File operation method of embedded system
An embedded system and file manipulation technology, applied in the fields of instruments, computing, electrical digital data processing, etc., can solve the problems of partition damage, partition damage, file loss, etc., and achieve the effect of improving file security performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
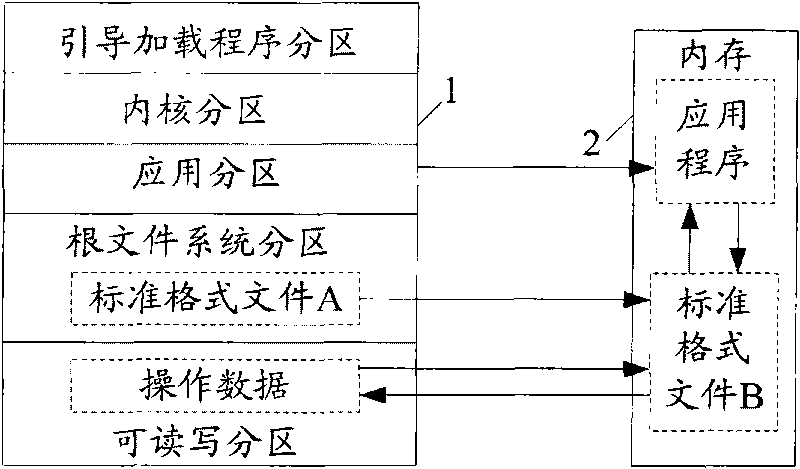
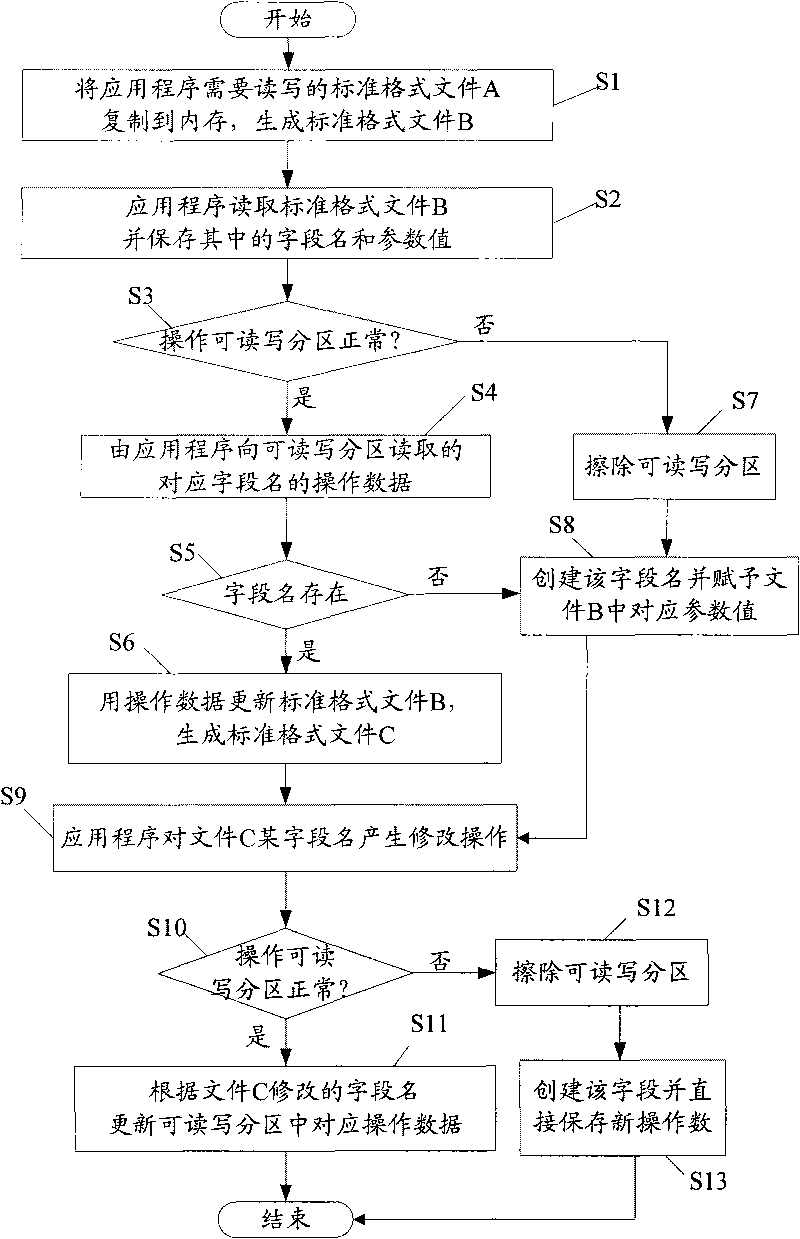
[0032] The present invention proposes a method of storing the data to be modified and the data not to be modified in files that need to be read and written separately in the Flash memory of an embedded device; data files that do not need to be modified are set as read-only, and data files that The file is first modified in the memory of the embedded device, and then updated to the readable and writable partition of the Flash memory.
[0033] In the file system of an embedded device, the files that need to be read and written generally include: system configuration files, version files, server address record files or user last operation record files, etc. Configuration files generally store user information such as IP addresses, user names, and passwords. The version file generally stores the version number and update time, etc. Other files generally store server addresses, upgrade server addresses, etc. In order to facilitate the search of the application, these files genera...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com