Method and system for safe operation of shell script based on sandbox technology
A safe operation and sandbox technology, applied in the field of information system security, can solve the problem that malicious scripts cannot provide security guarantees, and achieve the effect of enhancing security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
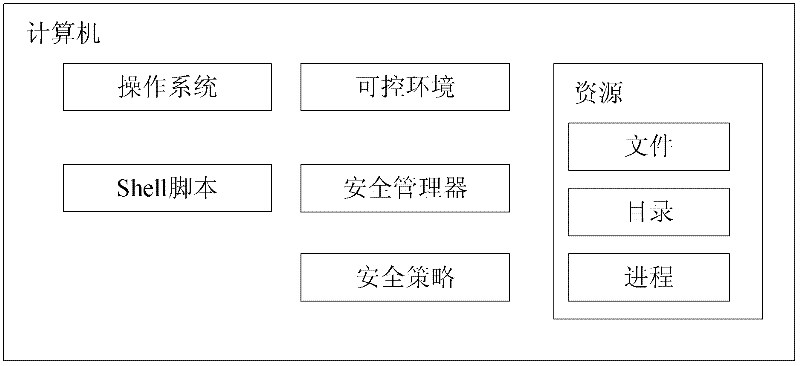
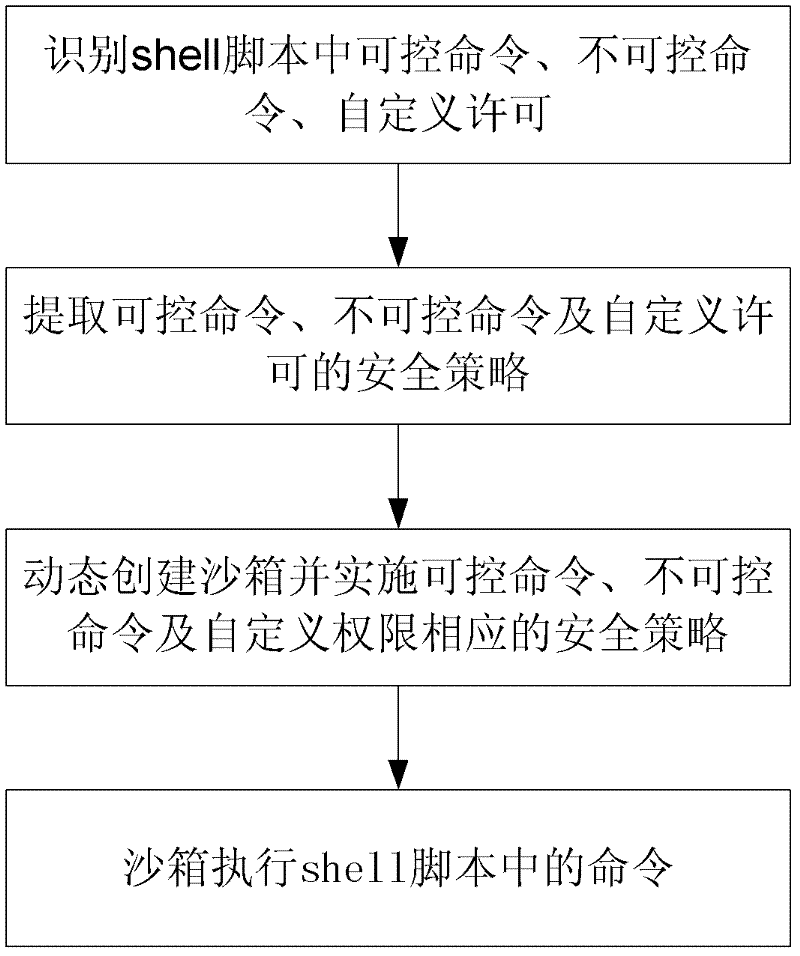
[0024] figure 1 It shows the structure of the shell script safe running system based on the sandbox technology of the present invention. This computer system comprises operating system, shell script, controllable environment, security policy, security manager and accessible resource, wherein controllable environment, security policy, security manager constitute the present invention's shell script safe running system based on sandbox technology . A typical computer contains an operating system. Shell scripts can be downloaded from the network, hard disk, CD, etc. These scripts can be safe or unsafe. The scripts can run in the foreground or in the background. The source and code of the script will affect the security manager What kind of security policy to adopt.
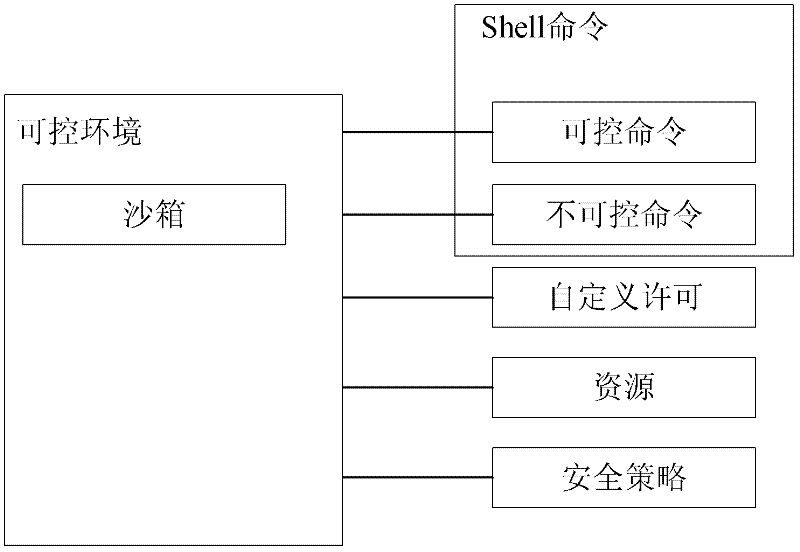
[0025] The controllable environment refers to the shell applying the security policy of the present invention, and shell scripts can be run on the shell. The controlled environment can configure (eg load) securit...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com