Safety parameter modification method and base station
A security parameter and base station technology, applied in the field of communication, can solve problems such as waste, multiple transmission resources and processing resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
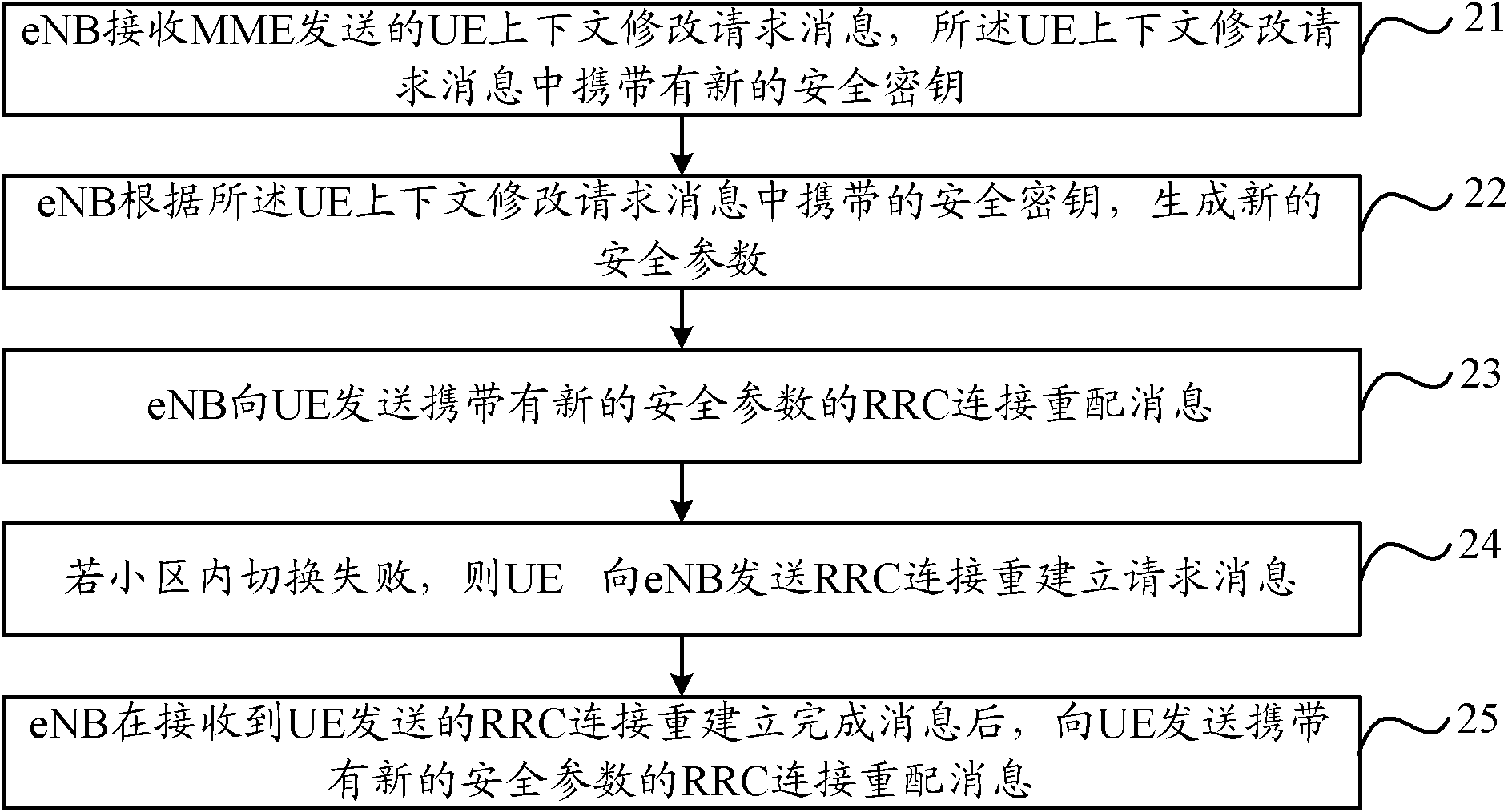
Image
Examples
Embodiment 1
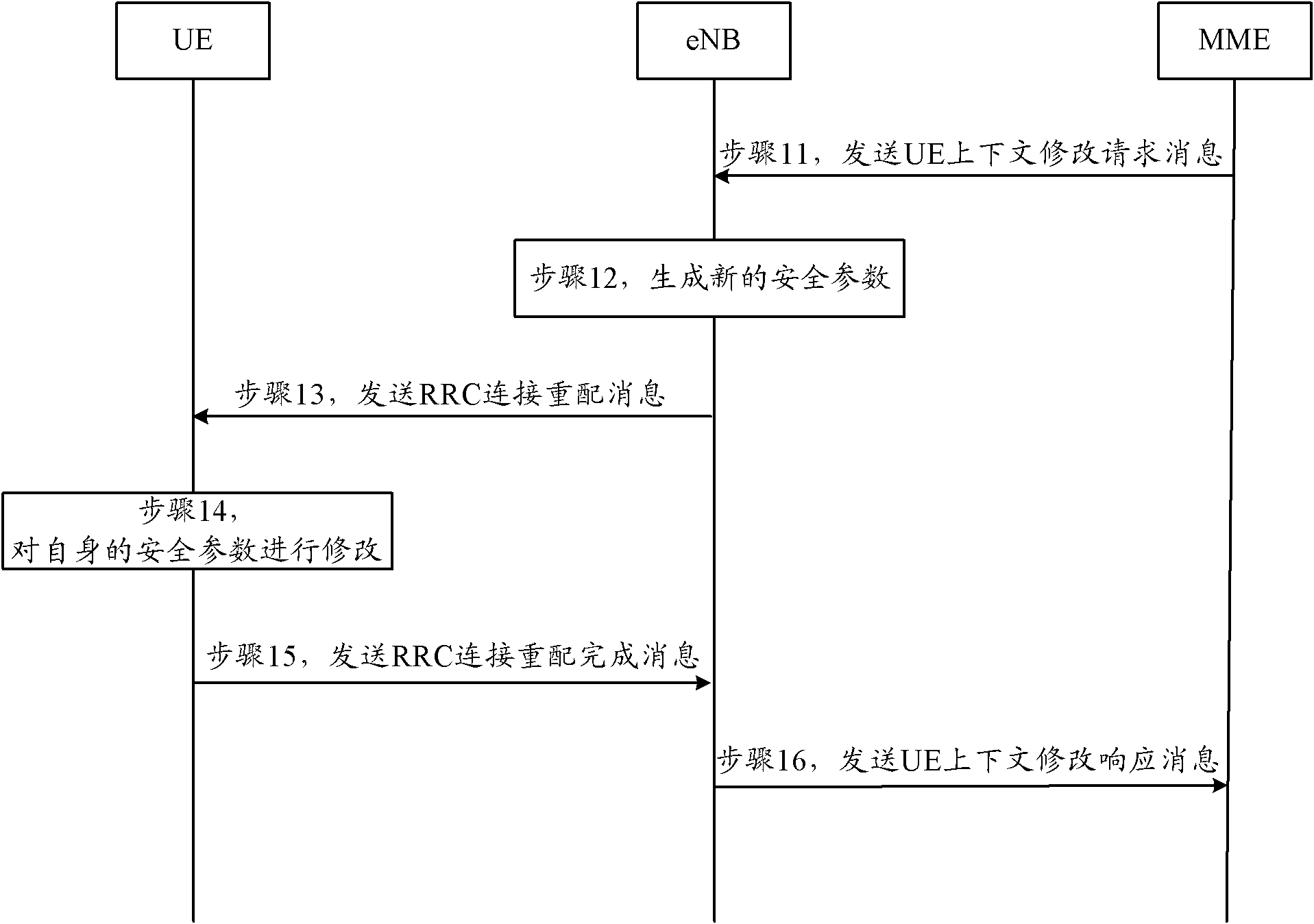
[0043] During the process of data upload and video call, the eNB receives the UE context modification request message issued by the MME, requesting to modify the security parameters. Before the eNB receives the UE context modification request, the next hop (NH, Next Hop) key is 5 , the next hop counter (NCC, Next hop Chaining Counter) is 1, and the new security key K generated by MME eNB for 10.
[0044] Such as image 3 As shown, it is a schematic flow diagram of the specific implementation flow of the security parameter modification method in Embodiment 1 of the present invention, and its specific processing process is as follows:
[0045] Step 31: During the UE data upload and video call process, the core network triggers the security parameter modification process, and the MME sends a UE context modification request message to the eNB, and the UE context modification request message carries a new security key K eNB ;
[0046] Step 32: After receiving the UE context modi...
Embodiment 2
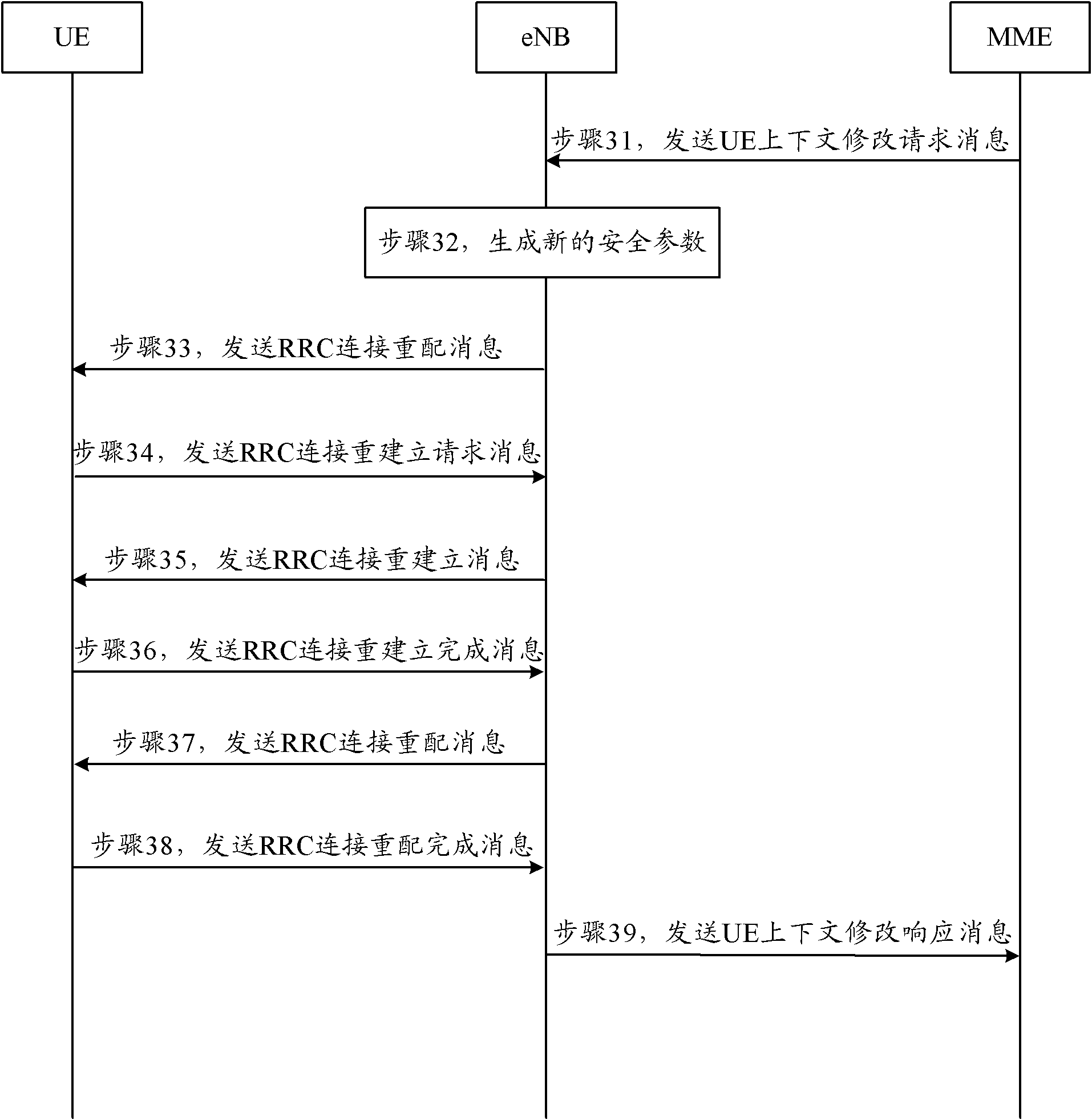
[0055] During data upload, the eNB receives a UE context modification request message issued by the MME to modify security parameters. Before the eNB receives the UE context modification request, the next hop (NH, Next Hop) key is 5, and the next hop The counter (NCC, Next hop Chaining Counter) is 1, and the new security key K generated by MME eNB for 10.
[0056] Such as Figure 4 As shown, it is a schematic flow diagram of the specific implementation flow of the security parameter modification method in Embodiment 2 of the present invention, and its specific processing process is as follows:
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com