Scheduling method under client-side/server-side architecture and server
A scheduling method and server-side technology, applied in the field of communication, can solve problems such as data confusion, and achieve the effect of improving ease of use and solving data confusion.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
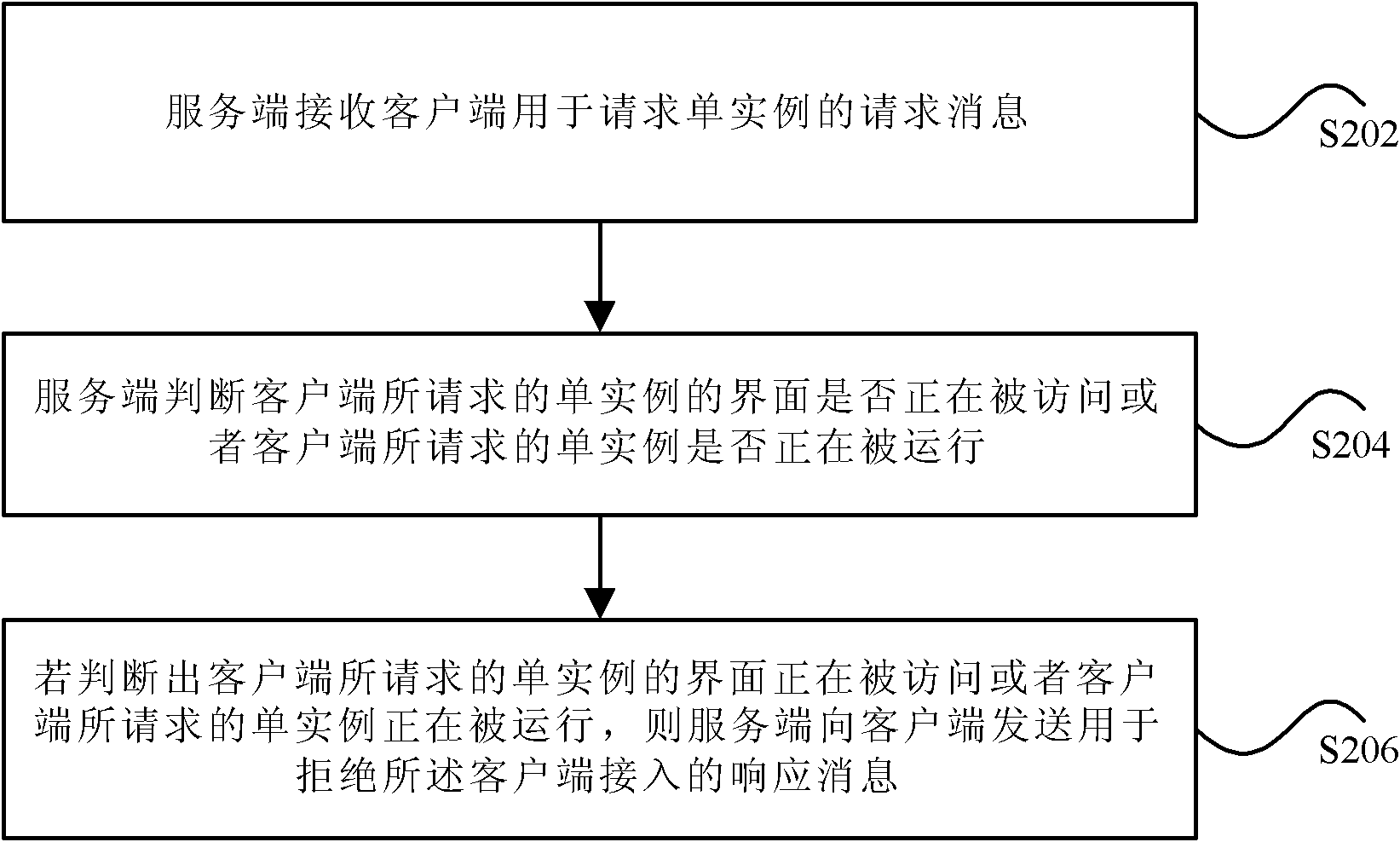
[0035] see figure 2 , the scheduling method under the client / server architecture according to this preferred embodiment includes the following steps:
[0036] S202. The server receives a request message from the client for requesting a single instance;
[0037] S204, the server determines whether the interface of the single instance requested by the client is being accessed or whether the single instance requested by the client is being run;
[0038] S206. If it is determined that the interface of the single instance requested by the client is being accessed or the single instance requested by the client is running, the server sends a response message to the client for denying access by the client.
[0039] In this preferred embodiment, the server judges whether the interface of the single instance requested by the client is being accessed or whether the single instance requested by the client is being run, so that the single instance can only be executed by one client at th...
Embodiment 2
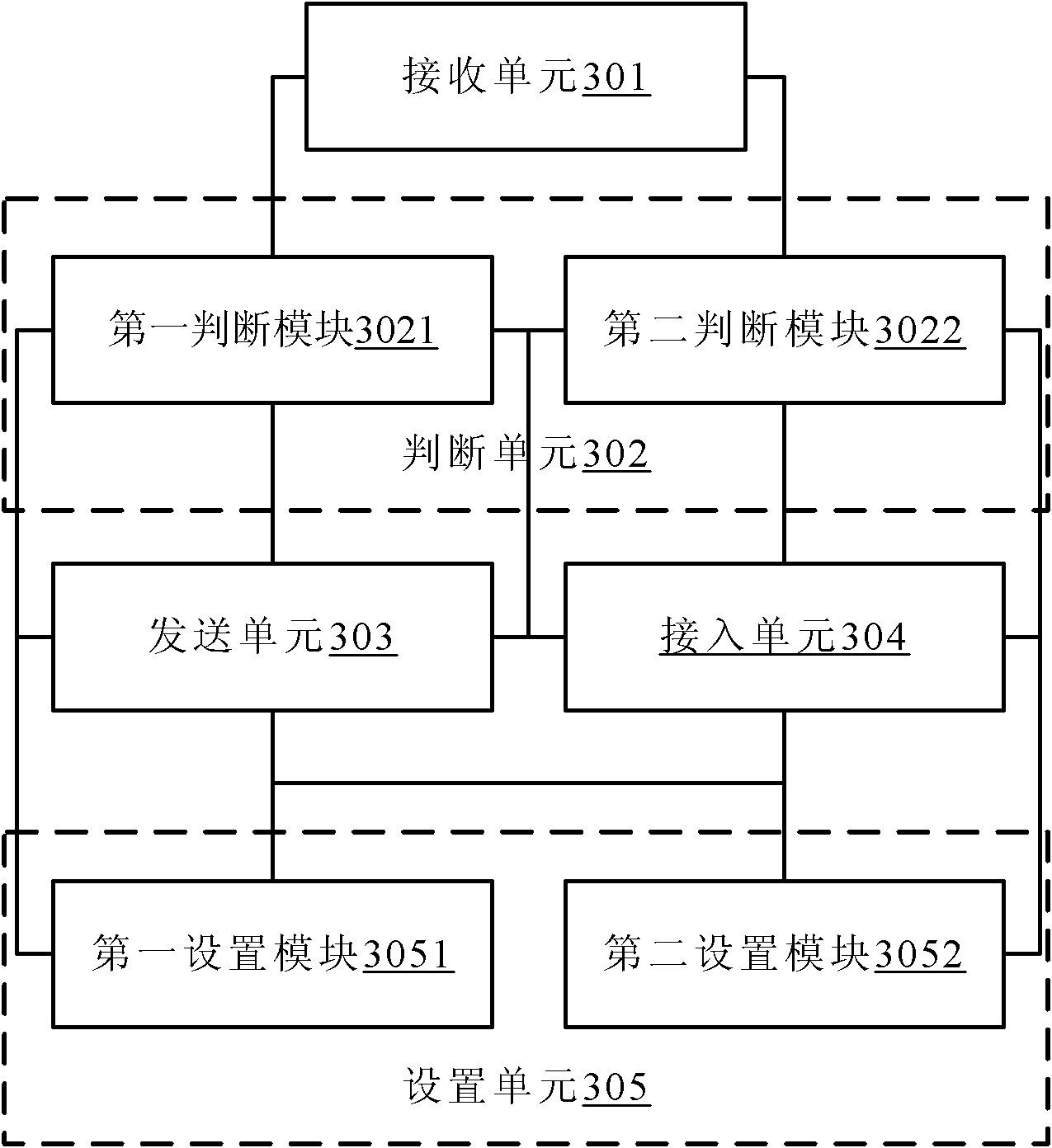
[0047] see image 3 , the present invention provides a server that adopts a scheduling method under the client / server architecture, including: a receiving unit 301 for receiving a request message from a client for requesting a single instance; a judging unit 302 for judging the client Whether the interface of the requested single instance is being accessed or whether the single instance requested by the client is being run; the sending unit 303 is used for determining whether the interface of the single instance requested by the client is being accessed or the client When the requested single instance is running, send a response message for denying client access.
[0048] In this preferred embodiment, the server judges whether the interface of the single instance requested by the client is being accessed or whether the single instance requested by the client is being run, so that the single instance can only be executed by one client at the same time , thereby solving the pro...
Embodiment 3
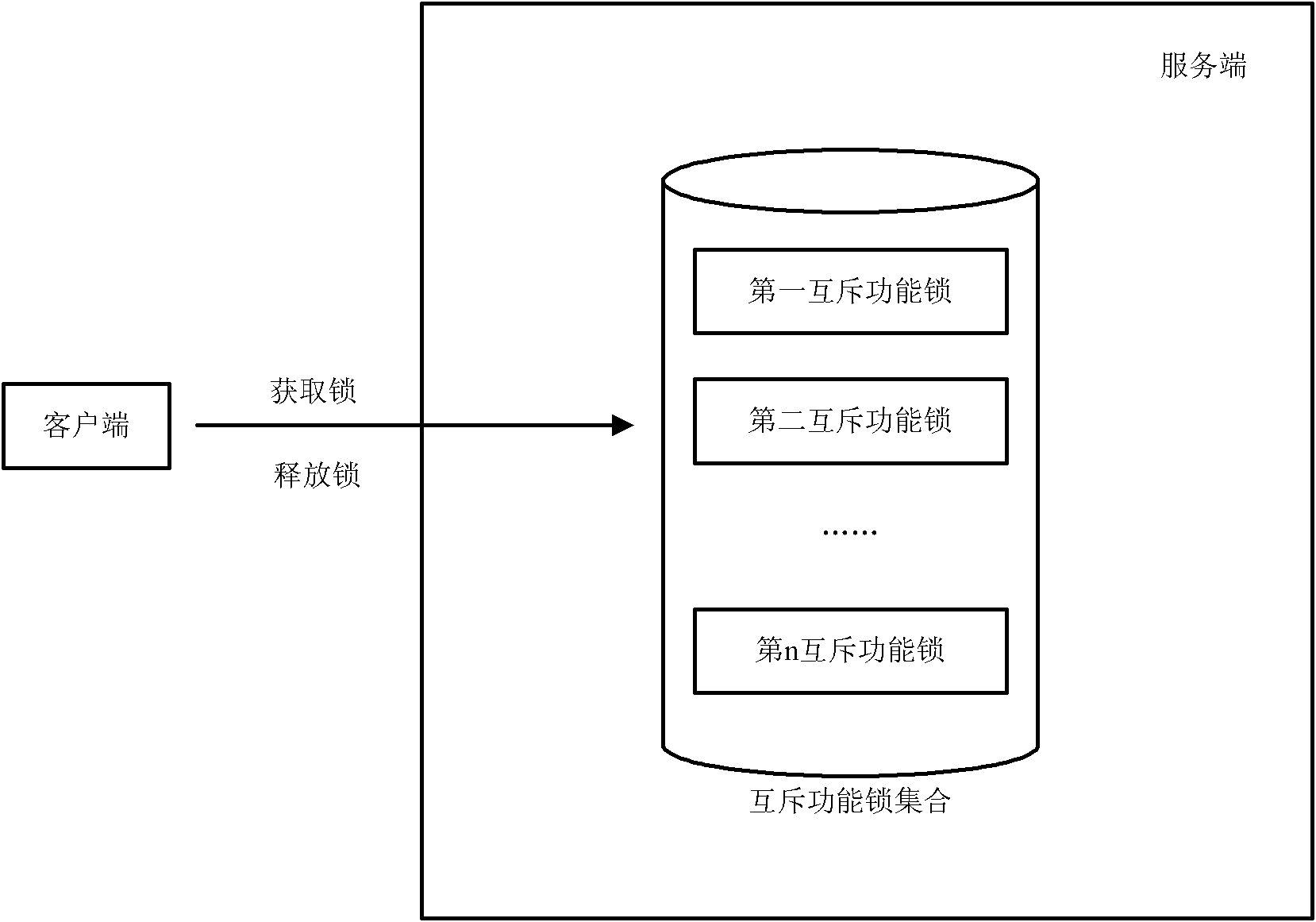
[0054] see Figure 4 , in the DL2SM scheduling method, first, a client status detector 402 (Client Status Detector) is used on the server 401 to monitor the exit of the client 403, and the specific implementation can be through a timing handshake mechanism. When the server 401 detects that the client 403 has exited abnormally without actively releasing the function lock, the server 401 will initiate the release of all locks occupied by the exiting client 403 .
[0055] Using this model with a client state detector 402 can prevent the disorder of the server 401 function mutex lock state caused by unpredictable abnormalities such as power failure and network disconnection in the client 403, and guarantee the function to a certain extent Correctness and robustness of locks.
[0056] see Figure 5 , and then, at the server end 501, a function lock attribute of Running Level (runtime level) is added for each single-instance function, which is used to indicate whether the single-i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com