Intelligent project data management method and system
A data management and intelligent technology, applied in the field of data processing, can solve the problems of information island site, lack of unified and secure authentication management method and authority management method, data security performance is not guaranteed, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
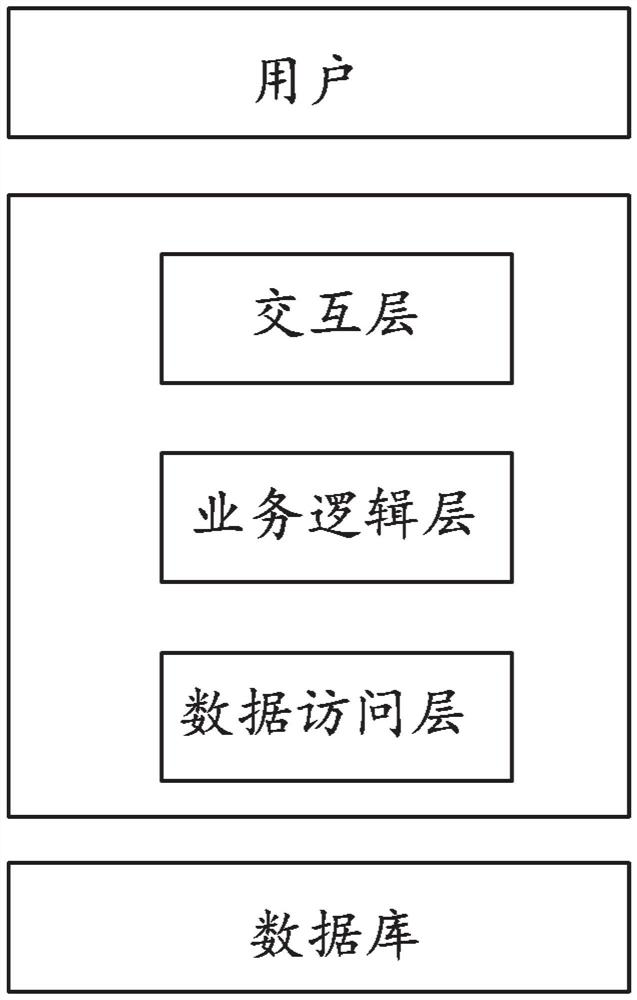
[0051] Such as figure 1 As shown, Embodiment 1 of the present disclosure provides an intelligent project data management system, including: a data access layer, a business logic layer and an interaction layer;
[0052] The data access layer is used for accessing the project data center library and performing the operations of Select, Insert, Update, and Delete of the data table;
[0053] Business logic layer, used to encapsulate the actual business logic;
[0054] The interaction layer is used for user interaction with the entire system.
[0055] Specifically, the three-layer structure can ensure that user access does not directly contact the background logic application and data resources, but accesses layer by layer, calling the business method of the middle layer to obtain the background data resources, so that the security of the background data can be guaranteed , and can guarantee performance and consistency.
[0056] The interaction layer determines the interface displ...
Embodiment 2
[0060] Embodiment 1 of the present disclosure provides a smart project data management method, including the following process:
[0061] Obtain a request to log into the project data center;
[0062] Unified identity verification is performed on the login request, and data access is allowed when the identity verification is passed;
[0063] Among them, unified identity verification includes:
[0064] Get the identity information of the login object, take out the user password in the login object and add a timestamp to form a new string, then encrypt the new string, match the encrypted result with the user password, and take the current server time and time If the difference is within a certain range and the user password can match, the authentication of the logged-in user is successful.
[0065] The project data center database includes at least: user entity class, audit entity class, permission entity class and permission granting role entity class;
[0066] Attributes of ...
Embodiment 3
[0073] Embodiment 3 of the present disclosure provides a smart project data management method, including the method described in Embodiment 2, and also includes the following process:
[0074] Users can only enter other pages from the main page, and are not allowed to search directly in the address bar; when switching pages, directly judge the user's authority, and at the same time verify whether the user's IP address is within the authorized range, otherwise they will not be logged in.
[0075] When a user logs in in the user center UC, the server side obtains and verifies the user's login information and queries the corresponding role information datasets of all sites in the database;
[0076] Save this data set in the local login ticket of the user center, and when generating a login reply, send the role in the target site requested by the user as part of the user identity information to the target site.
[0077] When the user requests to access the corresponding resource o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com