Safe access method based on extended 802.1x authentication system
A technology of secure access and authentication system, applied in the access field of data communication, can solve the problem of inability to realize trusted access of end users, and achieve the effect of ensuring authenticity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
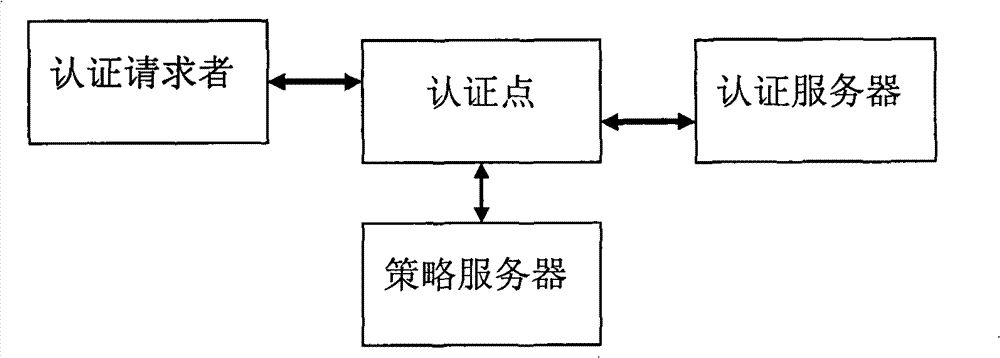
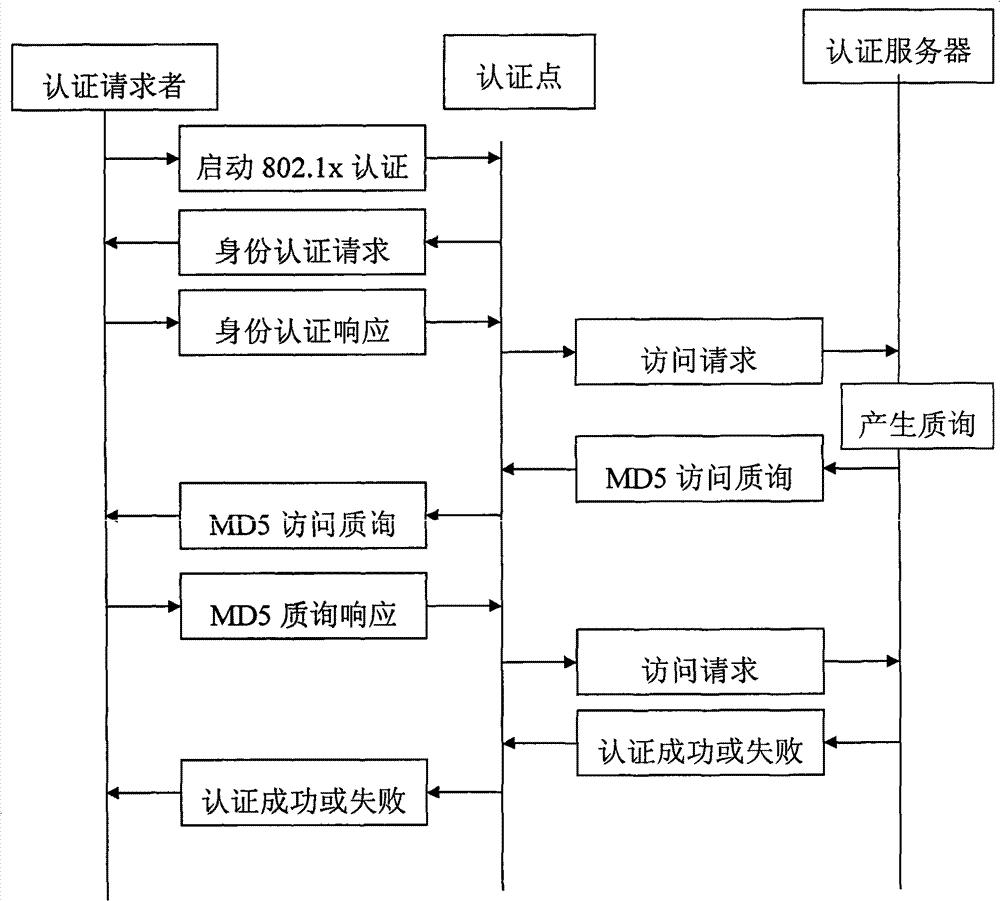
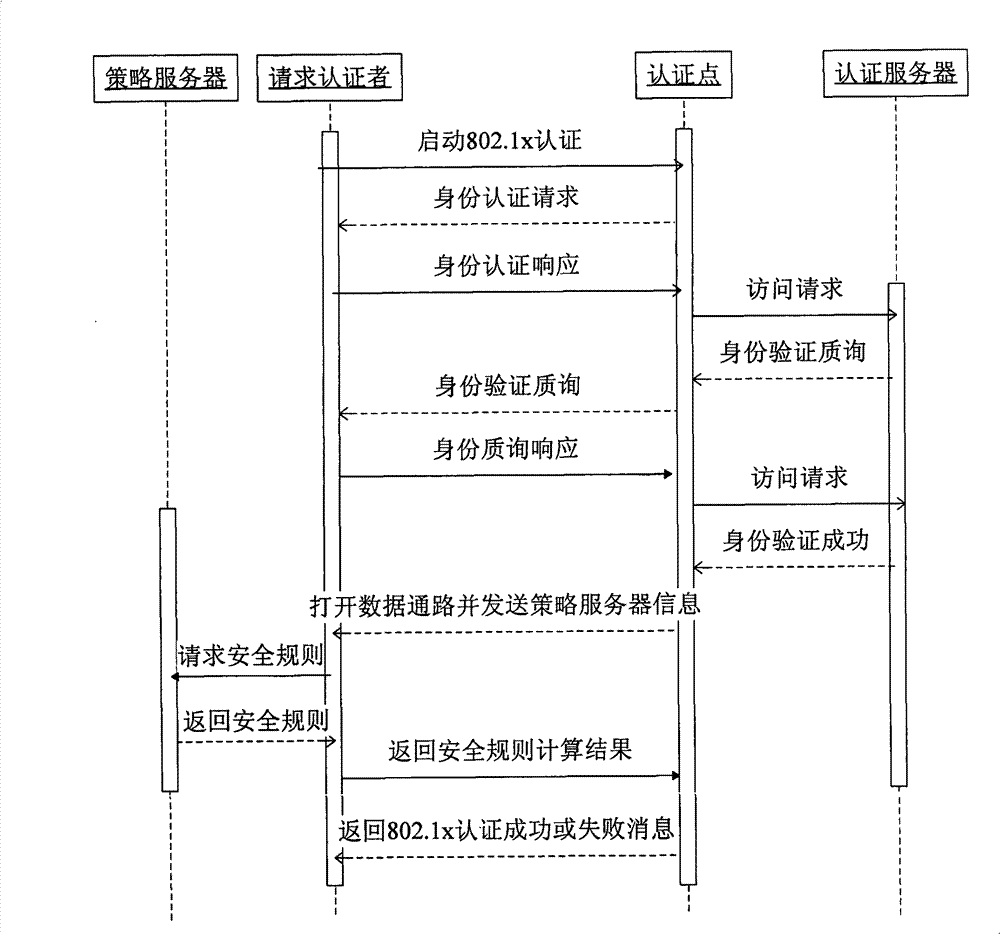
[0045] Combine now image 3 , the security access process of the present invention is described in detail: when the security terminal user and the two-layer access device have established a physical connection, the security terminal sends an EAPOL authentication start message to the two-layer access device according to the standard EAPOL protocol, and starts the 802.1 For xR authentication, the Layer 2 access device sends an EAP identity authentication request message to the security terminal, requiring the security terminal to submit a user name. The security terminal responds with an extended EAP identity authentication response message to the Layer 2 access device. The response message contains user name information and security access tag information. The Layer 2 access device records the response message with the security mark, and submits the user name to the RADIUS authentication service. The RADIUS authentication server generates a 128-bit challenge, and responds to t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com