Method for managing access of multiple visitors to mobile terminal
A technology for accessing mobile terminals and management methods, applied in branch equipment, electrical components, security devices, etc., can solve problems such as the inability to meet user sharing needs, meet the needs of sharing mobile phone information, enhance user experience, and protect privacy. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
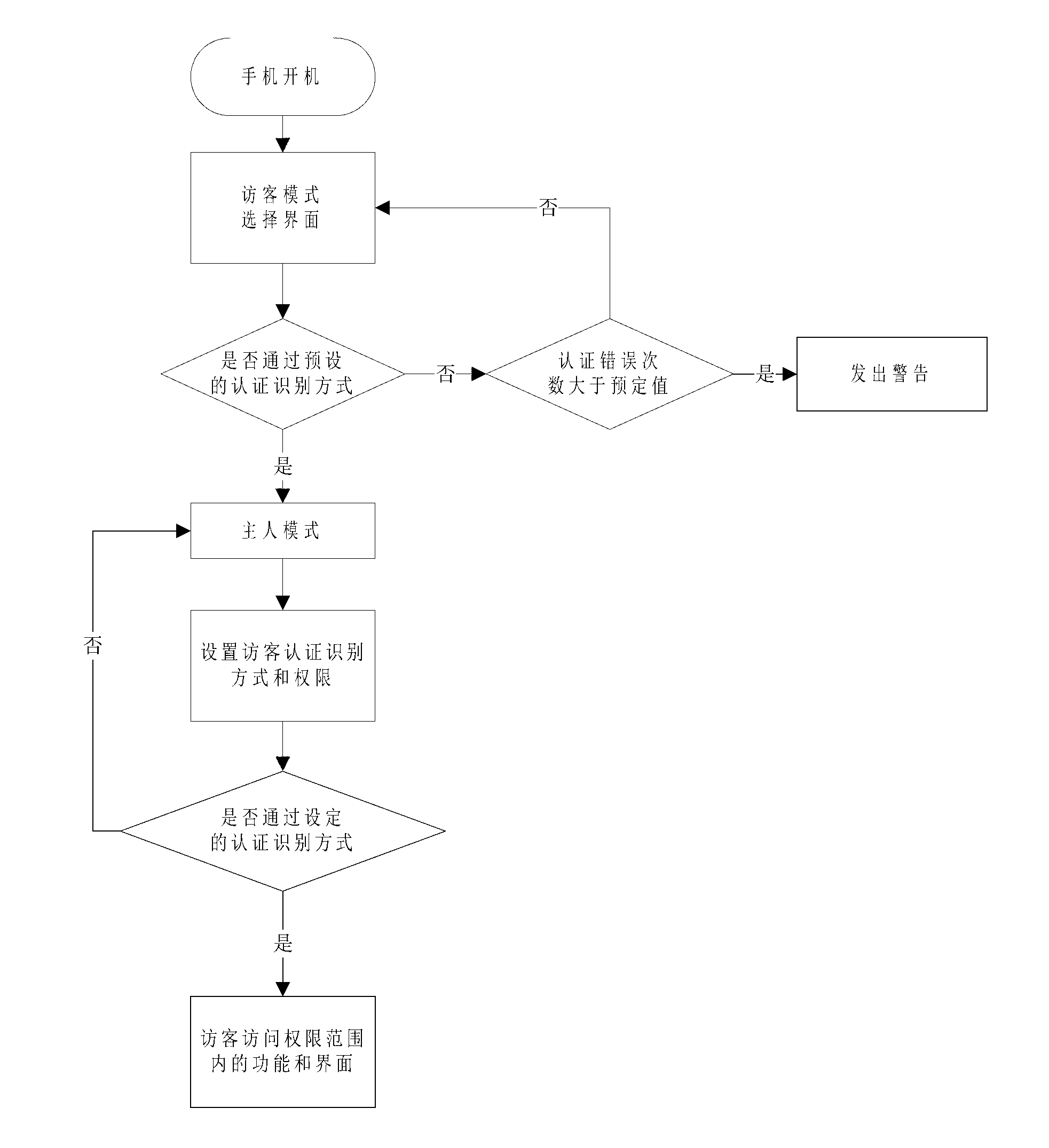
[0022] Such as figure 1 As shown, in an embodiment of a method for managing a multi-visitor access mobile terminal of the present invention, the method includes the following steps:
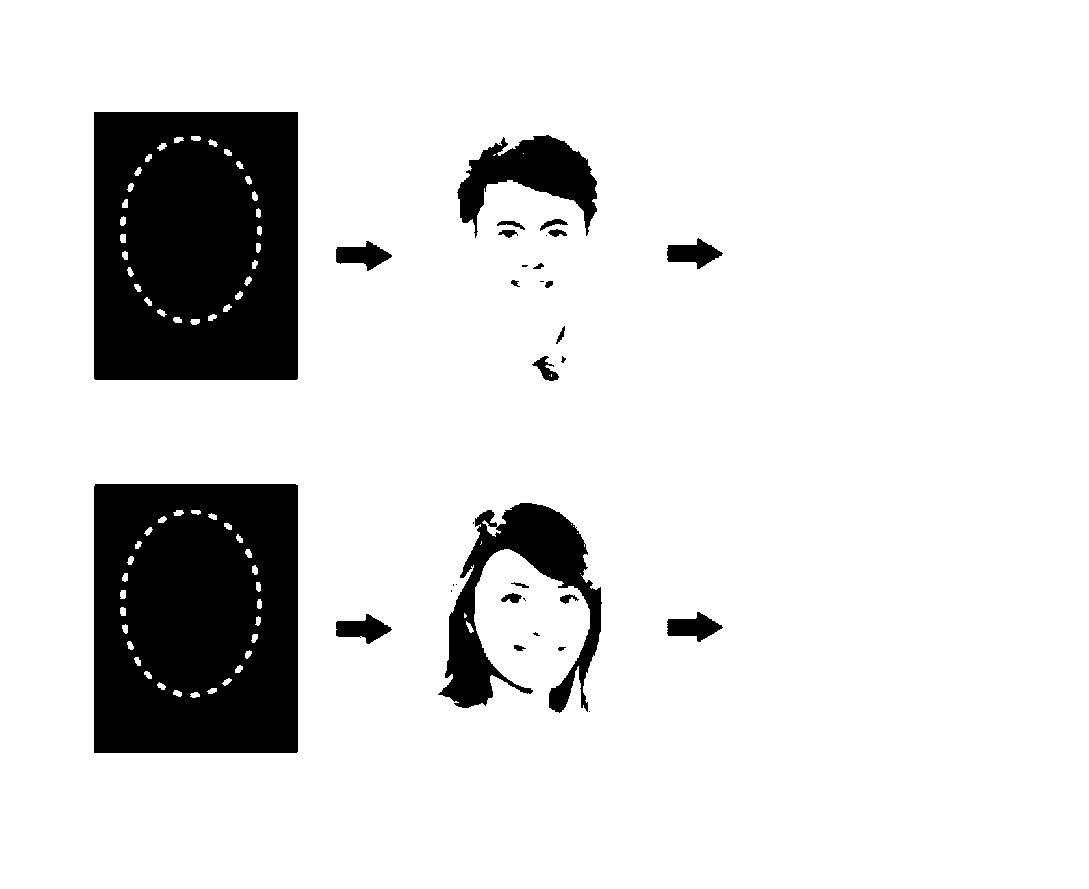
[0023] S1. Turn on the mobile phone and enter the visitor mode selection interface; S2. Through the preset authentication and identification method, the authentication and identification method can be set to Facebook, gesture or password. Such as figure 2 As shown, if it is set to facebook mode, the system determines whether to allow to enter the master mode by judging the comparison result between the input facebook information and the prestored facebook information; if the input facebook information is the same as the prestored facebook information, Then go to step S3 and enter the master mode; if not the same, turn back to the guest mode selection interface; the system counts the number of errors entered by the user, and when the number of errors entered by the user is greater than the numbe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com