Collecting and analyzing malware data
A malware and threat analysis technology, applied in the field of collecting and analyzing malware data, can solve problems such as non-receipt
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
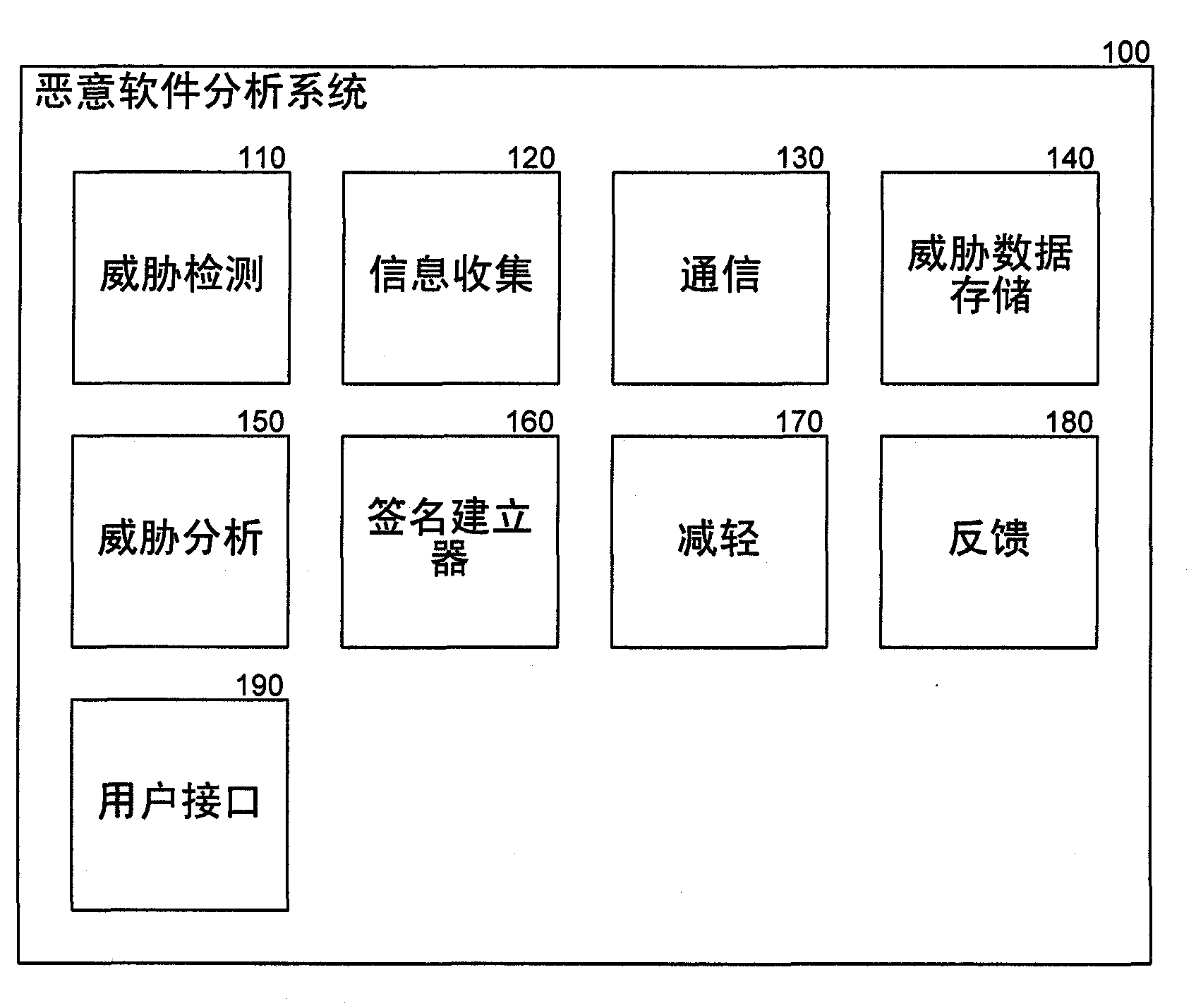
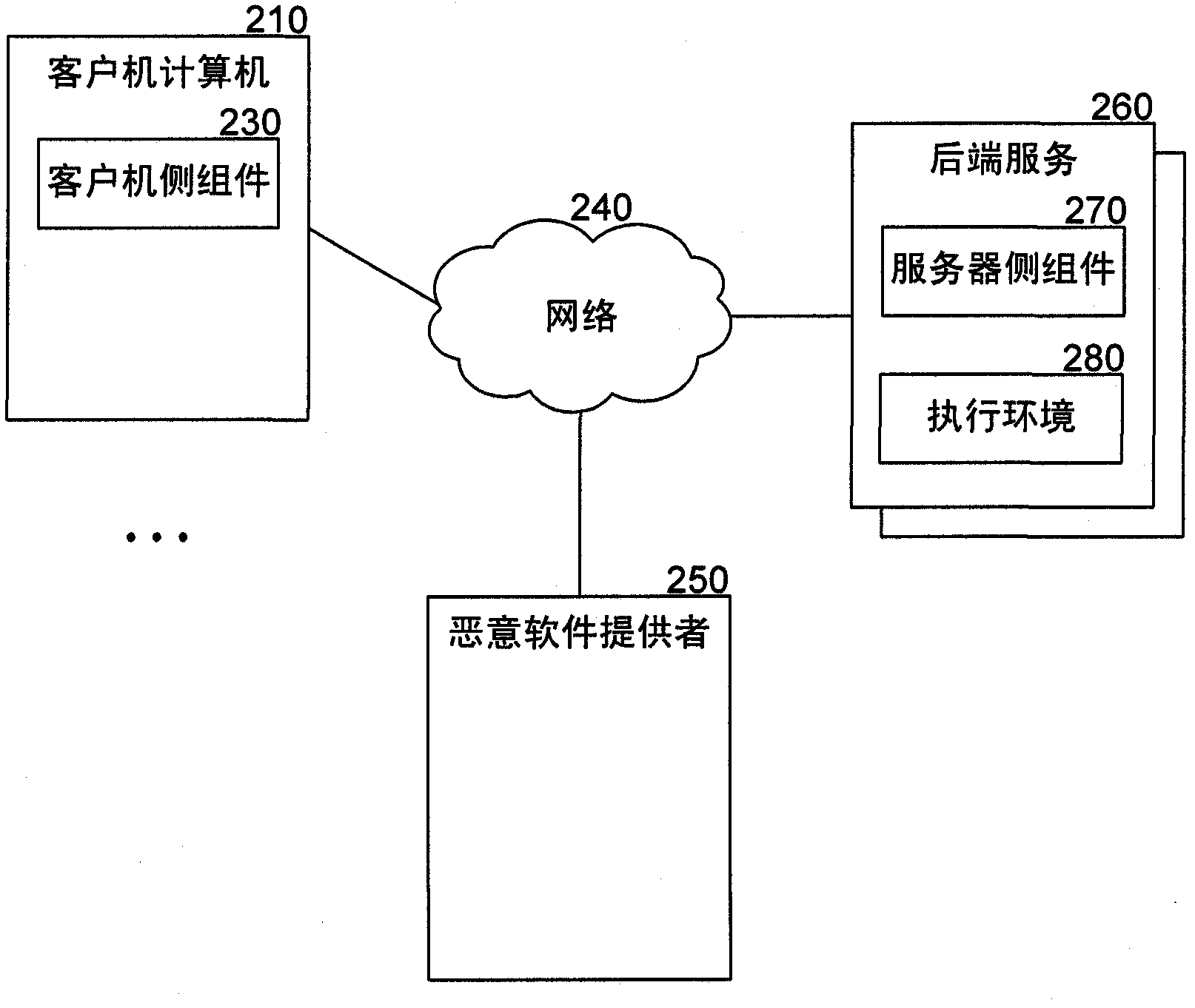
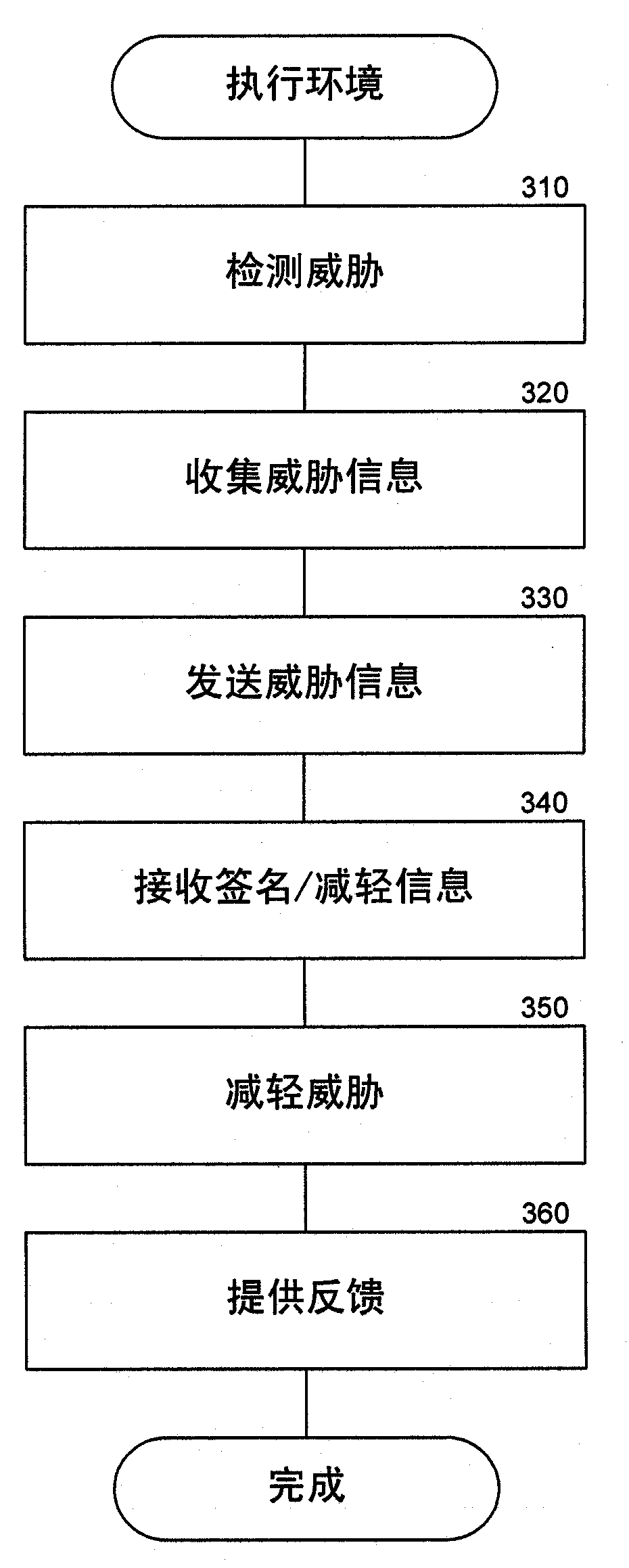
[0012] overview
[0013] A malware analysis system is described that provides information about malware execution history on client computers and allows automated back-end analysis for faster creation of signature signatures and removal instructions. The malware analysis system collects threat information on client computers and sends the threat information to a backend analysis component for automated analysis. For example, the system may collect URLs visited, user actions performed, files accessed, and other information about potential threats posed by malware. The system can trigger the collection of threat information when certain events occur, such as when an application attempts to access a website. The backend analysis component analyzes the threat information by comparing the threat information to information about known threats. For example, the backend analysis component can identify similar previous threats based on the threat information, and classify new threa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com