Method for transmitting and operating application program, system for operating application program, server and terminal
A technology of application program and sending method, which is applied in the fields of operation method, application program sending, system, server and terminal, and can solve problems such as inability to satisfy application program security at the same time, and achieve the effect of ensuring security and normal operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
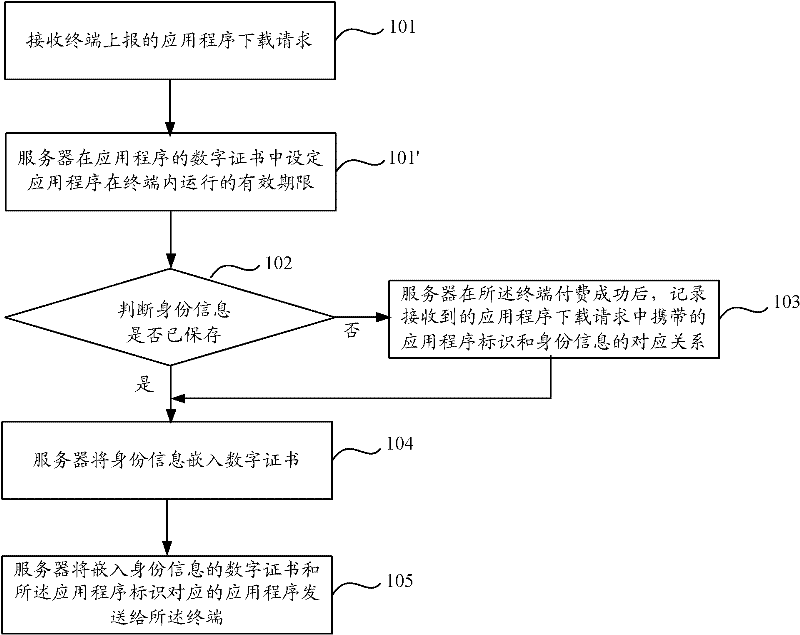
[0051] Embodiment 1 of the present invention provides a method for sending an application program. The steps of the method are as follows:figure 1 As shown, it specifically includes the following steps:
[0052] Step 101, receiving an application program download request reported by a terminal.
[0053] When a terminal needs to download an application program, it sends an application program download request to the server, and the application program download request carries identity information, and the identity information is used to determine the subject of the downloaded application program and to identify the user of the application program. Application ID of the application that the terminal requests to download.
[0054] Step 102, judging whether the identity information is the identity information corresponding to the application program identifier stored by the server.
[0055] In this step, the server may determine whether the saved identity information correspondin...
Embodiment 2
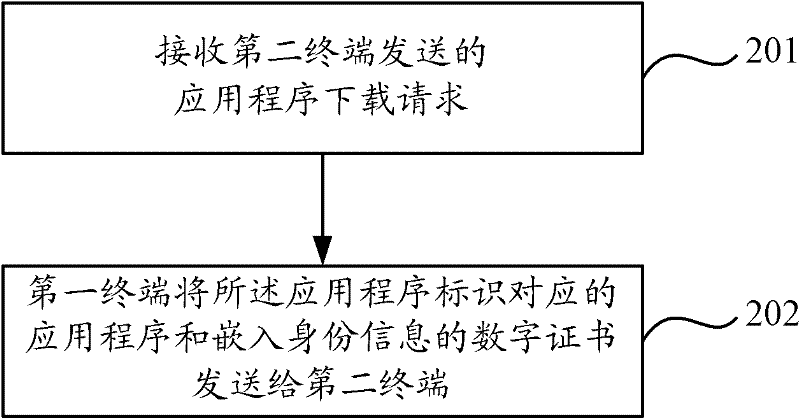
[0075] After the mobile terminal is replaced, the process of downloading the application program from the original mobile terminal by the replaced mobile terminal and running the application program normally will be described below. The original terminal is defined as the first terminal, and the replaced mobile terminal is defined as the second terminal. Then, Embodiment 2 of the present invention provides a method for sending an application from the perspective of the first terminal. The flow chart of the method is as follows image 3 As shown, it specifically includes the following steps:
[0076] Step 201. Receive an application program download request sent by a second terminal.
[0077] The application program download request carries the application program identification, and requests the first terminal to send the application program corresponding to the application program identification to the second terminal.
[0078] Step 202, the first terminal sends the applicat...
Embodiment 3
[0082] Embodiment 3 of the present invention provides a method for running an application program. The steps of the method are as follows: Figure 4 As shown, it specifically includes the following steps:
[0083] Step 301, the terminal receives a digital certificate embedded with identity information and an application program corresponding to the requested application program identifier.
[0084] In this embodiment, the digital certificate and the application program embedded with the identity information may be obtained by the terminal from the server or other terminals.
[0085] Step 302, the terminal runs the application program.
[0086] In this step, the terminal authenticates the identity information embedded in the received digital certificate, and the authentication specifically includes:
[0087] The terminal reads the locally stored identity information, and uses the locally stored identity information to authenticate the identity information embedded in the rece...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com