Network frangibility correlation analysis method based on gradient attack hypotheses
An association analysis and vulnerability technology, applied in the field of network security, can solve problems such as difficulty in solving problems, complex vulnerability associations, difficult task division, etc., to break through large-scale application bottlenecks, avoid detours of association paths, and save computing costs Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
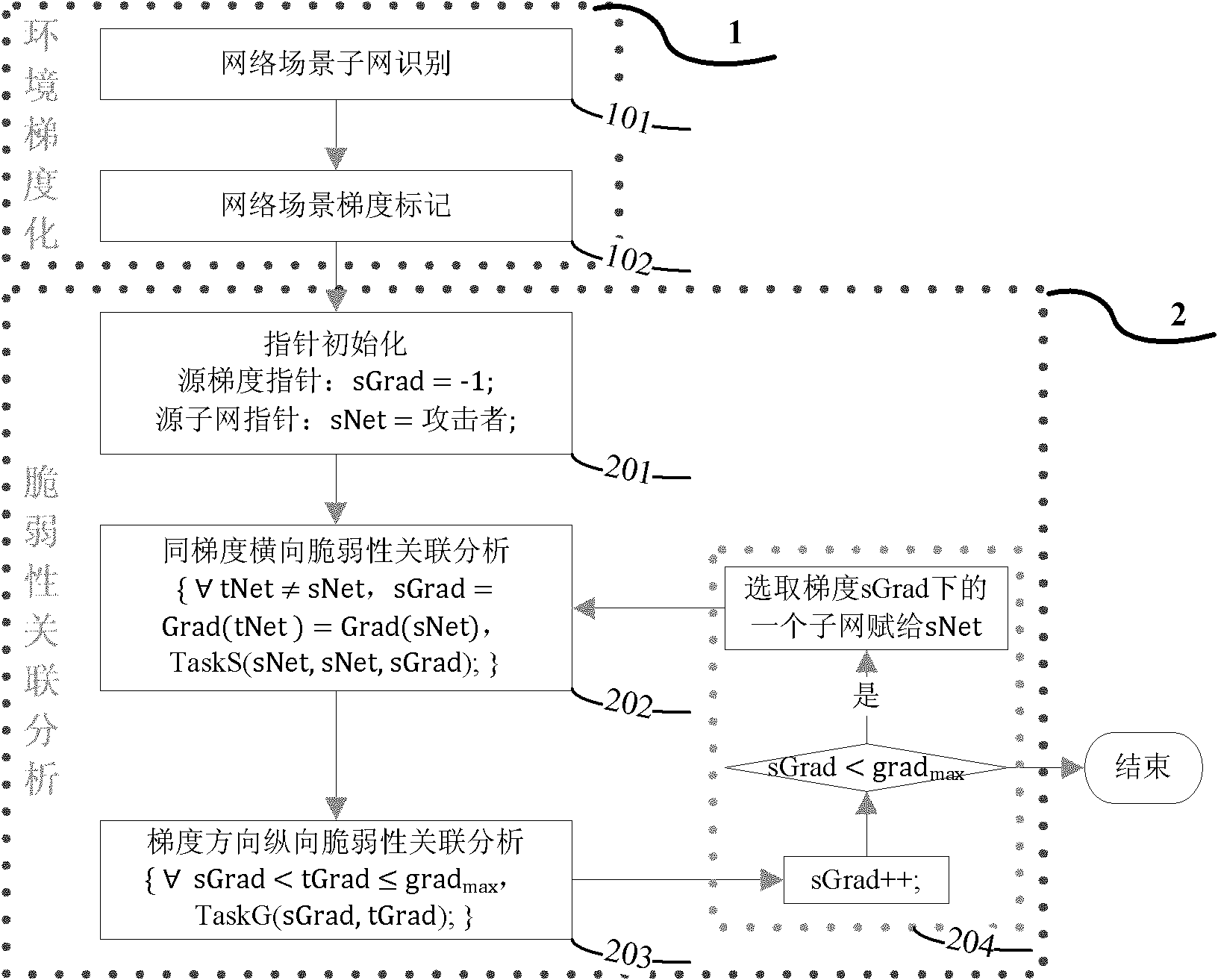
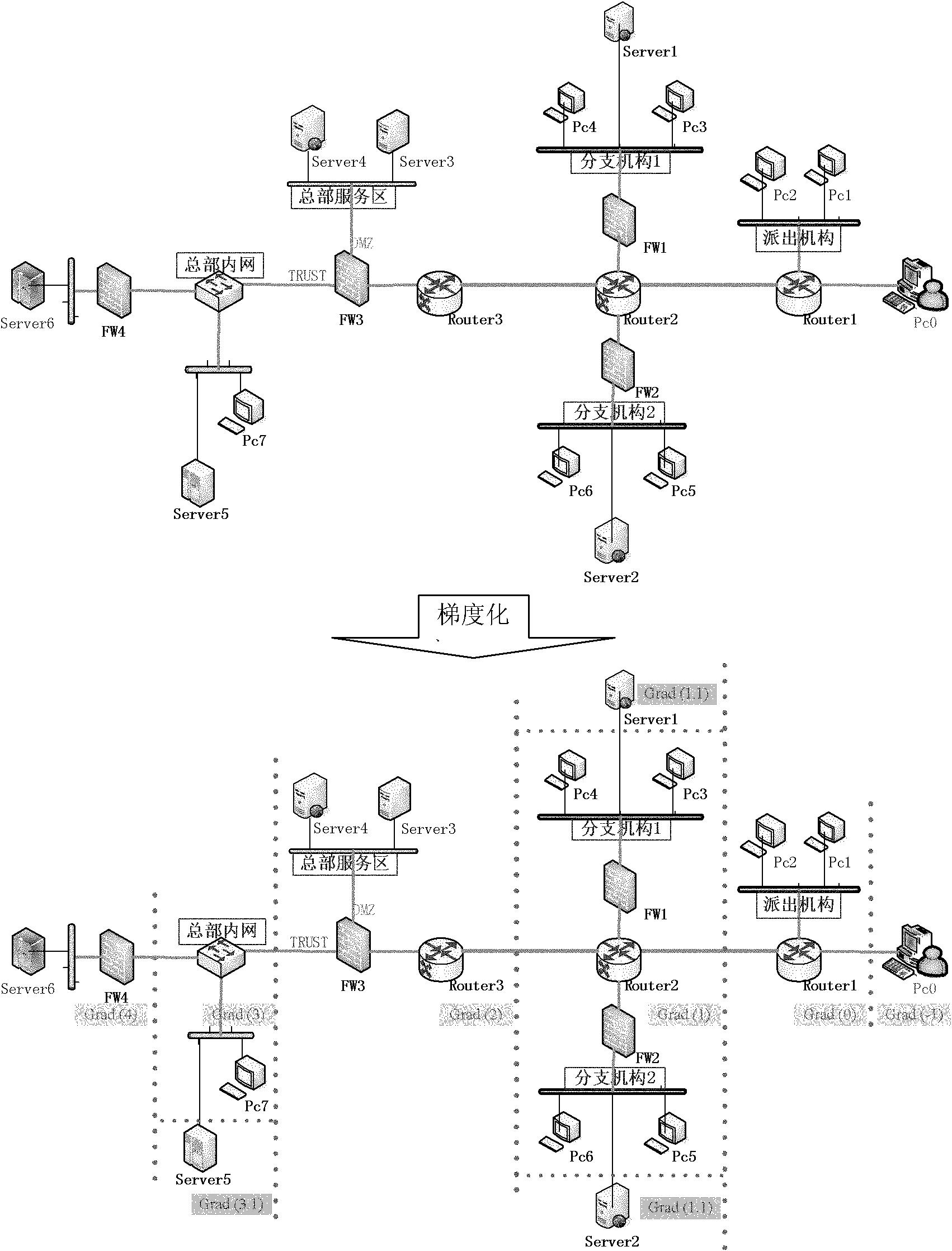
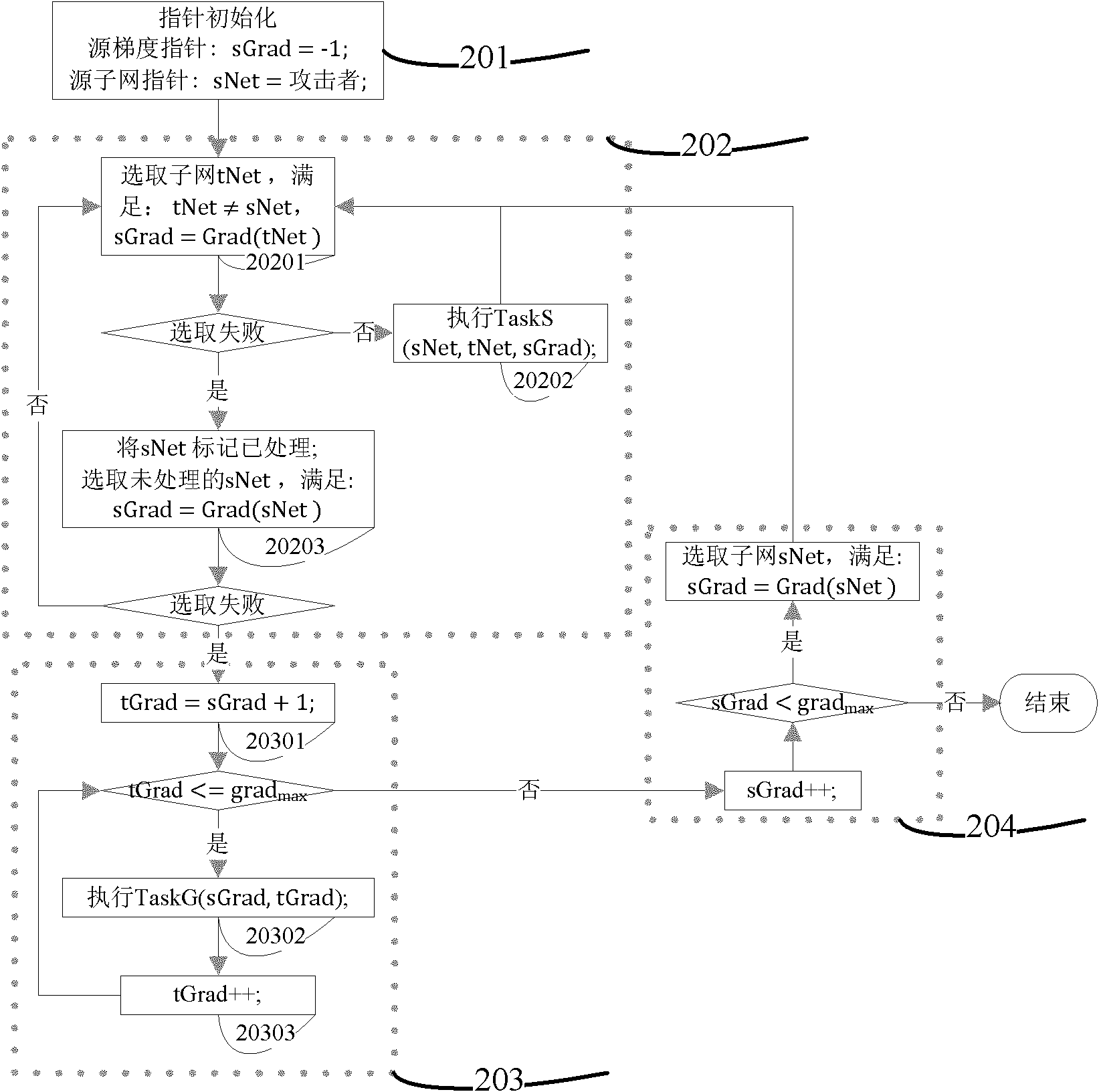
[0039] In order to illustrate the technical solutions of the present invention more clearly, several embodiments of the present invention will be introduced below in conjunction with the accompanying drawings. Those of ordinary skill in the art can also obtain other drawings or implementations based on these drawings without creative work, such as obtaining a simplified network scene gradient method and a reverse vulnerability correlation analysis method .
[0040] The following relevant definitions are used in the embodiments of the present invention:
[0041] Definition. The security gradient represents the scale of the security protection hierarchy of the network environment. Network nodes with higher gradients are more important, and network defenders pay more attention to them, and the consequences after being attacked are more serious. On the contrary, attackers will try to attack network nodes with high gradients. The security gradient reflects the level of network def...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com