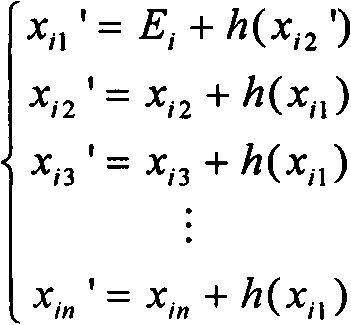Secure network coding transmission method and secure network coding transmission device using cache nodes
A secure network and caching node technology, applied in the field of communication, can solve the problems of confidentiality violation, large amount of encryption, huge calculation amount, etc., and achieve the effect of reducing complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] According to the description of the summary of the invention, the embodiments are specified here.
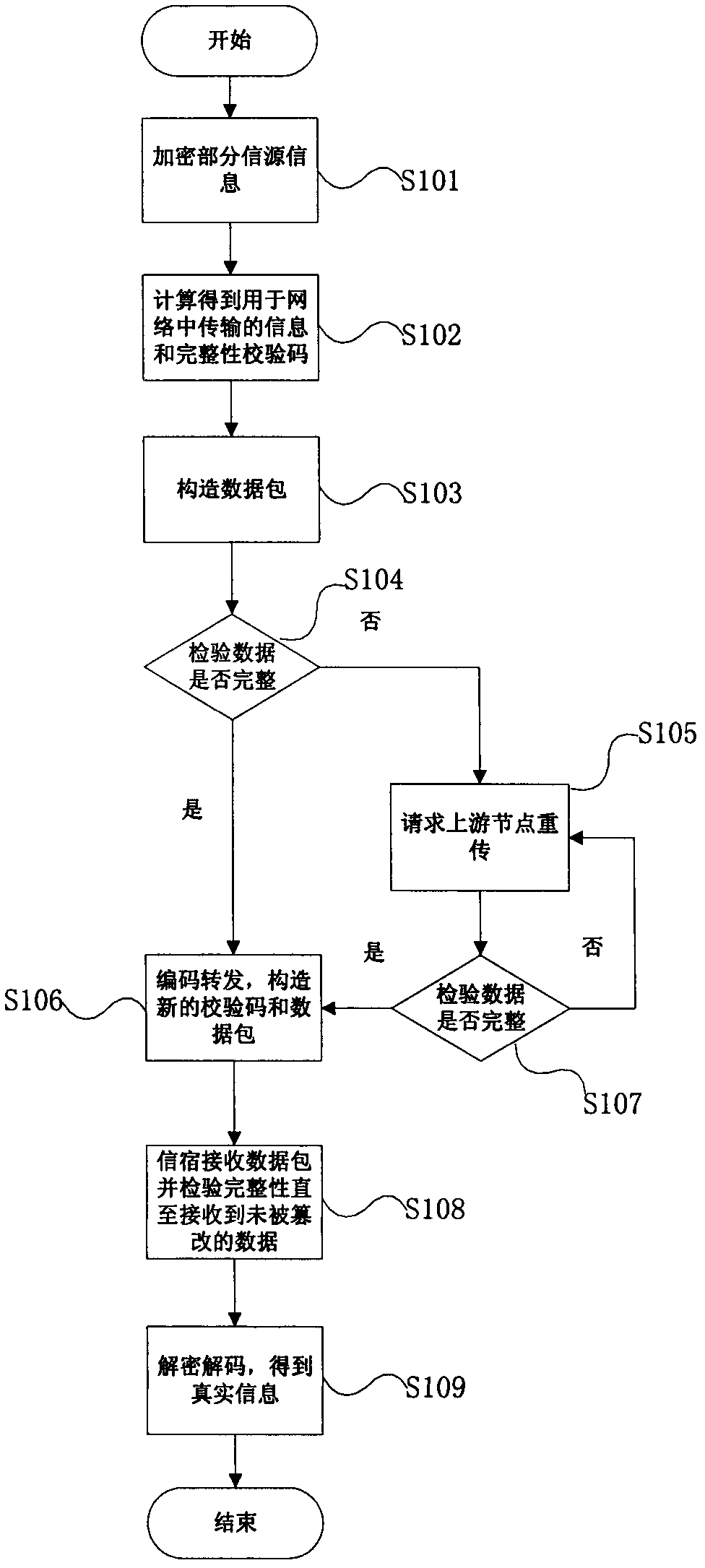
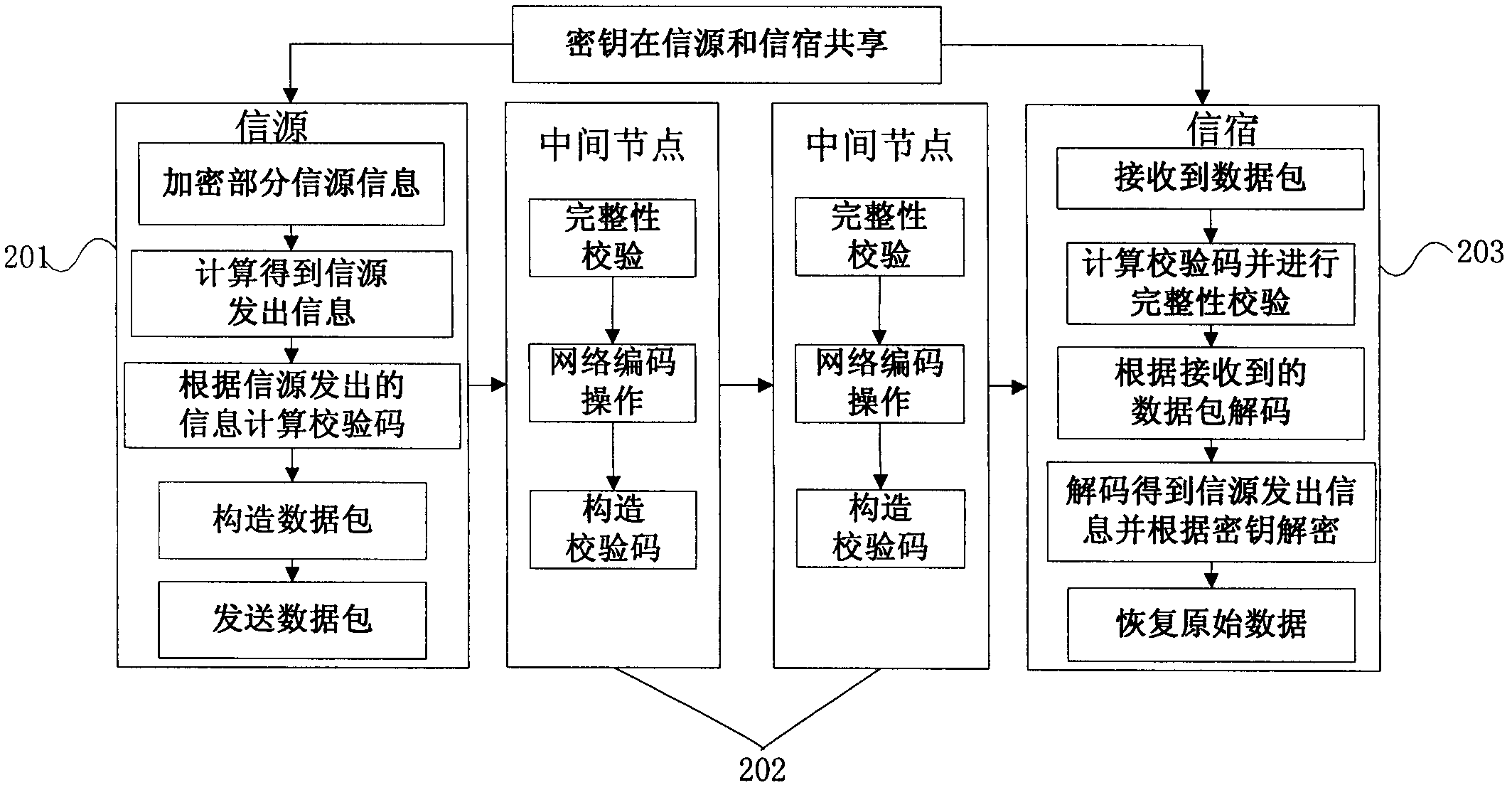
[0024] figure 1 Is the flow chart of the present invention, such as figure 1 As shown, the transmission process of the data packet is carried out in the order of the source, the intermediate node and the sink, and the operation of the source, the intermediate node and the sink on the data packet is different, so the present invention is introduced in three parts.
[0025] Information source: The information source has the functions of constructing data packets and hiding the information of the source, and the specific implementation is as follows:
[0026] S101: The data sent by the source can be expressed as X=(X 1 X 2 …X j ), a total of j dimensions, the number of dimensions here can be understood as a total of j-dimensional data to be sent, one of the one-dimensional data is sent in turn; each of the data in the dimension corresponds to an n-dimensional information vector X i ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com