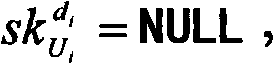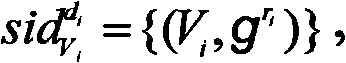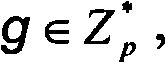Method for transforming unauthenticated key exchange protocol into authenticated key exchange protocol
A key exchange protocol, non-authentication technology, applied in the field of key exchange protocol, can solve problems such as low efficiency
Inactive Publication Date: 2010-12-15
UNIV OF ELECTRONICS SCI & TECH OF CHINA
View PDF3 Cites 3 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Although the K-Y protocol does not have the above two loopholes in security, its efficiency is relatively low. For example, the number of communication rounds is three, and each user must sign two messages
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
Embodiment Construction
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More PUM
 Login to View More
Login to View More Abstract
The invention discloses a method for transforming an unauthenticated key exchange protocol into an authenticated key exchange protocol. DSig=(Gen, Sig,Ver) is set as a standard digital signature algorithm by a digital signature method, wherein Gen is a key generation algorithm; Sig is a signature algorithm; Ver is a signature verification algorithm; and Gen generates a pair of signature / verification key pair for a user Ui. Simultaneously, the invention is an authenticated key exchange protocol and is used for fulfilling the aim of sharing one common conversion key among unacquainted members in a published network through interaction. The method for transforming the unauthenticated key exchange protocol into the authenticated key exchange protocol makes up security flaws of the conventional method and has higher security, and simultaneously compared with the conventional method, the method has the advantages of improvement on the calculation amount and communication traffic, and better application prospect.
Description
technical field The invention belongs to the technical field of communication, and in particular relates to a method for converting a non-authenticated key exchange protocol into an authenticated key exchange protocol. Background technique A key exchange protocol is a cryptographic primitive. As the name implies, a key exchange protocol is the establishment of session keys through the cooperation of participants. The key exchange protocol allows two or more participants to exchange information in an insecure channel controlled by the attacker, and negotiate a common session key through these exchanged information. This session key will be used in future secure communication, and the existence of this session key ensures secure communication on non-secure channels. In this way, the secure key exchange protocol can be used as the basic module for constructing secure, complex, high-level protocols. Key exchange protocols can be divided into non-authenticated key exchange pr...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More IPC IPC(8): H04L29/06
Inventor 许春香李成邦
Owner UNIV OF ELECTRONICS SCI & TECH OF CHINA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com