Secure multi-party computation privacy-protecting evaluation method based on scenes of internet of things
A secure multi-party computing, privacy protection technology, applied in computing, special data processing applications, user identity/authority verification, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0056] The process of the security multi-party computing privacy protection evaluation method based on the Internet of Things scenario can be described as follows:
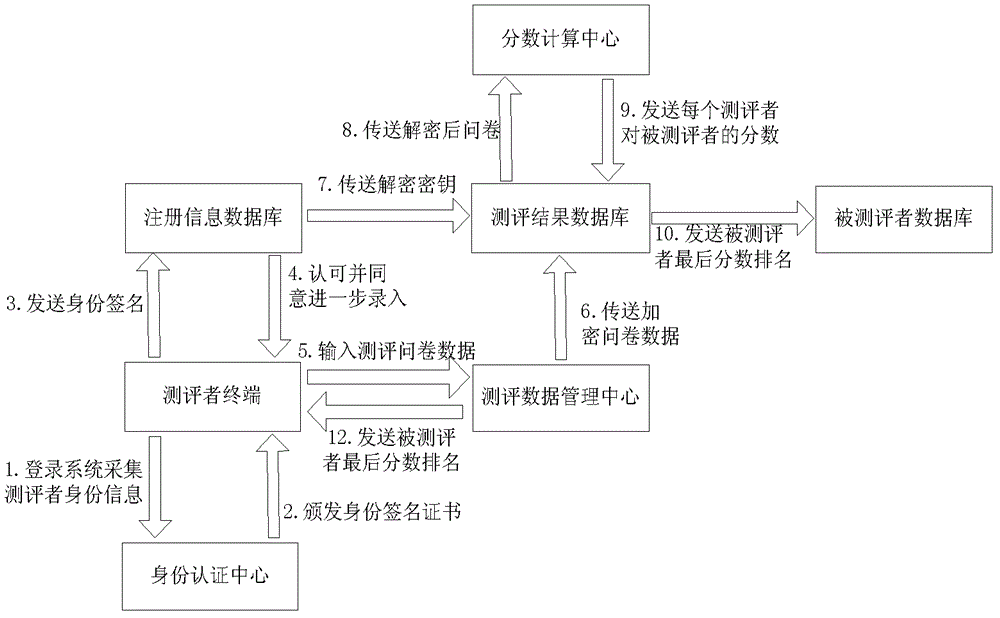
[0057] The scheme is composed of a collection of entities such as participants, an identity authentication center, a registration information database, an evaluation database center, an evaluation result database, a score calculation center, and an evaluator database. figure 1 shown:
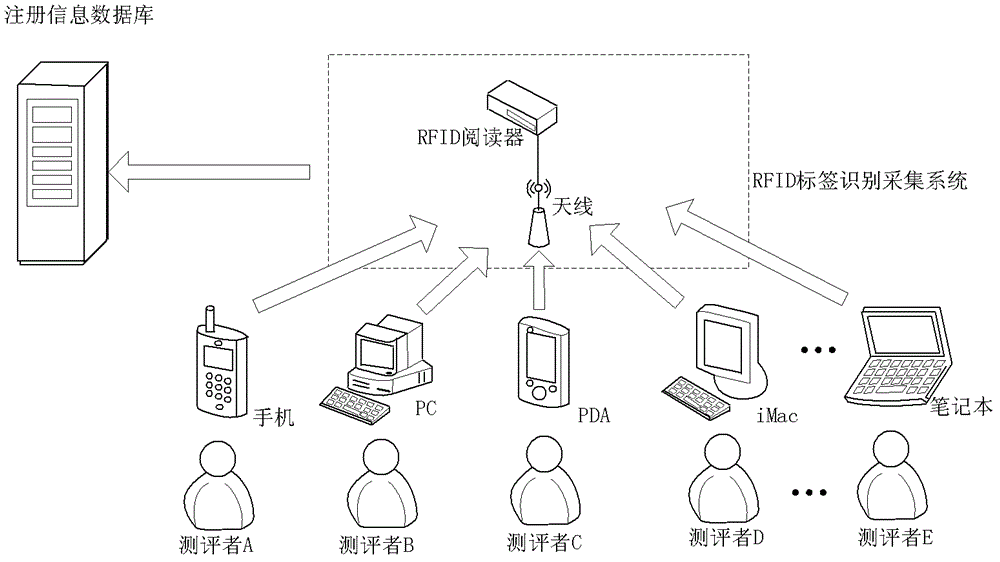
[0058] Step 1) Without loss of generality, it is assumed that there are n evaluators (n is a positive integer), these evaluators use different evaluation terminals in the Internet of Things to conduct online evaluations, and they identify their identity S i Stored in the radio frequency identification tag RFID attached to its terminal. When the evaluator uses the evaluation terminal for evaluation, the login system will automatically sense the RFID tag of the user terminal (such as figure 2 shown), and extract its identity S i A...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com