Method and device for safely producing intelligent key device
A technology of smart key equipment and safe production, which is applied to record carriers used by machines, instruments, digital mark record carriers, etc., and can solve problems such as message interception and insecure production process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
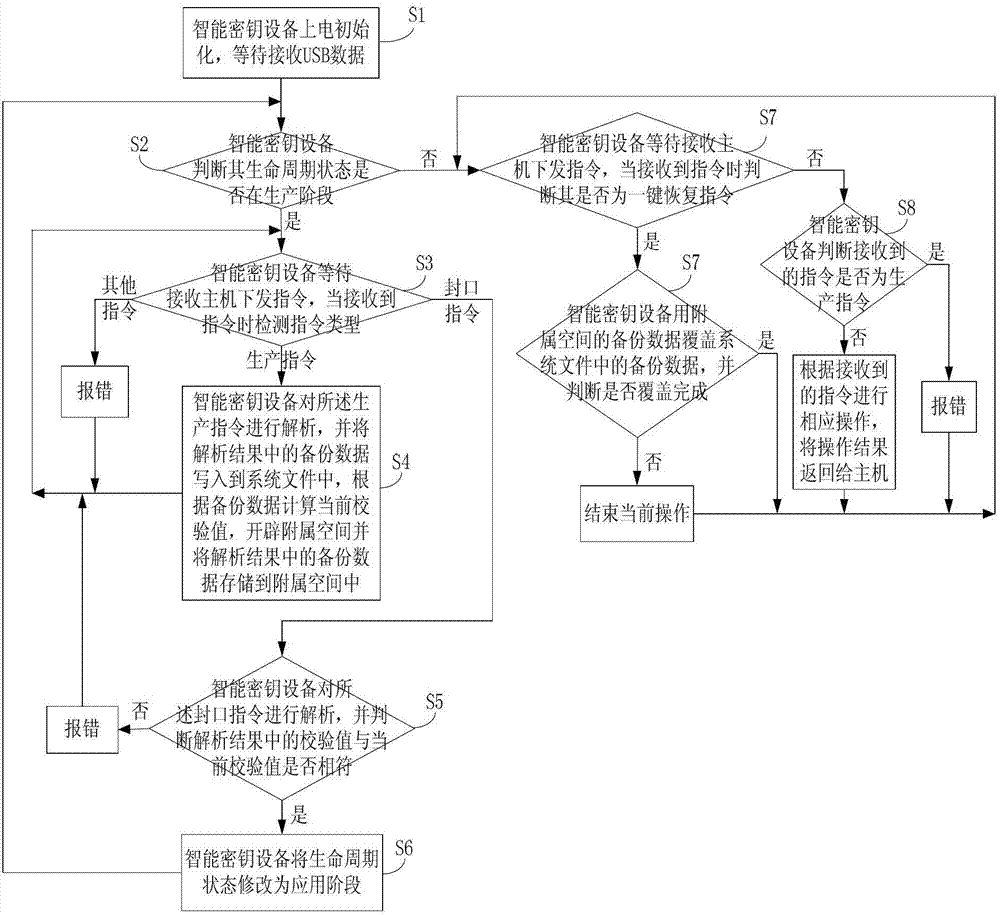
[0089] Embodiment 1 of the present invention provides a method for safely producing a smart key device. A log containing basic information of the smart key device is stored in the terminal. The basic information includes a PIN code, a production key, a key object, and a file object. and related hardware information, etc. Such as figure 1 As shown, the method includes:
[0090] Step S1: The smart key device is powered on and initialized, waiting to receive USB data;
[0091] Step S2: The smart key device judges whether its life cycle status is in the production stage, if yes, execute step S3, otherwise execute step S7;
[0092] Step S3: The smart key device waits for the command to be issued by the receiving host. When the command is received, the command type is detected. If it is a production command, execute step S4. If it is a sealing command, execute step S5. If it is another command, report an error and return to step S3;
[0093] Specifically, in this embodiment, the ...
Embodiment 2
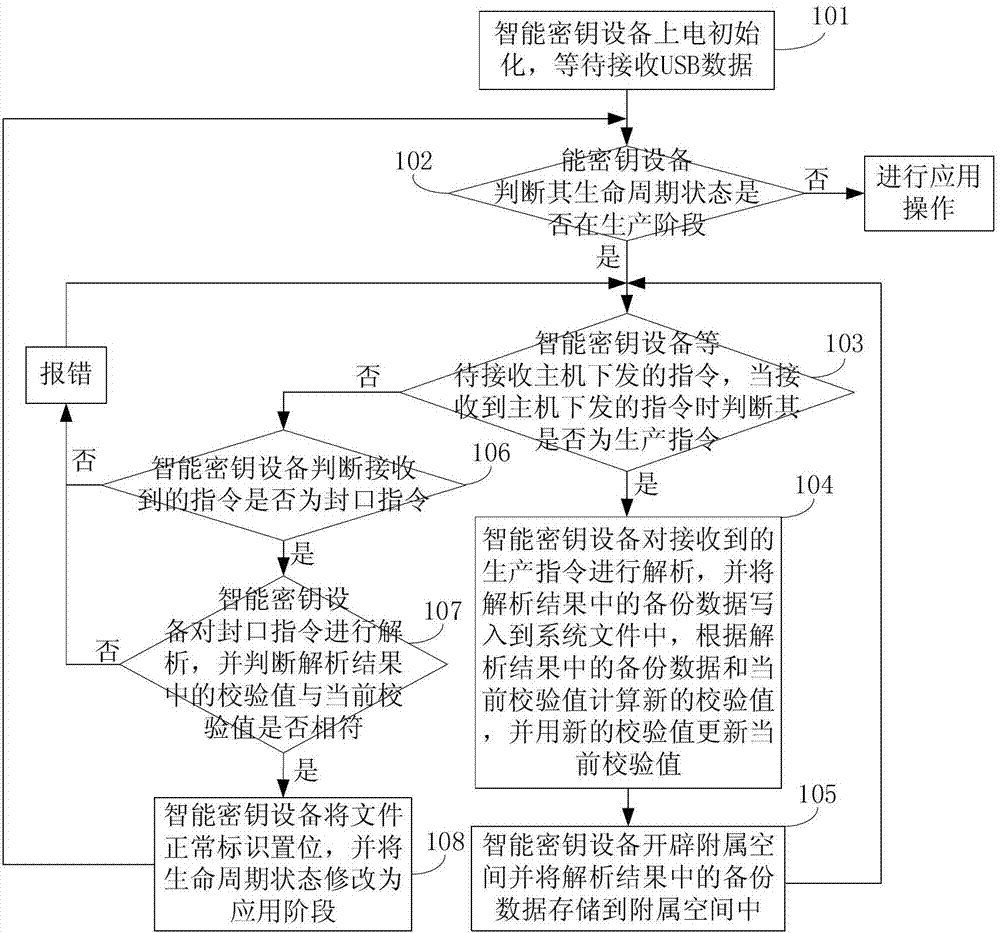
[0101] The second embodiment of the present invention provides a method for safely producing a smart key device, which is suitable for the production stage of the smart key device, and the backup data containing the basic information of the smart key device is stored in the terminal, and the basic information includes the PIN code , production keys, key objects, file objects, and related hardware information, etc. Such as figure 2 As shown, the method includes:
[0102] Step 101: The smart key device is powered on and initialized, waiting to receive USB data;
[0103] Step 102: The smart key device judges whether its life cycle status is in the production stage, if yes, execute step 103, otherwise perform application operation;
[0104] Step 103: The smart key device waits to receive an instruction issued by the host, and when receiving an instruction issued by the host, judges whether it is a production instruction, if yes, execute step 104, otherwise execute step 106;
...
Embodiment 3
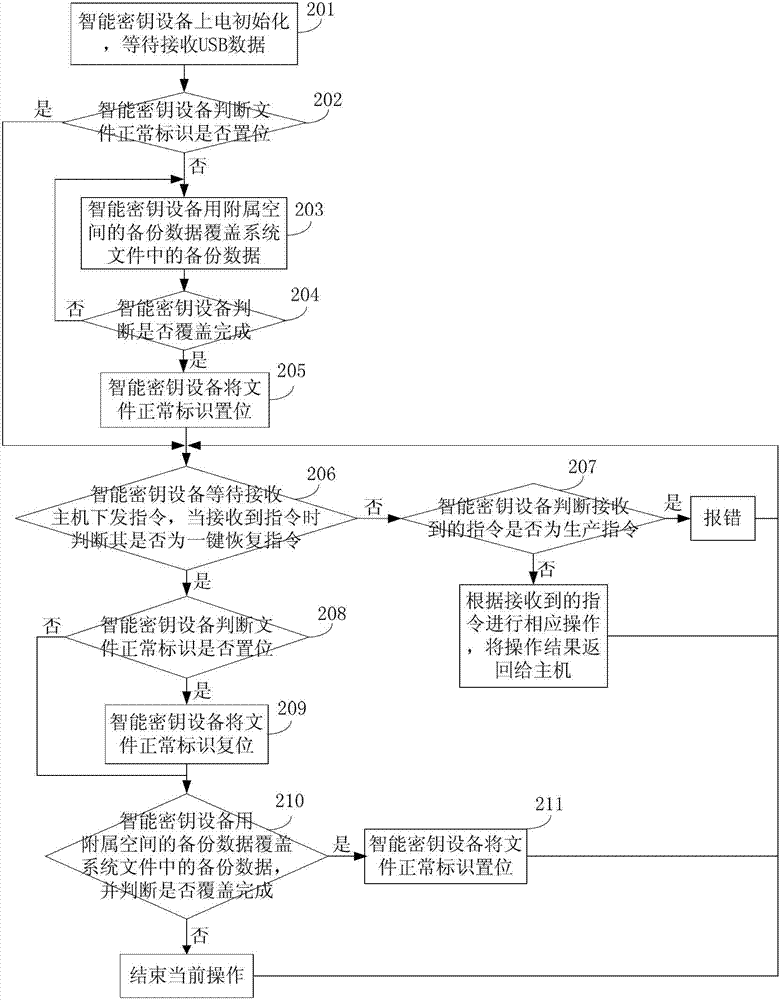
[0119] The third embodiment of the present invention provides a method for securely producing a smart key device, which is suitable for the application stage of the smart key device, and the backup data containing the basic information of the smart key device is stored in the terminal, and the basic information includes the PIN code , production keys, key objects, file objects, and related hardware information, etc. Such as image 3 As shown, the method includes:
[0120] Step 201: The smart key device is powered on and initialized, waiting to receive USB data;
[0121] Step 202: The smart key device judges whether the normal flag of the file is set, if yes, execute step 206, otherwise execute step 203;
[0122] Step 203: the smart key device overwrites the backup data in the system file with the backup data in the auxiliary space;
[0123] Specifically, in this embodiment, if the backup data in the auxiliary space is compressed data, first decompress the compressed backup ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com