Method and device for adding and deciphering webpage enciphered data
A technology of encrypting data and symmetric encryption algorithm, applied in the network field, can solve the problems of affecting the loading speed of web pages, wasting system resources, reducing the user experience, etc., to achieve the effect of simple and convenient encryption and decryption, and improve the user experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
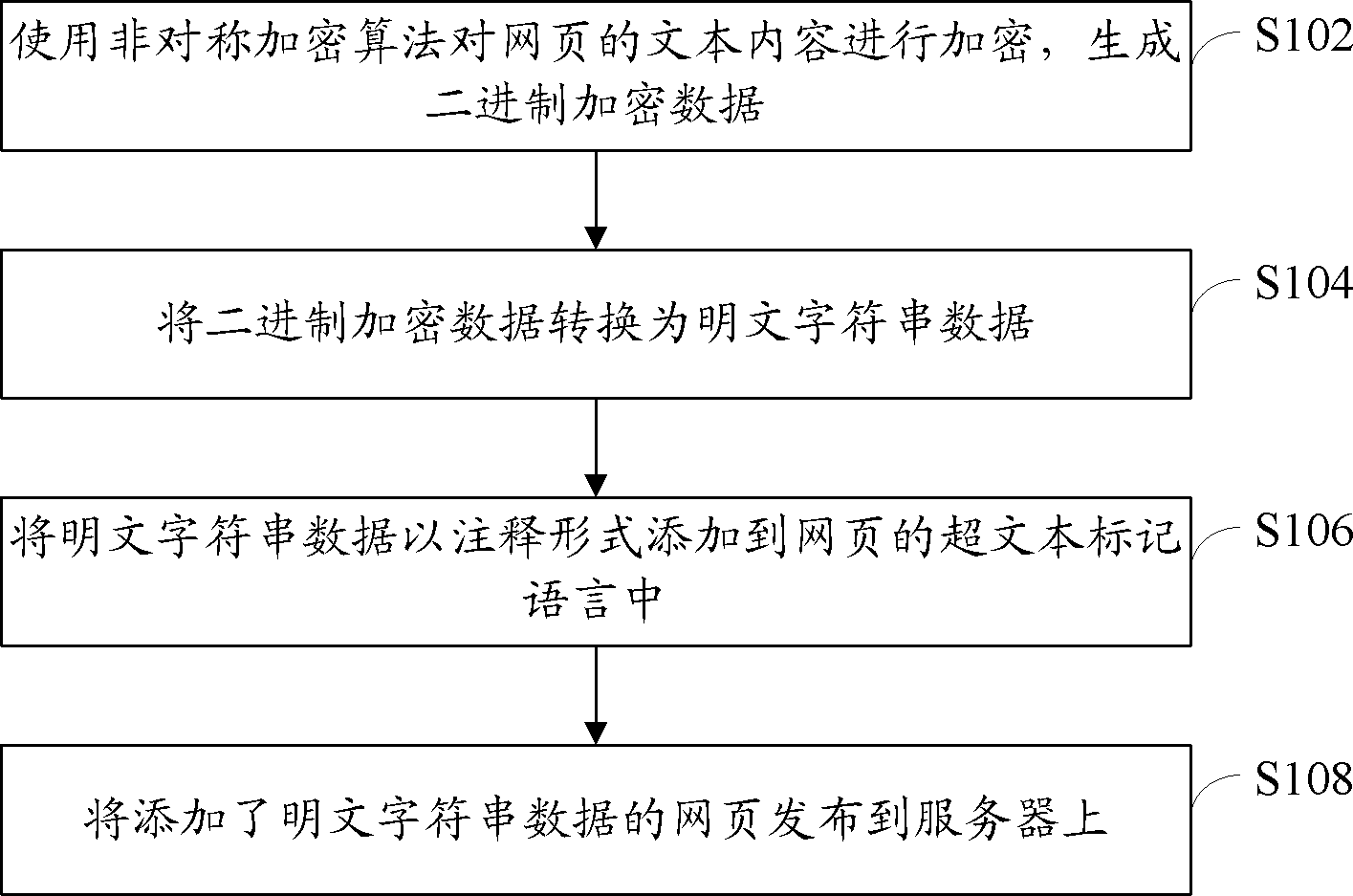
[0022] refer to figure 1 , shows a flow chart of steps of a method for adding encrypted webpage data according to Embodiment 1 of the present application.
[0023] The adding method of the webpage encryption data of the present embodiment comprises the following steps:
[0024] Step S102: Use an asymmetric encryption algorithm to encrypt the text content of the webpage to generate binary encrypted data.
[0025] An asymmetric encryption algorithm means that the key used for encryption is different from the key used for decryption, and the key for decryption cannot be derived from the encrypted key. Asymmetric encryption algorithm requires two keys: public key (publickey) and private key (privatekey). The public key and the private key are a pair. If the data is encrypted with the public key, only the corresponding private key can be used to decrypt it; if the data is encrypted with the private key, only the corresponding public key can be used to decrypt the data. decrypt. ...
Embodiment 2
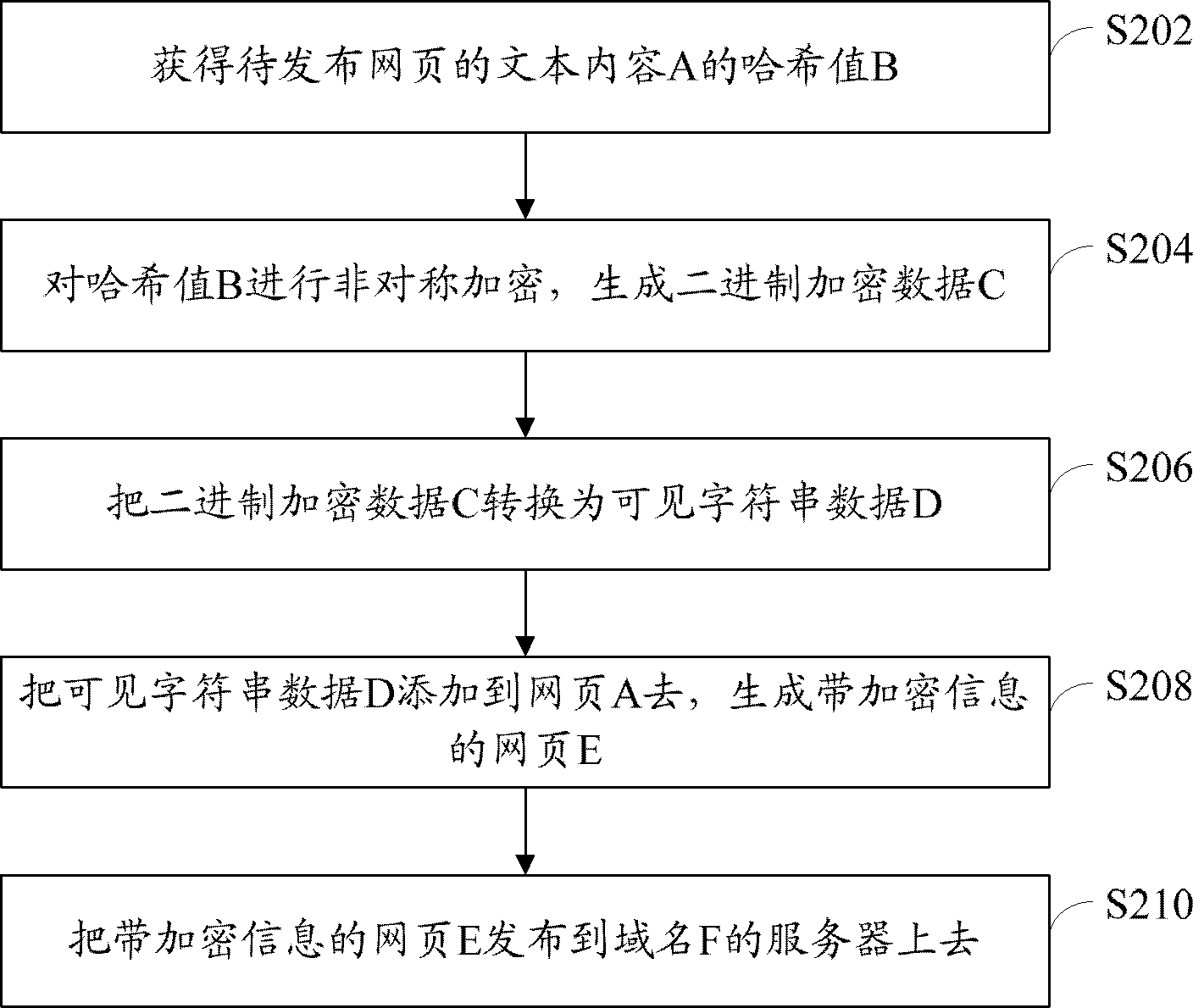
[0034] refer to figure 2 , shows a flow chart of steps of a method for adding encrypted webpage data according to Embodiment 2 of the present application.
[0035] When encrypting webpages, you can place the webpages to be encrypted on one or several fixed domain names F according to your needs, and then use the RSA algorithm to generate a pair of keys, namely the public key PKey (publickey) and the private key PrKey(privatekey). Then, integrate the verification logic into a browser such as 360 Secure Browser, where the verification logic uses Pkey, the release logic uses PrKey, and the format of the domain name F, key, and custom encryption are all pre-defined.
[0036] The adding method of the webpage encryption data of the present embodiment comprises the following steps:
[0037] Step S202: Obtain the hash value B of the text content A (character string) of the webpage to be published.
[0038] In this step, the text content of the webpage, such as the text content A o...
Embodiment 3
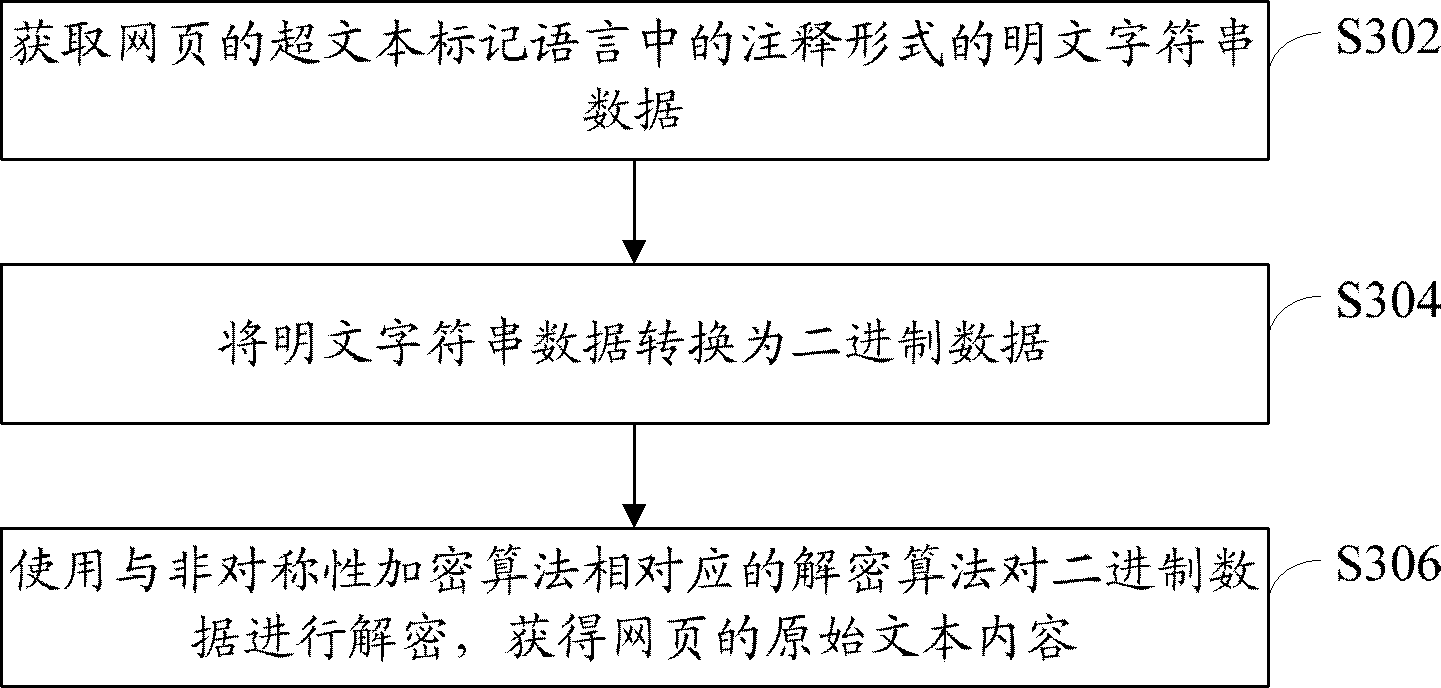
[0069] refer to image 3 , which shows a flowchart of steps of a method for decrypting encrypted webpage data according to Embodiment 3 of the present application.
[0070] The method for decrypting encrypted webpage data in this embodiment corresponds to the aforementioned method for adding encrypted webpage data, and is used to decrypt a webpage encrypted by using the aforementioned method for adding encrypted webpage data.
[0071] The decryption method of the webpage encrypted data of the present embodiment comprises the following steps:
[0072] Step S302: Obtain plain text string data in the form of comments in the hypertext markup language of the webpage.
[0073] Wherein, the plaintext character string data is the character string data obtained by converting the binary encrypted data generated by encrypting the original text content of the webpage with an asymmetric encryption algorithm.
[0074] Step S304: Convert plaintext character string data into binary data.
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com