Method for using digital signature to detect falsification possibility of software
A digital signature and software technology, applied in electronic digital data processing, instrument, platform integrity maintenance, etc., can solve problems such as affecting users' use, unable to open encrypted files, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
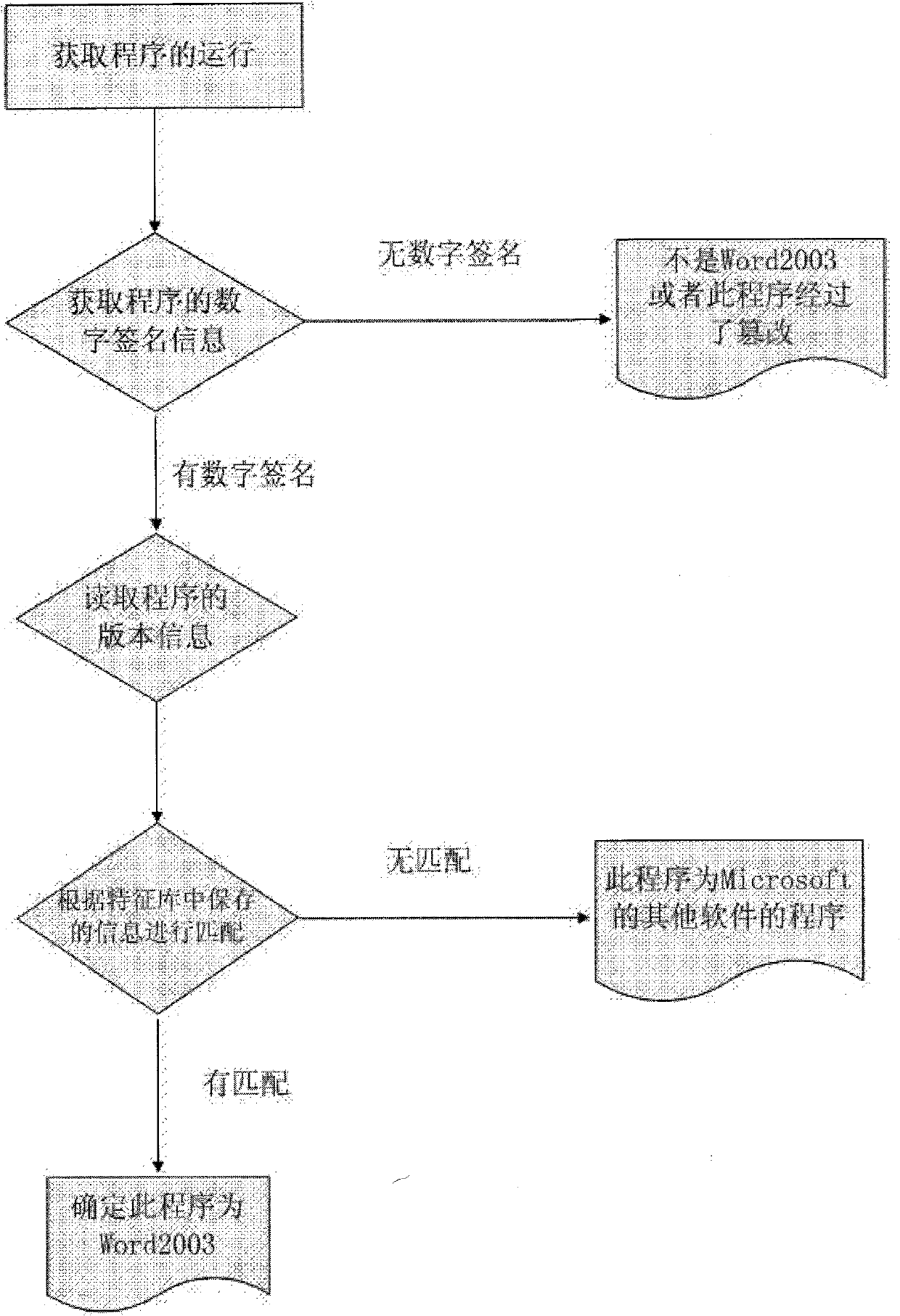
[0020] Take the detection of Word2003 in Office2003 as an example.
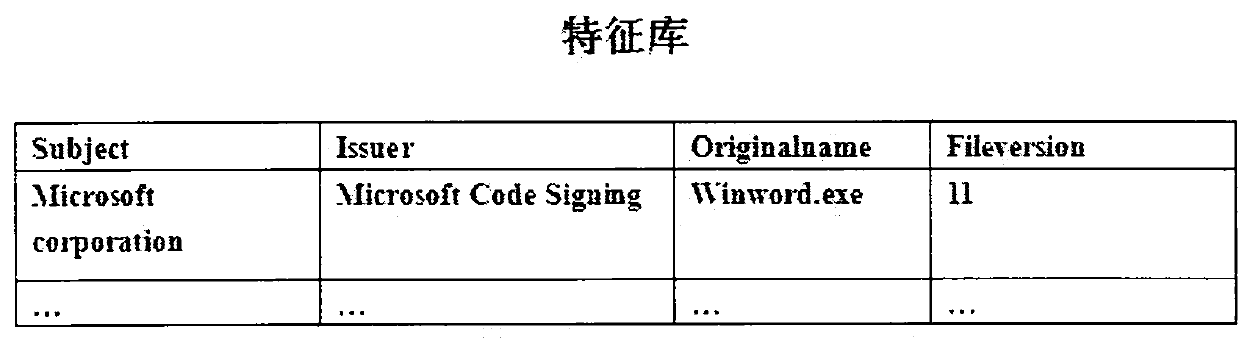
[0021] First, you need to store the relevant information of Word into the feature database. The issuer is "Microsoft Code Signing PCA", and the name of the signer is "Microsoft Corporation". The source file name in its version information is "WinWord.exe". Its file version is 11. refer to figure 1 .
[0022] When we know that Word2003 starts to run, we detect the characteristics of its program. First, we read whether the program has a digital signature. If not, it must not be Word2003 or the program has been tampered with. If there is a digital signature, and its issuer is "Microsoft Code Signing PCA" with the name of the signatory "Microsoft Corporation". Then we can be sure that this program has not been tampered with.
[0023] Going one step further, we read the version information of this program. If it has no version information or the source file name in its version information is not "WinWord.exe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com