Single sign-on method, server and client
A single sign-on, server-side technology, applied in the field of communication, can solve problems such as not using national secret algorithms, achieve the effect of improving user experience and protecting data security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
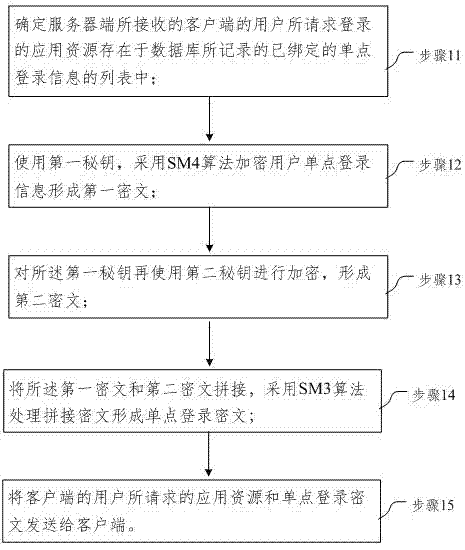
[0051] This embodiment provides a processing flow of a single sign-on method such as figure 1 As shown, in this embodiment, the server side receives the application request initiated by the client, establishes a two-way connection, and extracts the user identity; according to the user identity, search the user list of the bound single sign-on information recorded in the database Whether there is a login application resource requested by the user in ;
[0052] The processing steps are as follows:
[0053] Step 11, determining that the application resource requested by the user of the client terminal received by the server exists in the list of bound single sign-on information recorded in the database;
[0054] Step 12. Using the first secret key, the SM4 algorithm is used to encrypt the user's single sign-on information to form a first ciphertext;
[0055] Specifically, in this embodiment, random numbers are used to generate a symmetric key with a length of 32 bits as the fir...
Embodiment 2
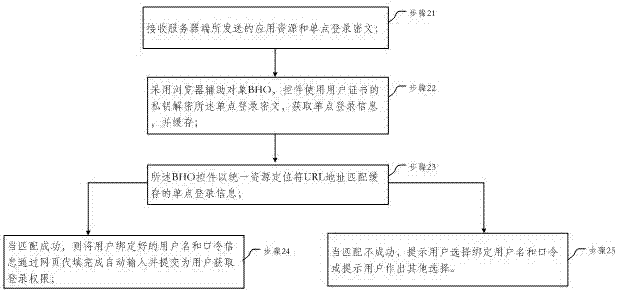
[0064] This embodiment provides a processing flow of a single sign-on method such as figure 2 As shown, in this embodiment, the client processing steps are as follows:
[0065] Step 21. Receive the application resource and SSO ciphertext sent by the server; specifically, in this embodiment, receive the application resource and SSO ciphertext sent by the server to form a login home page;
[0066] Step 22. Using the browser helper object BHO (Browser Helper Object), the control uses the private key of the user certificate to decrypt the SSO ciphertext, obtain the SSO information, and cache it;
[0067] In this embodiment, the BHO control is used to use the private key of the user certificate to decrypt the SSO ciphertext, obtain the SSO information, and cache it according to the agreed format; click to log in to the application resources on the homepage;
[0068] Step 23, the BHO control matches the cached single sign-on information with a Uniform Resource Locator URL (Uniform...
Embodiment 3
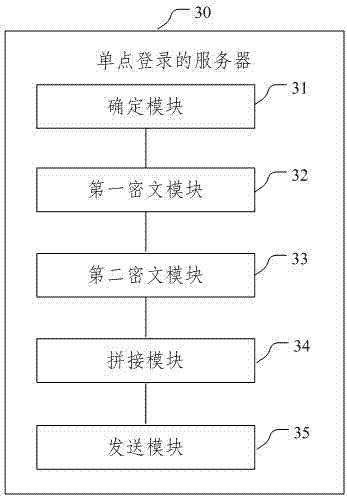
[0074] This embodiment provides a single sign-on server 30, and its specific implementation structure is as follows image 3 As shown, it can specifically include the following modules:
[0075] Determination module 31: it is used to determine that the application resource requested by the user of the client terminal received by the server exists in the list of bound single sign-on information recorded in the database;
[0076] The first ciphertext module 32: it is used to use the first secret key to encrypt the user's single sign-on information with the SM4 algorithm to form the first ciphertext;
[0077] The second ciphertext module 33: it is used to encrypt the first secret key with a second secret key to form a second ciphertext;
[0078] Splicing module 34: it is used for splicing the first ciphertext and the second ciphertext, using the SM3 algorithm to process the concatenated ciphertext to form a single sign-on ciphertext;
[0079] Sending module 35: used for sending...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com