Multi-tenant authority authentication method based on operation and maintenance auditing system
A multi-tenant, tenant technology, applied in the computer field, can solve problems such as low query performance of connected tables
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
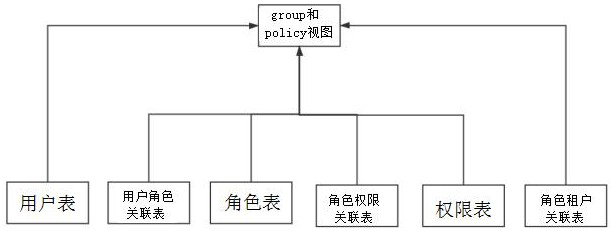
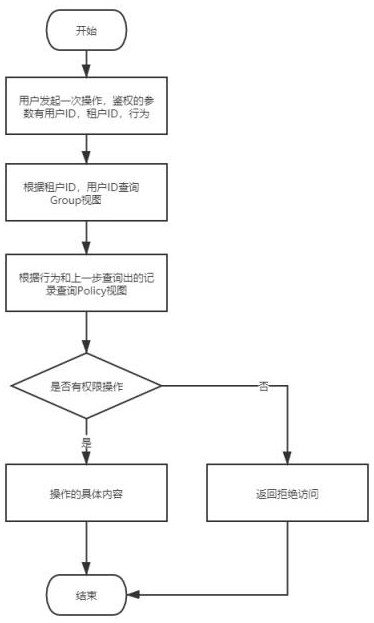
[0024] A multi-tenant permission authentication method based on the operation and maintenance audit system, such as figure 1 As shown, a unified materialized view is established for users, roles, roles, tenants, and their relationships. The view is divided into two materialized views, one is the policy view, which stores the relationship between roles, tenants, and permissions, and the other is the group view, which stores Users inherit roles, and tenants inherit tenant associations. The minimum models of each table are shown in Table 1-Table 7 below:
[0025] Table 1 user table user
[0026] ID name ... User ID user name The rest of the fields are irrelevant to this scenario
[0027] Table 2 role table role
[0028] ID name type character ID Role Name Role type, 1 is system built-in, 2 is custom
[0029] Table 3 tenant table tenant
[0030] ID name ... tenant ID tenant name The rest of the fields ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com