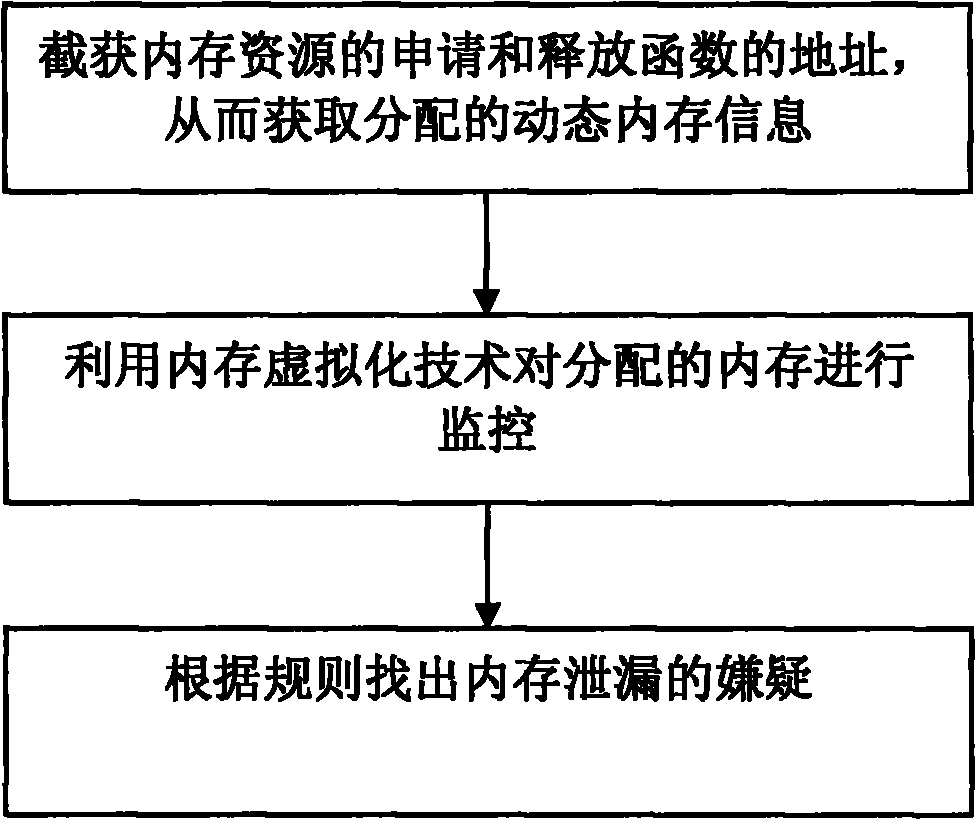
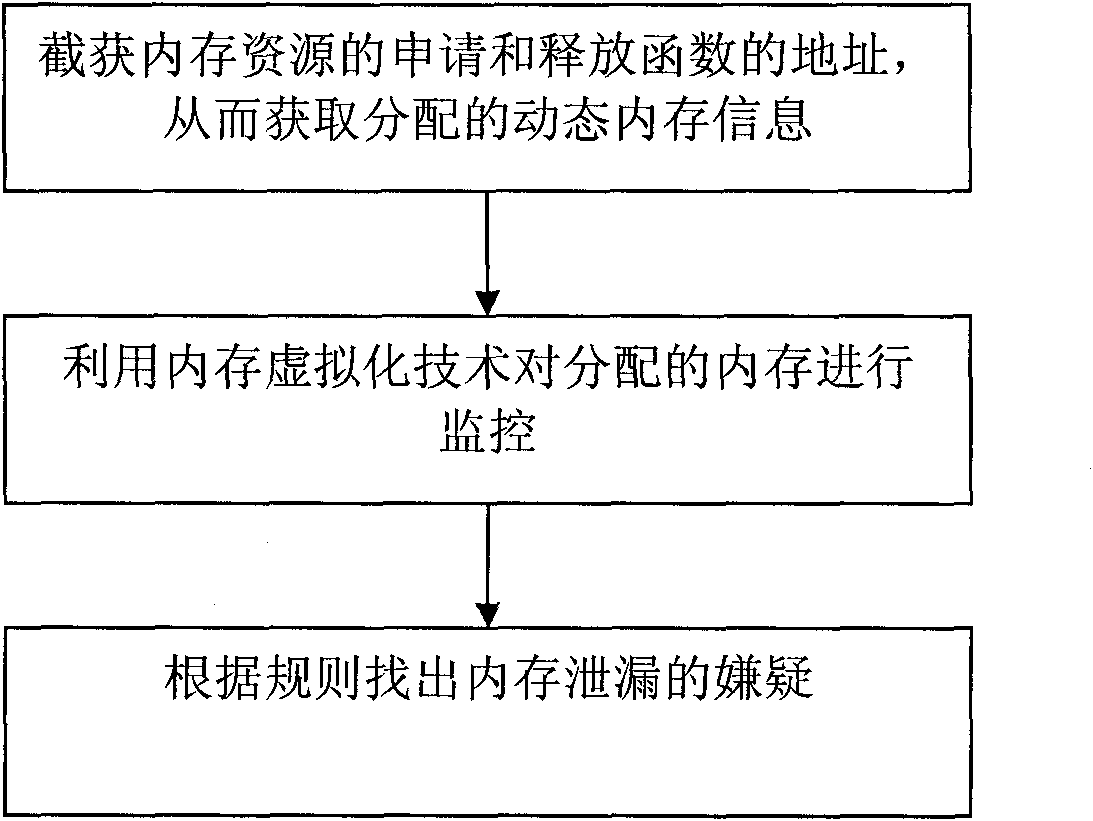
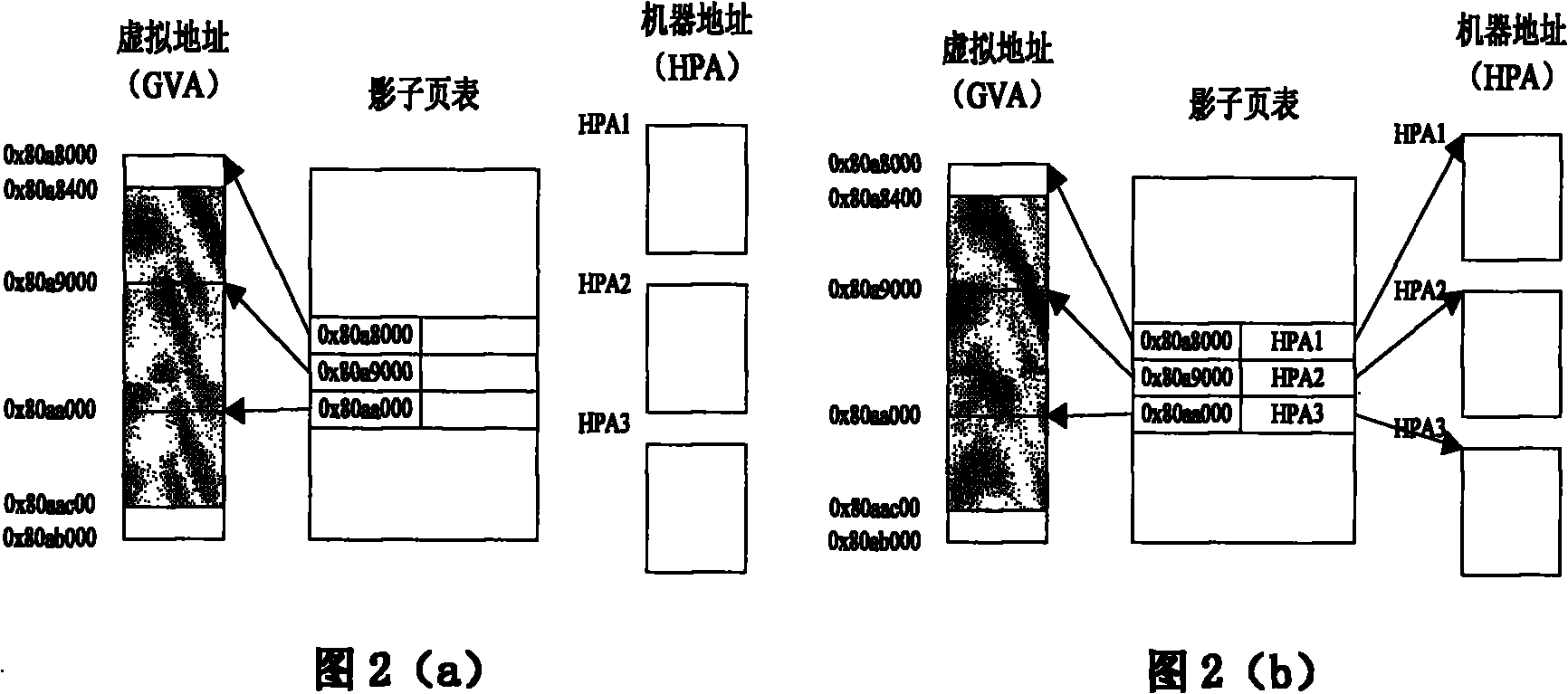
Memory leak detection method
A technology of memory leaks and detection methods, which is applied in software testing/debugging, hardware monitoring, etc., and can solve problems such as inability to stimulate problems, limited code, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0105] The following is a specific embodiment of the present invention, which is implemented based on the open source full virtualization virtual machine manager KVM-84. KVM is a virtual machine manager implemented based on GNU / Linux and runs in the operating system as a module. The virtual machine is represented as a qemu process in the operating system. Through the interaction with the KVM module, the process realizes processor virtualization, memory virtualization, and virtualization of some hardware; virtualization of other hardware devices such as network cards and external memory, Implemented by qemu. Because KVM is a module inside the operating system, its debugging and operation are very convenient. It can be updated through dynamic loading and unloading of modules. This is something that xen cannot provide. Every modification on it requires restarting the hardware.
[0106] In this experiment, the operating system used by the virtual machine is the relatively mainstr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com