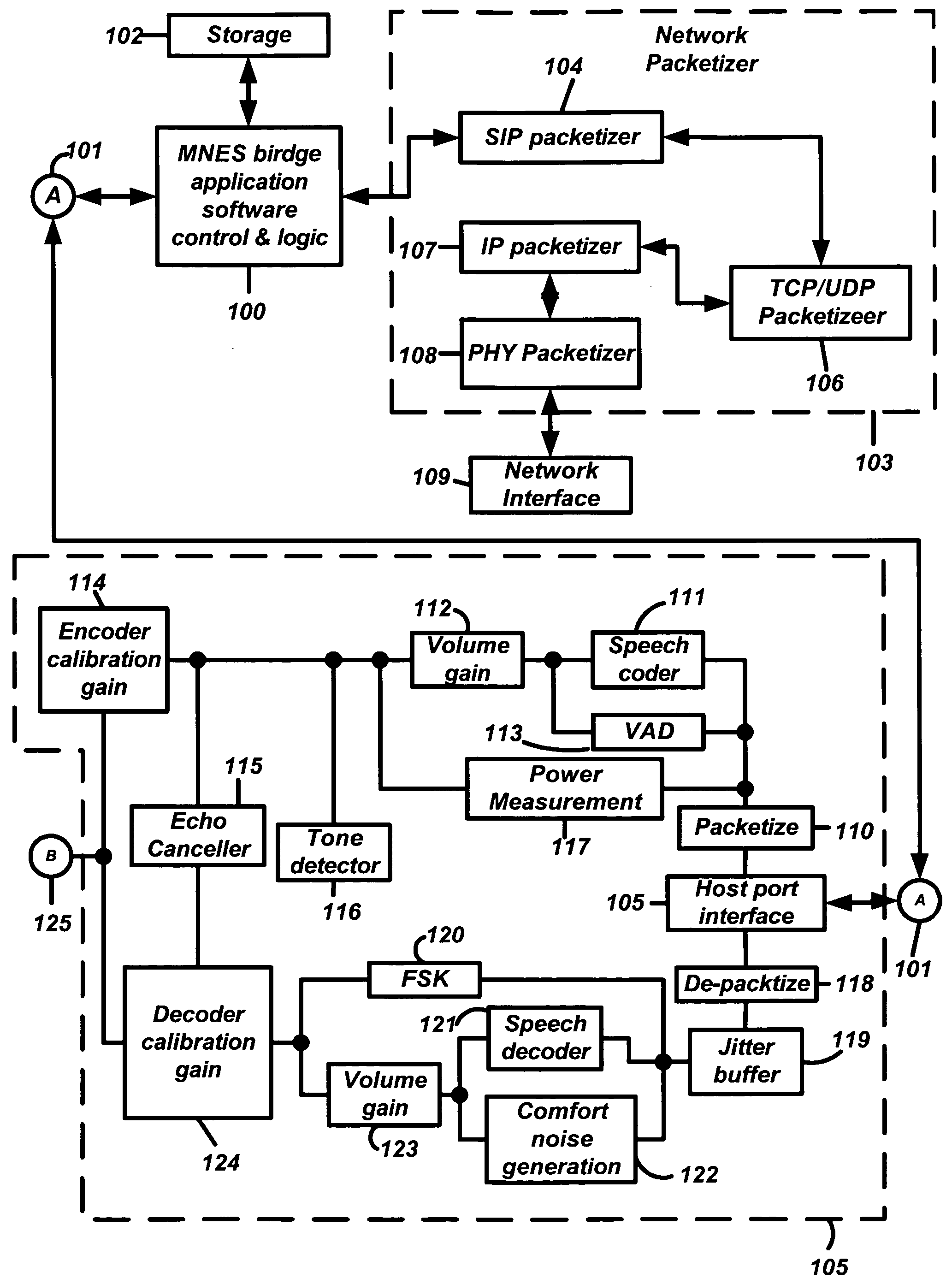
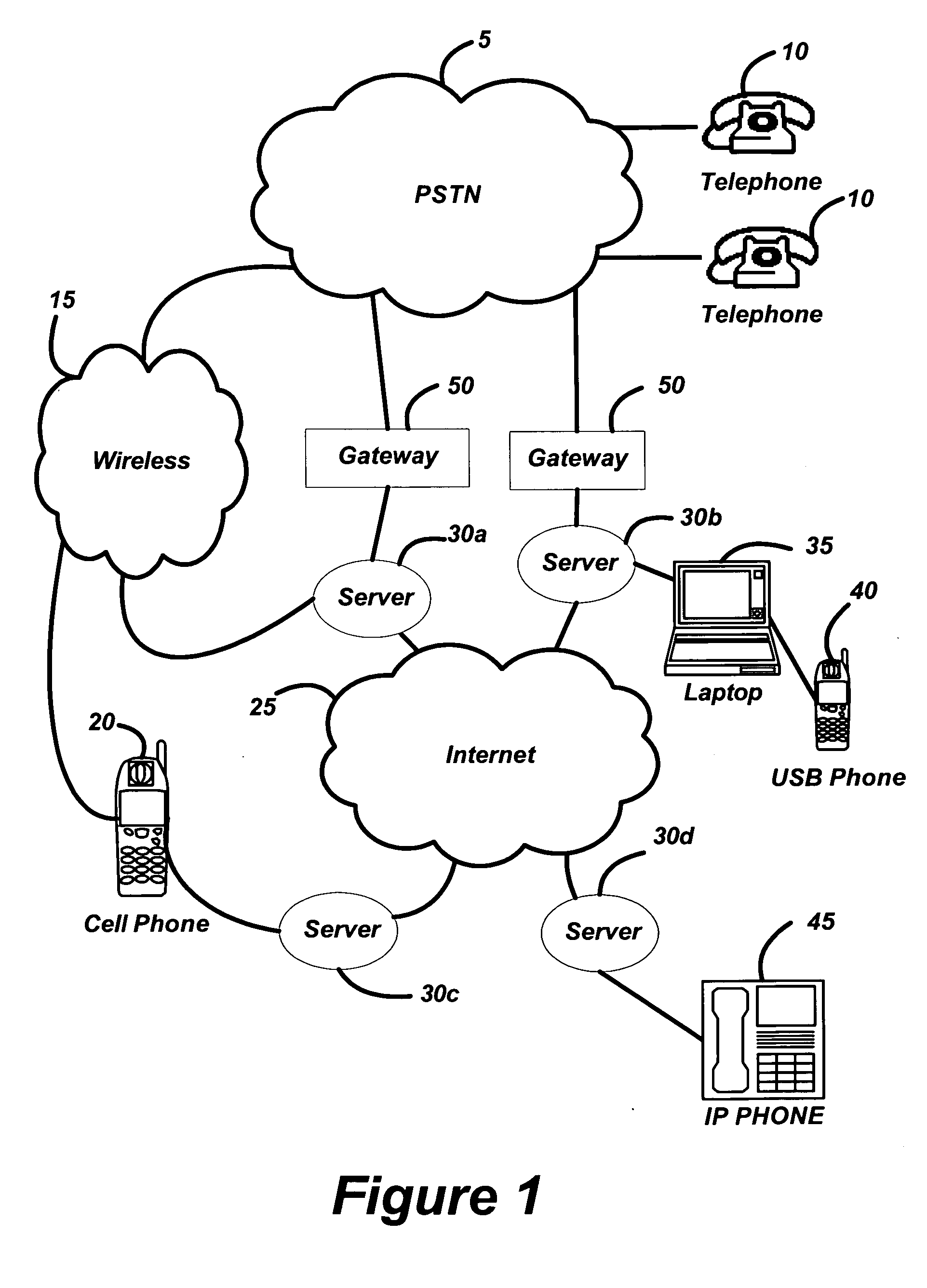
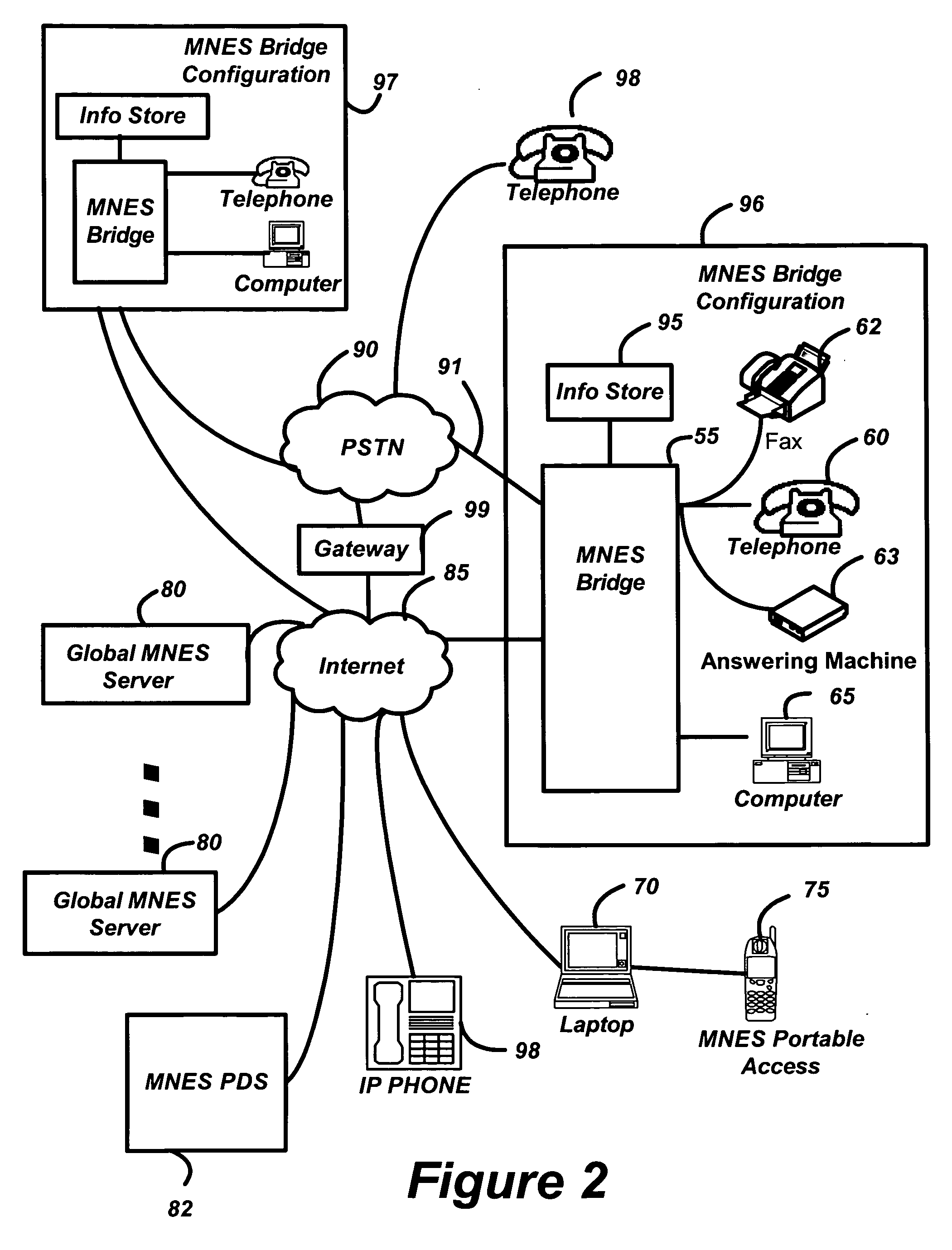
Multi-network exchange system for telephony applications
InactiveUS20050091407A1Protect data securityEasy transferInterconnection arrangementsError preventionThe InternetElectronic information
A multi-network exchange system has a first type network (PSTN) and a second type network (Internet) and a multi-network exchange bridge in communication with the first and second type networks for the transfer of electronic information signals (telephone calls) between the first and second type networks. The multi-network exchange bridge apparatus facilitates transfer of electronic information signals to a portable access device or a gateway portal in communication with a node of one of second type networks from the first network. The multi-network exchange bridge has at least one multi-network instantiation device that enables the portable access device to function as a remote extension of the multi-network exchange bridge. A fixed address translation device provides conversion of a first address fixedly describing a node of the first type network to a second address or third address virtually describing nodes of the second type network
Owner:EMERJ
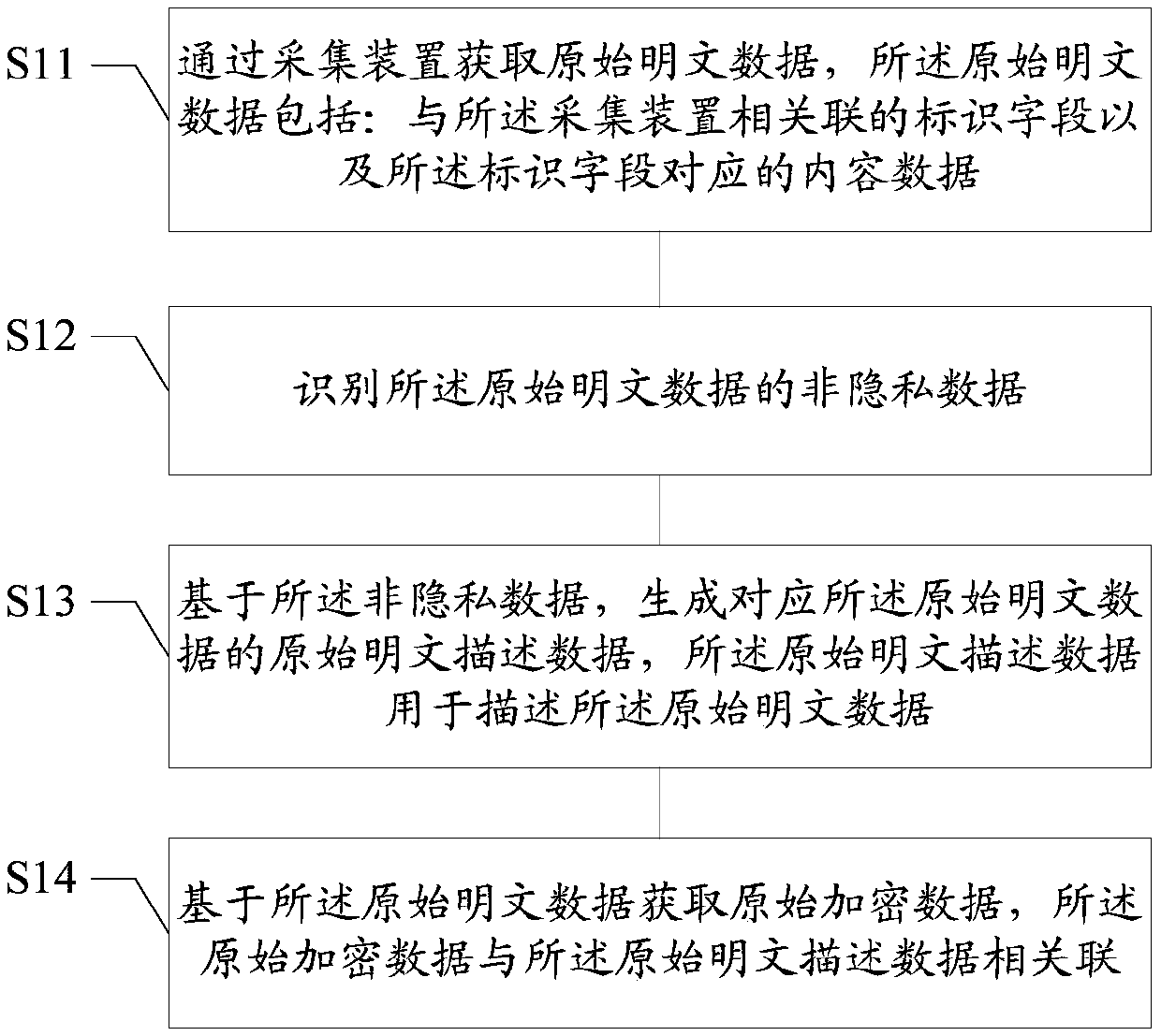
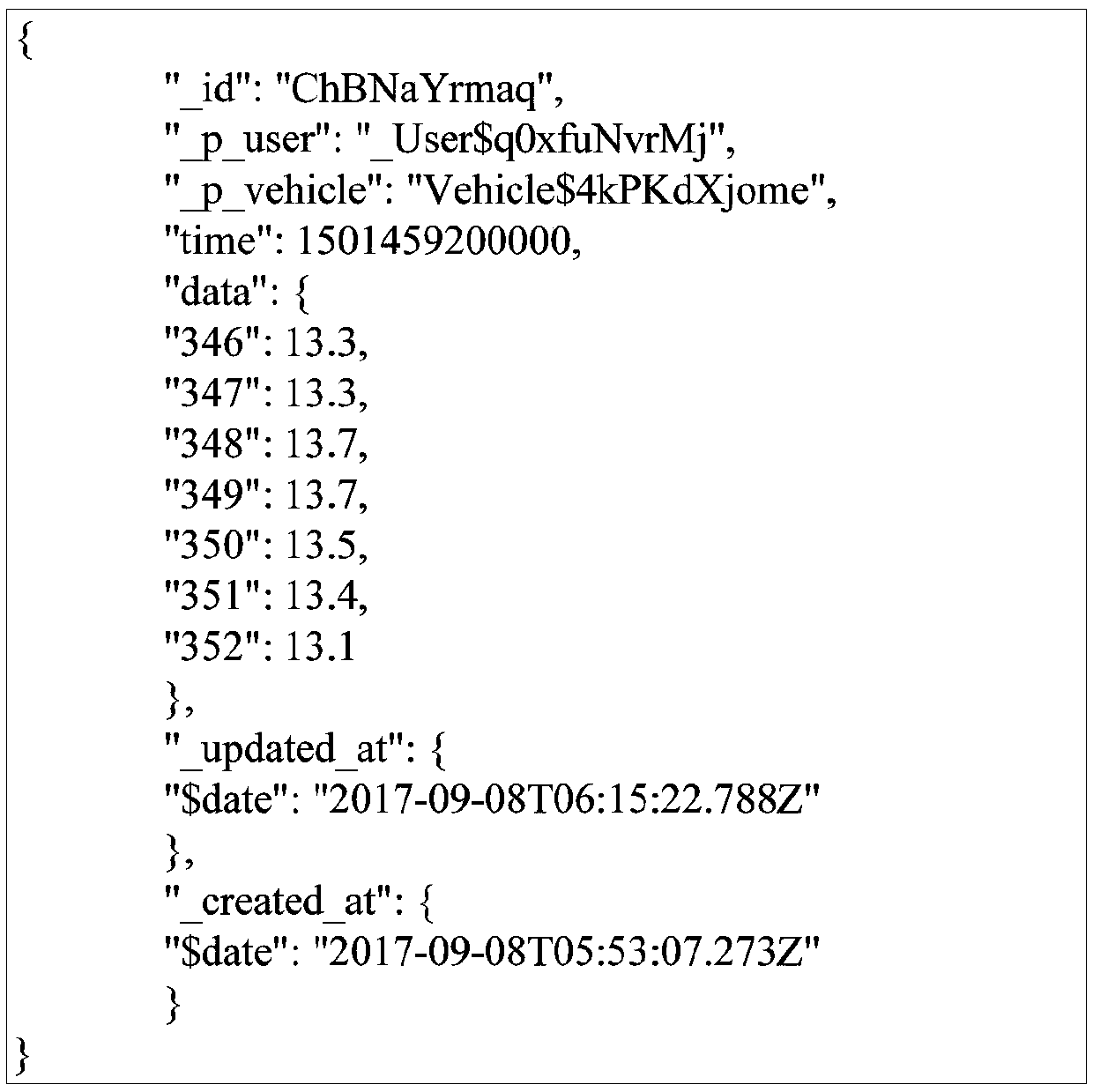
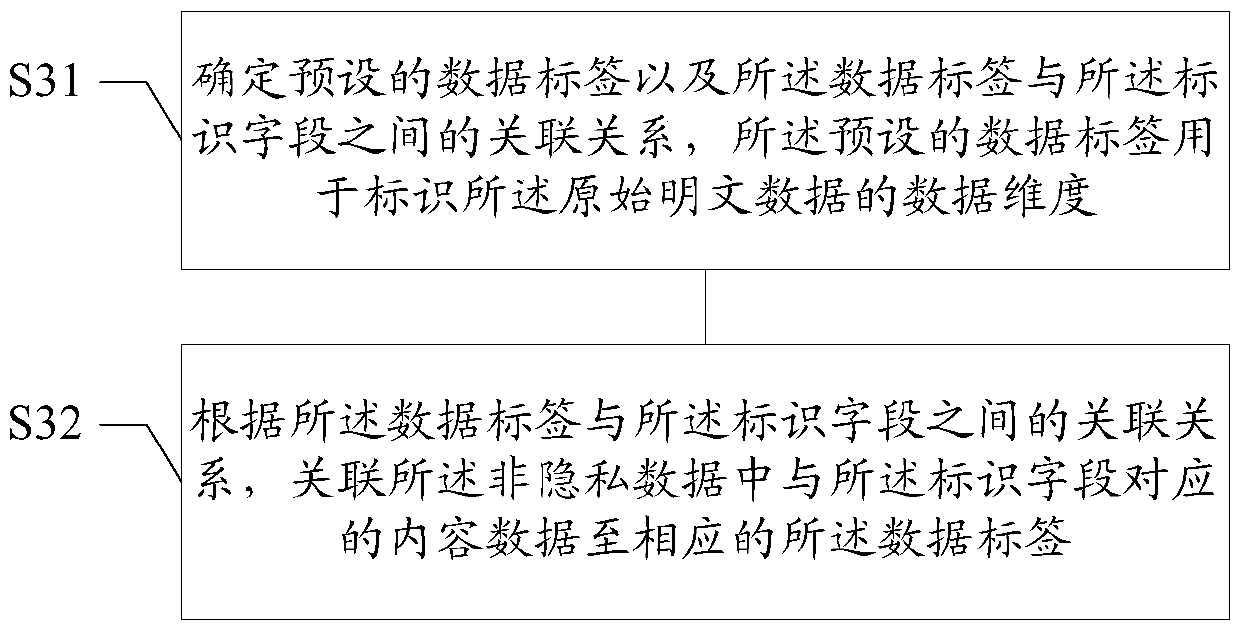
Data processing method and device, medium and terminal
Embodiments of the invention disclose a data processing method and device, a medium and a terminal. The data processing method comprises the following steps of acquiring original plaintext data through an acquisition device, wherein the original plaintext data comprises an identification field associated with the acquisition device and content data corresponding to the identification field; identifying non-privacy data of the original plaintext data on the basis of the identification field; generating original plaintext description data corresponding to the original plaintext data on the basisof the non-privacy data, wherein the original plaintext description data is used for describing the original plaintext data; and obtaining original encrypted data based on the original plaintext data, wherein the original encrypted data is associated with the original plaintext description data. According to the technical scheme, the security of data in a data trading process can be improved.
Owner:石更箭数据科技(上海)有限公司
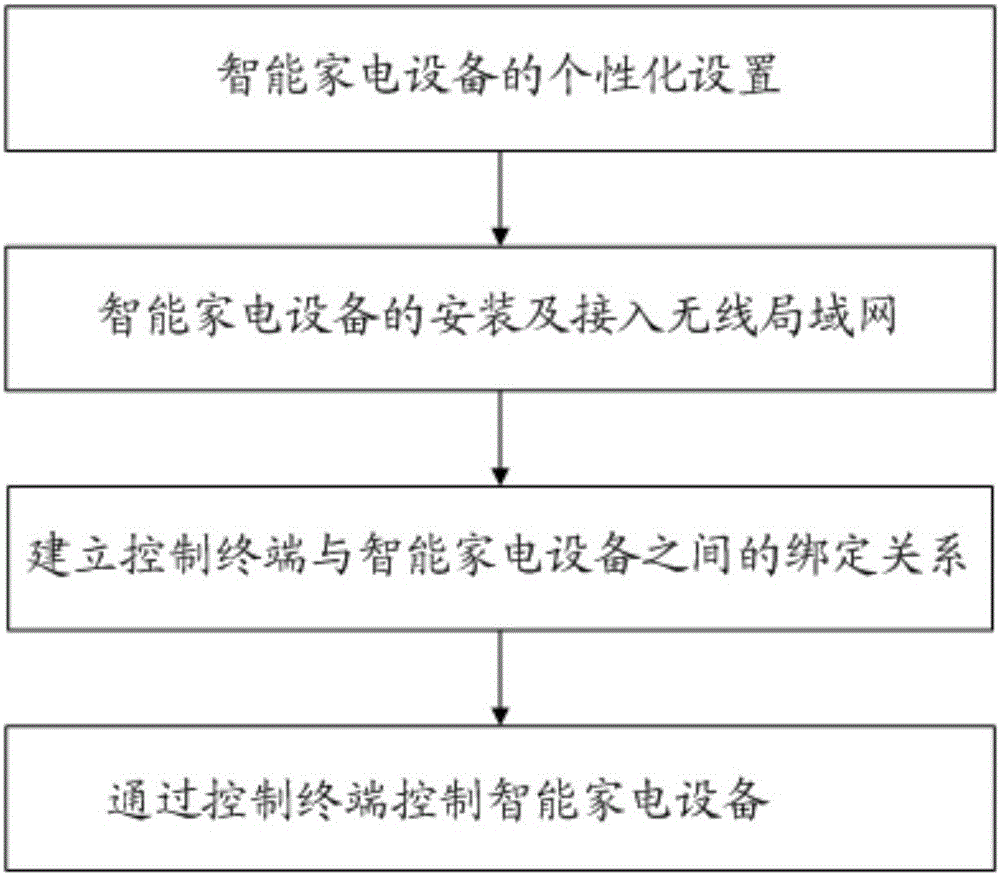
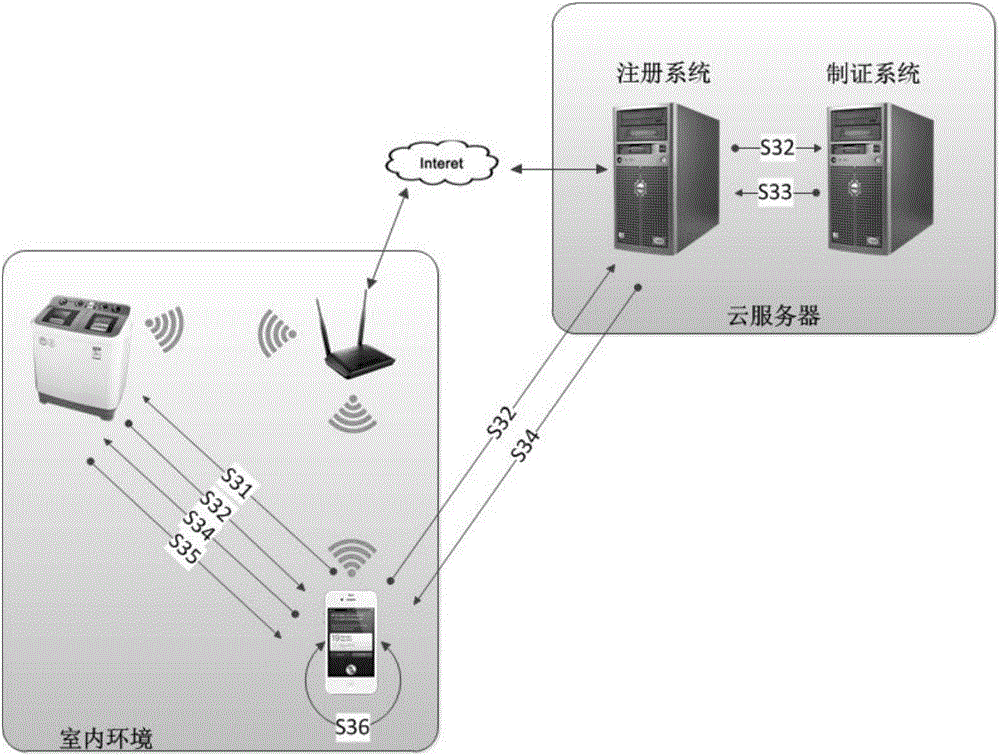
Intelligent household appliance remote control method based on PKI system
ActiveCN106130982AProtect data securitySimplify the encryption and decryption processTransmissionSmart appliancePersonalization
The invention discloses an intelligent household appliance remote control method based on a PKI system, which relates to the field of remote control of intelligent household appliances. The method comprises the steps that: firstly, a to-be-controlled intelligent household appliance is subjected to personalized setting; the intelligent household appliance decrypts ciphertext data sent by a control terminal and further accesses a wireless local area network; under coordination of a cloud server, and by taking a device certificate as a root of trust, a binding relation between the control terminal and the intelligent household appliance is established; and finally, the intelligent household appliance is controlled through the control terminal. In the intelligent household appliance remote control method based on the PKI system, functions, such as network identity recognition, network communication secrecy keeping, communication data tampering prevention and communication subject non-repudiation, are realized through a PKI key system technology, the data used in a communication process are all transmitted in a ciphertext mode, security of the data is guaranteed by strength of an encryption algorithm used, thus, problems, such as tampering of the communication data and information leakage, are avoided, and various security risks in the existing intelligent household appliance remote control method are solved.
Owner:北京万协通信息技术有限公司
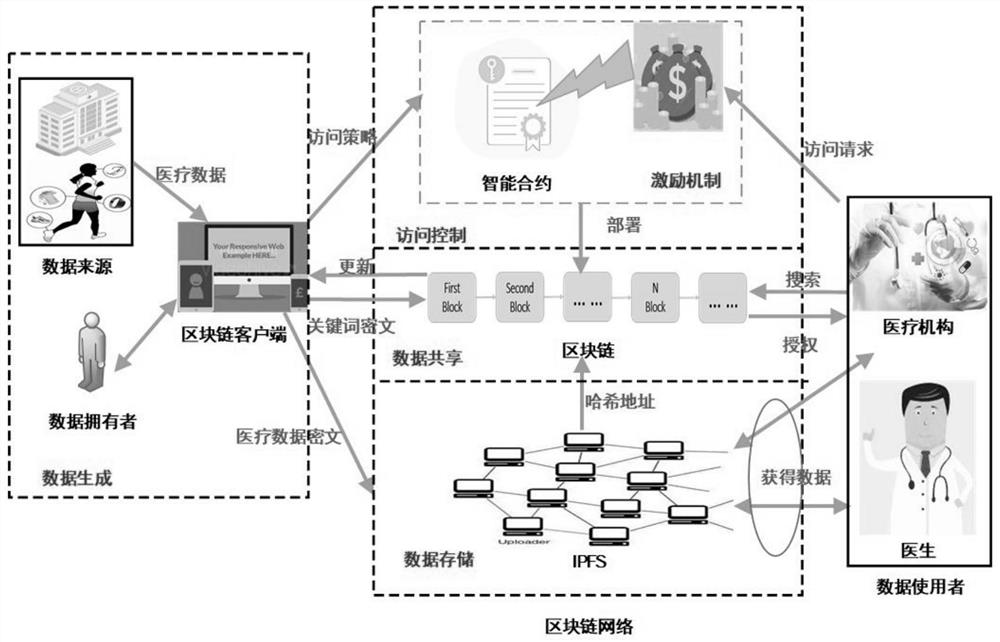
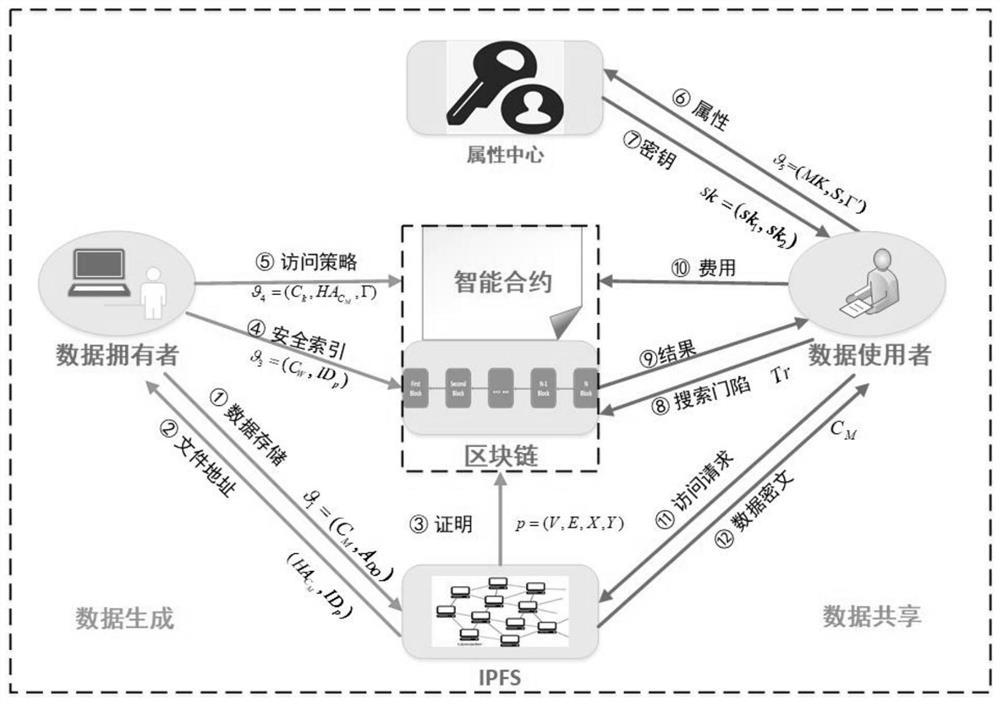
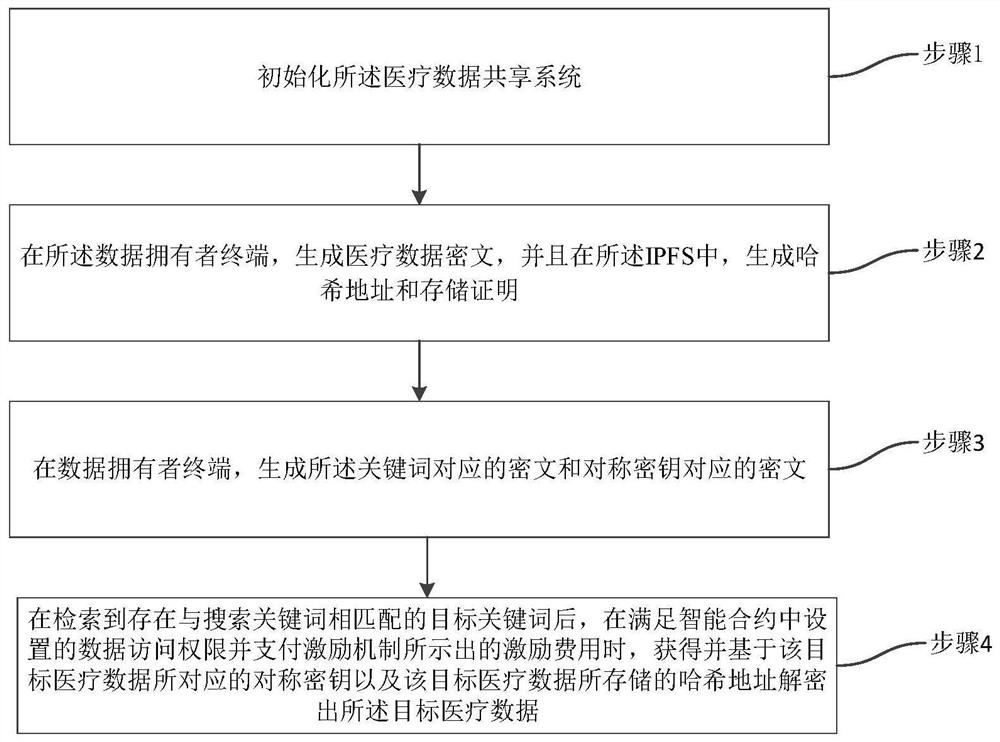
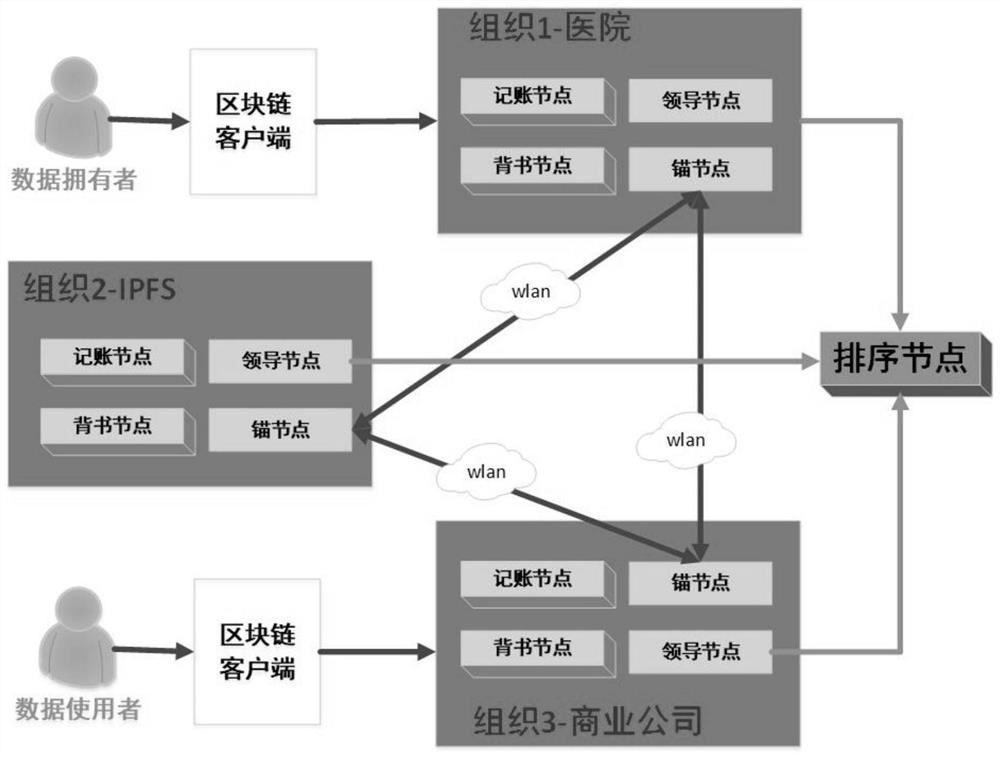
Medical data security sharing system and method based on IPFS and alliance chain
PendingCN111916173AEnable secure storageImplement fine-grained access controlDigital data protectionFile metadata searchingSafe storageData security
Owner:ANHUI NORMAL UNIV
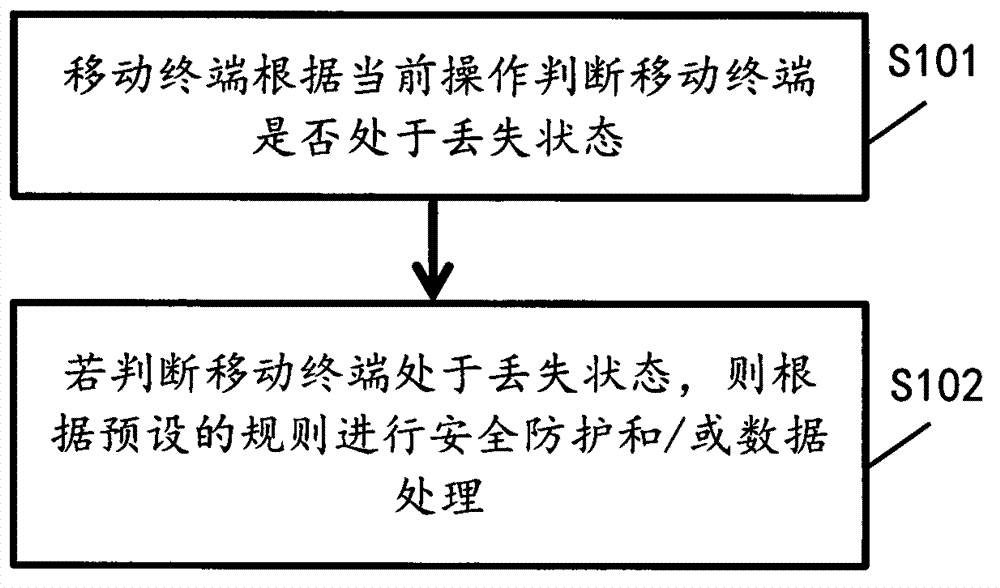
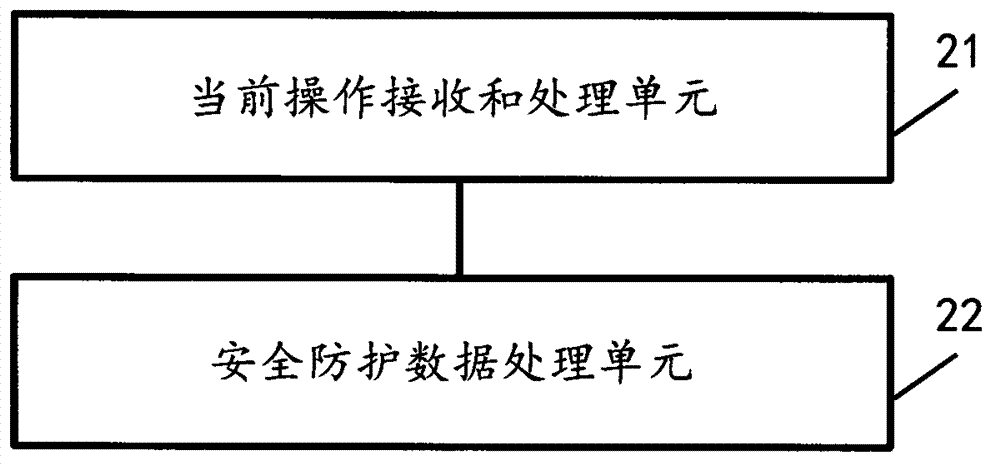
Method for initiatively performing loss judgment and data processing and mobile terminal
InactiveCN102929807AProtection securityProtect data securityMemory loss protectionPasswordComputer engineering
The invention discloses a method for initiatively performing loss judgment and data processing and a mobile terminal. The method comprises the step that the mobile terminal judges whether the mobile terminal is under loss state or not according to present operation. The present operation comprises that a present operator inputs a password to the mobile terminal; or the mobile terminal is powered on or powered off; or the mobile terminal operates according to a preset protocol; the operation at least comprises the following steps: receiving a loss state judgment command of the mobile terminal remotely sent by a user of the mobile terminal; or / and automatically positioning position data by the mobile terminal according to the preset protocol. If the mobile terminal is judged to be in the loss state, safety protection and / or data processing are / is performed according to preset rules. The mobile terminal is initiatively judged to be in the loss state or not through recognizing result data of the present operation, data, privacy and property safety of the user of the mobile terminal are effectively protected.
Owner:周万荣
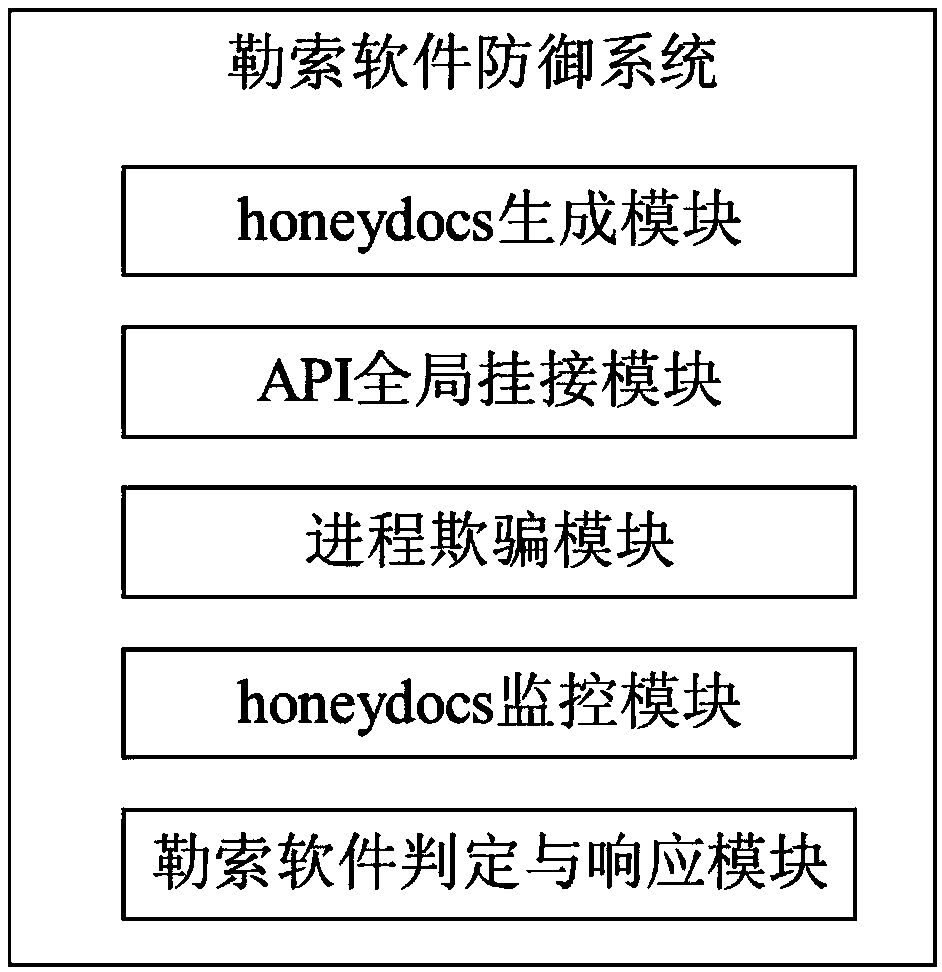
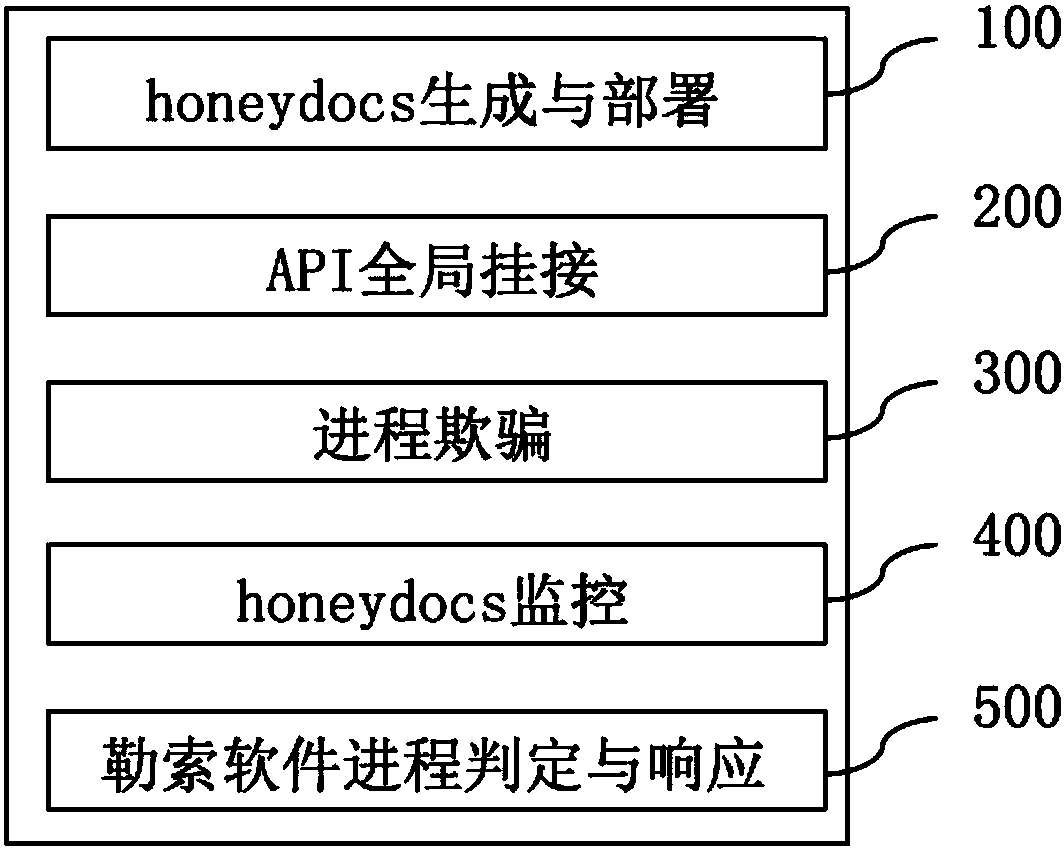
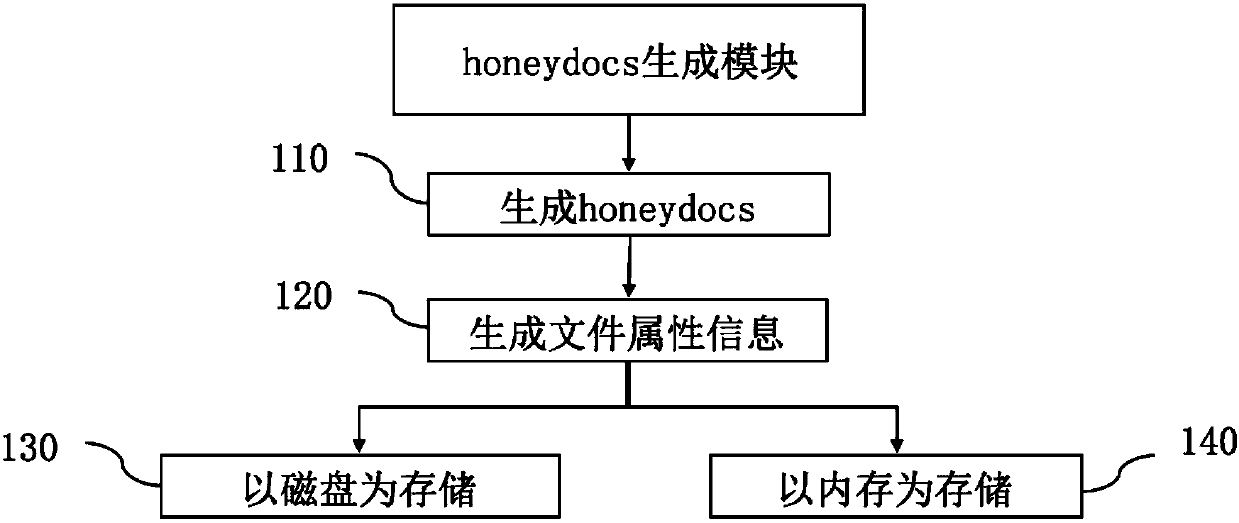
Ransomware defense method and system
ActiveCN107729752ANo normal file system effectsGuaranteed lossDigital data protectionPlatform integrity maintainanceRansomwareFinite segment
The invention relates to a ransomware defense method and system. The method comprises the following steps that 1, overall hooking is performed on an API which must be called by ransomware in the kernel mode or the user mode of an operation system; 2, finite segment cheating data is generated and deployed; 3, when a process is subjected to file traversal operation, a certain amount of cheating datais inserted into the traversal result and returned back to the process so as to cheat the process; 4, when the API obtained after overall hooking finds that the process operates the cheating data, whether the cheating data is abnormally changes or not is monitored so that whether the process is a malicious act of the ransomware or not is determined; 5, if the process is the malicious act of the ransomware, the process is ended and the user is informed. Under the condition of low consumption and zero loss, real-time detection and termination can be performed on the process of the ransomware, and users' and enterprises' data and property safety are protected.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
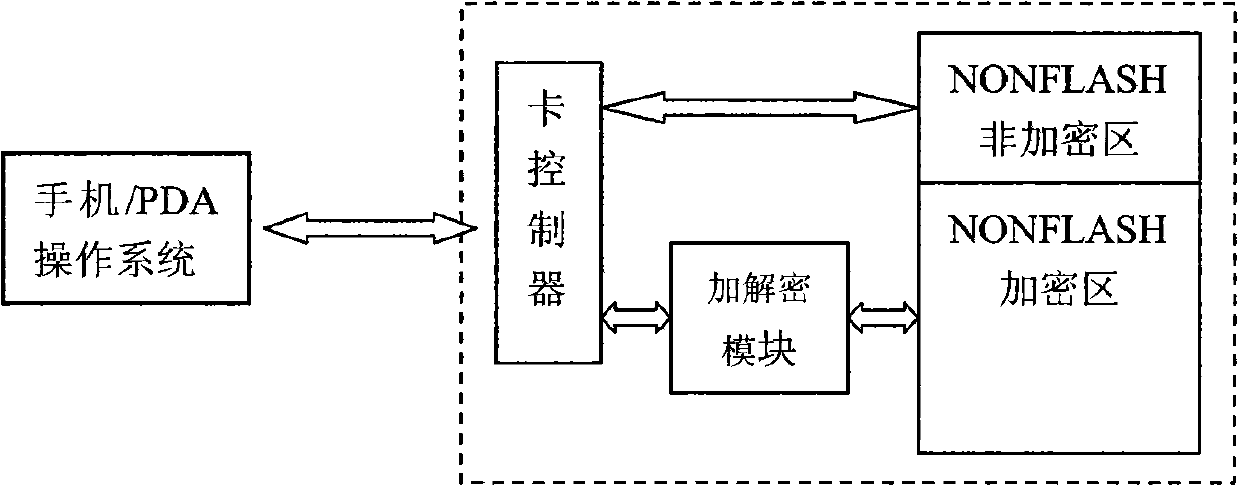
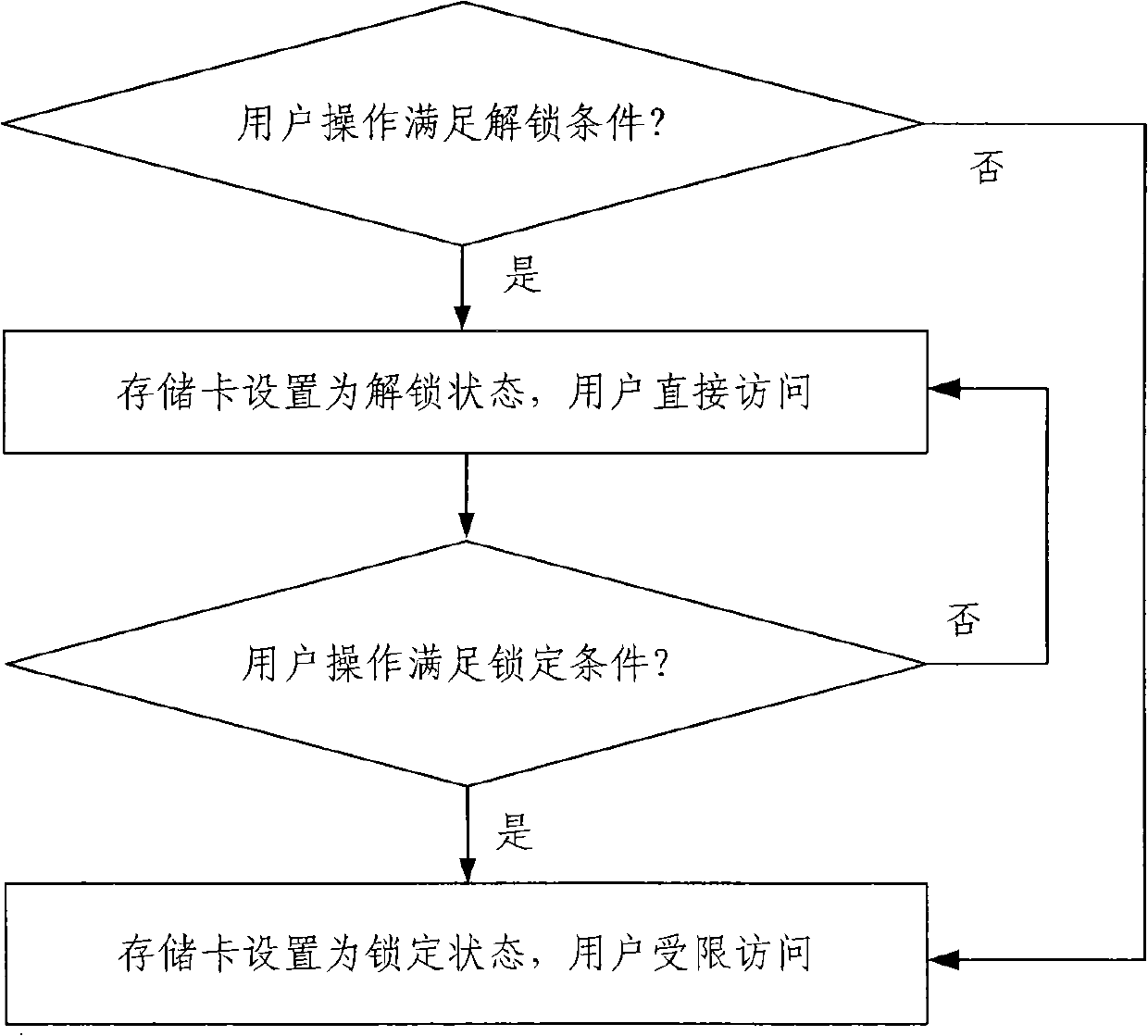
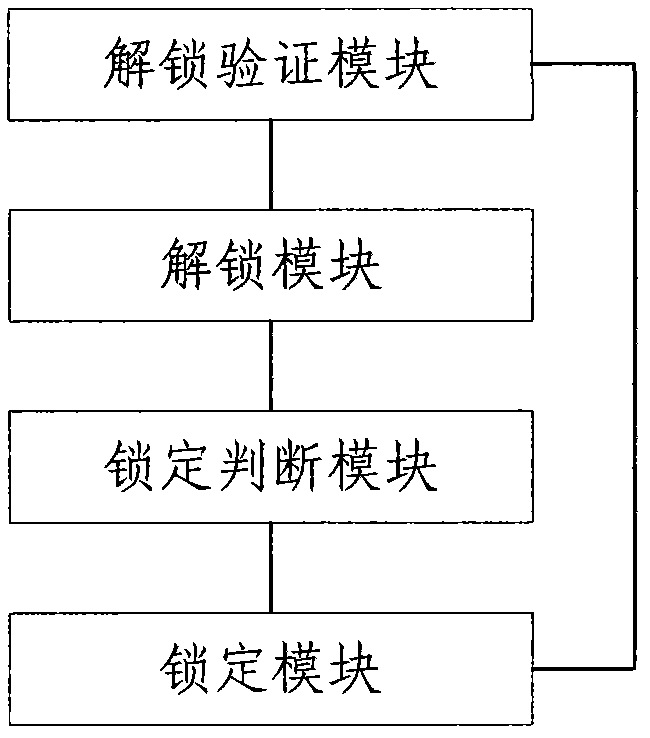
Storage card locking method and system
InactiveCN102646075AFreedom of operationEasy to operateUnauthorized memory use protectionComputer hardwareOperational system
The invention relates to the technical field of content protection of storage cards and discloses a storage card locking method and system. The method comprises the following steps: S1, a user accesses data on a storage card, an operating system uses a universal command to perform operation, a storage card controller intercepts the operation and performs verification, if unlocking conditions are met, the step S2 is implemented, otherwise, the state of the storage card is kept in a locking state; S2, the storage card controller is used for converting the state of the storage card to an unlocking state; S3, the storage card controller is used for judging whether the logic of the operating system against the current operation of the storage card meets the locking conditions, if so, the step S4 is implemented, otherwise, the state of the storage card is kept in the unlocking state; and S4, the storage card controller is used for setting the storage card in the locking state. According to the method disclosed by the invention, the leakage of important data of the storage card can be prevented, the safety is enhanced, and the privacy of the user is protected; and in addition, the universal command is used for verification, thus the operation of the system is facilitated and the compatibility is ensured.
Owner:兰宦泽 +2
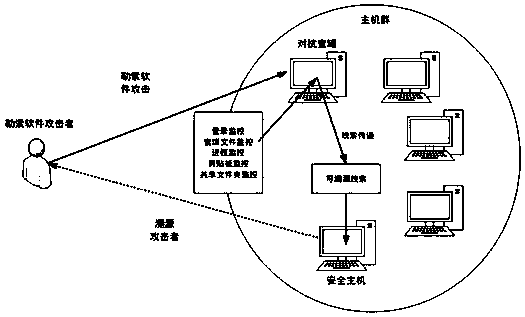
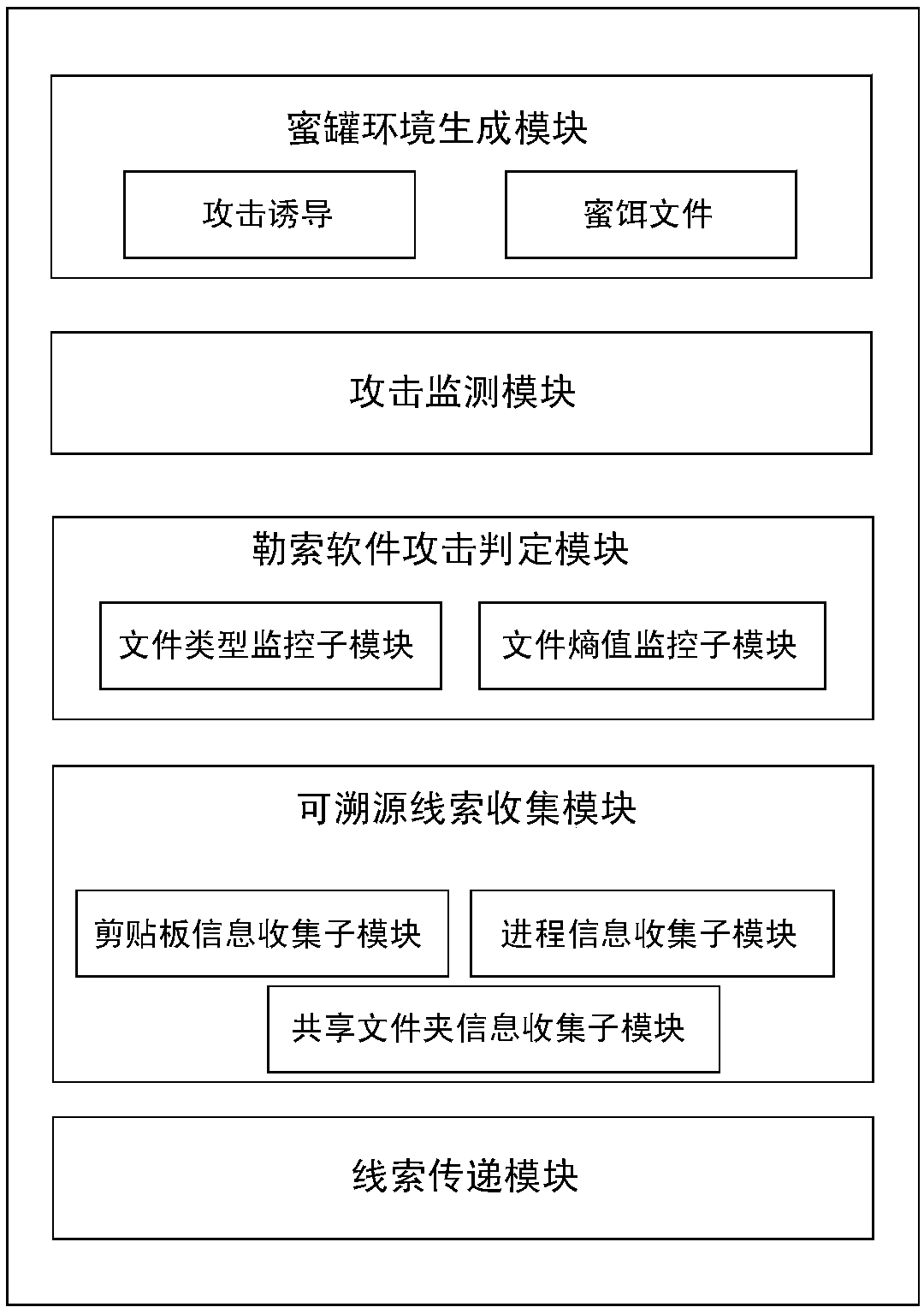
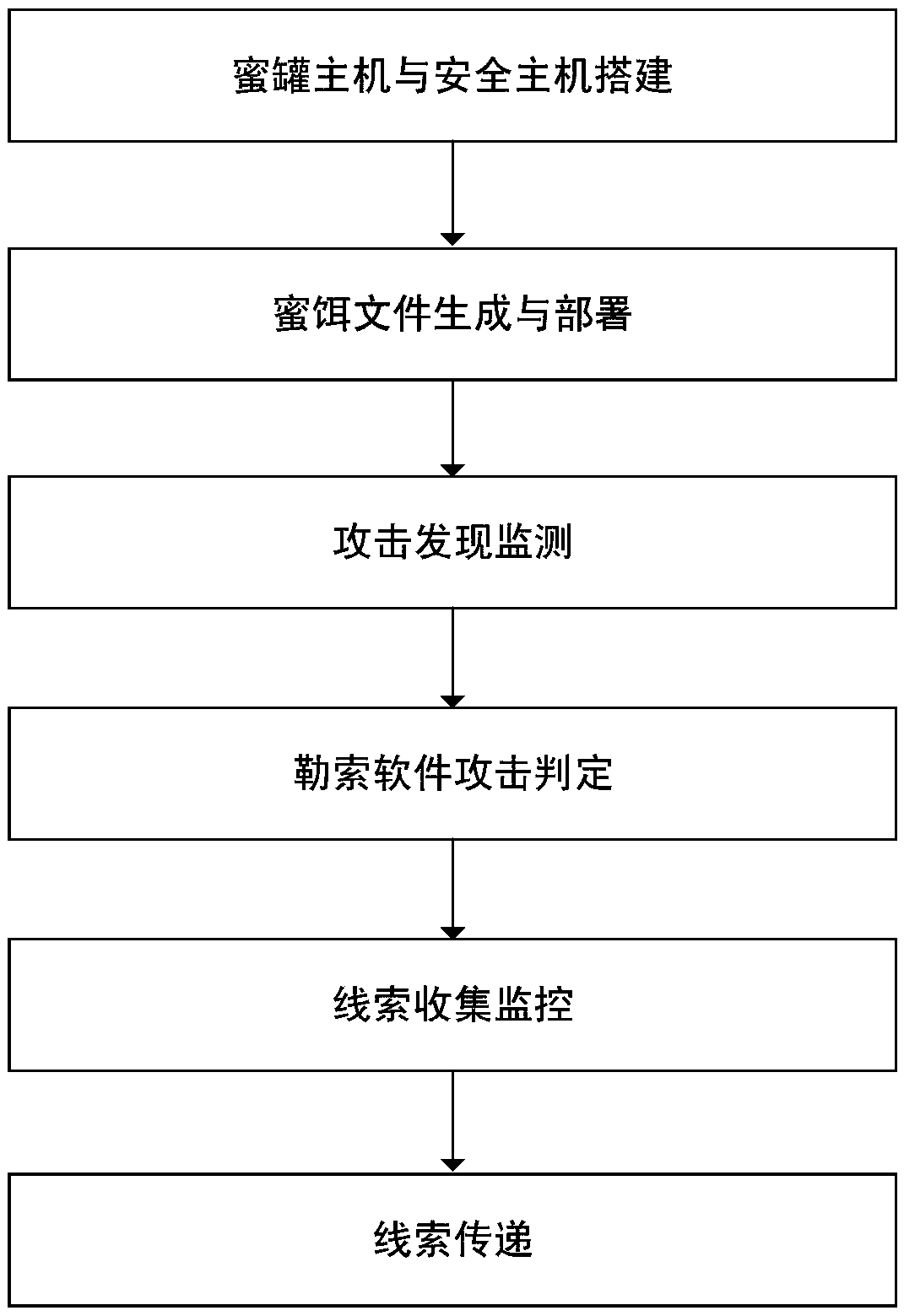
Method and system for resisting ransomware attacks based on host honeypot
The invention relates to a method and a system for resisting ransomware attacks based on a host honeypot. The method comprises steps of: 1) building a host honeypot environment in a host group; 2) generating and deploying a honey bait file in the host honeypot, and recording the initial file type and the entropy value state thereof; 3) monitoring the remote login state of the host honeypot, and notifying the host honeypot to start a real-time monitoring behavior, when the system detects that a remote login operation occurs; 4) monitoring the file type and the entropy value information of the honey bait file, and determining ransomware attacks when both the file type and the entropy value have abnormal changes; 5) collecting the traceable information of an attacker host, when the host honeypot detects the ransomware attacks; and 6) sending traceable information of the collected attacker host to a secure host as a traceable clue. According to the method and the system for resisting ransomware attacks based on the host honeypot, the method and the system can protect the data and property security of users and enterprises, by deceiving attackers and defending against ransomware attacksunder conditions of a low consumption and a zero loss.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
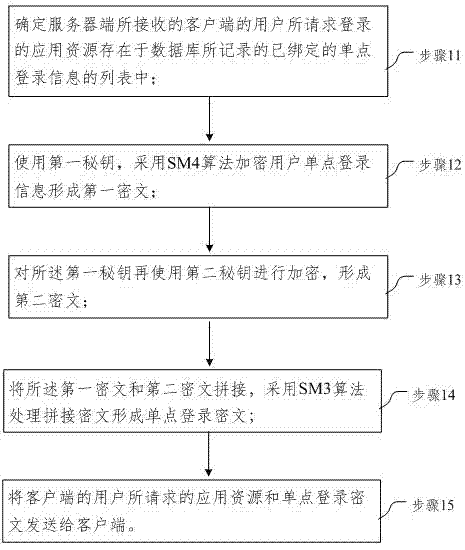
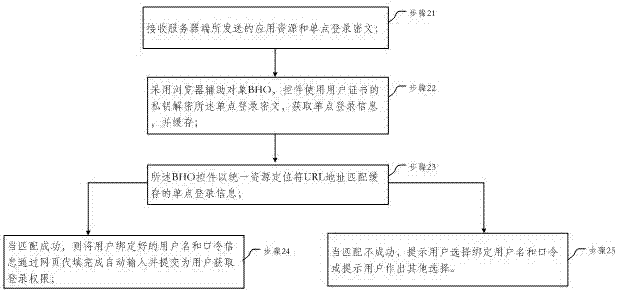
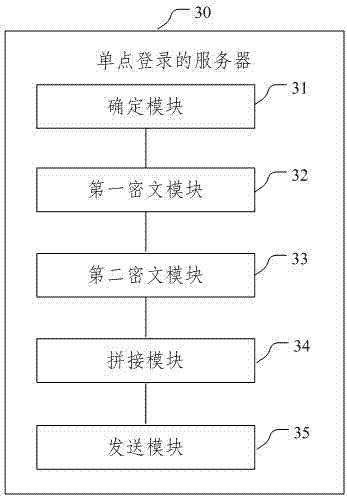
Single sign-on method, server and client
InactiveCN106936759AProtect data securityImprove user experienceTransmissionClient-sideData security
The embodiment of the invention provides a single sign-on method, server and client. In the embodiment of the invention, the method comprises the following steps: determining that application resources on which a user of a client requests to sign received by a server side exist in a list of bound single sign-on information recorded in a database; encrypting single sign-on information of the user by a first key through an SM4 algorithm to form a first ciphertext; encrypting the first key with a second key to form a second ciphertext; splicing the first ciphertext and the second ciphertext, and processing a spliced ciphertext through an SM3 algorithm to form a single sign-on ciphertext; and transmitting the application resources requested by the user of the client and the single sign-on ciphertext to the client. Through adoption of the single sign-on method, server and client, data security is protected through a GMB algorithm; the identity of the user is identified by taking a digital certificate as a carrier; uniform authentication is realized; a plurality of independent application systems can be used in single sign-on; and the user experience is improved.
Owner:AEROSPACE INFORMATION
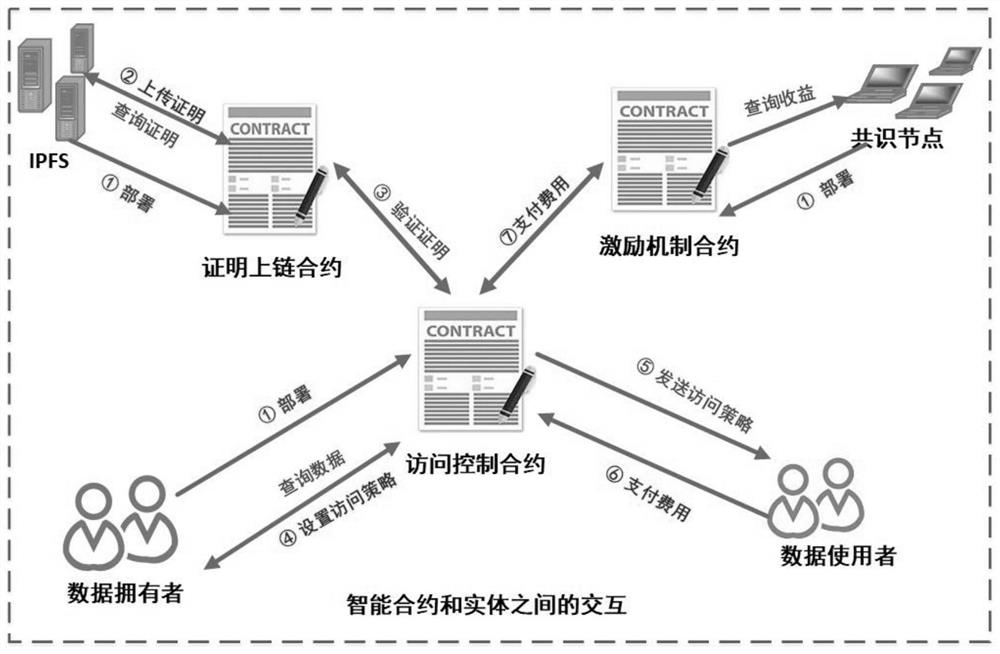
Medical data sharing system based on blockchain smart contract
PendingCN111916172ARealize reasonable allocation and maximize utilizationAchieving Efficient AvailabilityDigital data information retrievalDigital data protectionSafe storageEngineering
The invention relates to the technical field of block chains, and discloses a medical data sharing system based on an IPFS (Internet Protocol File System) and an alliance chain, which comprises a block chain system configured with block chain core service modules and respectively used as peers to organize and form the block chain system, in hospitals and data service companies, ACC and ISC are configured; the patient client is used for sharing the medical data of the patient in the ACC and setting the access permission and incentive cost corresponding to the medical data when accessing the blockchain core service module configured in the hospital; and the data user client is used for querying the target medical data and the corresponding access permission through the ACC when accessing theblockchain core service module configured by the data service company. According to the invention, safe storage and sharing of medical data and authorization management in the sharing process are realized.
Owner:ANHUI NORMAL UNIV
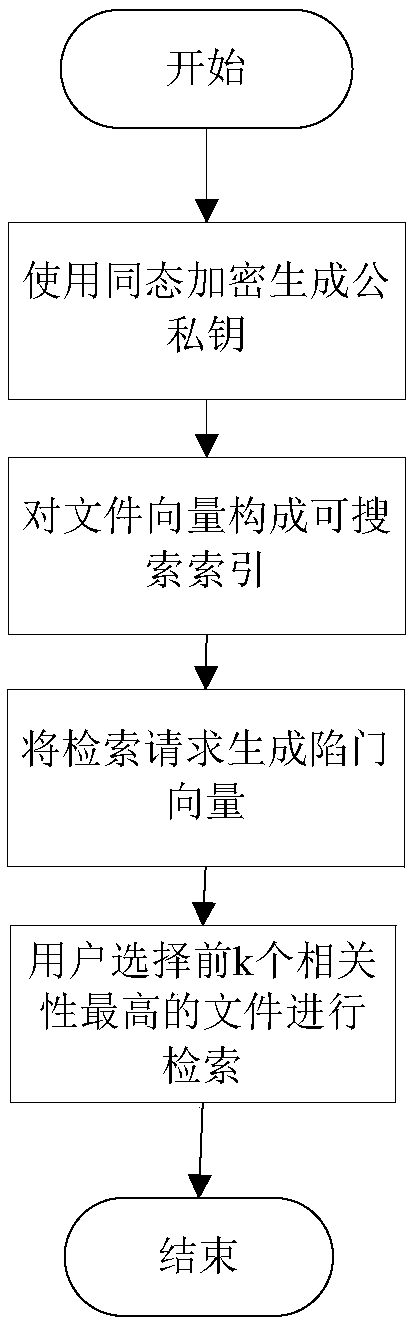
Ciphertext multi-keyword grading security retrieval method
InactiveCN107704768AProtect query privacyImprove securityPublic key for secure communicationDigital data protectionCiphertextUser privacy
The invention discloses a ciphertext multi-keyword grading security retrieval method. A ciphertext file set and indexes uploaded by a data owner in a cloud storage server are subjected to grading retrieval. A data user sends a retrieval request to generate a trap door vector; the data owner enables the trap door vector to form a security trap door vector by using a homomorphic encryption algorithmand uploads the security trap door vector to the cloud storage server; the authorized data user can obtain a decryption key and calculate a ciphertext of a trap door and a security index inner product for the cloud storage server; an encrypted correlation score sequence is returned and is decrypted and sorted; first k file identifiers with highest correlation scores are selected to be sent to thecloud storage server; and finally most correlated files are returned to the data user through the cloud storage server. According to the method, the problem of user privacy and data security in a cloud environment is solved; the communication overhead is reduced; and the ciphertext retrieval problem is solved.
Owner:SHANGHAI MARITIME UNIVERSITY
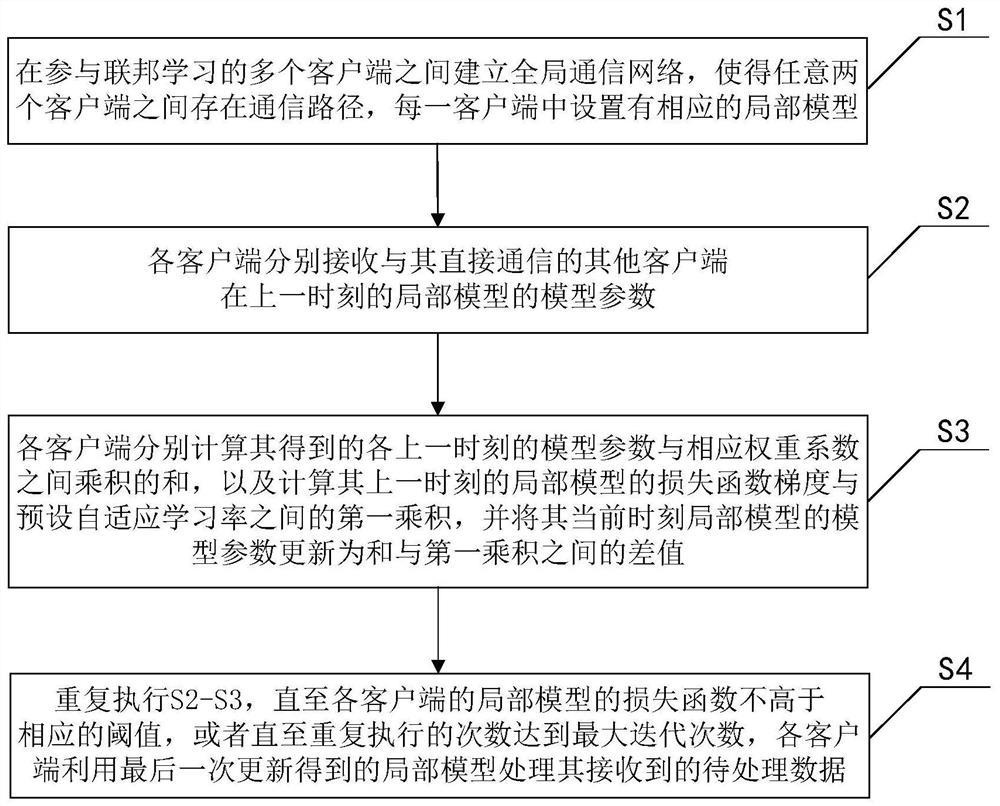
Decentralized federated learning method, device and system
ActiveCN113645197AProtect privacy and securityProtect data securityMachine learningData switching networksEngineeringData mining
The invention discloses a decentralized federated learning method, device and system, and belongs to the field of federated learning, and the method comprises the steps: building a global communication network among a plurality of clients participating in federated learning, and enabling a communication path to exist between any two clients; each client respectively receiving the model parameters of other clients directly communicating with the client at the previous moment, respectively calculating the sum of the products of the obtained model parameters at the previous moment and the corresponding weight coefficients, and calculating the first product of the loss function gradient of the local model at the previous moment and a preset adaptive learning rate; updating a model parameter at the current moment to a difference value between the model parameter and the first product; and repeatedly executing the iteration updating operation until the loss function of the local model of each client is not higher than the corresponding threshold value, or until the number of times of repeated execution reaches the maximum number of iterations. While privacy and data security of each client are protected, each local model is globally trained.
Owner:HUAZHONG UNIV OF SCI & TECH
Data processing method and device, computer equipment and storage medium
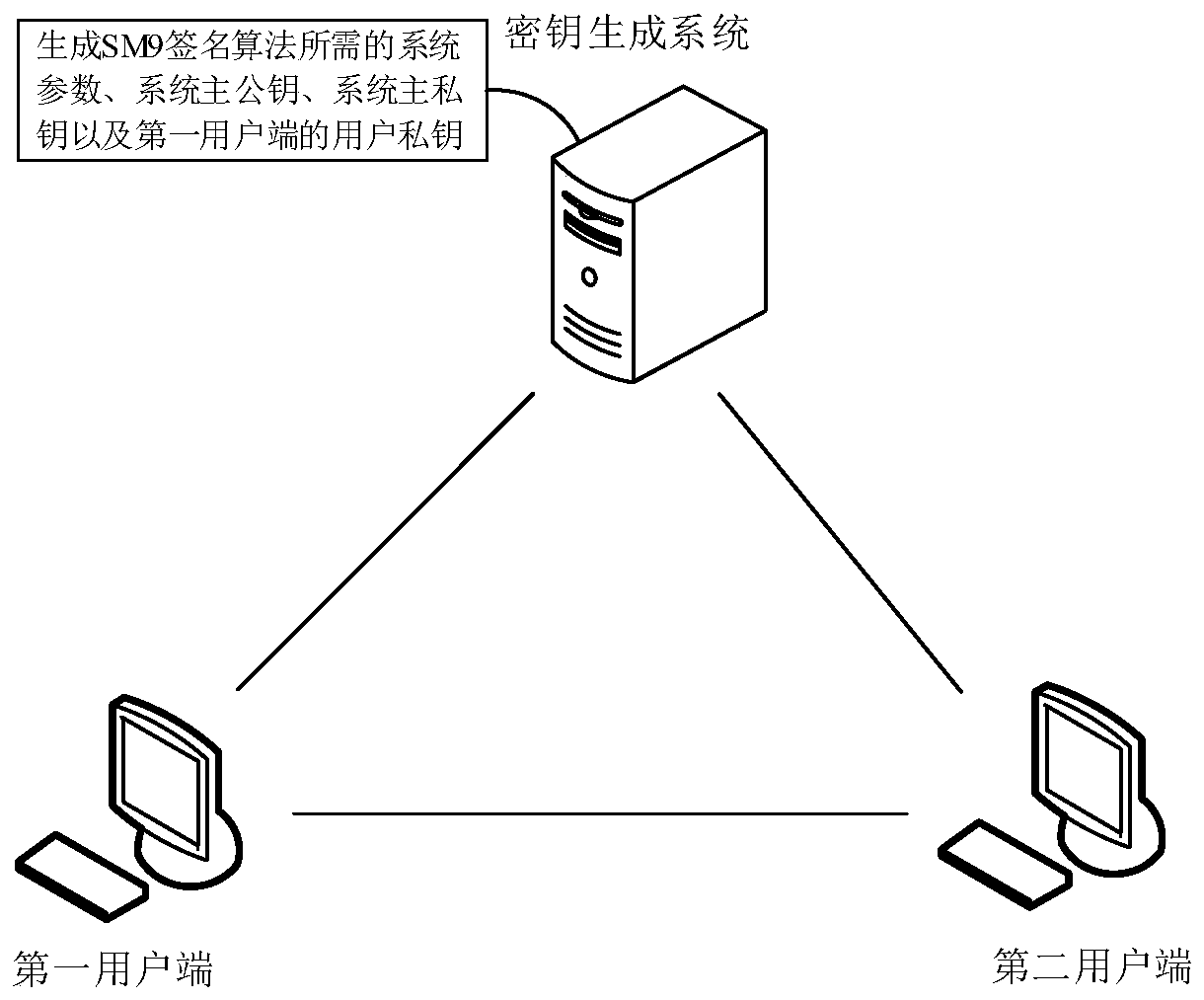
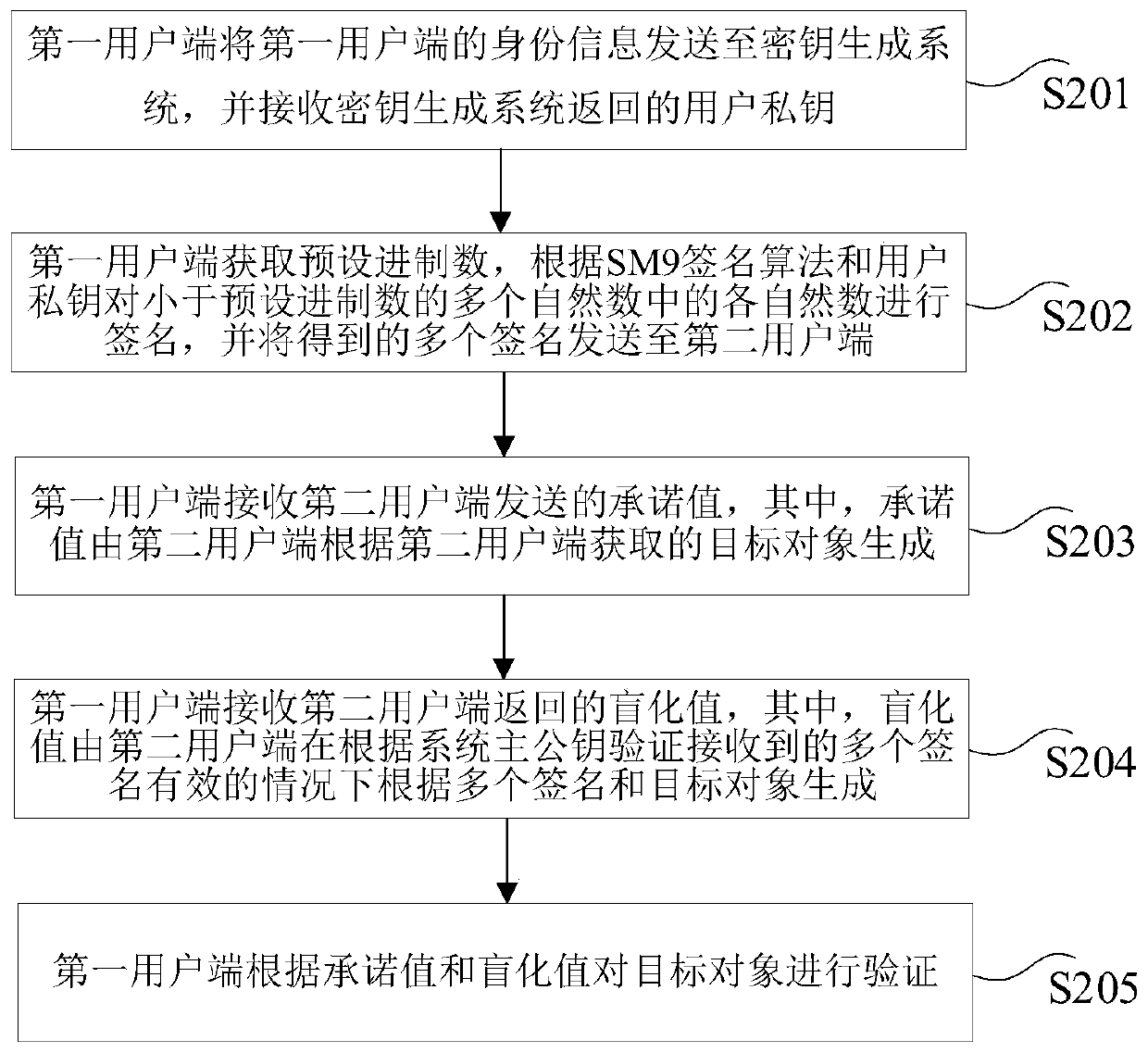
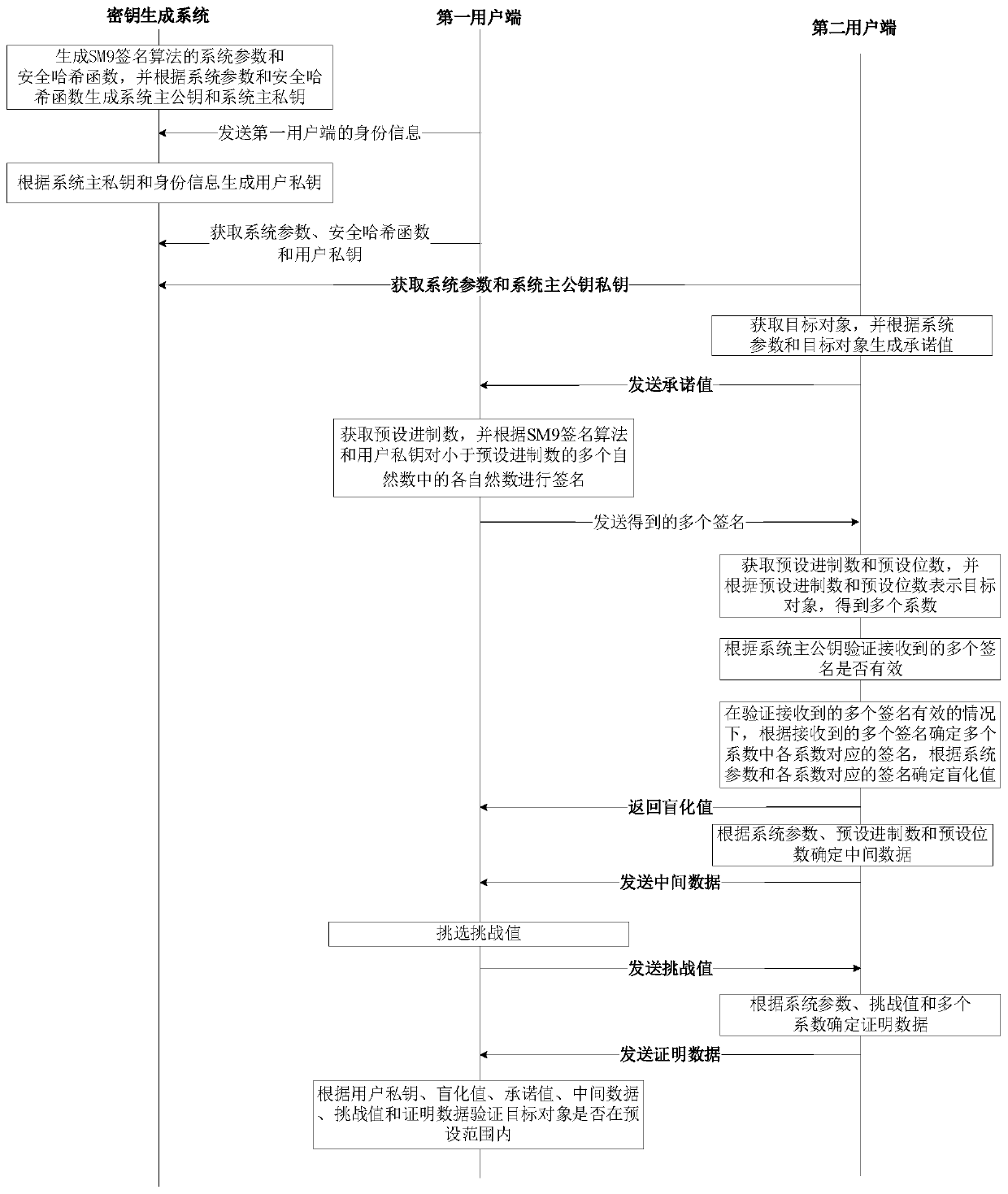
ActiveCN110311776AAvoid administrative overheadReduce verification costsKey distribution for secure communicationEncryption apparatus with shift registers/memoriesKey generationComputer equipment
The invention provides a data processing method and device, computer equipment and a storage medium, and the method comprises the steps: sending the identity information of a first user side to a keygeneration system, receiving a user private key returned by the key generation system, wherein the key generation system generates the user private key according to the identity information and a system main private key; obtaining a preset system number, signing each natural number which is smaller than the preset system number according to an SM9 signature algorithm and a user private key, and sending the obtained signatures to a second user side; receiving a commitment value sent by a second user side, the commitment value being generated by the second user side according to the target object; receiving a blind value returned by the second user side, the blind value being generated by the second user side according to the plurality of signatures and the target object, and the system mainpublic key being generated by the key generation system; and verifying the target object according to the commitment value and the blind value. According to the scheme, high certificate management expenditure is avoided, and the cost is effectively reduced.
Owner:JUZIX TECH SHENZHEN CO LTD +1
Method and device for safely sharing user data
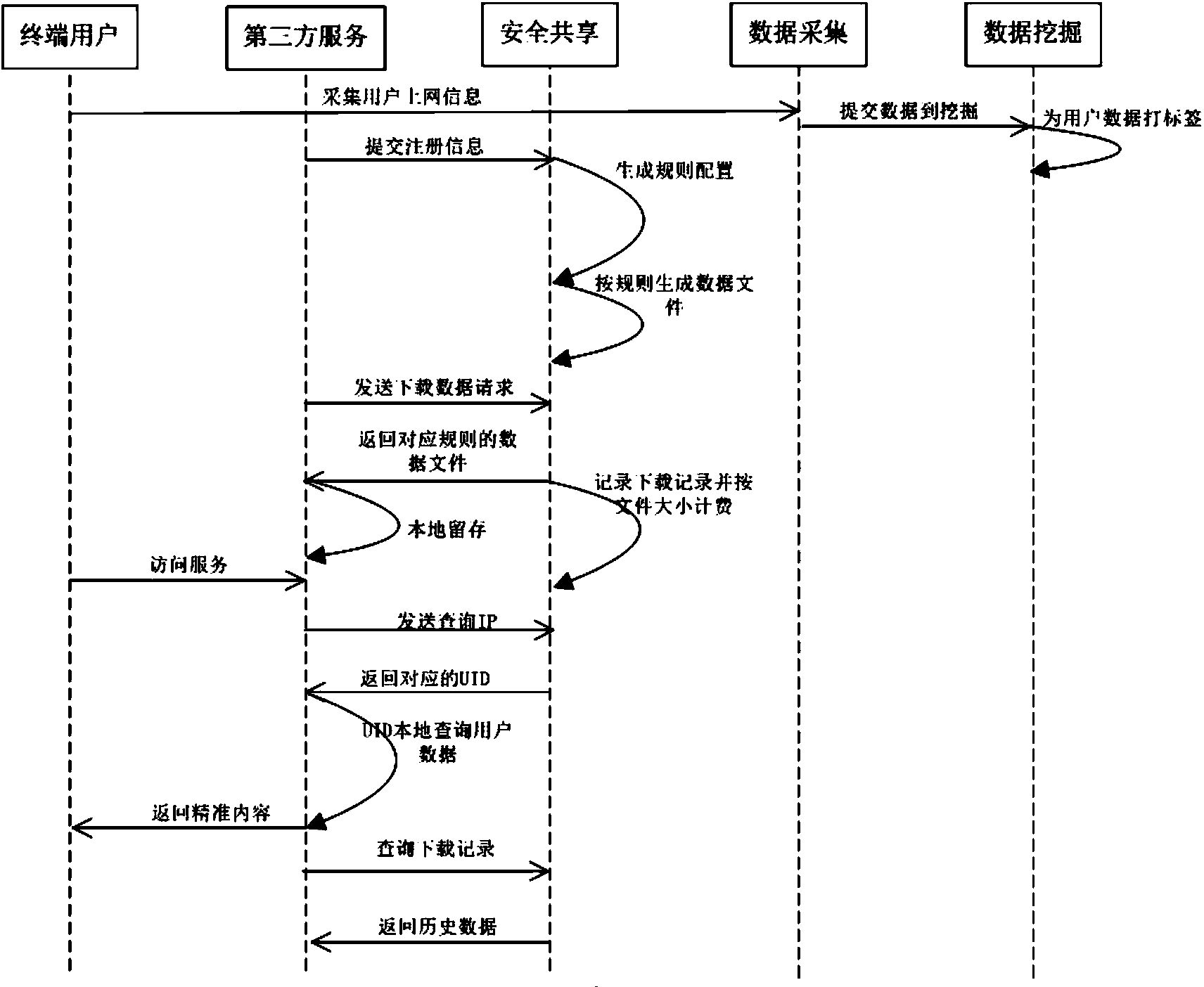
ActiveCN103780690AProtect privacy and securityProtect data securityTransmissionSpecial data processing applicationsPlaintextThird party
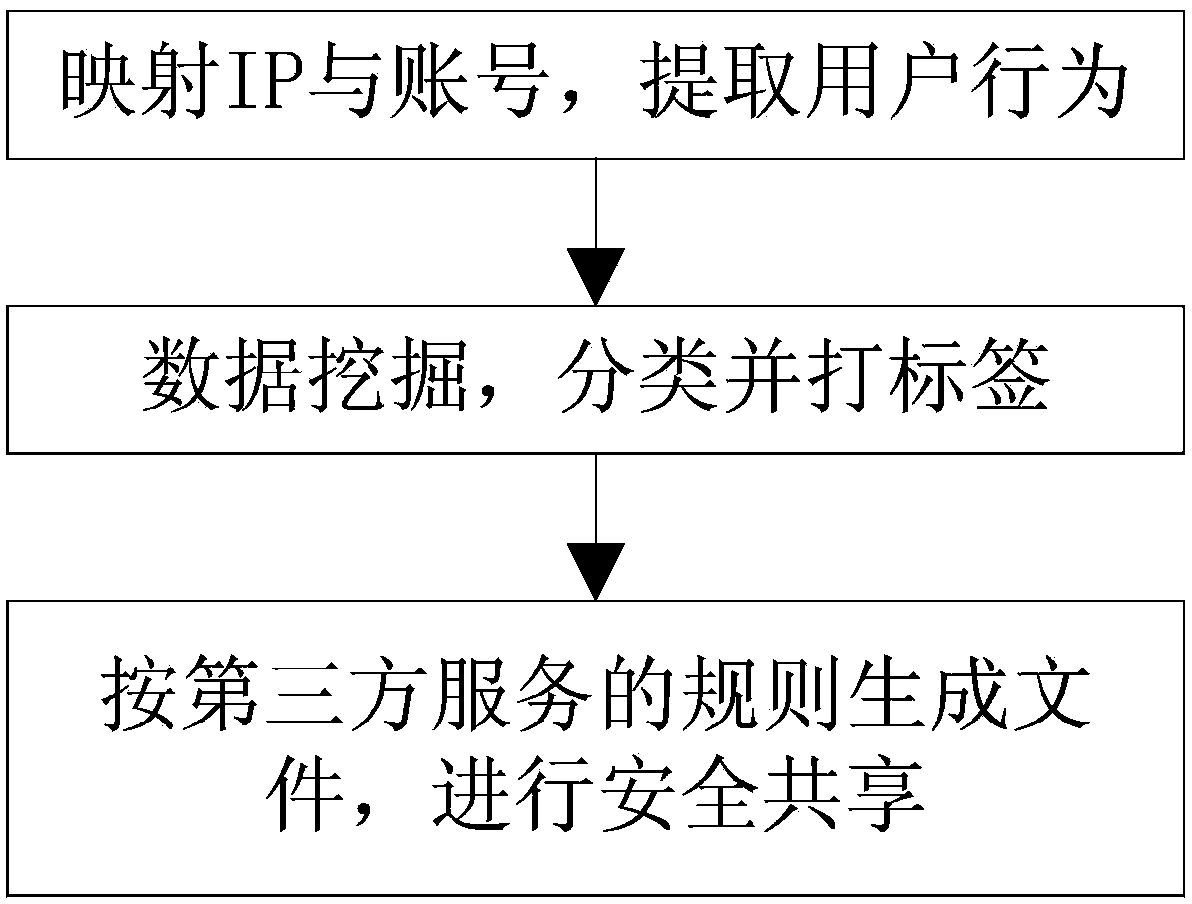
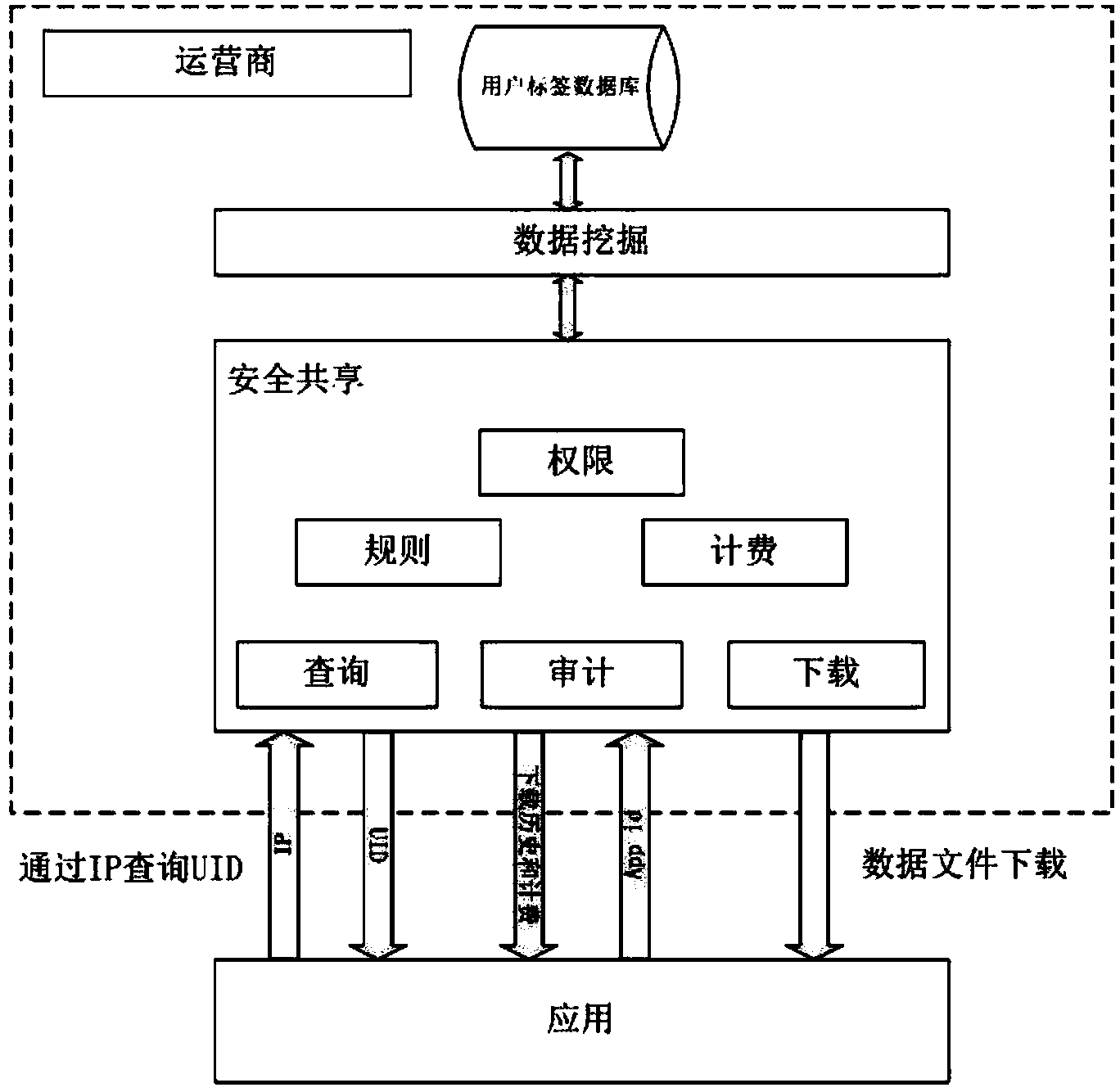
The invention relates to the technical field of Internet application, and provides a method and device for safely sharing user data. The method includes the steps that the IP of a terminal user and an encrypted Internet account are mapped, and real-time network access behaviors of the user are continuously extracted; access behavior data of the user are mined, classified, labeled, and then stored in a coded form; data files which meet a rule are generated for a third party service according to configuration of the rule of the third party service, and the third party service downloads the data files within limits of authority of the third party service after being authorized. The data are mined and processed for the service on the side of a service supplier, plaintexts of the user data do not need to be directly provided, and therefore privacy of the user and data safety are protected.
Owner:GEO POLYMERIZATION (BEIJING) ARTIFICIAL INTELLIGENCE TECH CO LTD
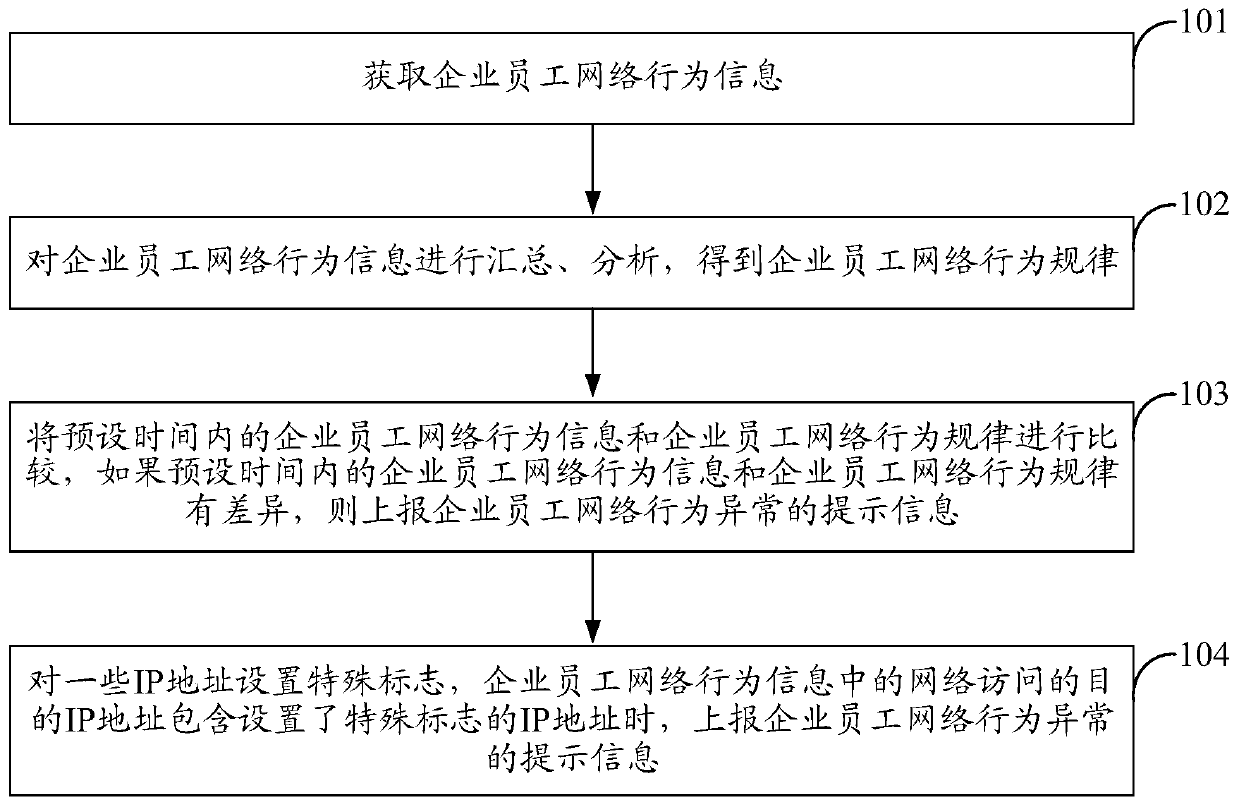
Data access exception monitoring method and device
ActiveCN111343173AProtect data securityProtection securityCharacter and pattern recognitionTransmissionInformation accessBusiness enterprise
The invention provides an exception monitoring method and device for data access and a storage medium. The method comprises the steps of receiving a data access request for a target employee, whereinthe data access request is used for requesting to access target resource data corresponding to a target service in an enterprise management system; based on the data access request, access informationincluding an access permission bit is determined, and the access permission bit is used for identifying an access permission corresponding to the target resource data; predicting a job role of the target employee through a role classification model based on the access information; obtaining a job role of the target employee in the enterprise management system; matching the predicted job role withthe job role of the target employee in the enterprise management system to obtain a matching result; and when the matching result represents that the predicted job role is different from the job roleof the target employee in the enterprise management system, returning prompt information of refusing the data access request. According to the invention, the accuracy of exception monitoring of dataaccess can be improved.
Owner:TENCENT CLOUD COMPUTING BEIJING CO LTD
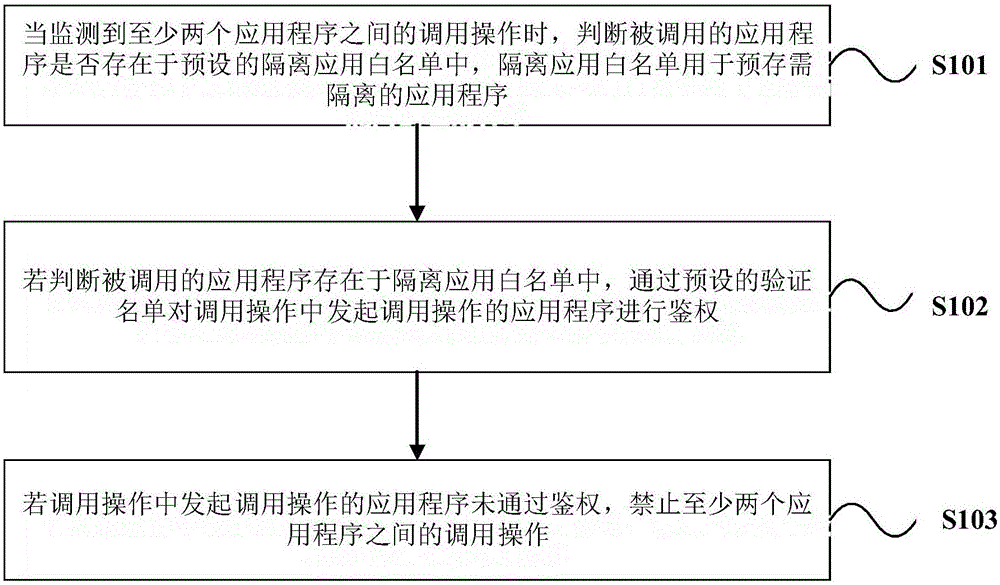
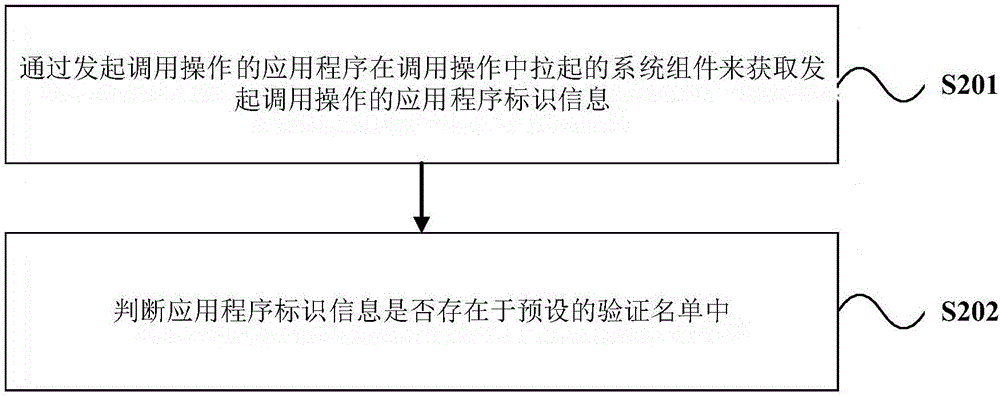
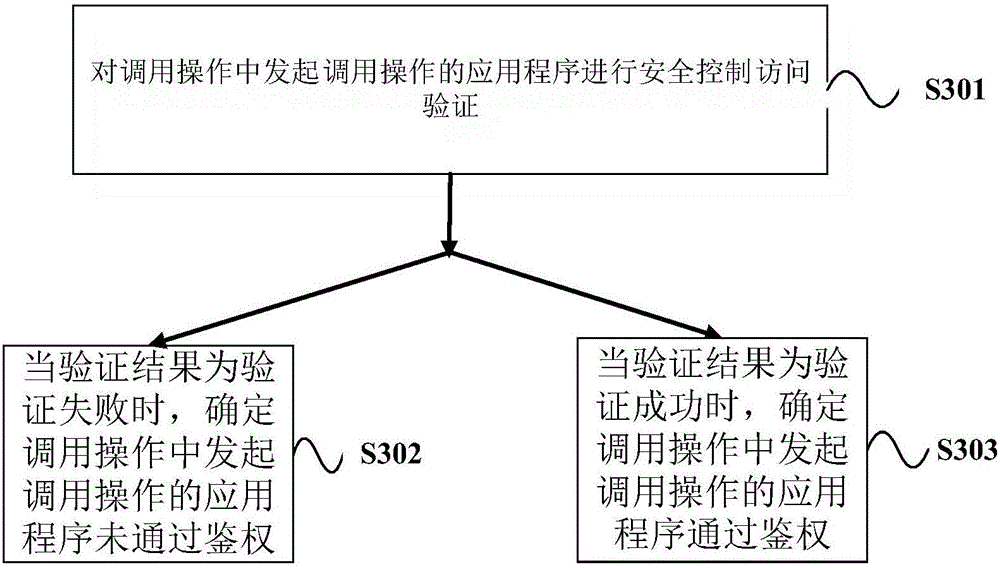
Method and device for controlling the application calls
InactiveCN106778228AProtection securityProtect data securityDigital data authenticationWhitelistApplication software
The invention provides a method and device for controlling the application calls. The method includes that when call operation between at least two applications is monitored, whether the called applications are on the predetermined isolation application white list is judged. The predetermined isolation application white list is applied to stored applications required isolation. If the called applications are on the predetermined isolation application white list, authentication undergoes to the application that initiates calls in the call operation according to the predetermined verification list. If the application that initiates calls in the call operation fails the authentication, the call operations between at least two applications are prohibited. The technical scheme of the method and device for controlling the application calls prevents malicious applications from intercepting the call operation and coverage displays the self-designing malicious user interface on the top of the application's interface based on the call operation to cheat the user and therefore the purpose of stealing the user's property data and private data is achieved.
Owner:BEIJING ANYUNSHIJI TECH CO LTD
Intelligent resource allocation method in mobile blockchain
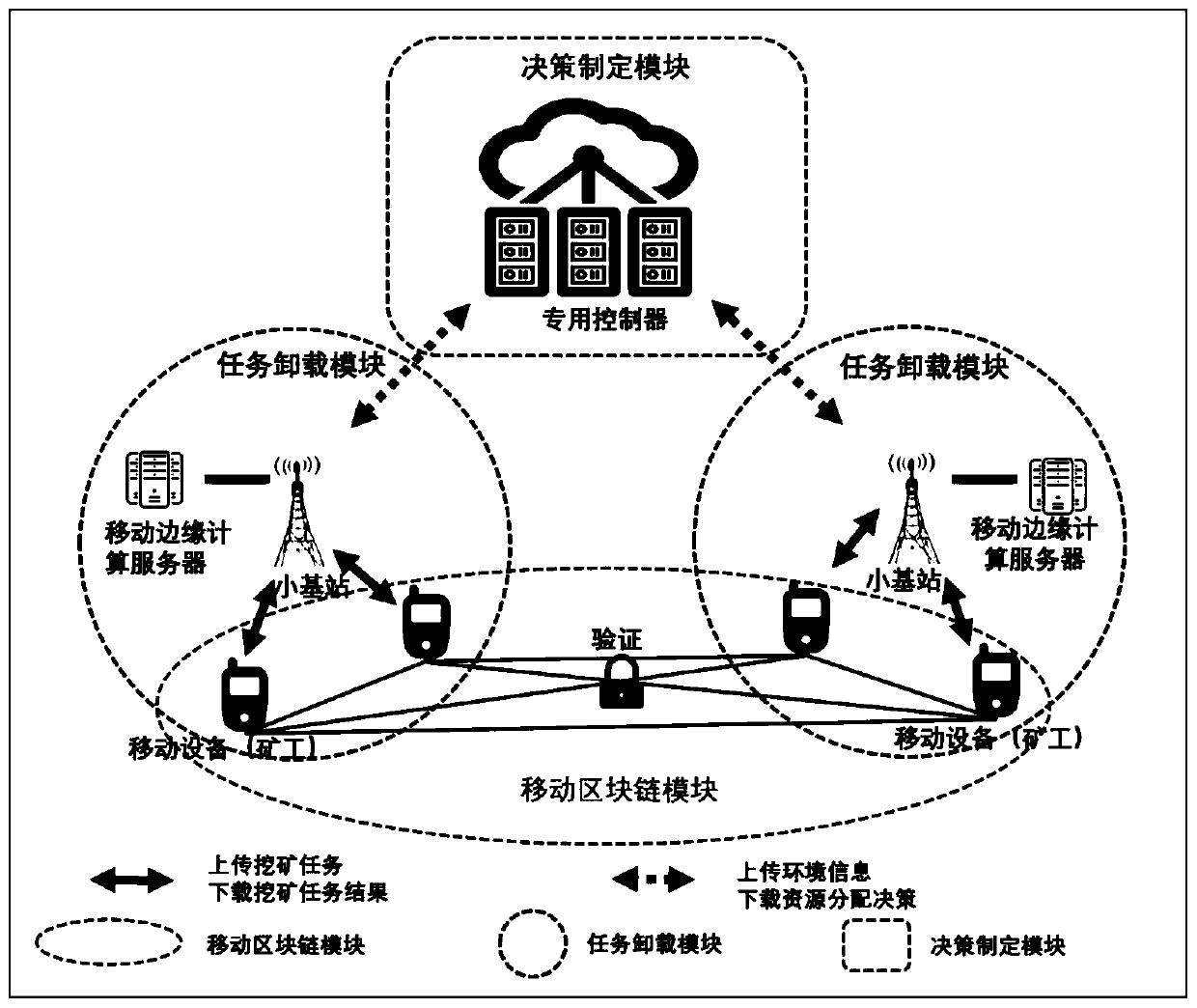
PendingCN111565420AProtect privacy and securityProtect data securityNetwork traffic/resource managementArtificial lifeEngineeringIndustrial Internet
The invention belongs to the technical field of industrial Internet of Things, and discloses an intelligent resource allocation method in a mobile blockchain. Specifically, the method comprises the steps: establishing a mobile blockchain framework for protecting privacy and data security of mobile equipment in a transaction process of the mobile equipment through a blockchain and a mobile edge computing technology, wherein the mobile blockchain framework comprises three modules, namely a mobile blockchain module, a task unloading module and a decision making module; modeling the utility of equipment in the system, and establishing a small base station bandwidth and computing power resource joint allocation model; decomposing the joint allocation model into two sub-models, namely a bandwidth allocation sub-model and a computing power allocation sub-model; and designing a deep reinforcement learning and particle swarm optimization combined method to solve the bandwidth allocation sub-model and the computing power allocation sub-model. The invention provides the mobile blockchain framework for protecting privacy and data security of mobile equipment, and provides a new solution for the problem of joint allocation of bandwidth and computing power resources.
Owner:DALIAN UNIV OF TECH
Method for completely removing original information on smart phone
InactiveCN107277089AEasy to deletePrevent leakageSubstation equipmentTransmissionInternet privacyComputer terminal
The invention relates to relates to the technical field of information safety, specifically to a method for completely removing original information on a smart phone. The method includes a control terminal, a server and a smart phone. The control terminal accesses the server to completely remove information on the smart phone. Through the method, a smart phone can quickly be located and searched to conveniently delete the user's information on the smart phone, thereby protecting the personal privacy and the data security, and preventing information leakage.
Owner:DATANG NETWORK CO LTD
Environmental parameter-based server cluster automatic protection system
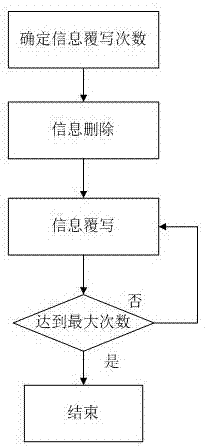
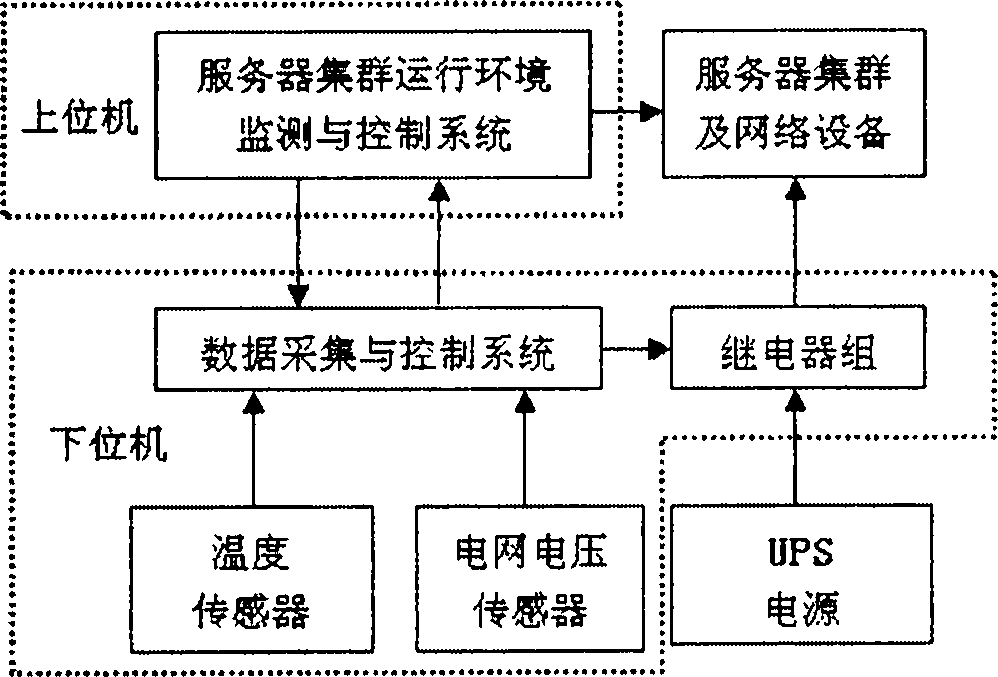
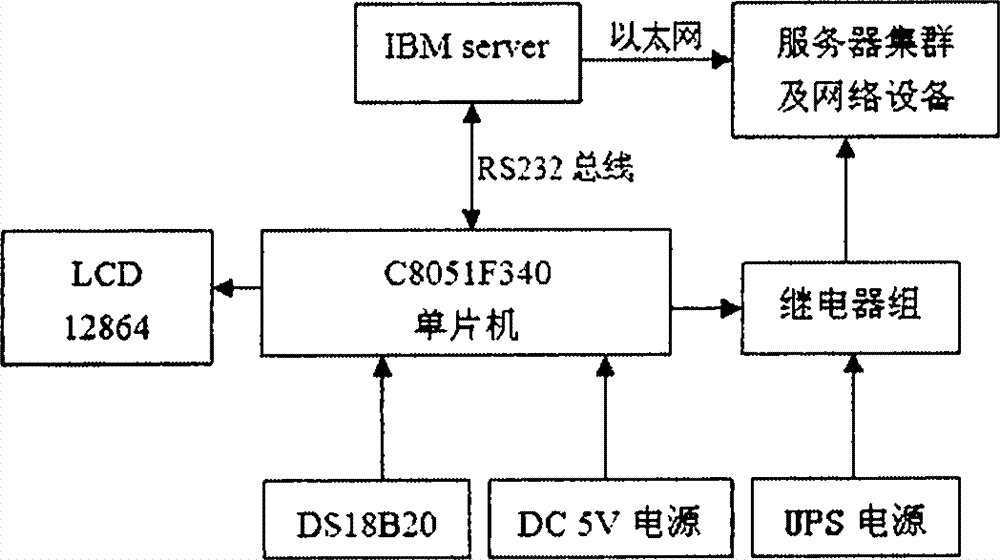
InactiveCN103760838AProtect data securityProtect device securityTotal factory controlProgramme total factory controlControl systemData acquisition
The invention, which belongs to the technical field of server safety, relates to an environmental parameter-based server cluster automatic protection system comprising a lower computer and an upper computer. The lower computer consists of a data acquisition and control system, a temperature sensor, a grid voltage sensor and a relay group; the temperature sensor and the grid voltage sensor and a relay group are connected to the data acquisition and control system; the data acquisition and control system is connected with the relay group; and the relay group uses an uninterrupted power supply (UPS) for power supplying. Besides, the upper computer includes a server cluster operation environment monitoring and control system; the lower computer includes an IBM server; and the upper computer and the lower computer are connected by an RS-232 bus and are connected with the server cluster by the ethernet network. With the protection system, an objective of safety protection of server data and equipment can be achieved; and the workload of the technical management personnel can be substantially reduced.
Owner:NORTHWEST A & F UNIV
Model training system based on separation degree index
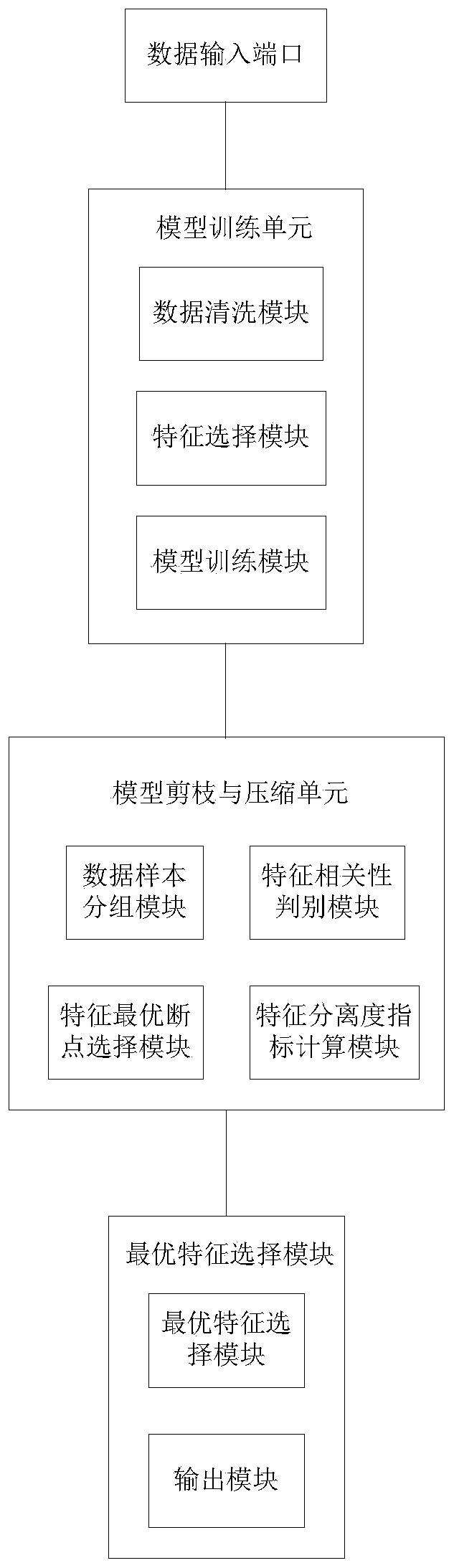
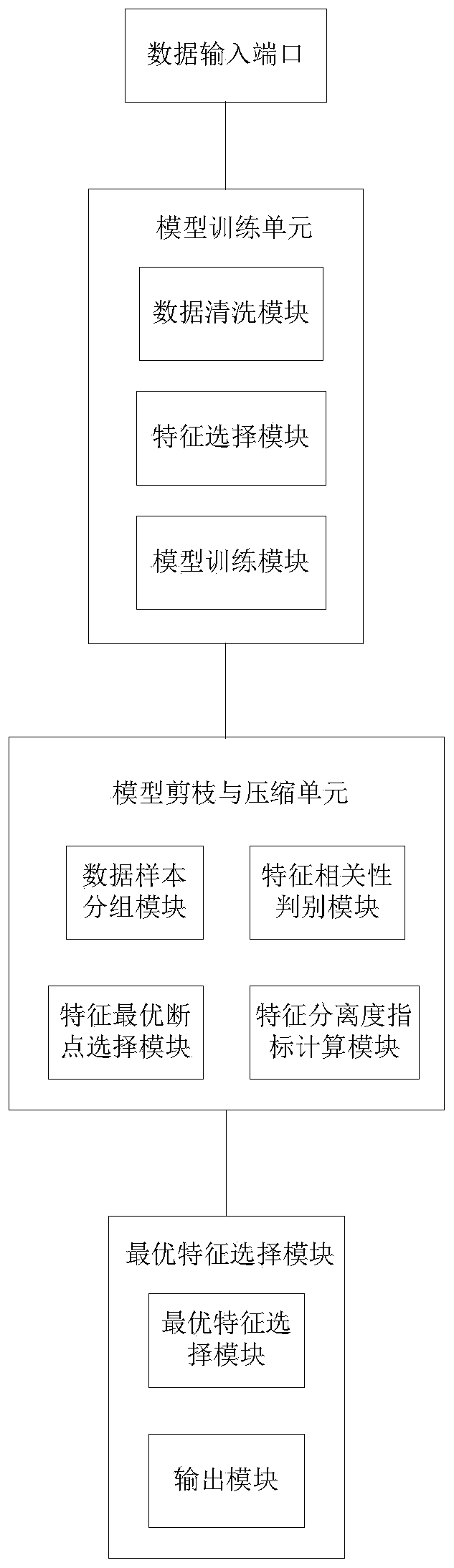
ActiveCN111126627ALow selectivityReduce model sizeMachine learningCorrelation coefficientFeature set
The invention relates to a model training system based on a separation degree index. The model training system comprises a model training unit, a model pruning and compressing unit and an output unit.The model training unit comprises the following modules of: a, data cleaning module for original variable cleaning; b, a feature selection module for screening candidate feature sets compressed by amodel; c, a model training module for model training and optimization. The model pruning and compressing unit comprises the following modules of: d, a data sample grouping module for data sample grouping; e, a feature correlation discrimination module used for calculating correlation coefficients of features and target variables and grouping and sorting samples; f, a feature optimal breakpoint selection module for selecting the optimal breakpoints of the features; g, a feature separation degree index calculation module which constructs feature separation degree indexes and outputs a feature with the best effect. The output unit comprises the following modules of: h, an optimal feature selection module for optimal feature selection; and i, an output module used for outputting a single-pointrule list. According to the method, the established model can be trained under the condition that the data of one party is not transmitted out, so that the data security and customer privacy of two parties are effectively protected.
Owner:SICHUAN XW BANK CO LTD
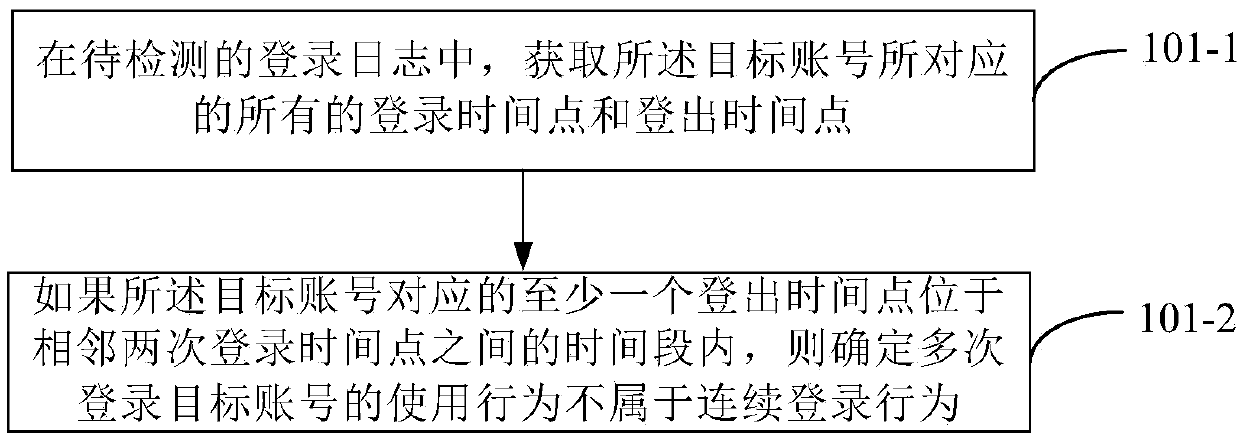
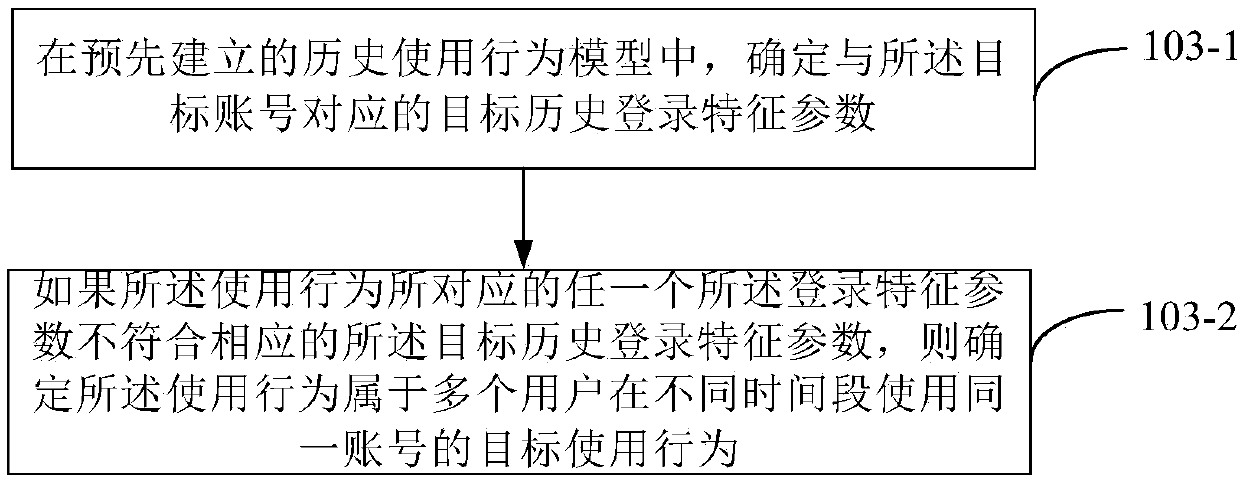
Method and device for detecting account usage behavior
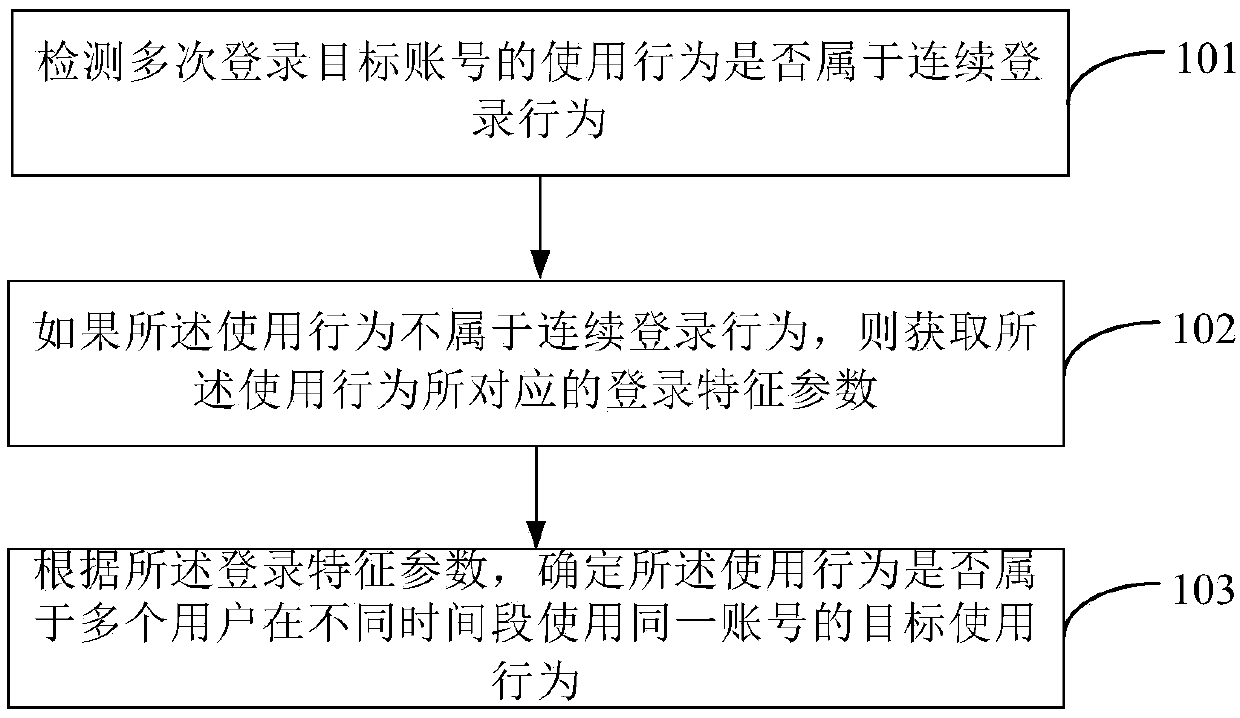
The disclosure provides a method and device for detecting an account usage behavior, wherein the method comprises the following steps: detecting whether a usage behavior of multiple login times of a target account belongs to a continuous login behavior; if the usage behavior does not belong to the continuous login behavior, acquiring login feature parameters corresponding to the usage behavior; and determining, according to the login feature parameters, whether the usage behavior belongs to a target usage behavior of multiple users using the same account at different time periods. The disclosure can more accurately and efficiently detect whether there is a target usage behavior of multiple target users in the data sharing exchange platform using the same account at different time periods,thereby better protecting account security and data security.
Owner:HANGZHOU DT DREAM TECH
Multi-rotor unmanned aerial vehicle carbon tube damping and shock absorption undercarriage
InactiveCN106697269AProtect data securityReduce the risk of crashing and bombingAlighting gearData securityEngineering
Belonging to the technical field of aircrafts, especially to the multi-rotor unmanned aerial vehicle field, the invention relates to a multi-rotor unmanned aerial vehicle carbon tube damping and shock absorption undercarriage, and aims to provide an undercarriage that can optimize multi-rotor unmanned aerial vehicle landing action by a pure mechanical way, correct abnormal landing state, protect whole vehicle and internal data security, and reduce the crash smashing risk. The undercarriage comprises a retracting mechanism, a shaft end, a damping shock absorber, a socket end, and a rubber protective pad. The damping shock absorber is mounted between the shaft end and the socket end, and is mounted in the socket end. The rubber protective pad is fixed at the socket end bottom, and the rubber protective pad can be directly mounted to and disassembled from the socket end in an interference fit way. And the damping shock absorber adopts pneumatic bumper. The undercarriage provided by the invention can absorb the moment pneumatic kinergety generated during unmanned aerial vehicle landing, realizes soft landing of each landing, and prolongs the service life of the whole vehicle.
Owner:天津晓奇科技发展有限公司
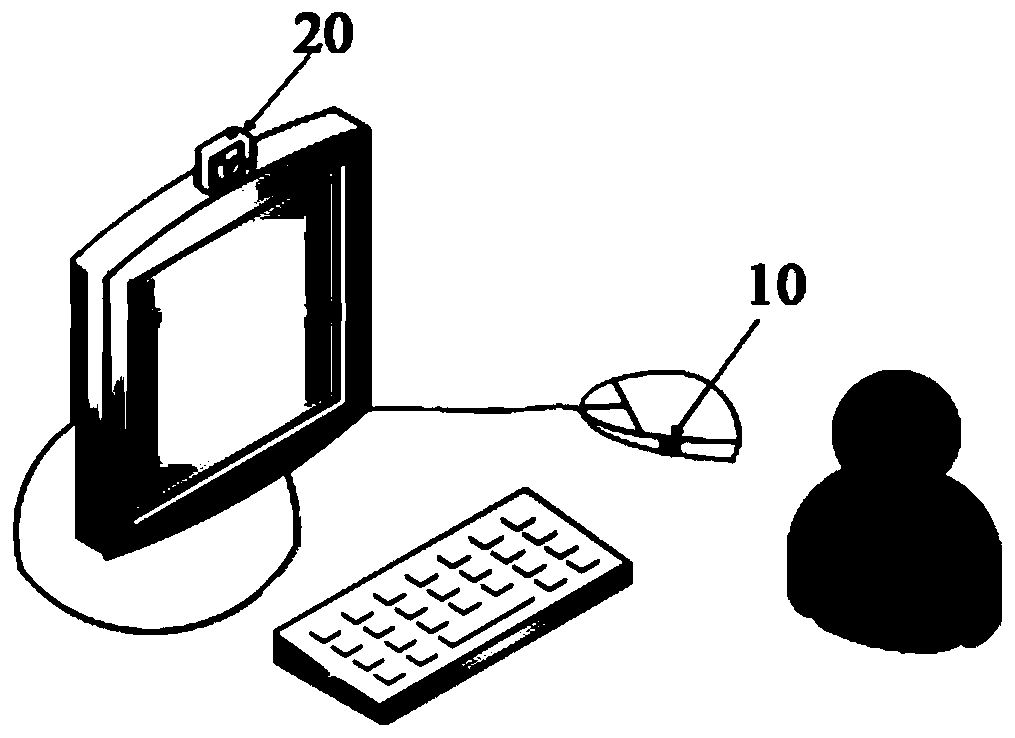
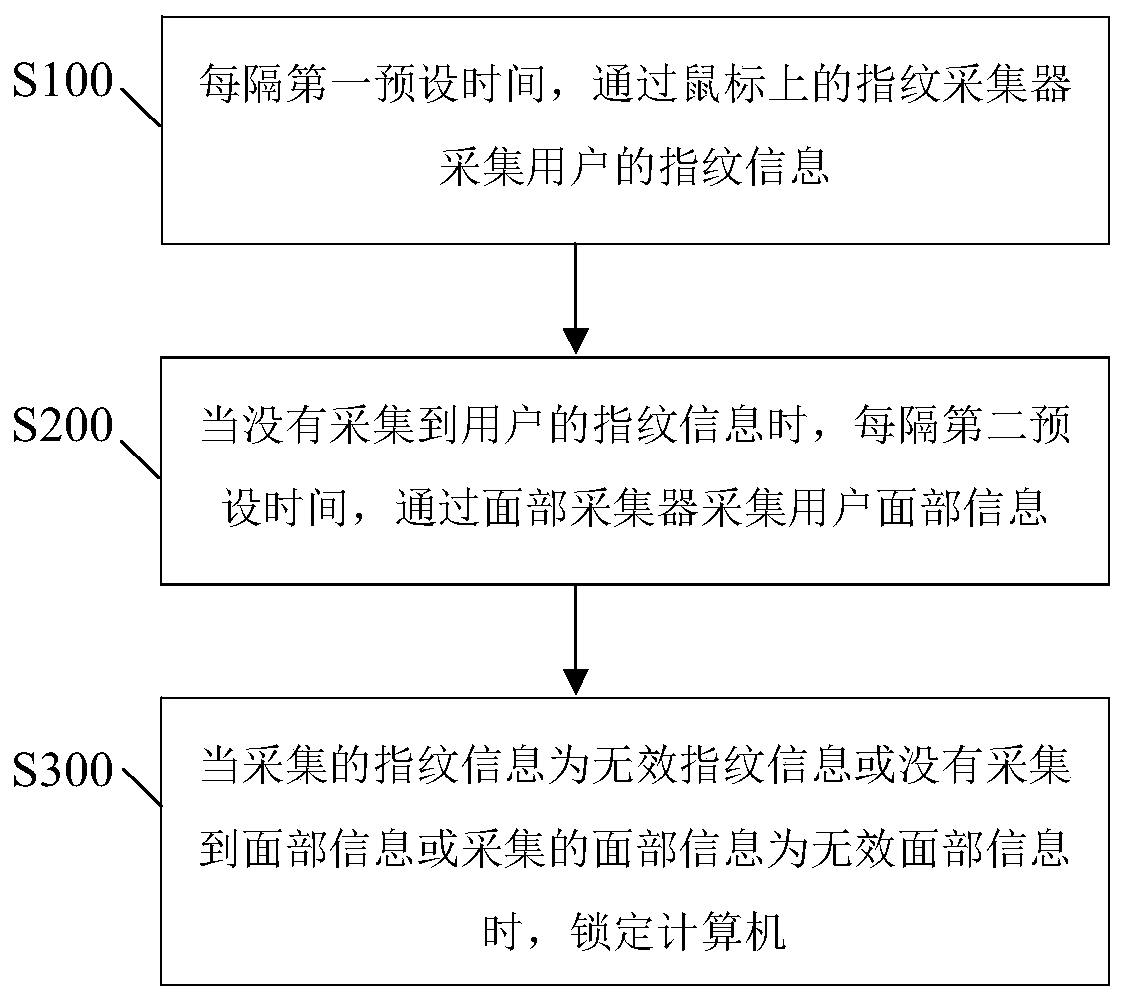
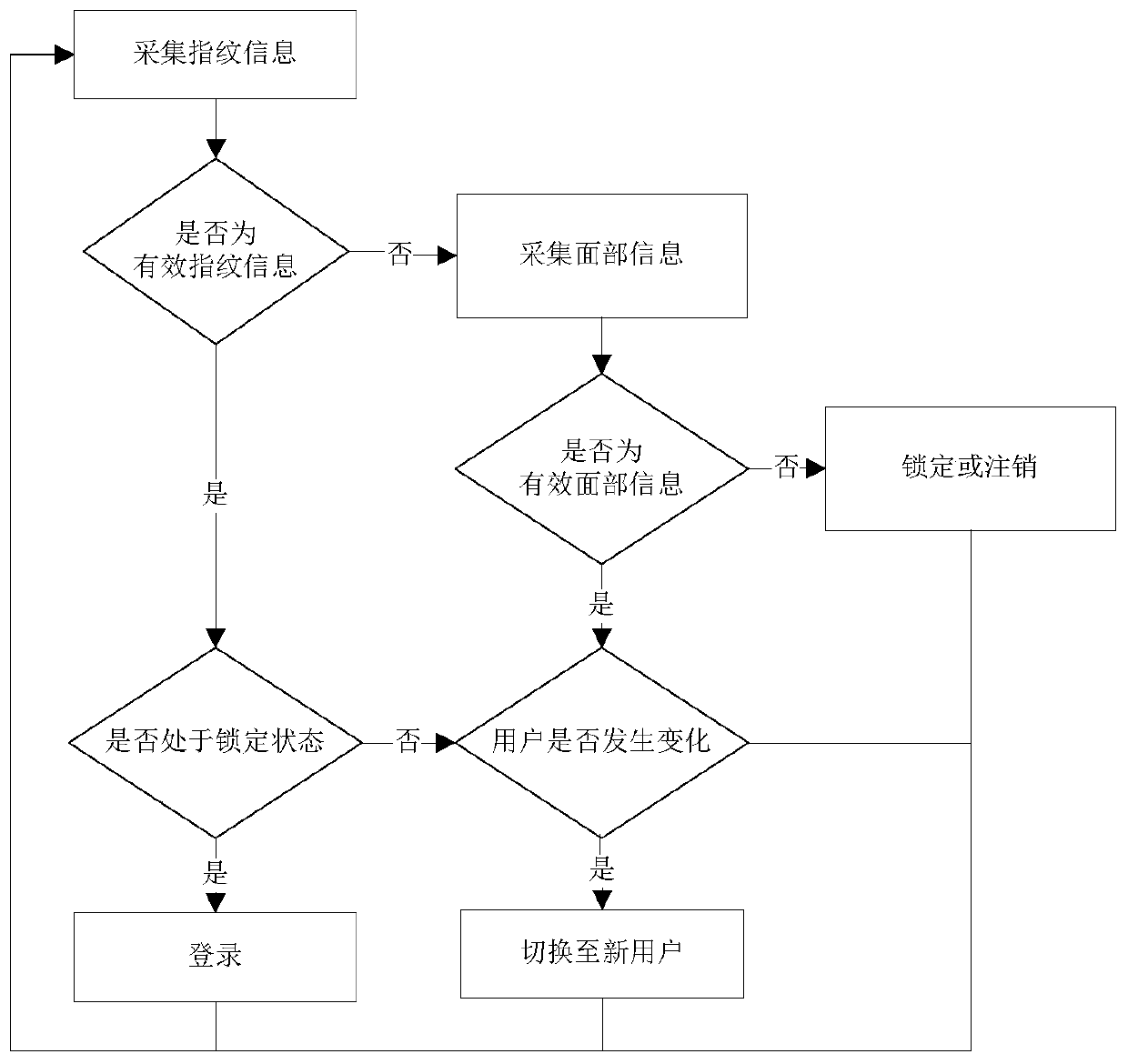
Continuous authentication method based on biological characteristics and system thereof
InactiveCN109933966AGuaranteed non-sensitivityAchieve securityCharacter and pattern recognitionDigital data authenticationUser privacyFingerprint
The invention discloses a continuous authentication method and system based on biological characteristics and a system thereof. The method comprises the following steps: A, fingerprint information ofa user is collected through a fingerprint collector on a mouse every other first preset time; B, when the fingerprint information of the user is not collected, collecting user face information througha face collector at an interval of second preset time; and C, when the collected fingerprint information is invalid fingerprint information or the face information is not collected or the collected face information is invalid face information, locking the computer. Continuous authentication is carried out in a comprehensive authentication mode that fingerprint authentication is mainly carried outand fingerprint authentication and face authentication are combined, the computer is locked after authentication fails, safety can be achieved, and user privacy and data safety are protected.
Owner:NAT UNIV OF DEFENSE TECH
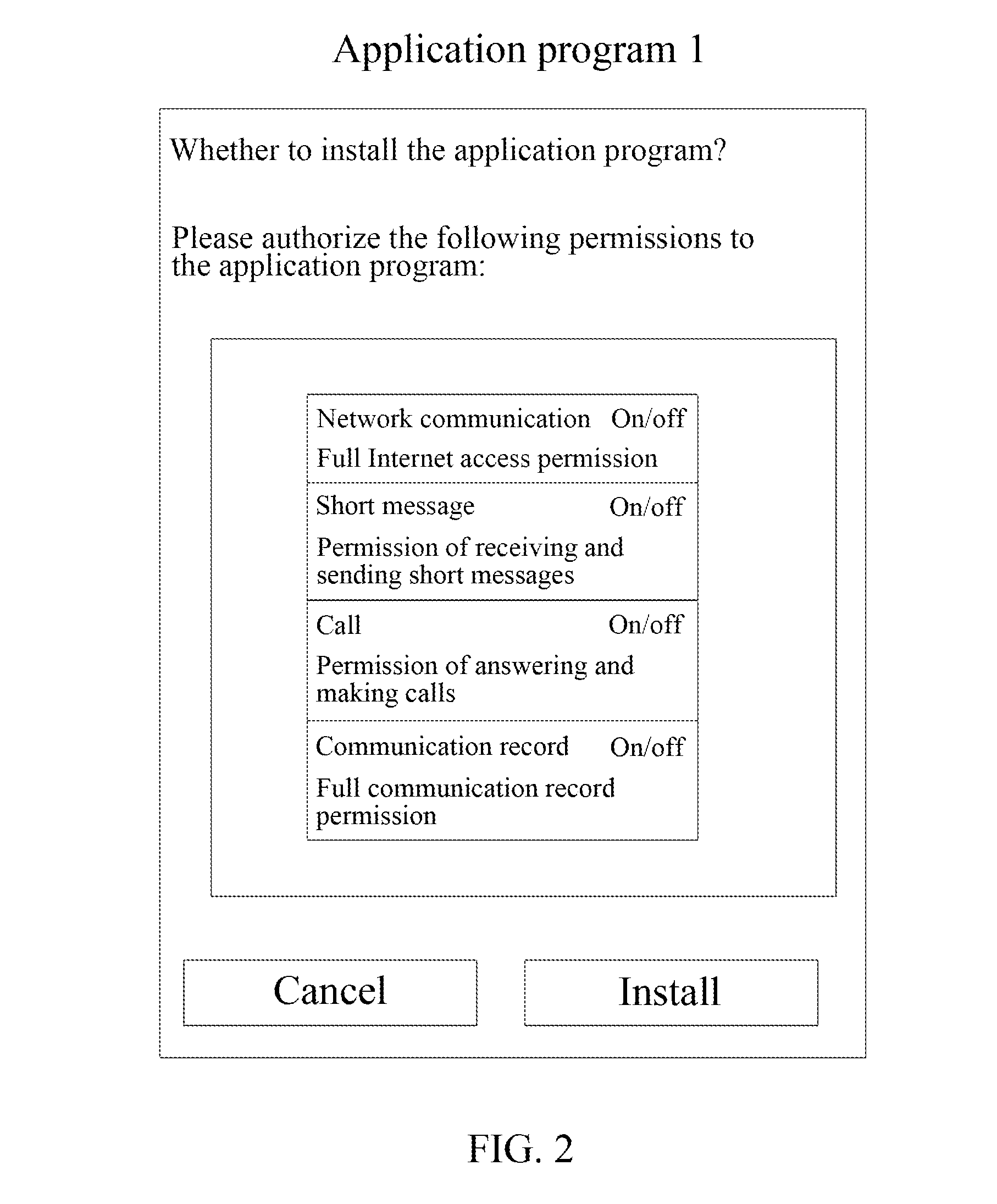
Application Program Management Method, Device, Terminal, and Computer Storage Medium
InactiveUS20160350525A1Protect data securityProtect the charging processDigital data authenticationProgram loading/initiatingProgram managementComputer terminal
Disclosed in an embodiment of the present document are an application program management method and an application program management device, a terminal and a computer storage medium, wherein the method includes: acquiring a list of permissions declared by an application program, and displaying an interface indicating whether individual permissions in the list of permissions are granted to the application program; and according to the acquired operations on the interface, identifying whether the individual permissions in the list of permissions are granted to the application program in a permission control table.
Owner:ZTE CORP
Key level-to-level management method and device for federated learning and privacy calculation
ActiveCN114499866AProtection securityPrivacy protectionKey distribution for secure communicationPublic key for secure communicationEngineeringData science
The invention relates to a secret key level-to-level management method and device for federated learning and privacy calculation. In various applications in the technical fields of federated learning and privacy computing, the method and the device prevent the secret key from being leaked and overcome the problem of secret key loss caused by factors such as restart, meanwhile, various feasible external resources can be utilized, data security and privacy information can be protected, cost is reduced, and deployment time is shortened.
Owner:CLUSTAR TECH LO LTD
Data-encrypting method and decrypting method for a mobile phone
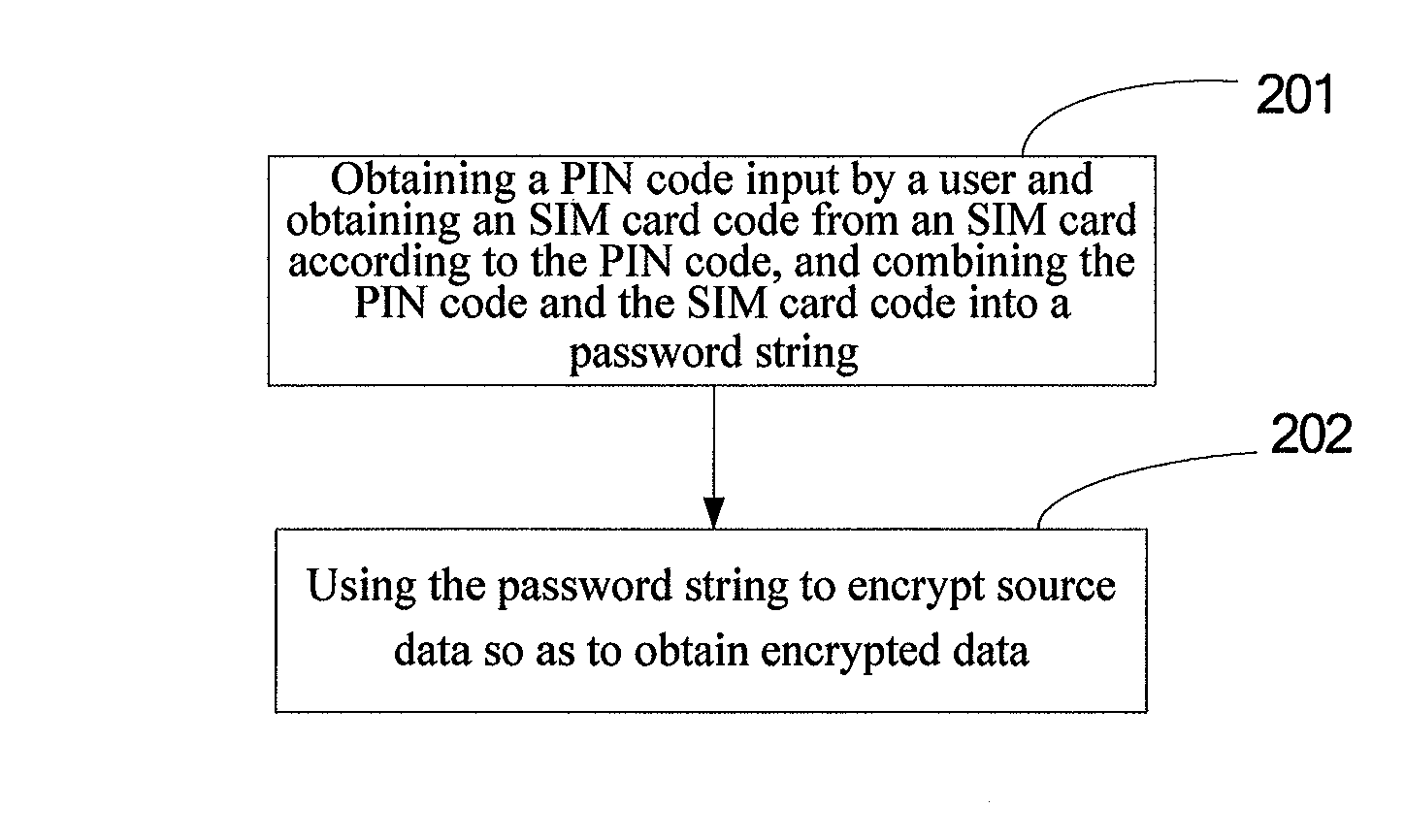
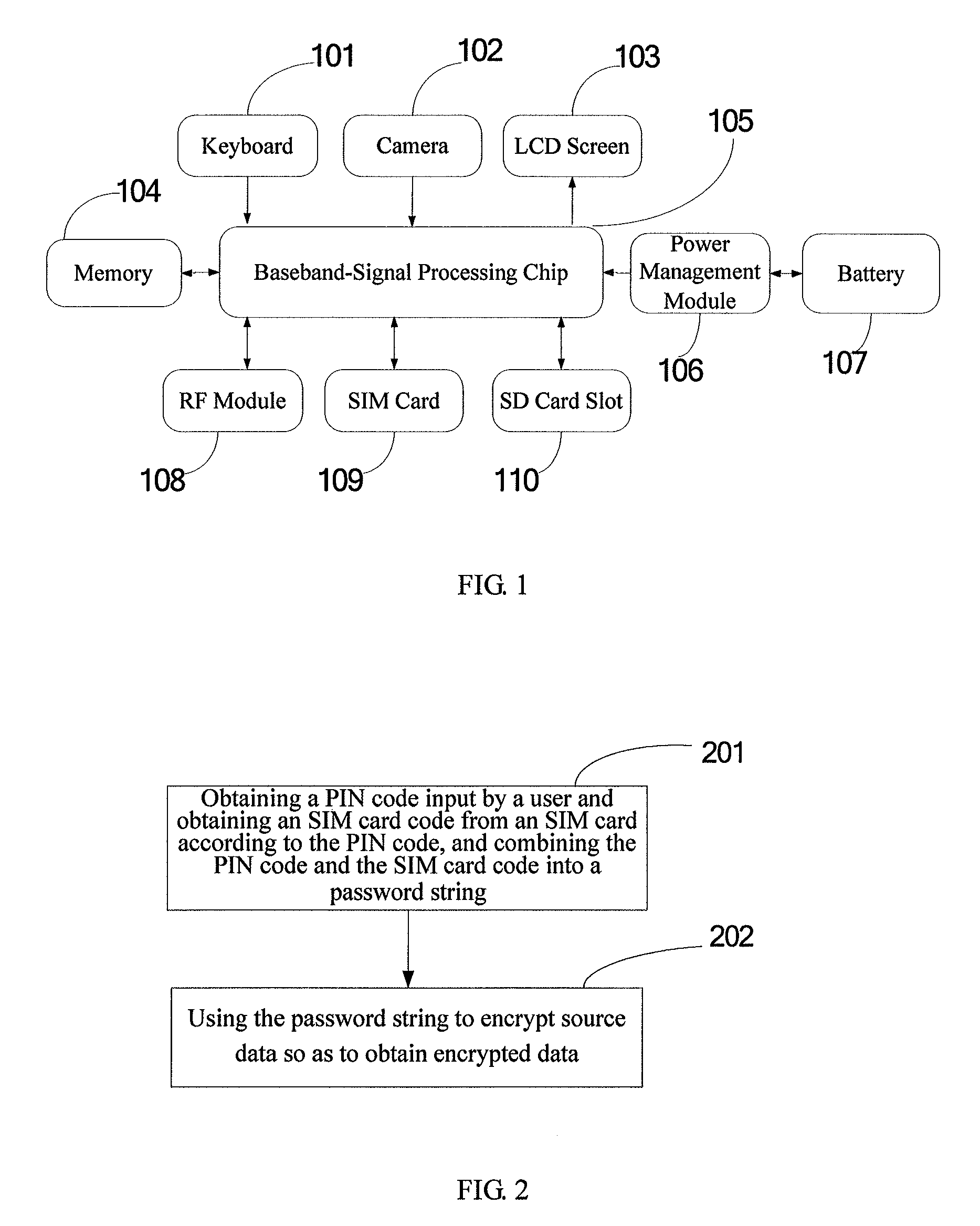
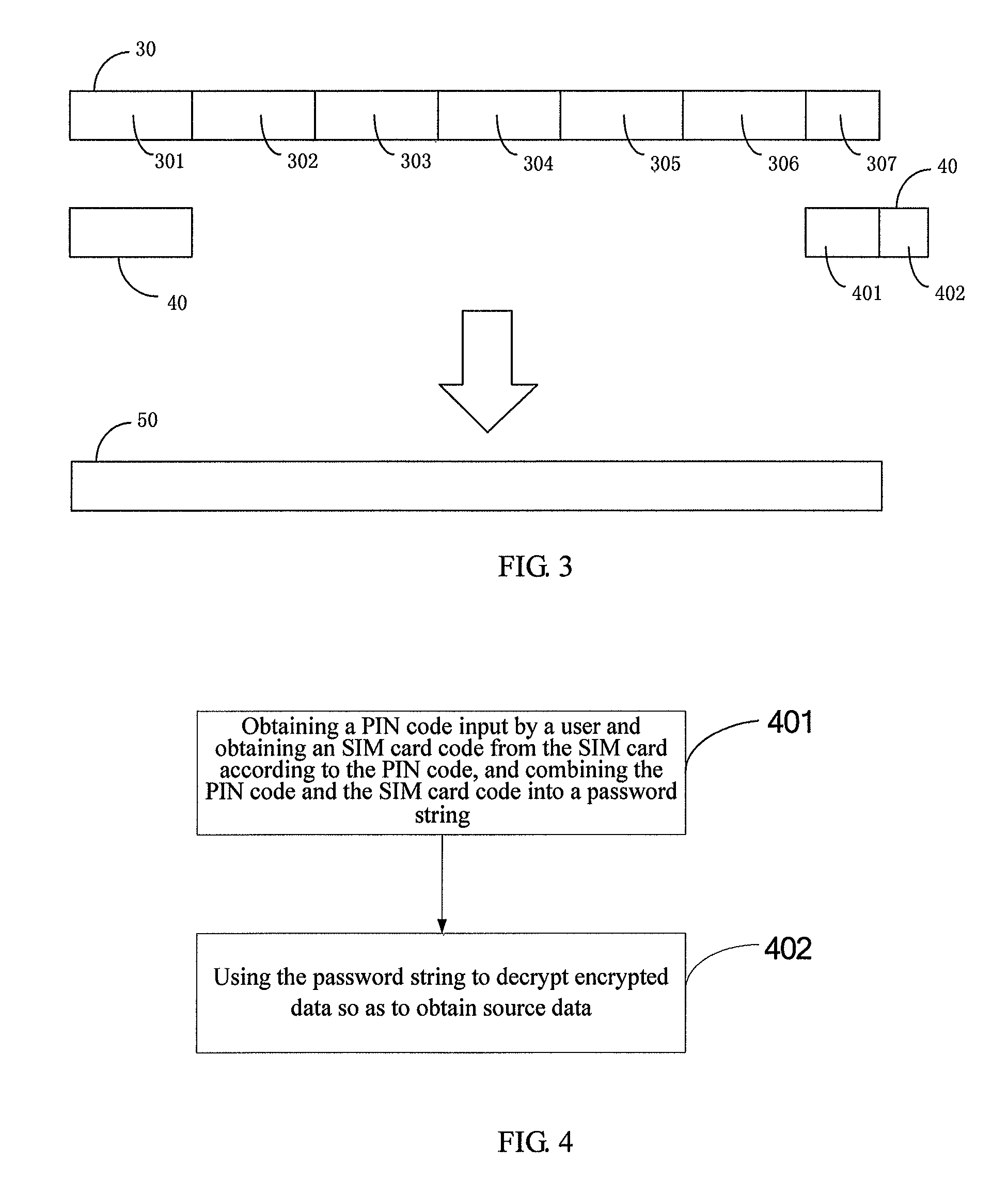
ActiveUS9276748B2Protect data securityImprove securityKey distribution for secure communicationUser identity/authority verificationComputer hardwareUser input
Disclosed is a cell phone data encryption method, which comprises the steps of obtaining a PIN code which is input by a user, obtaining a SIM card code from a SIM card according to the PIN code, and combining the PIN code with the SIM card code to form a password string; and encryption source data using the password string, so as to obtain encrypted data. Also provided is a cell phone data encryption method. Through the manner mentioned above, the technical solution provided in the present invention can protect cell phone data.
Owner:COLUMBIA PEAK VENTURES LLC
Multilevel locking and multilevel unlocking method for mobile device
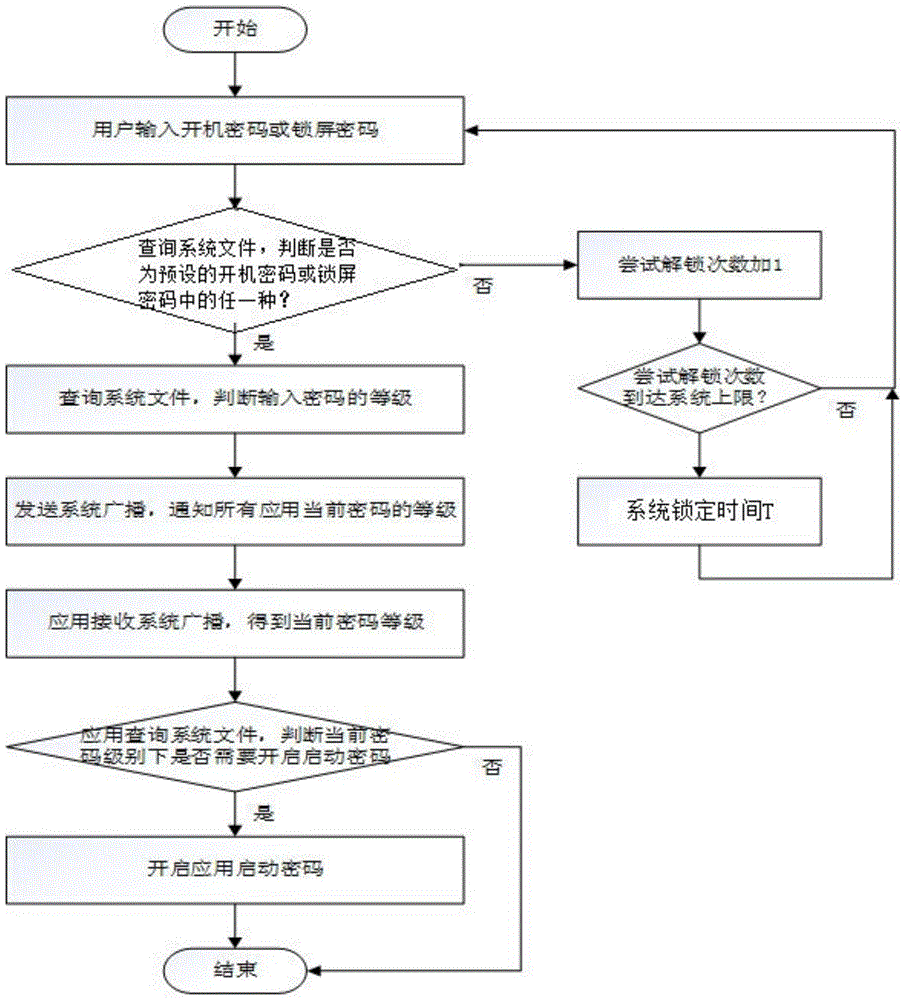
InactiveCN105787348AProtect data securityGuarantee data securityDigital data authenticationData securityPassword
The invention relates to a multilevel locking and multilevel unlocking method for a mobile device. The method comprises the following specific steps: (1) multistage locking: a user presetting a locking level of a system, a system-level password, a starting password of each application and an application list requiring to use the starting password under each locking level, wherein the different locking levels are corresponding to different system-level passwords and the application list requiring using the starting password; (2) multilevel deciphering: 1) when the user inputs the password to power on the mobile device or unlock the screen, the system acquiring the password input by the user; 2) judging whether the input password is any one of the power-on password or the screen-locking password, if so, judging the locking level, and notifying all applications on the mobile device, judging whether the starting password requires to use. Through the adoption of the method provided by the invention, the data security of the mobile terminal under special scene can be protected, the specific scene is mainly the scenes that the mobile device is lent to friends and strangers or the mobile device is lost.
Owner:SHANDONG UNIV
Image transmission method, device and terminal device
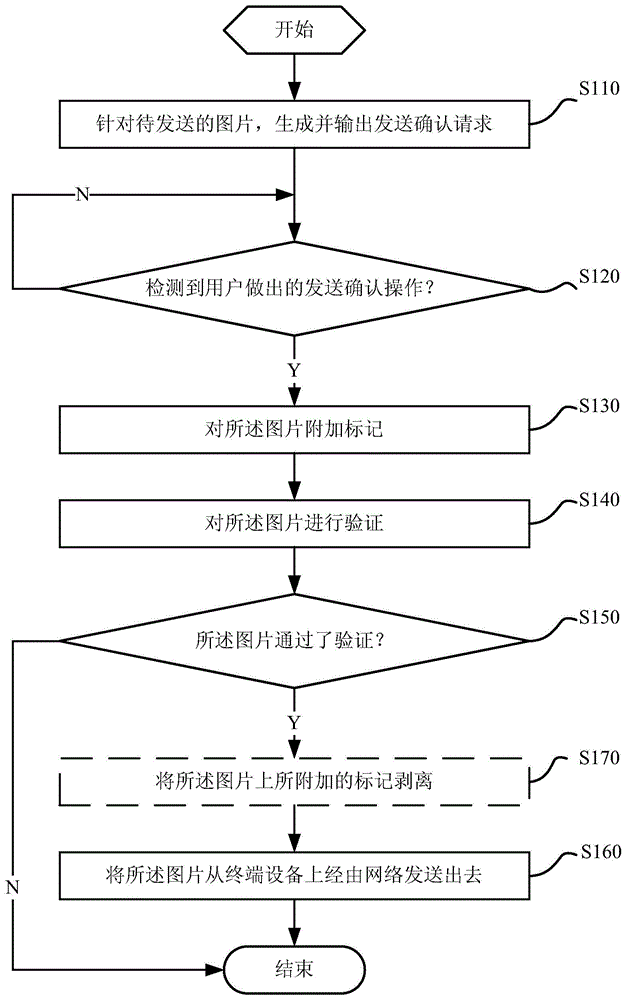
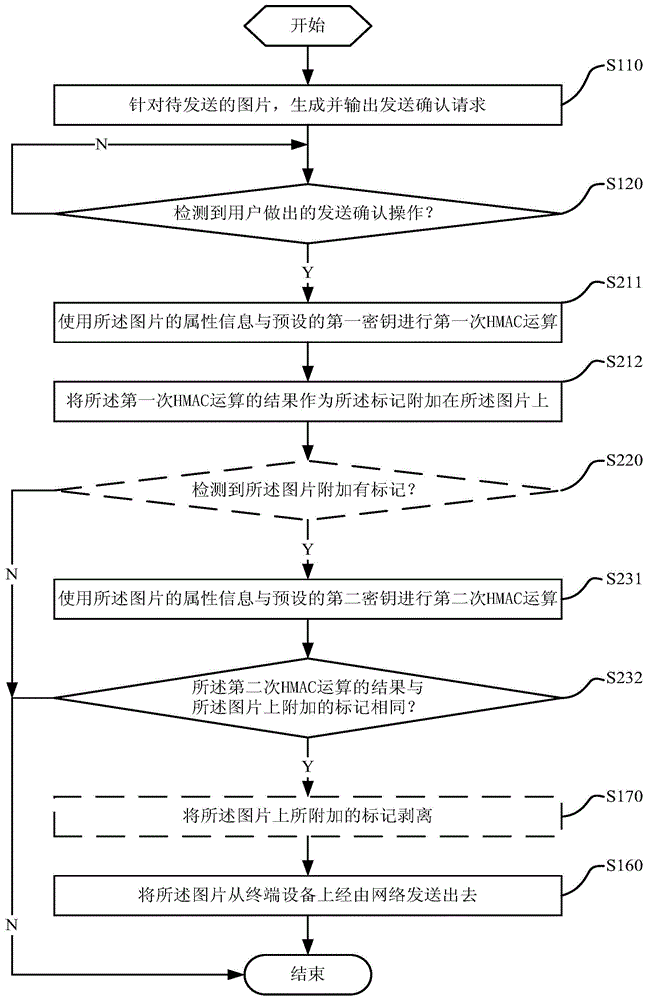
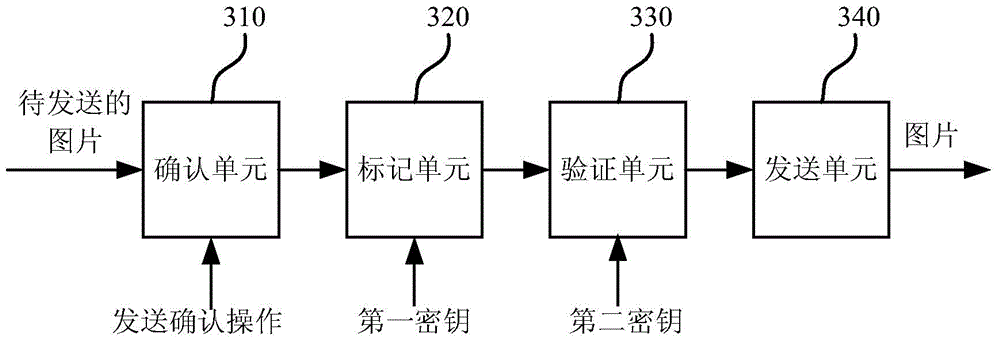
InactiveCN104995635APrevent outflowProtect data securityDigital data protectionComputer hardwareTerminal equipment
The invention discloses an image transmission method, device and terminal device. The method comprises: generating and outputting transmit confirmation requiry according to the image to be transmitted; attaching a lag to the image when detecting the user has made a transmit confirmation operation according to the transmit confirmation requiry; confirming the image; transmitting image via network from the terminal device on the premise of that the image is verified; wherein the transmit confirmation requiry is used for inquiring the user to confirm if the image can be transmitted, the transmit confirmation operation is executed by user, with predetermined style and on the terminal device, in response to transmit confirmation requiry. The image transmission method ,device and terminal device of the invention can ensure that the image transmitted from the terminal device is consented to transmit by the user, thereby preventing unauthorized photographing or stealing from the terminal device and invasion of privacy of the user, effectively protecting data safety of the user.
Owner:HUAWEI TECH CO LTD
Application method for budget management software
InactiveCN104268696AAvoid modification and data theftProtect data securityComputer security arrangementsResourcesThree levelSoftware
The invention relates to an application method for budget management software. The application method comprises the steps that (1) a software login program is started to enter a login interface, and login permissions are selected for login to enter the program, wherein the login permissions comprise the budgeter permissions, the budget dedicated permissions and the reading permissions; (2) after login is successful, a main page is entered, wherein the main page is divided into a static menu bar and a dynamic menu bar; (3) according to different execution tasks, a static menu is opened to enter a second-level menu, and according to different execution tasks, the static menu bar is opened to enter the second-level menu to further select execution tasks of a dynamic menu, wherein the static menu contains budge reporting, payment budgets, query printing and statements; (4) furthermore, according to different execution tasks, the second-level menu is opened to enter a three-level menu, wherein the three-level menu contains a budget application at the year beginning, a monthly budget application, a monthly budget payment, a viewing option and a printing option; (5) according to an option system of task execution, budget data are automatically budgeted and summarized.
Owner:国网河南禹州市供电公司
Case uncovering detection system and implementing method
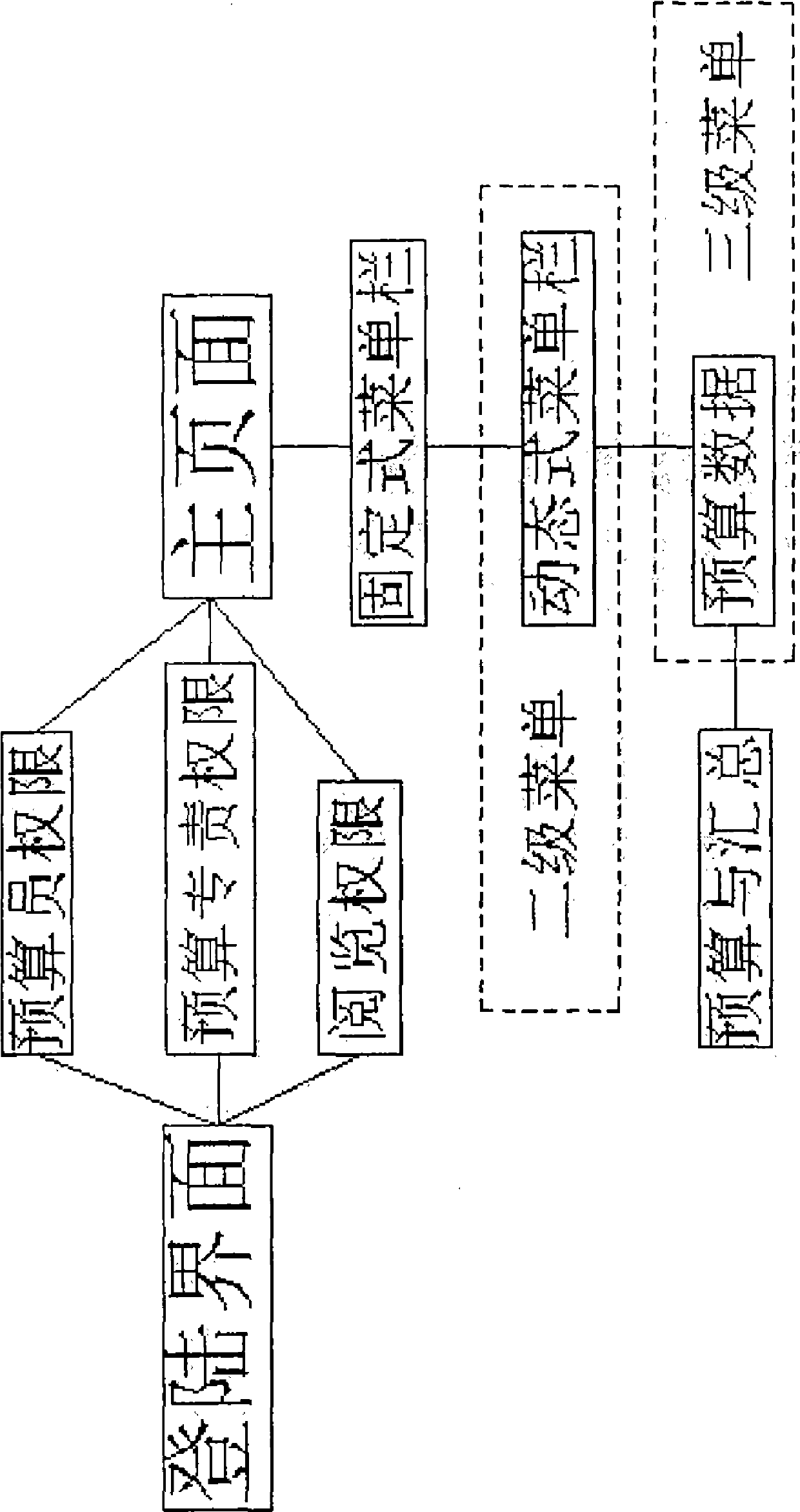
InactiveCN105787397AProtect data securitySimple wiringHardware monitoringInternal/peripheral component protectionComputer caseControl system
The invention discloses a case uncovering detection system. The system comprises a case as well as a mainboard, a key destroying switch, a storage module and a power supply which are arranged in the case, wherein a control system for controlling the working state of the storage module is arranged on the mainboard, the case comprises a case body with an opening in the top and an upper cover detachably arranged at the opening, the mainboard is paved and fixed on the bottom surface of the case body, the key destroying switch is welded on the mainboard, a ball is butted against the bottom surface of the upper cover, and a leaf spring is pressed on a shift switch. The invention further provides an implementing method of the case uncovering detection system. Case information safety can be ensured, interior wiring of the case is reduced, and the mounting process of an information protecting structure is simplified.
Owner:深圳市亿威尔信息技术股份有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com