Information safety equipment, control method and system
A technology of information security and control methods, applied in the fields of instruments, electrical digital data processing, etc., can solve the problems of inconvenient use of information security equipment, users cannot log in and use, and operations cannot continue, and achieve the effect of improving the convenience of use.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
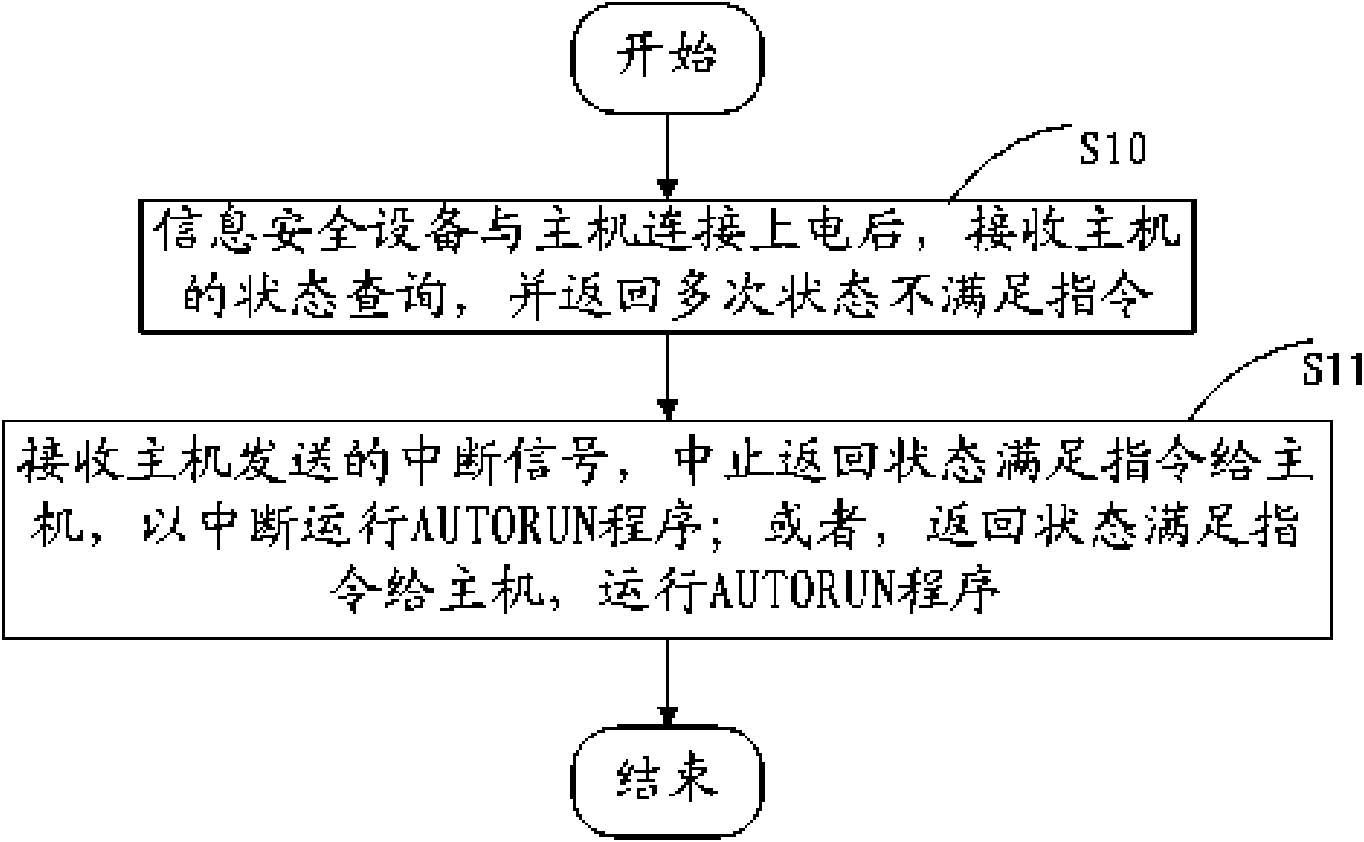
[0034] refer to figure 1 , the first embodiment of the present invention proposes a method for controlling information security equipment, including steps:
[0035] S10. After the information security device is connected to the host and powered on, it receives the status query of the host and returns multiple times that the status does not meet the instruction;
[0036] S11. Receive the interrupt signal sent by the host, and stop returning a status satisfaction command to the host to interrupt running the AUTORUN program; or, return a status satisfaction command to the host to run the AUTORUN program.
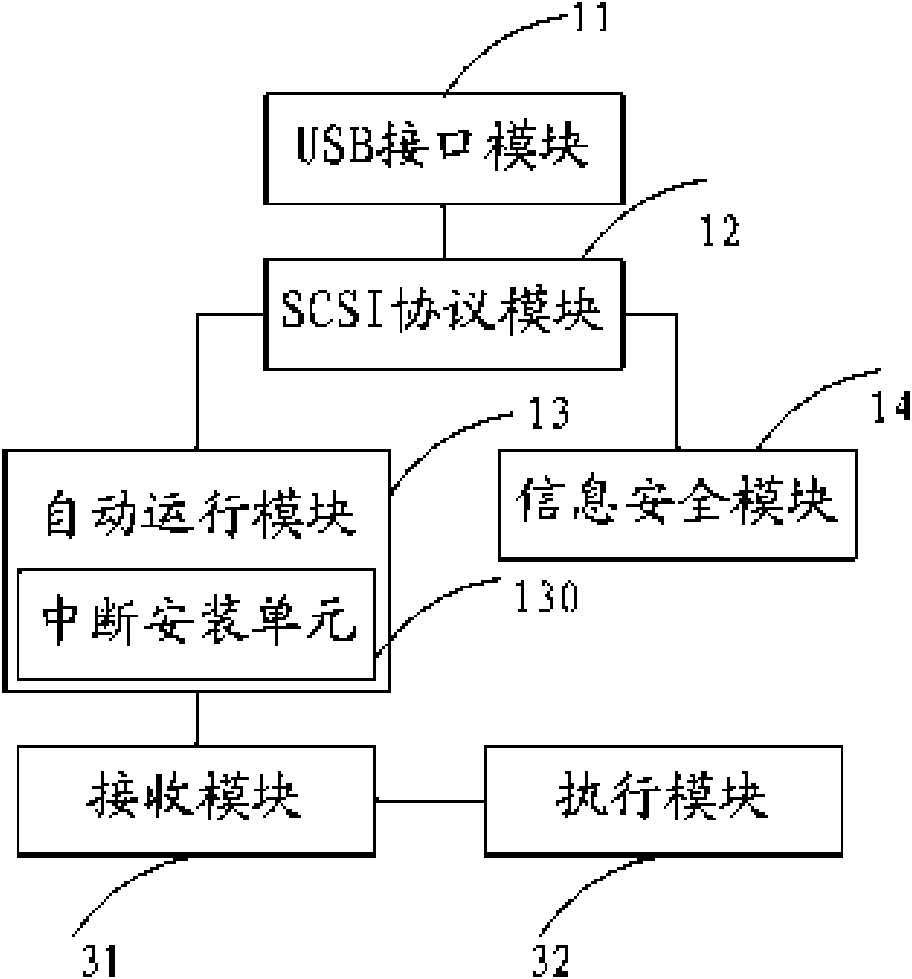
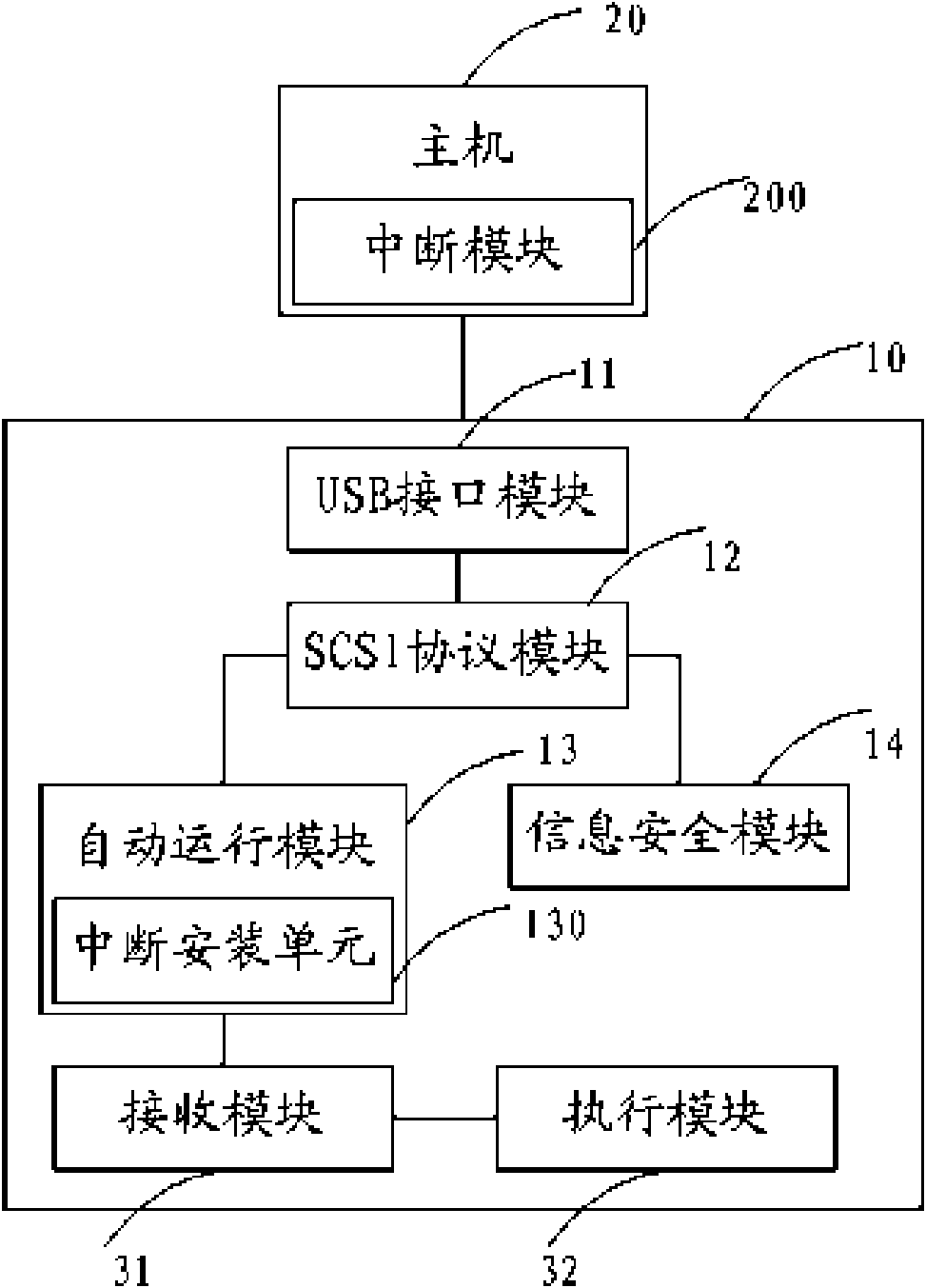
[0037] The above information security equipment may include: USB (Universal Serial Bus, universal serial bus) interface module, SCSI (Small Computer System Interface, small computer system dedicated interface) protocol module, automatic operation module and information security module, etc. The information security device can communicate with the host through the USB interface...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com