Method for aggregating security situation of hierarchic network
A network security and security posture technology, applied in data exchange networks, digital transmission systems, electrical components, etc., can solve problems such as poor network security posture, and achieve the effect of improving rationality and accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
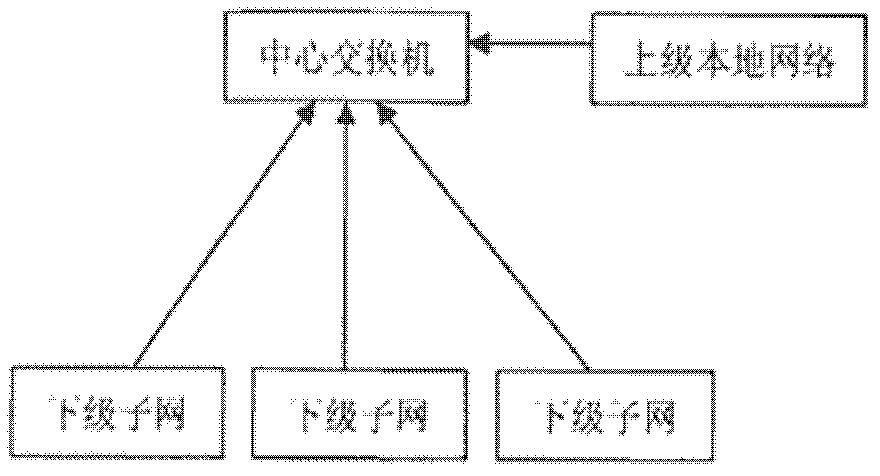
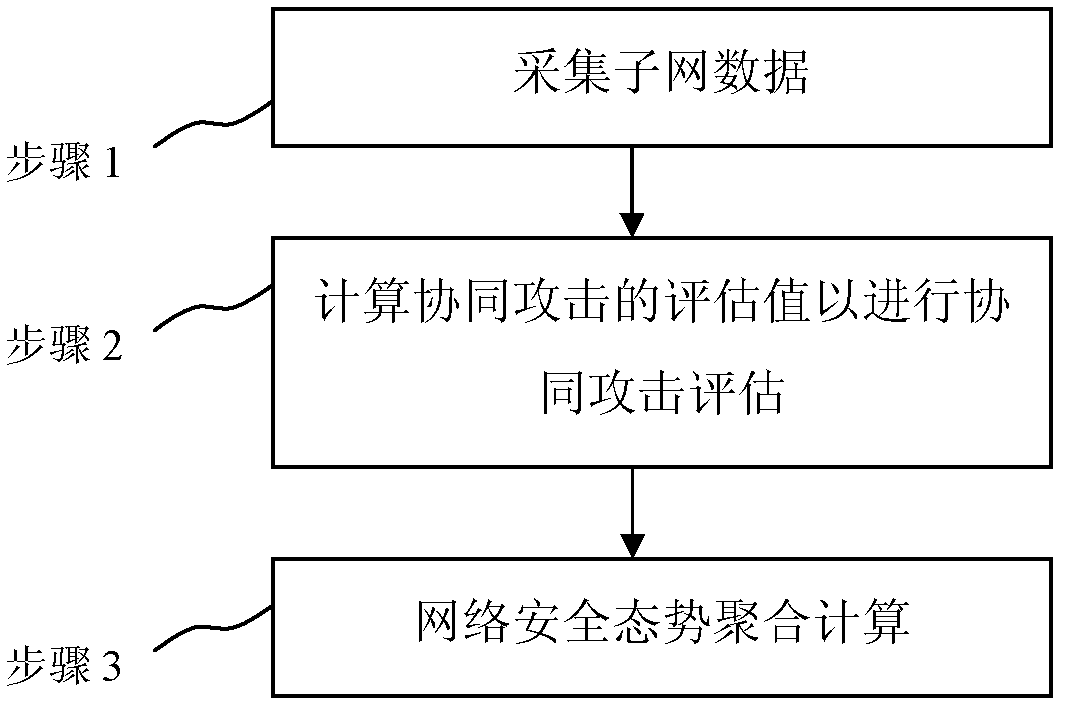
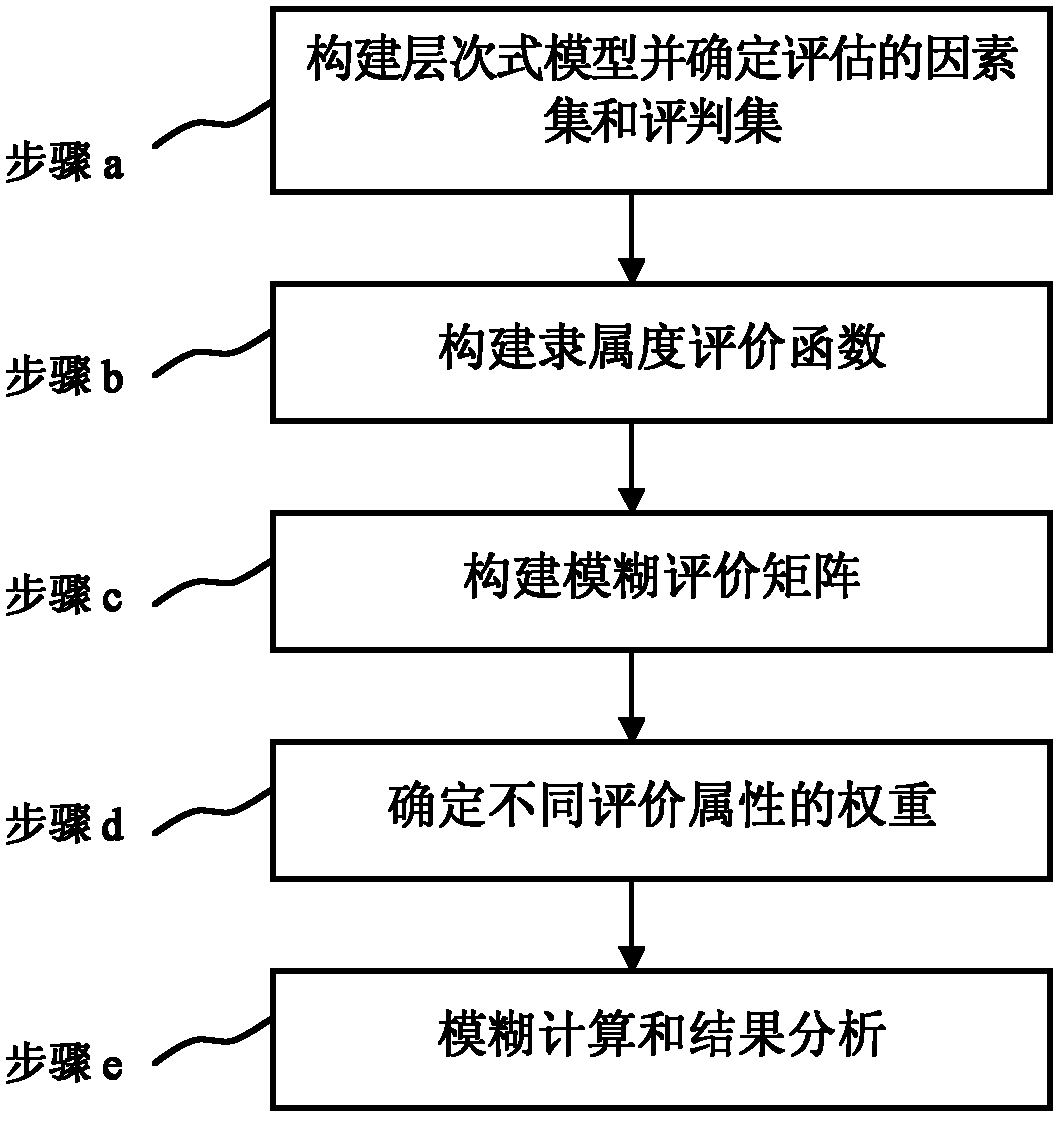
[0013] How to aggregate the security situation of the lower-level sub-networks to obtain the security situation of the upper-level network is an important issue in the assessment of the hierarchical network security situation. In order to reasonably, accurately and quickly assess the security situation of a large-scale hierarchical network, the present invention makes a compromise between the above two prior technologies, and mainly solves the problems of rationality and accuracy in the subnet situation aggregation algorithm. The security situation of the upper-layer network is not just a simple aggregation of the security situation of the lower-layer subnets. The correlation of situations between subnets will have a significant impact on the security situation of the overall network. And because not all security events that occur in a subnet will have a great impact on the security situation of the entire upper-level network, some security events may only occur in a certain su...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com