Solution method of address conflict in point-to-network tunnel mode
A technology of address conflict and solution method, applied in the field of address conflict under the point-to-network tunnel mode, can solve the problem of inability to meet the access and other problems, and achieve the effect of broadening the scope of use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment
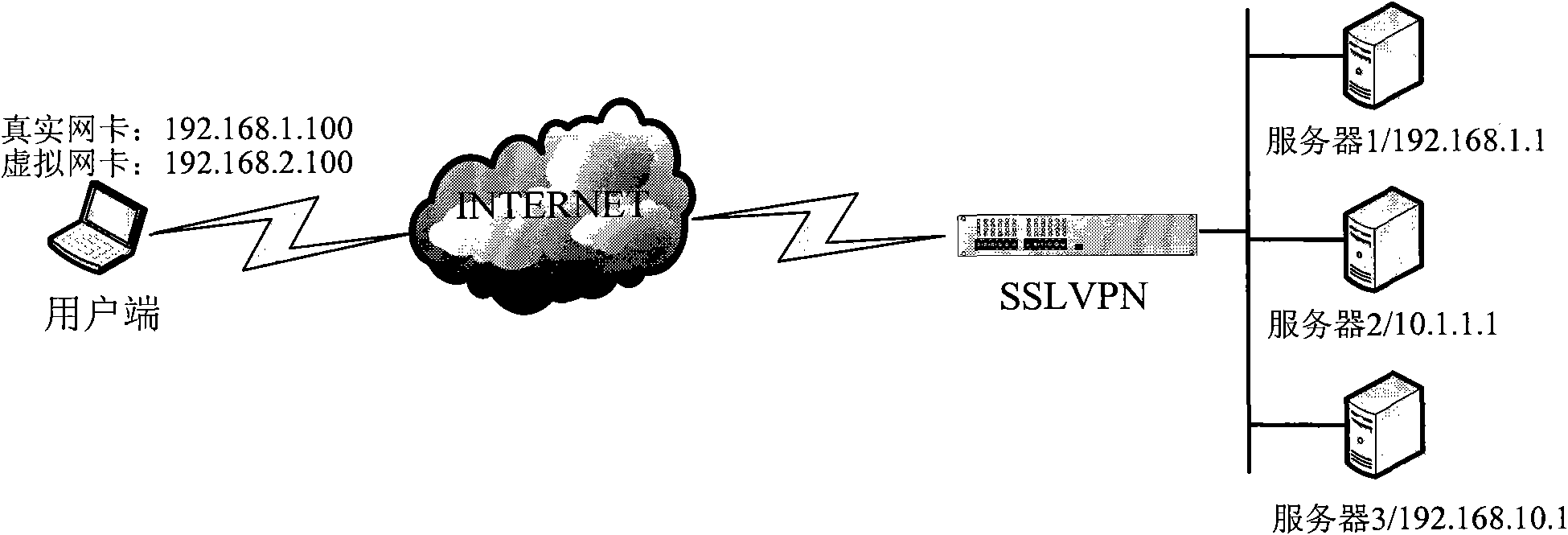
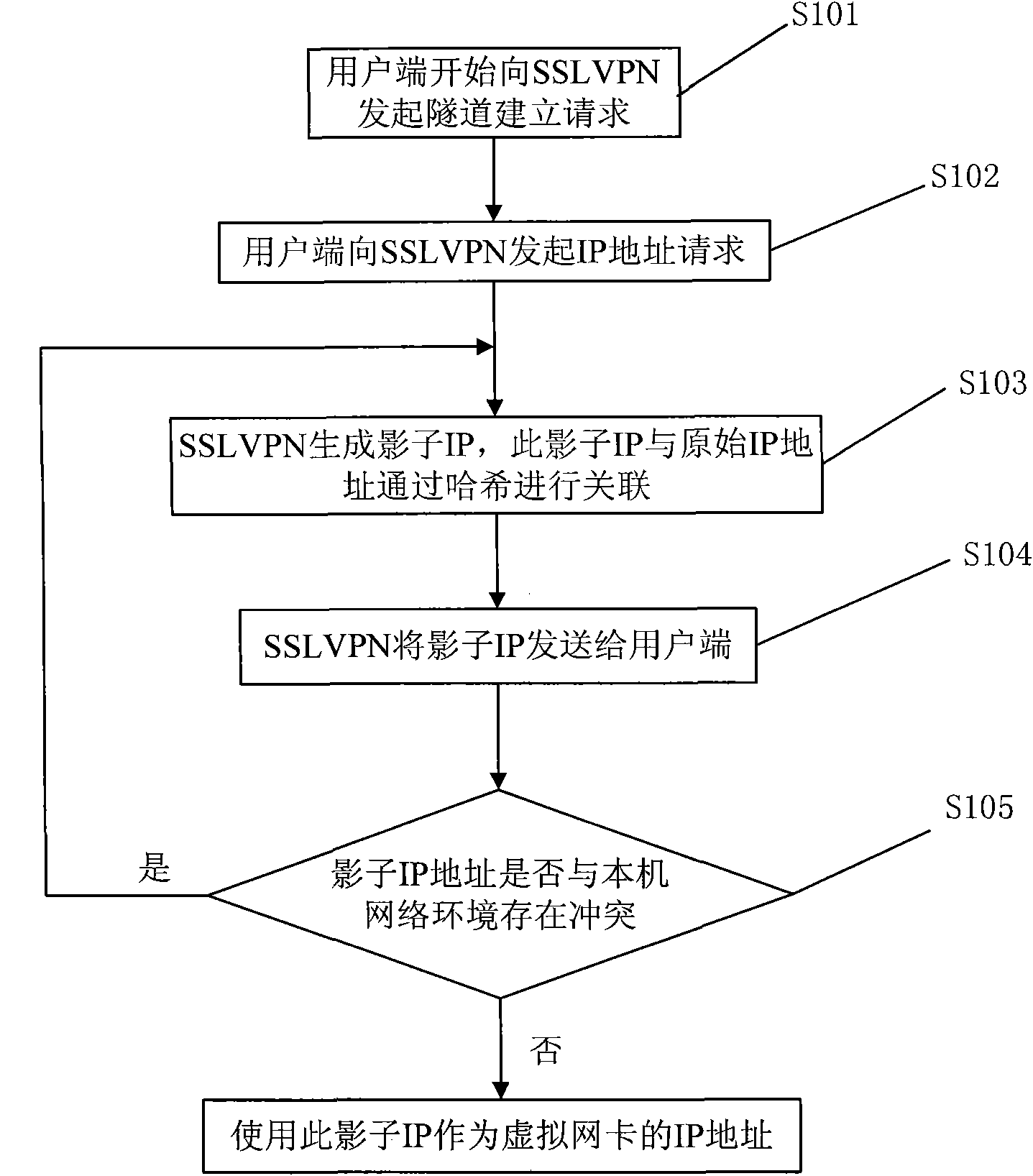
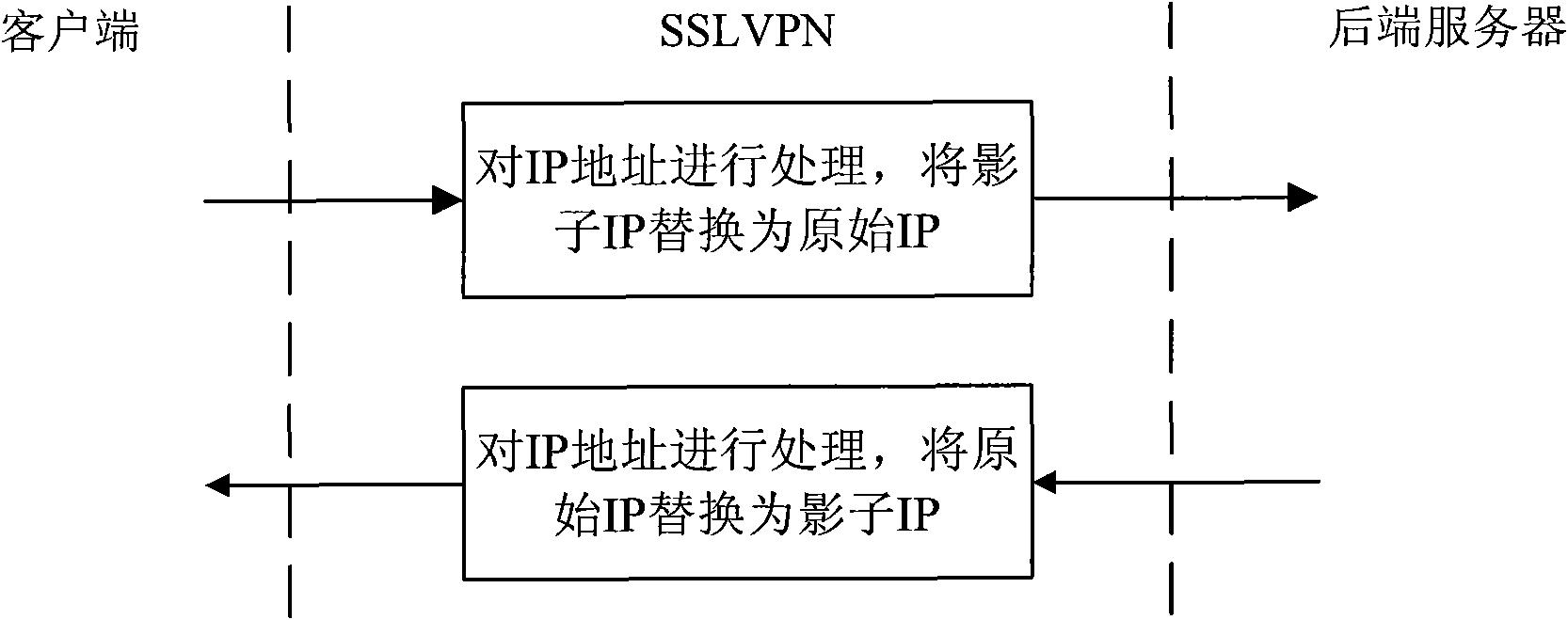
[0052] The IP address of the real network card on the client side is 192.168.1.100, and it is going to access server 1 through a tunnel, but server 1 requires only users whose source address is 192.168.1.100 to access, that is, the IP address of the virtual network card on the client side should be 192.168.1.100 . Based on this, SSLVPN assigns a virtual IP address: 192.168.1.100 to the client. However, this IP address conflicts with the real network card IP address of the client, and the tunnel cannot be used, so the client notifies SSLVPN of the conflict, and SSLVPN generates a shadow IP 192.168.2.100 for the client according to the algorithm, and sends it to the client. Document the association of these two IP addresses. Since there is no conflict between 192.168.2.100 and the client, the tunnel is established successfully. The client initiates a resource request to server 1 through this tunnel. The source IP and destination IP of this request are: 192.168.2.100->192.168.1...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com