Method and device for generating dynamic passwords
A technology of dynamic passwords and commands, applied in the field of identity authentication, can solve problems such as affecting users' rights and interests, data tampering, and damage to users' interests.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
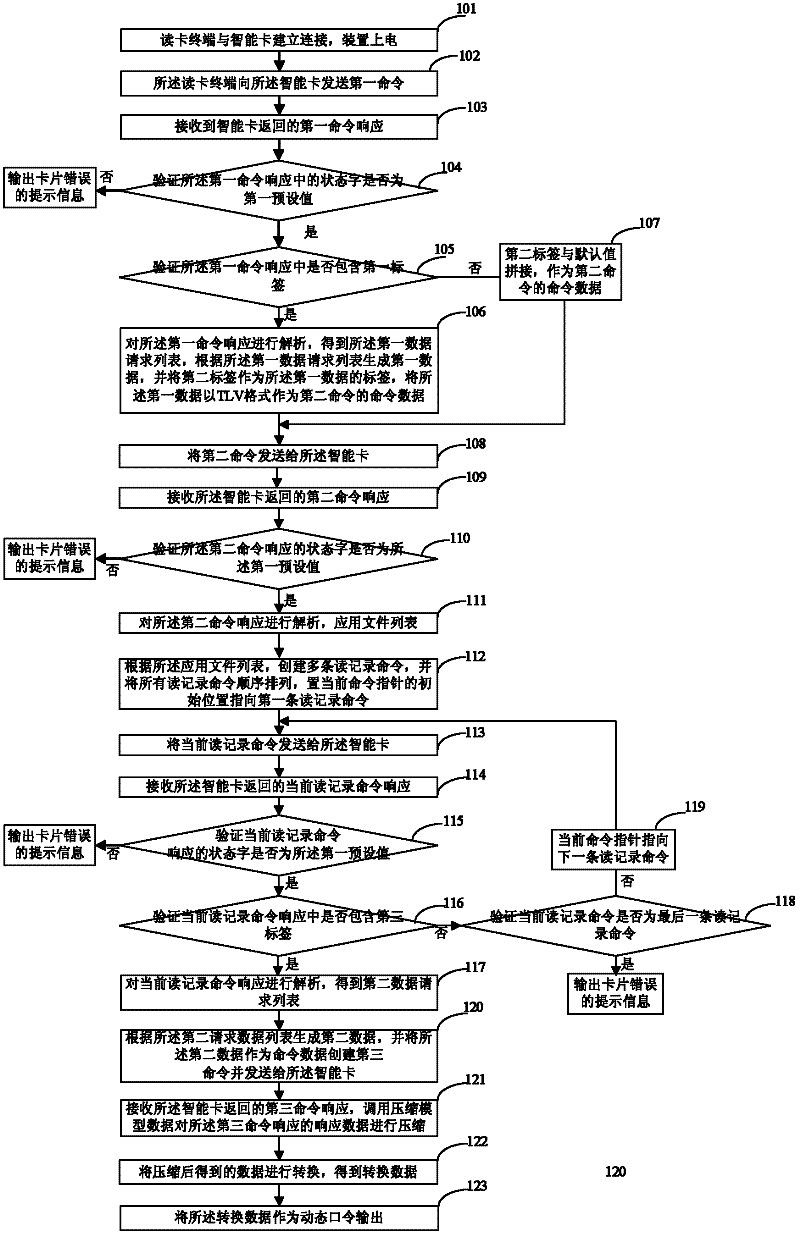
[0076] see figure 1 , Embodiment 1 of the present invention provides a method for generating a dynamic password, the specific steps are as follows:
[0077] Step 101: The card reader terminal establishes a connection with the smart card, and the device is powered on;
[0078] Preferably, in this embodiment, after the card reader establishes a connection with the smart card, the circuit is turned on, the device is automatically powered on, and when the power-on time reaches a preset time, the device is automatically powered off.
[0079] Preferably, in this embodiment, after the device is powered on, the following steps may also be included:
[0080] Step 101-1: The card reader terminal prompts the user to input a PIN code;
[0081] Preferably, in this embodiment, the PIN code may be the PIN code of the card reader terminal, or the offline PIN code of the smart card.
[0082] Step 101-2: Obtain the PIN code entered by the user, and verify whether the PIN code entered by the ...
Embodiment 2
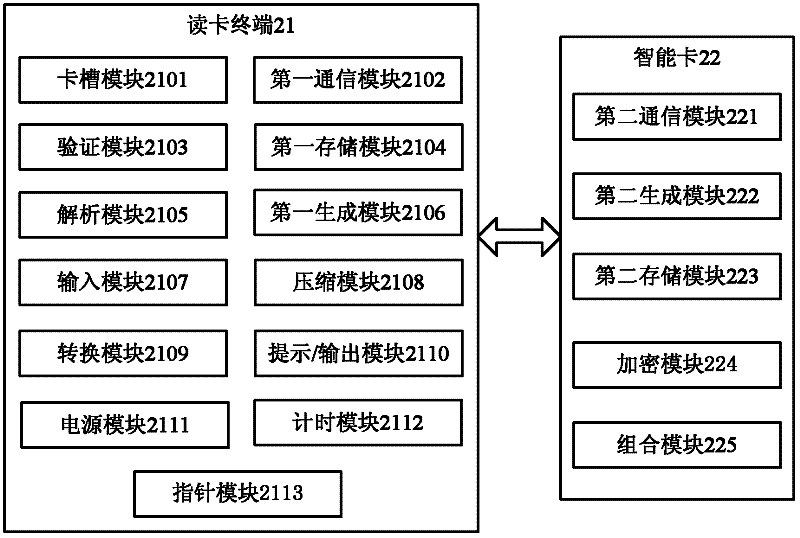
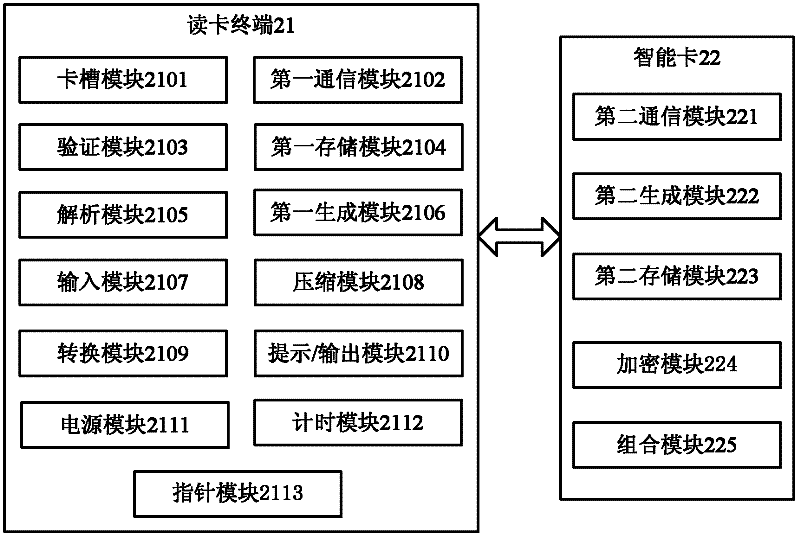
[0147] see figure 2 , Embodiment 2 of the present invention provides a device for generating a dynamic password, including a card reader terminal 21 and a smart card 22, specifically as follows:
[0148] The card reader terminal 21 includes
[0149] The card slot module 2101 is used to establish a connection between the card reader terminal 21 and the smart card 22;
[0150] The first communication module 2102 is configured to send the first command to the smart card 22; receive the first command response sent by the smart card 22 to the card reader terminal 21; send the second command to the smart card 22; receive The second command response sent by the smart card 22; for sending the third command to the smart card 22; sending the third command, receiving the third command response returned by the smart card; for sending the read record command to the smart card, and receive the read record command response returned by the smart card; it is also used to realize the transmi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com