Multiple-access-level lock screen
A lock screen, access level technology, applied in the field of multi-level access lock screen
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 4
[0025] Example 4 - An Exemplary System Employing Various Technology Combinations
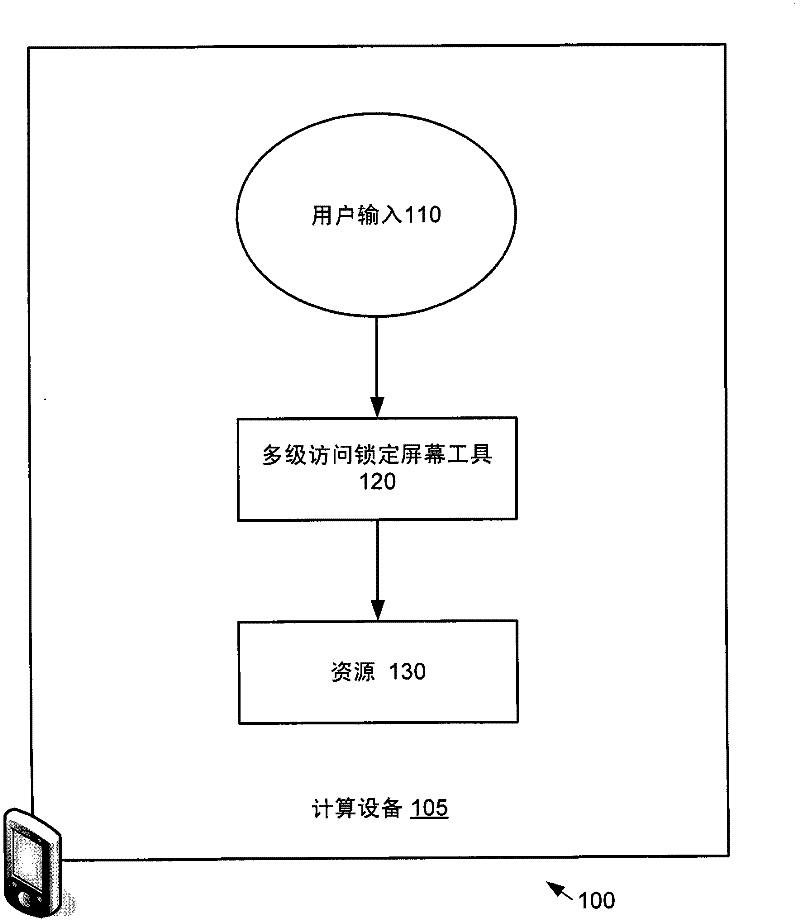
[0026] figure 1 is a block diagram of an example system 100 that implements one or more of the multi-level access lock screen techniques described herein. In this example, computing device 105 implements a multi-level access lock screen utility 120 that accepts user input 110 . User input 110 may include touch-based user input, such as one or more gestures on a touch screen. For example, a device operating system (OS) with a touch-based user interface (UI) system may receive touch-based user input information (e.g., indication information such as speed, direction, etc.), interpret it, and provide the interpreted touch-based User enters information to submit to multi-level access lock screen tool. Alternatively, user input 110 may include other input, such as keyboard input.
[0027] The multi-level access lock screen tool 120 presents a lock screen pane to the user. The multi-level access l...
example 8
[0042] Example 8 - An Exemplary Method of Applying a Combination of Techniques
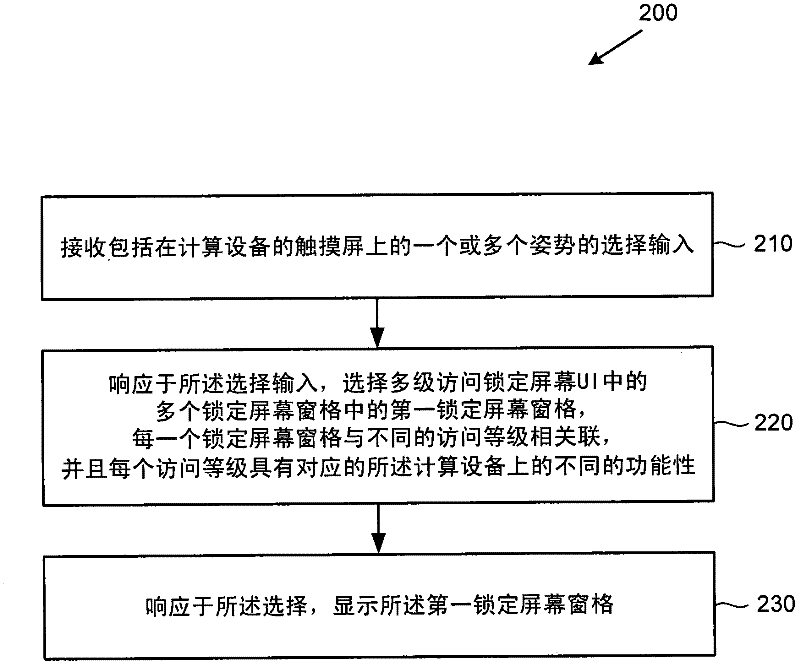
[0043] figure 2 is a flowchart of an exemplary method 200 for implementing one or more of the multi-level access lock screen techniques described herein, and the method may be used, for example, in figure 1 implemented in the system shown. The techniques described herein may be generalized to operating system or hardware details, and may be applied in any of a variety of environments to take advantage of the described features.
[0044] At 210, the computing device receives a selection input comprising one or more gestures at a touchscreen of the computing device. For example, a user performs a gesture on a touchscreen of a computing device in a locked state. At 220, in response to the selection input, the computing device selects a first lock screen pane of the plurality of lock screen panes in the multi-level access lock screen user interface. Each lock screen pane of the plurality of lock ...
example 13
[0061] Example 13 - An Exemplary Method of Applying a Combination of Techniques
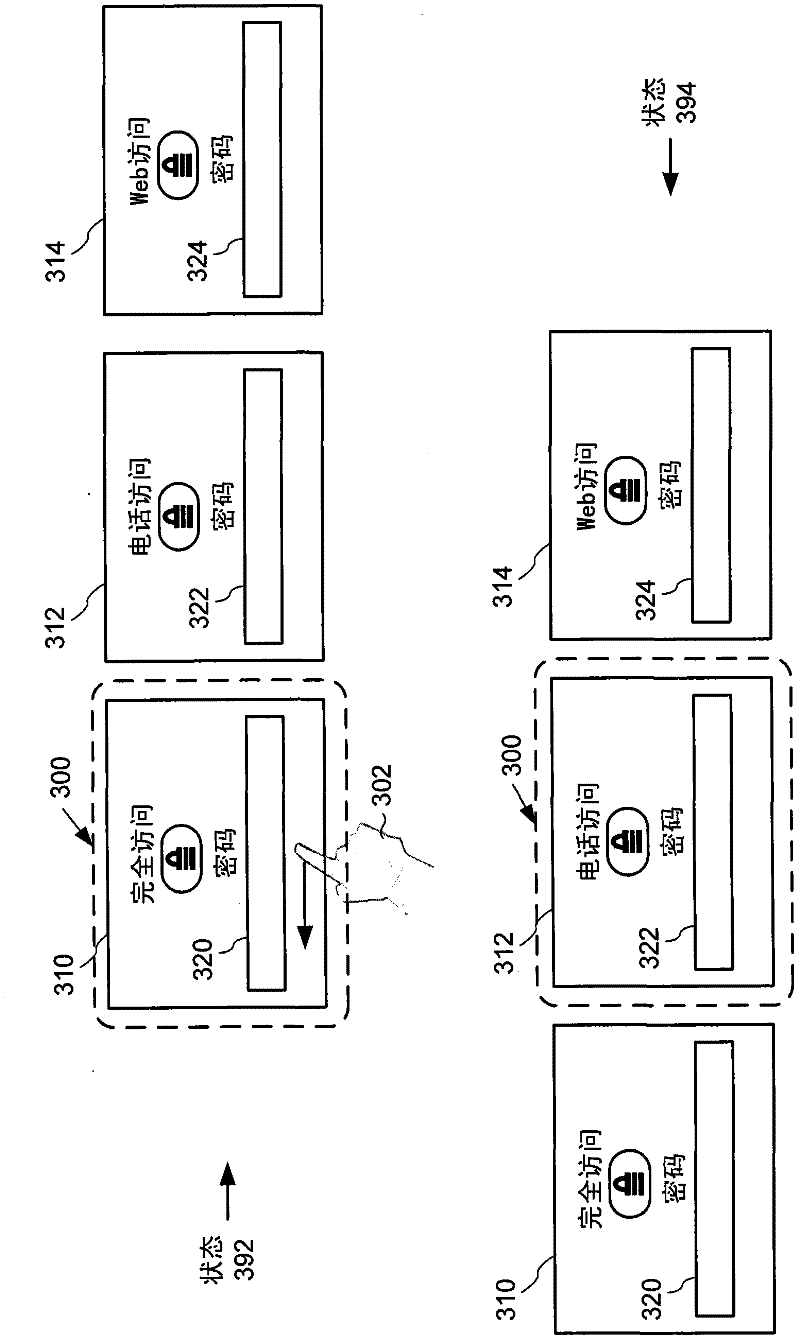
[0062] Figure 5 is a flowchart of an exemplary method 500 for implementing the multi-level access lock screen techniques described herein, and may be used, for example, in figure 1 implemented in the system shown.
[0063] At 510, the system receives an indicator at a computing device. For example, the system may receive a new text message or some other event, such as an indicator of a phone call. At 520, in response to the indicator, the system selects a lock screen pane from a multi-level access lock screen user interface that includes multiple lock screen panes, each lock screen pane associated with a different access screen having a corresponding different functionality. grades are associated. Such a lock screen pane may be referred to as an event-triggered lock screen pane. The selected lock screen pane is associated with an access level having a corresponding functionality associated ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com