Coding vector encryption based secure network coding method
A technology of encoding vectors and encoding methods, which is applied in the direction of public keys for secure communication, etc., can solve the problems of increased calculation and large number of encryptions, and achieve the effects of reducing the amount of encryption, ensuring integrity, and reducing complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
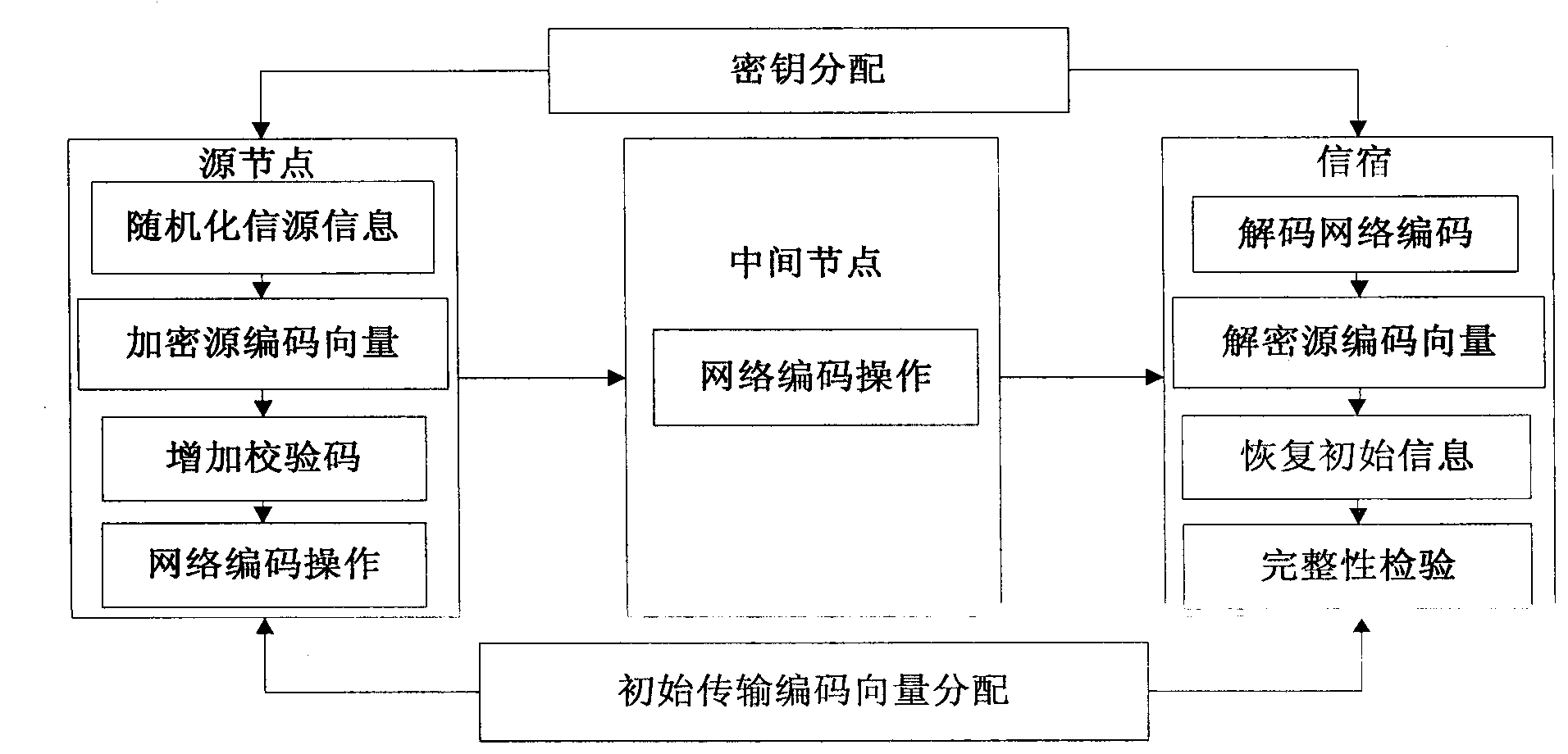
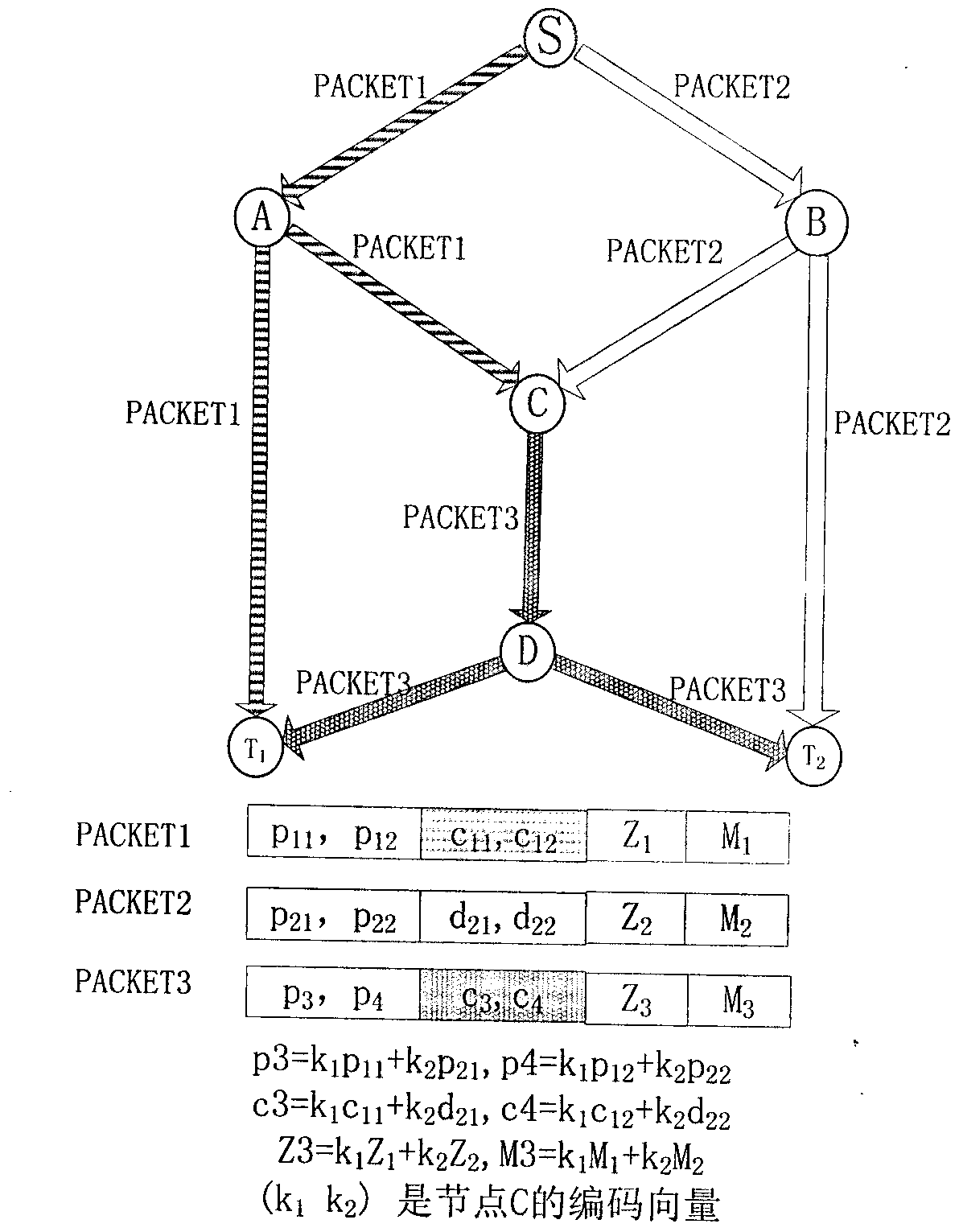
[0030] Here, first for Figure three In the classic butterfly network topology shown, a simple implementation method is given, and then generalized to the general form, and secure network coding is also implemented using the method of encrypting coding vectors. There are three types of data packets in the network, which are marked as PACKET1, PACKET2, and PACKET3 in the figure. PACKET3 is a linear combination of PACKET1 and PACKET2.
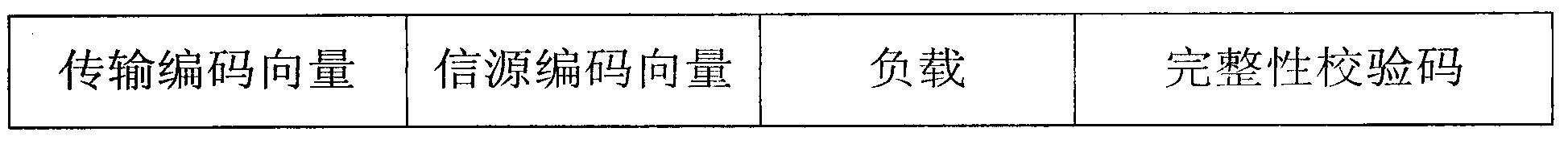
[0031] According to the introduction of the specific implementation process above, the check code can be obtained at the source S The loads obtained are Z 1 = P 11 (d 11 x 1 +d 12 x 2 )+p 12 (d 21 x 1 +d 22 x 2 ),Z 2 = P 21 (d 11 x 1 +d 12 x 2 )+p 22 (d 21 x 1 +d 22 x 2 ), the encoding vector P will be transmitted 2 =(p 11 p 12 ) And P 2 =(p 21 p 22 ) Are placed at the head of the package, D 1 =(d 11 d 12 ) Encrypted as C 1 =(c 11 c 12 ), D 2 =(d 21 d 22 ) Without encryption, replace C 1 And D 2 Into the second part of the package, and separate t...
Embodiment 2
[0037] Such as Figure Four As shown, the present invention is also applicable to other atypical network topologies. Three channels of data are sent from the source to the three sinks. 1 , T 2 , T 3 Although in the classic butterfly network, only one channel of information can be encrypted to ensure the confidentiality of the network, in the illustrated topology, at least two channels of information need to be encrypted to ensure the confidentiality of the network. It can be seen that if only one channel of information is blocked Encryption, the eavesdropper can obtain the original information of the source through the other two channels of information, which is generalized to the following theorem:
[0038] Theorem: Assuming that the source of information is k and the maximum flow of the network is n, after verification, it is necessary to encrypt at least k-n+1 channels of information to ensure the confidentiality of the network. Here, only the amount of encrypted information ca...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com