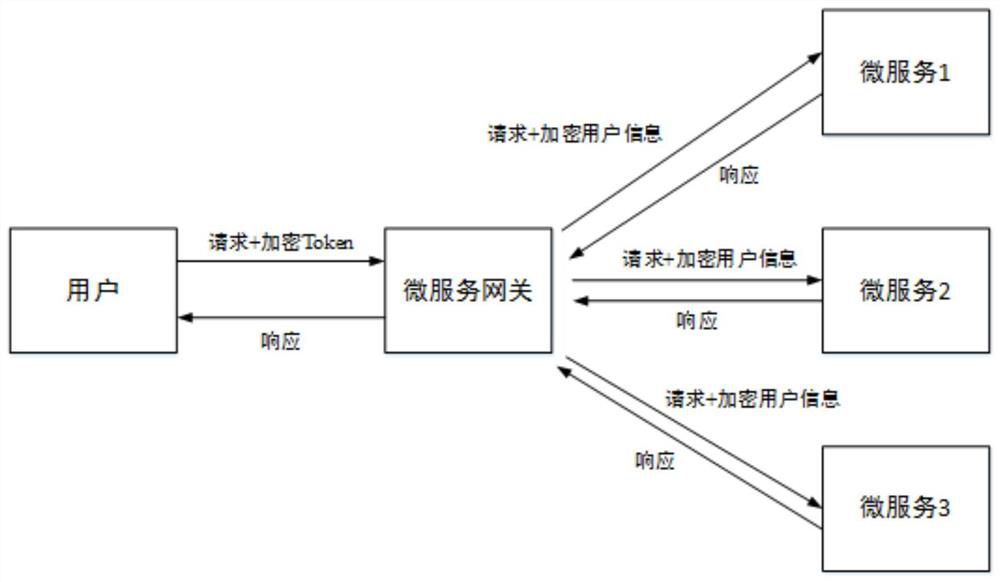
Stateless authentication method for micro-service system
A micro-service, stateless technology, applied in the transmission system, digital transmission system, user identity/authority verification, etc., can solve the problems of JWT protocol performance degradation, server pressure increase, large bandwidth occupation, etc., to reduce pressure and reduce docking Difficulty, smooth running effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] OAuth is an open network standard about authorization. Through this network standard, a third-party application can obtain specific resources stored by resource owners (users) in service providers (service providers that provide services to users). In this standard, third-party applications cannot directly log in to the service provider, and resource owners are only responsible for making decisions about whether to authorize and which resources to authorize. Obtain specific resources from service providers through tokens.
[0021] JSON Web Token (JWT) is an open standard (RFC 7519) that defines a protocol to securely transmit information between two points in a self-contained JSON format. The transmitted information can be verified and trusted because it uses digital signatures. JWT can be digitally signed by using a secret key (HMAC algorithm) or a public key / secret key pair (RSA algorithm).
[0022] Redis is an open-source, log-type, Key-Value database written in AN...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com