Threshold secret information distribution and recovery method and device
A threshold secret and information distribution technology, applied in the field of information security, can solve the problems of not allowing participants to share, the amount of restoration calculation cannot be reduced, and the efficiency is low.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0061] The device and method for allocating and restoring threshold secret information proposed by the present invention are described as follows in conjunction with the accompanying drawings and embodiments.
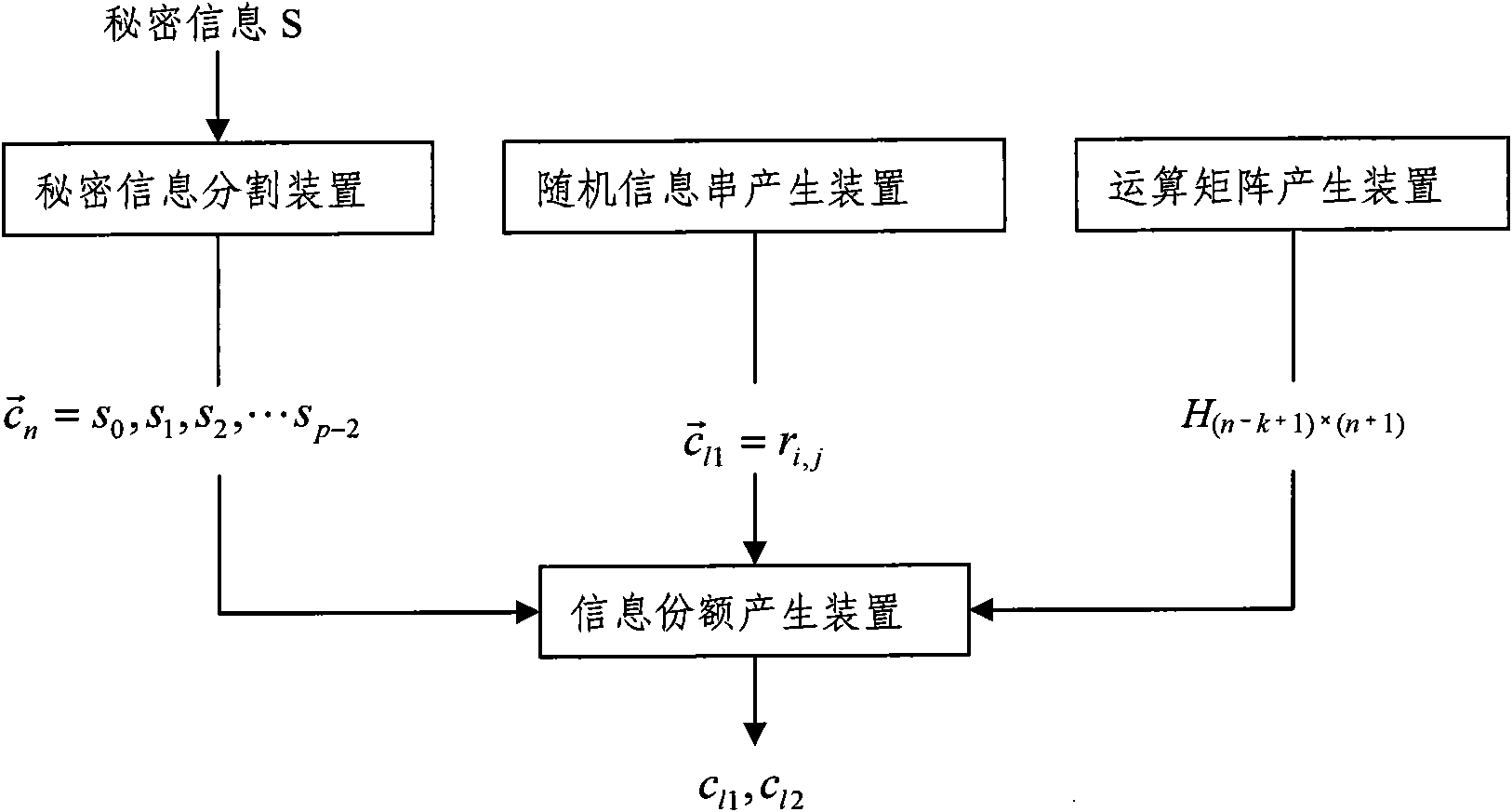
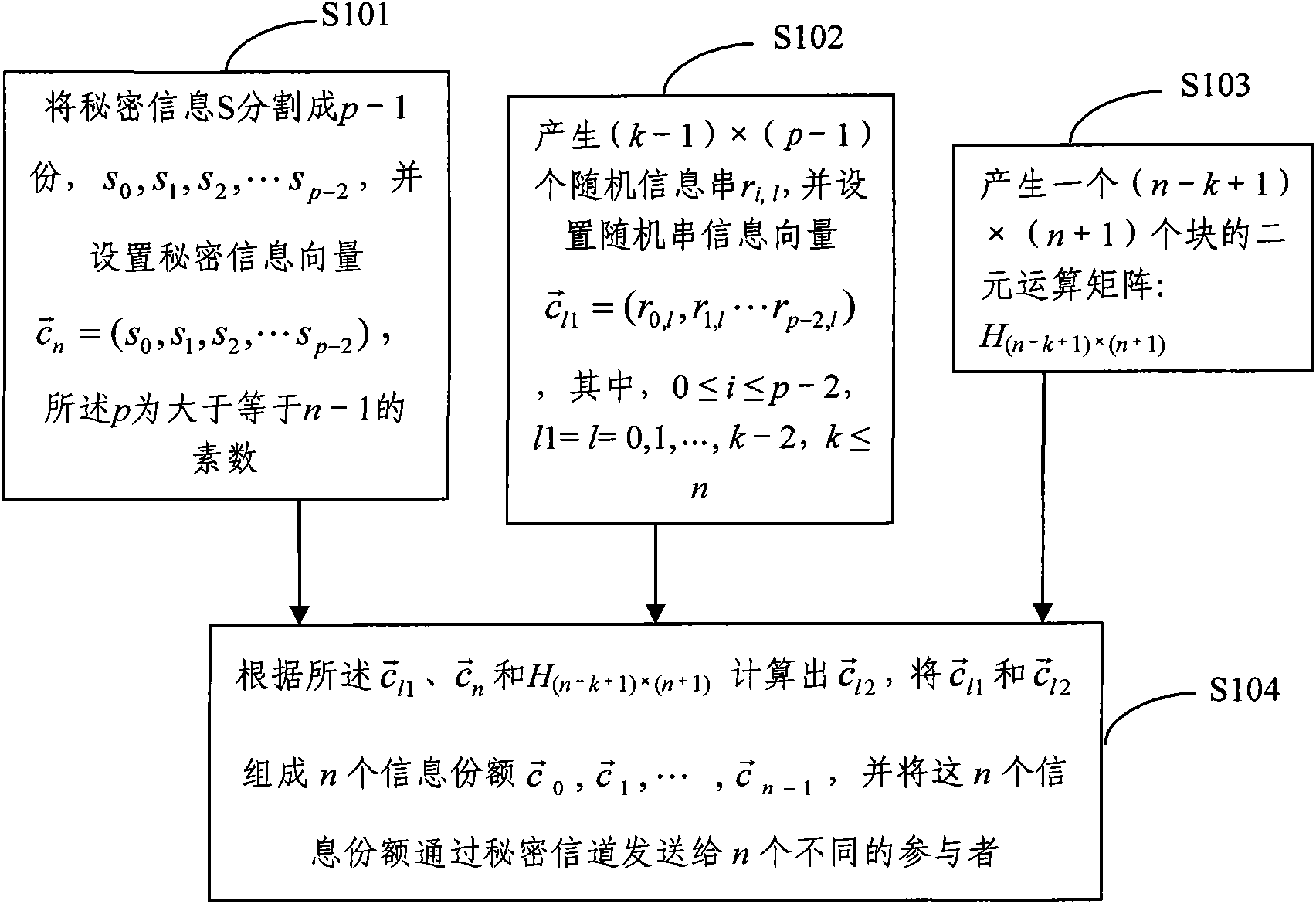
[0062] Such as figure 1 As shown, it is the threshold secret information distribution device of the present invention, which includes: a secret information dividing device, which is used to divide the secret information (such as the college entrance examination paper) divided into p-1 parts: s 0 ,s 1 ,s 2 ,...,s p-2 , and set the secret information vector p is a prime number greater than or equal to n-1, and the preferred division method is equally divided by equal length; the random information string generating device is used to generate (k-1)×(p-1) random information strings r i,l , and set the random string information vector group Among them, 0≤i≤p-2, l1=l=0, 1, ..., k-2, k≤n, the random information string is preferably equal in length and equal in length ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com