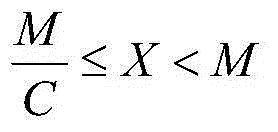Method and system for preventing semi-join attack
A technology of semi-connection and number of connections, which is applied in the field of network communication and can solve problems such as occupation, memory exhaustion of network equipment, and system crash of network equipment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] The specific implementation manners of the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments. The following examples are used to illustrate the present invention, but are not intended to limit the scope of the present invention.
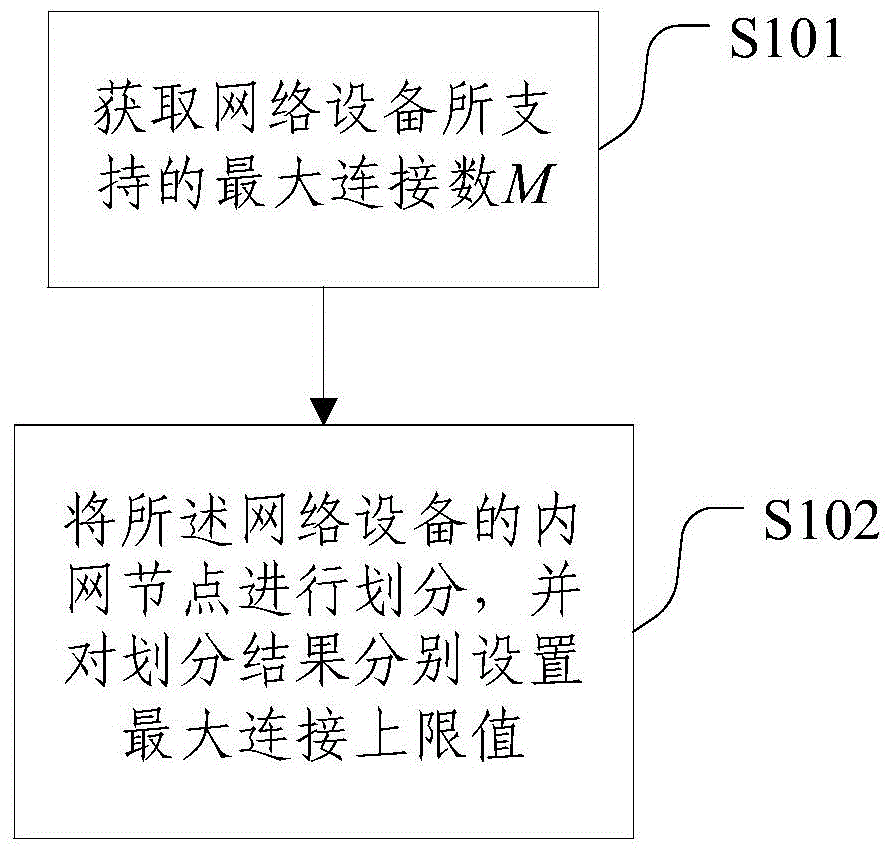
[0032] figure 1 It is a flowchart of a method for preventing semi-join attacks according to an embodiment of the present invention; refer to figure 1 , the method includes:
[0033] S101: Obtain the maximum number of connections M supported by the network device (the network device may be a firewall, a router, a switch, etc.), where the M is a positive integer greater than 0;
[0034] S102: Divide the intranet nodes of the network device, and respectively set maximum connection upper limit values for the division results.
[0035] The present invention can adopt two kinds of division methods, one is to divide the intranet ip address, and the other is to divide the int...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com