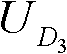Bilinear-group-based cross-domain union authentication method
A bilinear group and authentication method technology, applied in the field of network communication security, can solve the problems of authentication center network bottlenecks, symmetric key management and key negotiation complexity, and inability to defend against authentication centers, etc., to achieve good anonymity and defense Aggression, the effect of good aggressive behavior
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0082] The preferred embodiments of the present invention will be specifically described below in conjunction with the accompanying drawings.
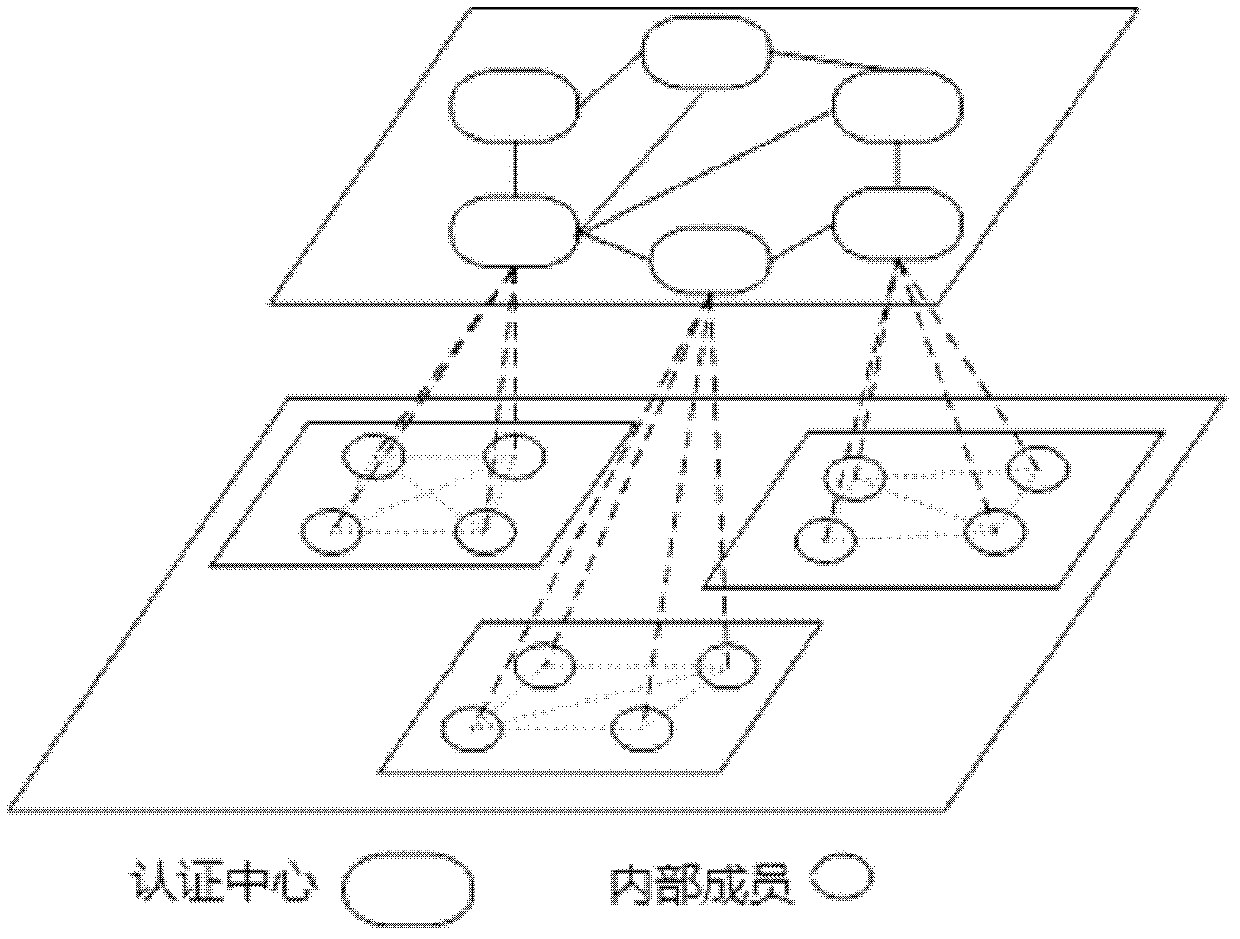
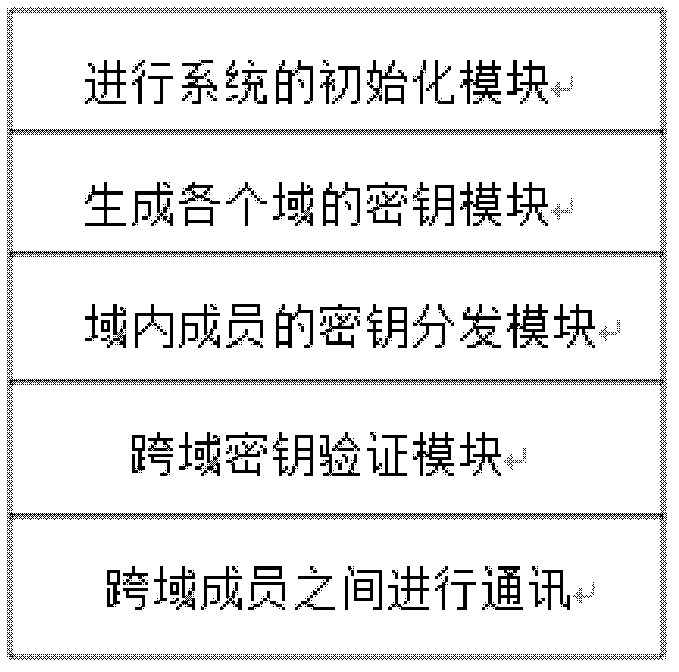
[0083] In this embodiment, the system is composed of multiple domains, and each domain is independent and autonomous, such as figure 1 shown. Each domain is composed of an authentication center and multiple internal members of the domain. The authentication center is like a traditional CA or PKG. The respective internal members are resource owners and visitors. During collaborative computing, the internal members of each domain need cross-domain access resource. Each certification center selects one of multiple heterogeneous cyclic groups, and uses this cyclic group to design its own key parameters, distributes and manages the keys in its domain, and at the same time discloses the public key of the certification center in this domain, so that mutual Inter-access and authentication. When members join the domain, real identity reg...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com