Key level-to-level management method and device for federated learning and privacy calculation
A hierarchical management and key technology, applied to the public key and key distribution of secure communication, can solve the problems of key leakage and inability to restore sensitive data, so as to prevent key leakage, reduce costs and deployment time, and protect data Effects on Security and Privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
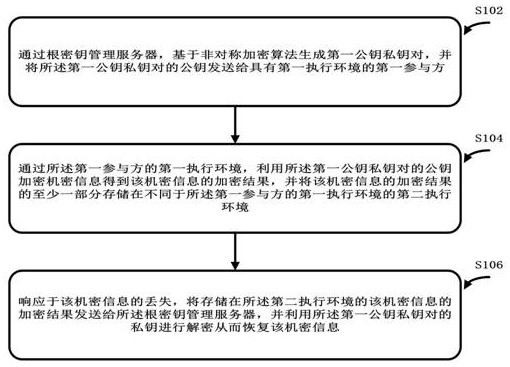
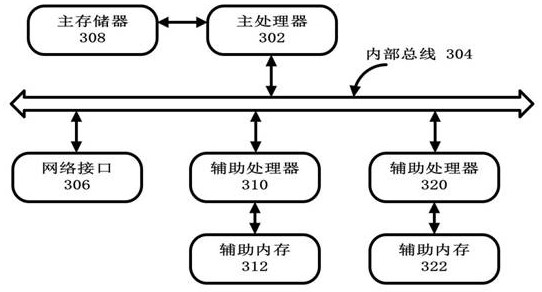
[0036] In order to solve the above-mentioned key leakage problem and key loss problem caused by server restart, the embodiment of the present application proposes a key hierarchical management method and device for federated learning and privacy computing. Wherein, the key hierarchical management method includes: using the root key management server to generate a first public key-private key pair based on an asymmetric encryption algorithm, and sending the public key of the first public key-private key pair to the A first participant in the execution environment; through the first execution environment of the first participant, use the public key of the first public key-private key pair to encrypt the confidential information to obtain an encryption result of the confidential information, and convert the confidential information to at least a portion of the encrypted result of the information is stored in a second execution environment different from the first execution environ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com