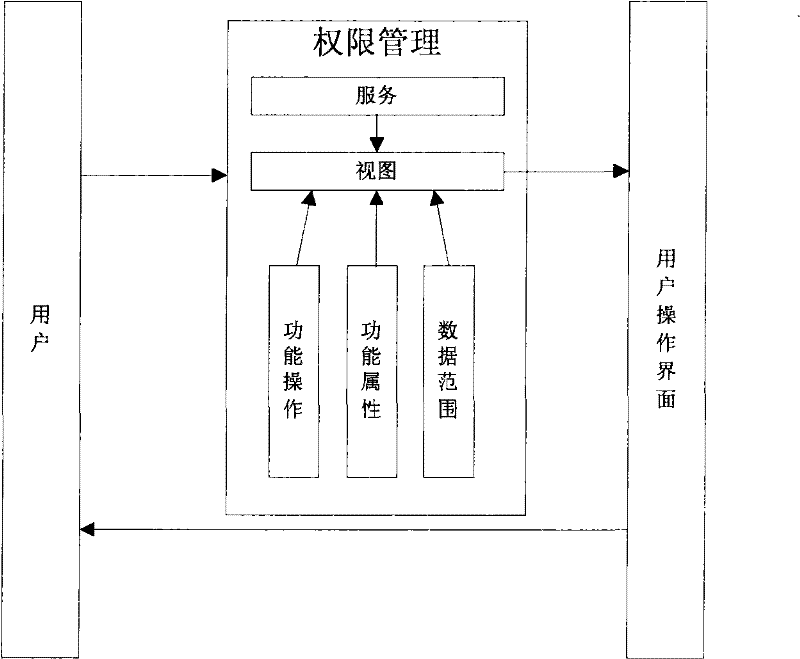
Service system-oriented and oriented object-based rights management method
An object-oriented and service-oriented technology, applied in the field of computer security, can solve the problems of inability to flexibly support enterprise security policies, single authority management, and increase the complexity of authorization management, so as to improve the authority management mechanism, reduce management overhead, and increase the complexity of authorization management. The effect of stretch
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] The preferred embodiments will be described in detail below in conjunction with the accompanying drawings. It should be emphasized that the following description is only exemplary and not intended to limit the scope of the invention and its application.
[0032] Step 1: Identify the services of the target system and the functions they contain, and create the basic data required for the model in the target system database:
[0033] Convert the service in the target system to figure 2 The structure is stored in the target system database service table;
[0034] Convert the functions in the target system to image 3 The structures are stored in target system database function tables.
[0035] Step 2: Identify the attributes contained in each function of the target system, and at the same time, create the basic data required for the model in the target system database: that is, the input controls and buttons contained in the function interface,
[0036] Move the button...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com