Method and device for code obfuscation
A technology of code and equipment, applied in the field of confusing software, can solve problems such as difficulties
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
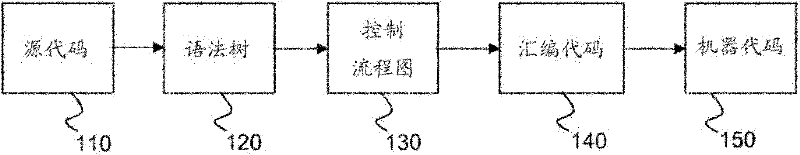
[0024] Figure 1 illustrates the prior art process of compiling software. Some basic knowledge of this routine will help in understanding the description that follows. Compilation translates source code 110 into machine code 150 via a number of intermediate steps during which syntax tree 120 , control flow graph 130 and assembly code 140 are generated.
[0025] The main idea of the present invention is to use safer branch function calls than those used by Linn and Debray. As already discussed, their branching functions can be simulated fairly easily. Although Jakubowski and Jacob made the branching function safe by making the branching function dynamic, the branching function can still be computed. This solution makes branch functions safe in different ways, as will be described in detail below.
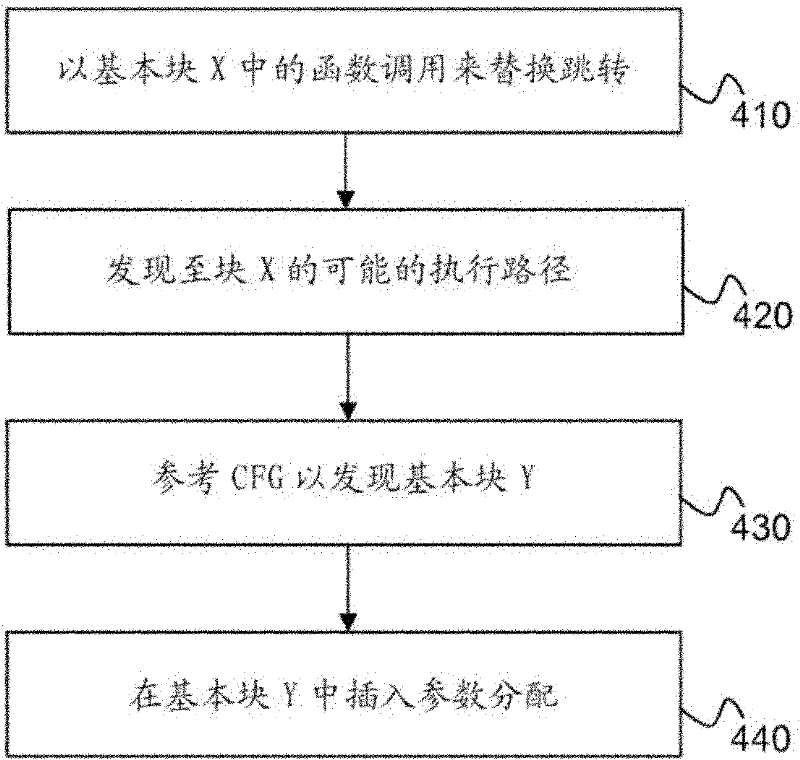
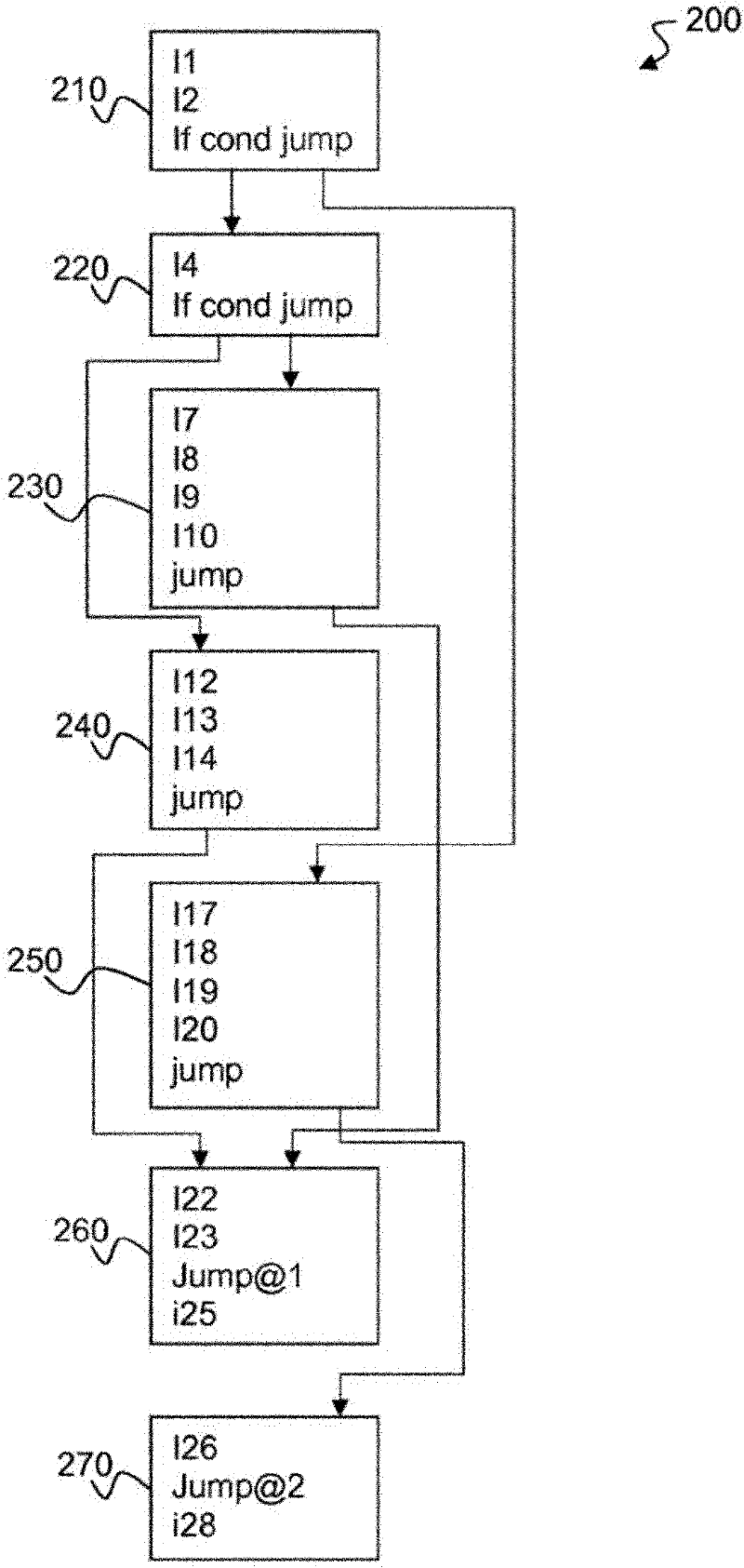
[0026] In order to easily appreciate the solution of the invention, the prior art obfuscation solution is first illustrated in FIG. 2 . Following a control flow diagram, program...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com