Intelligent antitheft method, terminal and system
An anti-theft method and intelligent technology, applied in the field of communication, can solve the problems of low timely rate, single anti-theft method, damage, etc., and achieve the effects of improving the timely rate of triggering, various identification methods, and convenient use.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings.
[0025] An intelligent anti-theft method, comprising the following steps:
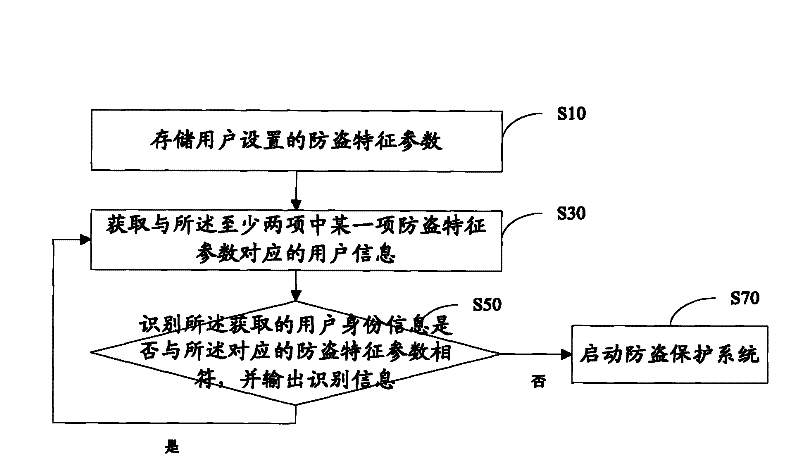
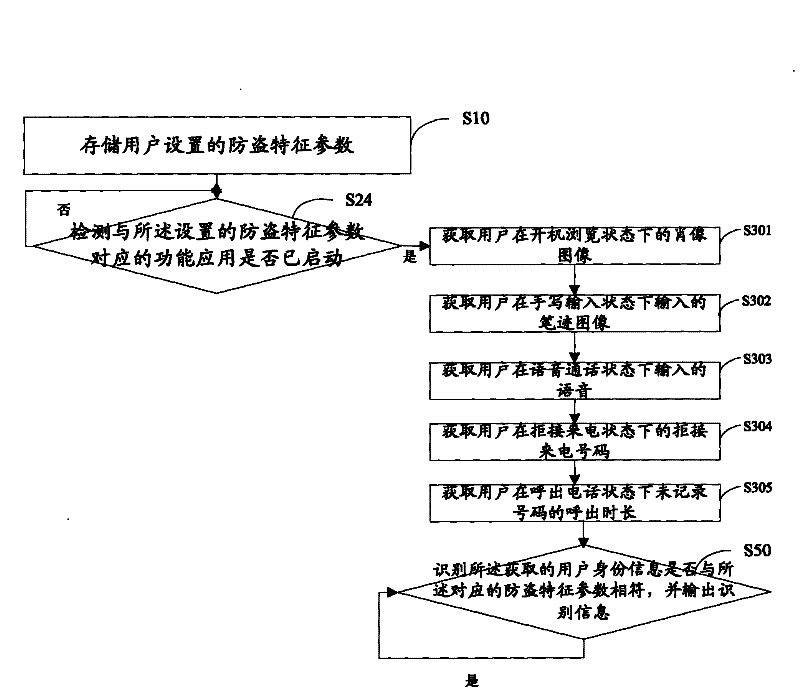
[0026] Storing the anti-theft feature parameters set by the user, the anti-theft feature parameters include at least two items;
[0027] Obtaining user information corresponding to one of the at least two anti-theft feature parameters;
[0028] Identifying whether the obtained user information matches the corresponding anti-theft characteristic parameters, and outputting identification information, if they match, continue to obtain and identify user information corresponding to other anti-theft characteristic parameters, otherwise, activate the anti-theft protection system.
[0029] see figure 1 , an intelligent anti-theft method, comprising:
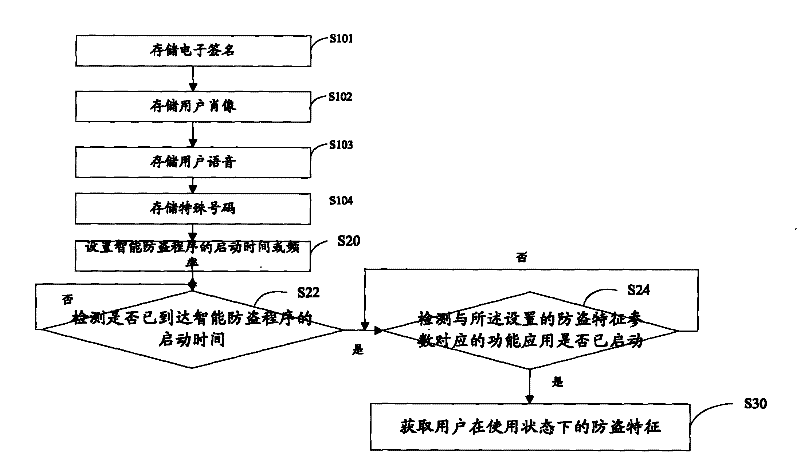
[0030] Step S10, storing the anti-theft fea...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com