A control method, device and system for a user identification card
A technology for user identification and control device, applied in the control field of user identification card, can solve problems such as high arrears, loss of SIM card control, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
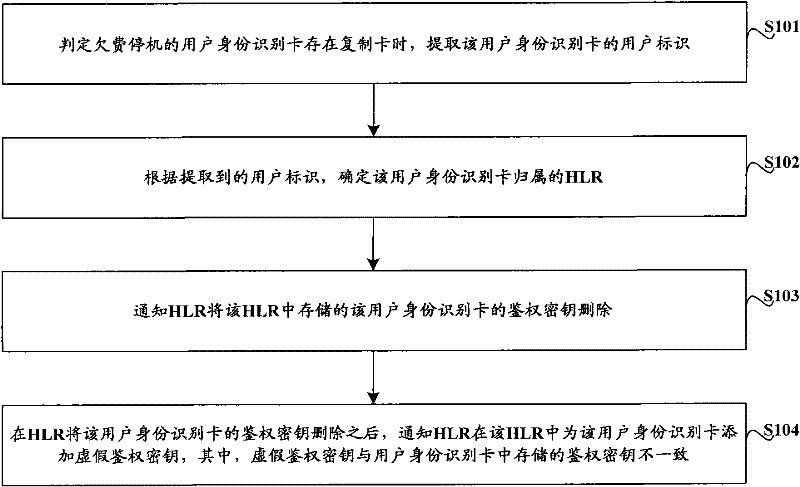
[0030] Such as figure 1 As shown, the control method of the user identification card provided by the embodiment of the present invention includes the following steps:
[0031] S101. When it is determined that there is a duplicate card in the user identification card for the arrears shutdown, extract the user identification of the user identification card;
[0032]The user identifier of the user identification card may be the MSISDN of the user identification card, or the IMSI of the user identification card.
[0033] S102. According to the extracted user identification, determine the HLR to which the user identification card belongs;
[0034] In specific implementation, the corresponding relationship between the user identification and the location information of the HLR can be stored in advance, and the location information of the HLR corresponding to the user identification can be obtained by querying the corresponding relationship stored in advance, and the user identity c...
Embodiment 2
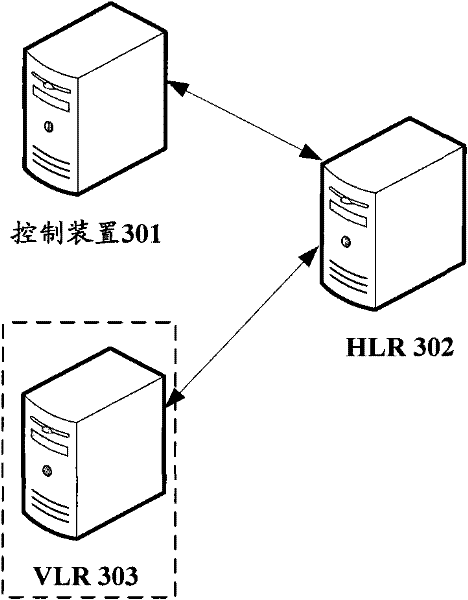
[0059] Based on the same technical idea, the embodiment of the present invention provides a control system for user identification cards, such as image 3 As shown, it includes a control device 301 and an HLR 302. Preferably, the control device 301 can be set in a BOSS (Business Operation Support System, business operation support system), and of course it can also be set in other network entities. in:
[0060] The control device 301 is configured to extract the user identification of the user identification card when there is a duplicating card in the user identification card that is suspended due to arrears; determine the HLR to which the user identification card belongs according to the extracted user identification; and notify the HLR Delete the authentication key of the user identification card stored in the HLR;
[0061] The HLR 302 is configured to delete the locally stored authentication key of the subscriber identity card according to the notification sent by the con...
Embodiment 3
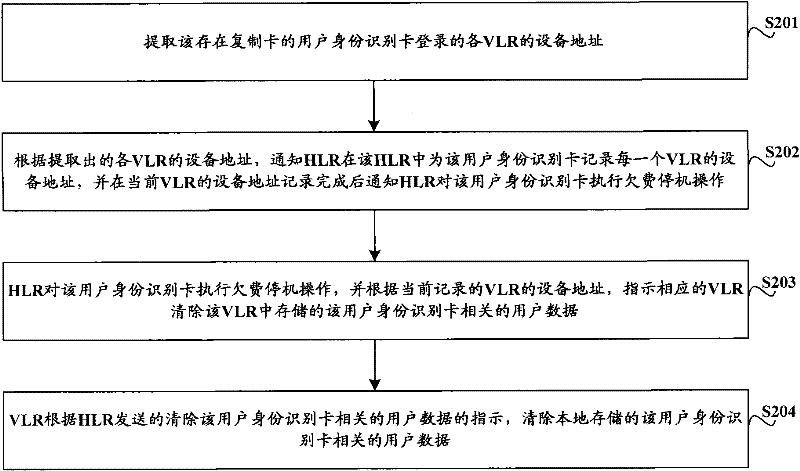
[0083] Taking the suppression of a SIM card with duplicate cards from producing a large number of spam short messages and causing high arrears as an example, a better SIM card control method provided by the embodiment of the present invention is introduced in detail, assuming that the BOSS in the existing GSM system is To transform, the control device provided by Embodiment 2 is set in BOSS, such as Figure 5 shown, including the following steps:
[0084] S501. If the SIM card that is shut down due to payment sends a short message, the BOSS obtains the shutdown time of the SIM card that is stopped due to payment;
[0085] S502, BOSS compare short message sending time and downtime, if the short message sending time is after the set time length from the downtime point, then it is determined that the SIM card has a duplicate card, and the SIM card is extracted from the billing bill MSISDN number and device addresses of all VLRs logged in by the SIM card;
[0086] S504. The BOSS...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com