Identity management method used for mobile terminal and apparatus thereof
A technology for identity management and mobile terminals, applied in user identity/authority verification, security devices, secure communication devices, etc., can solve problems such as poor user experience, inability to manage in a unified way, troublesome and laborious, etc., to reduce the risk of identity leakage and realize The effect of unified management and avoiding duplication of development
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
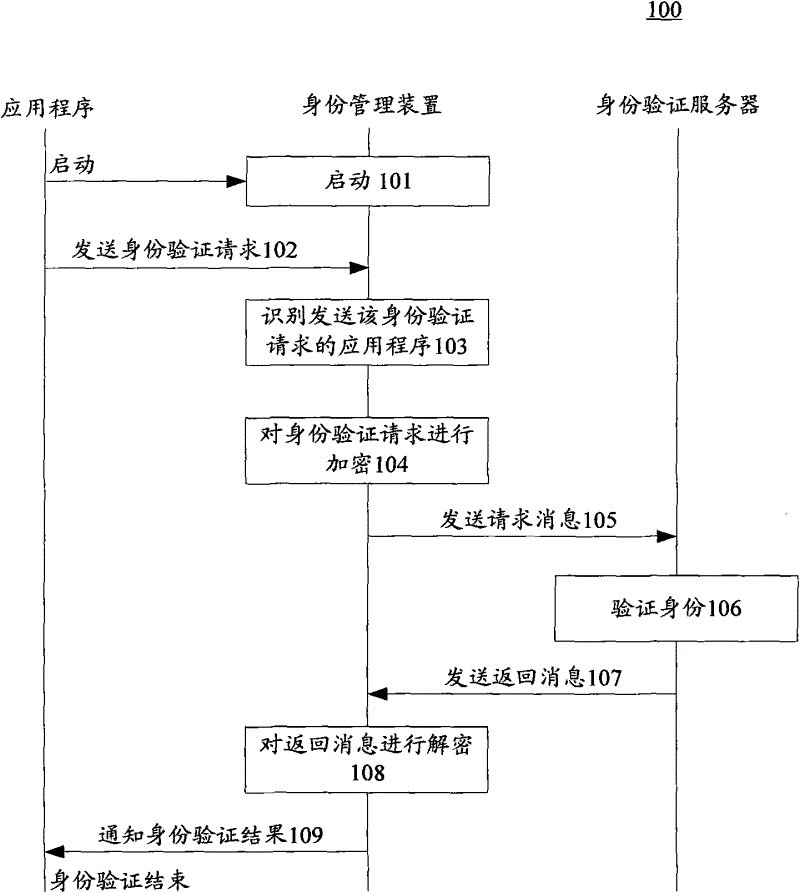
[0018] The identity management method and device proposed by the present invention aim to realize unified identity information management and unified identity verification of multiple application programs on a mobile terminal.
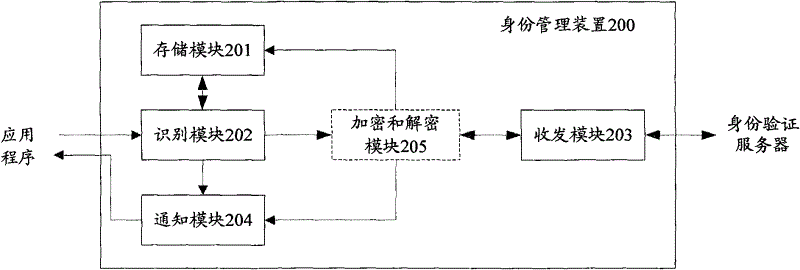
[0019] In the present invention, in order to provide identity verification services to multiple applications on the mobile terminal, and to avoid re-authentication of the identity that has passed the identity verification, when receiving an identity verification request from one of the multiple applications, identify The application program that sends the authentication request, and sends the request message generated according to the authentication request to the authentication server; and when receiving the return message from the authentication server, the authentication The result is notified to all applications in the related application list to which the identified application belongs.
[0020] In order to make the purpose, technical solution and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com