Authentication device, authentication method, and program to execute same by computer
A technology for authentication equipment and project teams, applied in the field of programs that enable computers to execute the authentication method, can solve problems such as complicated operations and difficulty in remembering passwords, and achieve the effects of improving security and reducing the possibility of inappropriate authentication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] Hereinafter, embodiments of the present invention will be described with reference to the accompanying drawings.
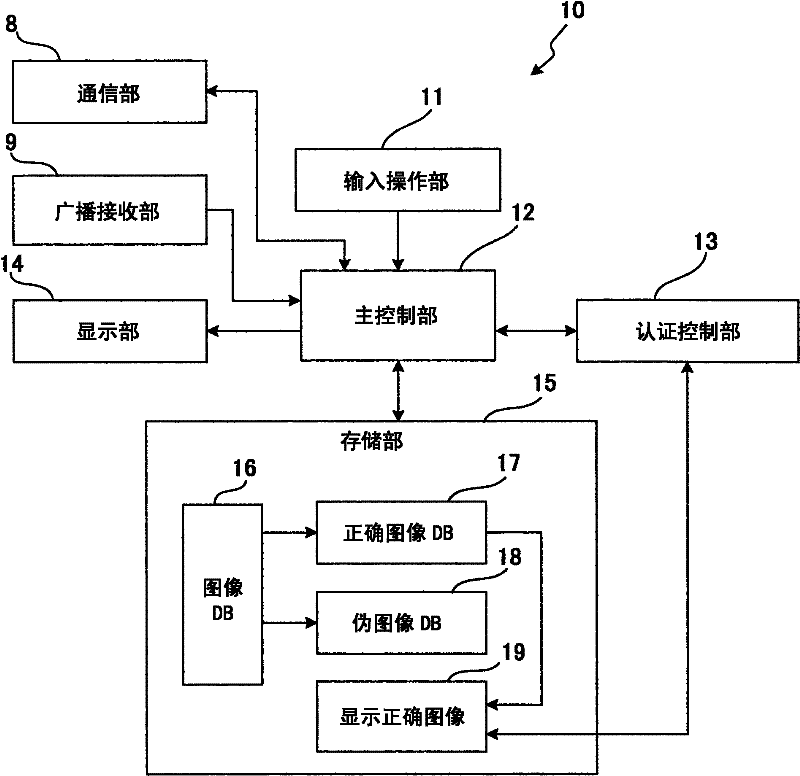
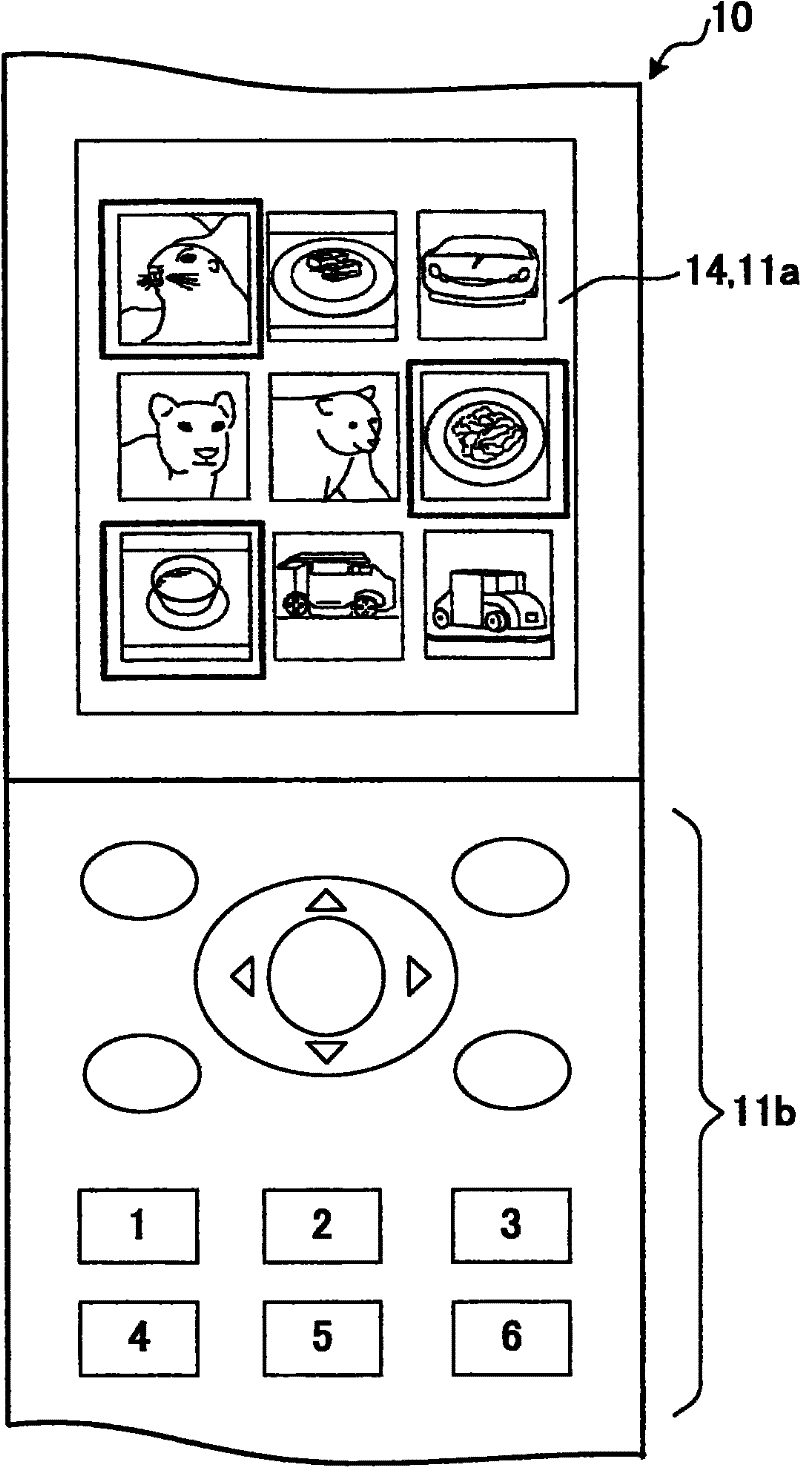
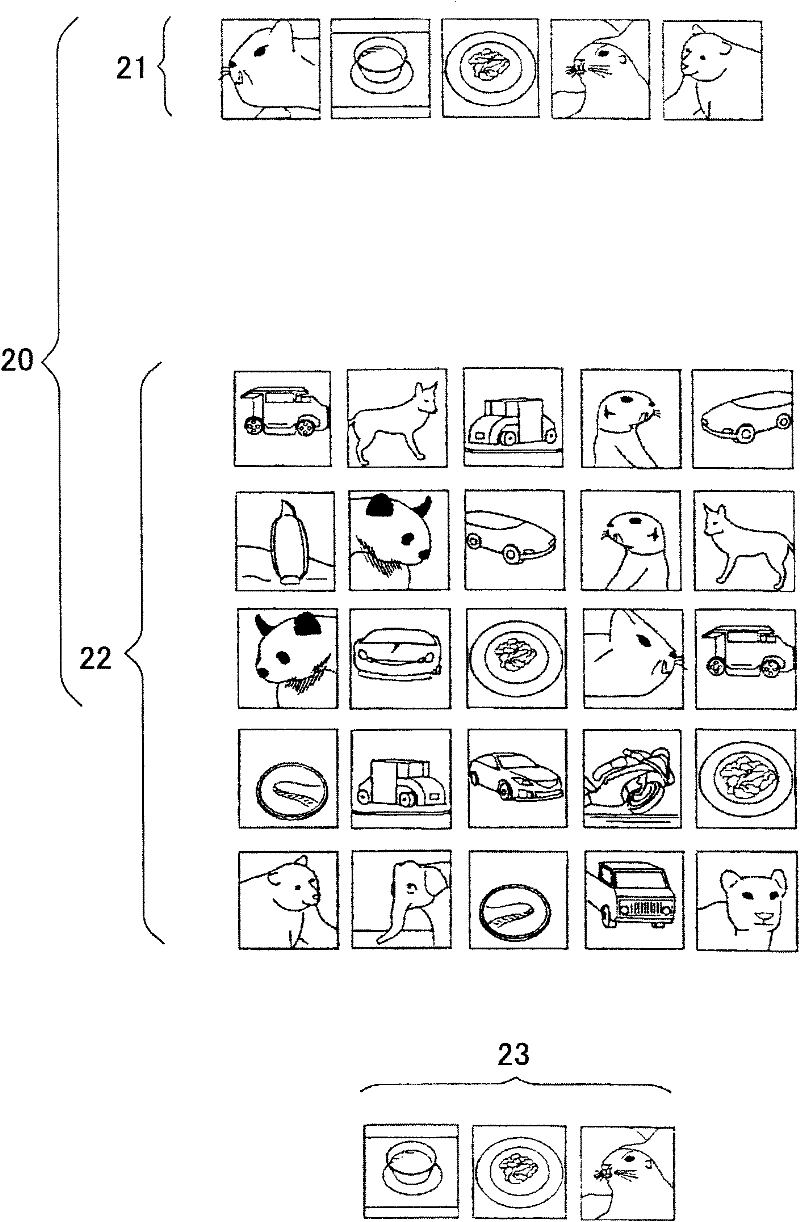
[0030] figure 1 is a block diagram showing an embodiment of an authentication device according to the present invention. figure 2 is an explanatory diagram in which image display is performed by a mobile phone as an authentication device. In this embodiment, a portable phone functions as an authentication device, however the present invention is not limited thereto, and an information terminal such as a personal computer or a PDA may also be used.
[0031] This authentication device (mobile phone) 10 has a communication unit 8 , a broadcast receiving unit 9 , an input operation unit 11 , a main control unit 12 , an authentication control unit 13 , a display unit 14 and a storage unit 15 .
[0032] The communication section 8 includes a telephone call function and a mail function and an access function to a network such as the Internet, like a portable p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com