System, application and method for IP network access authentication based on personal identification module IM
An identity recognition module and access authentication technology, applied in user identity/authority verification, transmission system, network connection, etc., can solve problems such as insecure IP network password authentication, and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
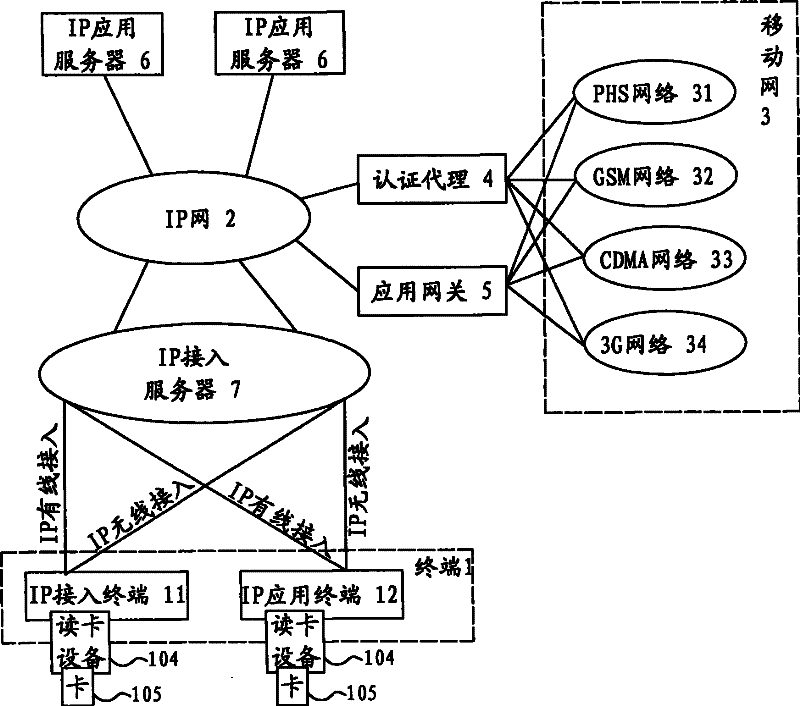
[0037]The present invention adopts PIM / SIM / UIM / USIM card as user identification, utilizes the identity authentication function of mobile networks such as PHS, GSM, CDMA and 3G, realizes IP access and user identity authentication of the application system based on IP access. The user identity authentication system and method provide uniform identity authentication for an application system, thereby supporting provision of multiple services.
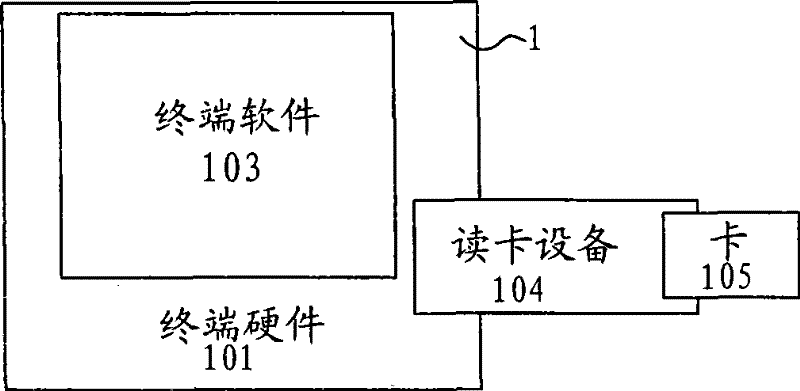
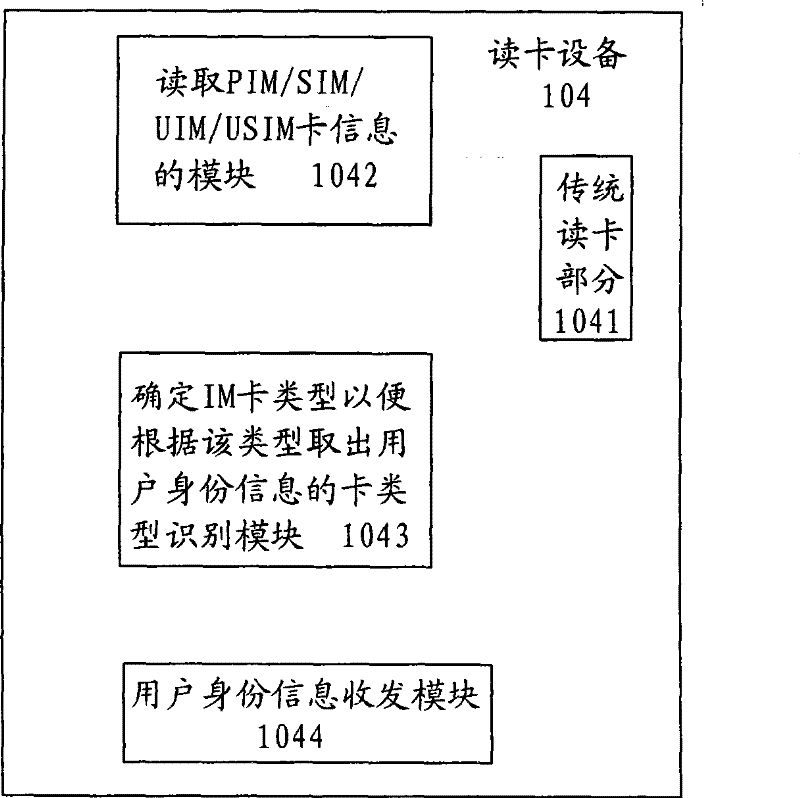
[0038] figure 1 Is the overall system block diagram of the present invention. figure 1 The system in includes: an IP network (2) coupled to each IP terminal (1), and the figure shows that the IP terminal (1) includes an IP access terminal (11) and an IP application terminal (12), but is not limited to This; Mobile network (3), shows that mobile network (3) comprises PHS network (31), GSM network (32), CDMA network (33), 3G network (34) in the figure, but is not limited to this; Coupling The application gateway (5) between the IP network ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com