Speech input authentication method and device
A voice input and voice technology, applied in voice analysis, security devices, voice recognition, etc., can solve the problems of high error probability and high misoperation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] The present invention will be further described below in conjunction with accompanying drawing.
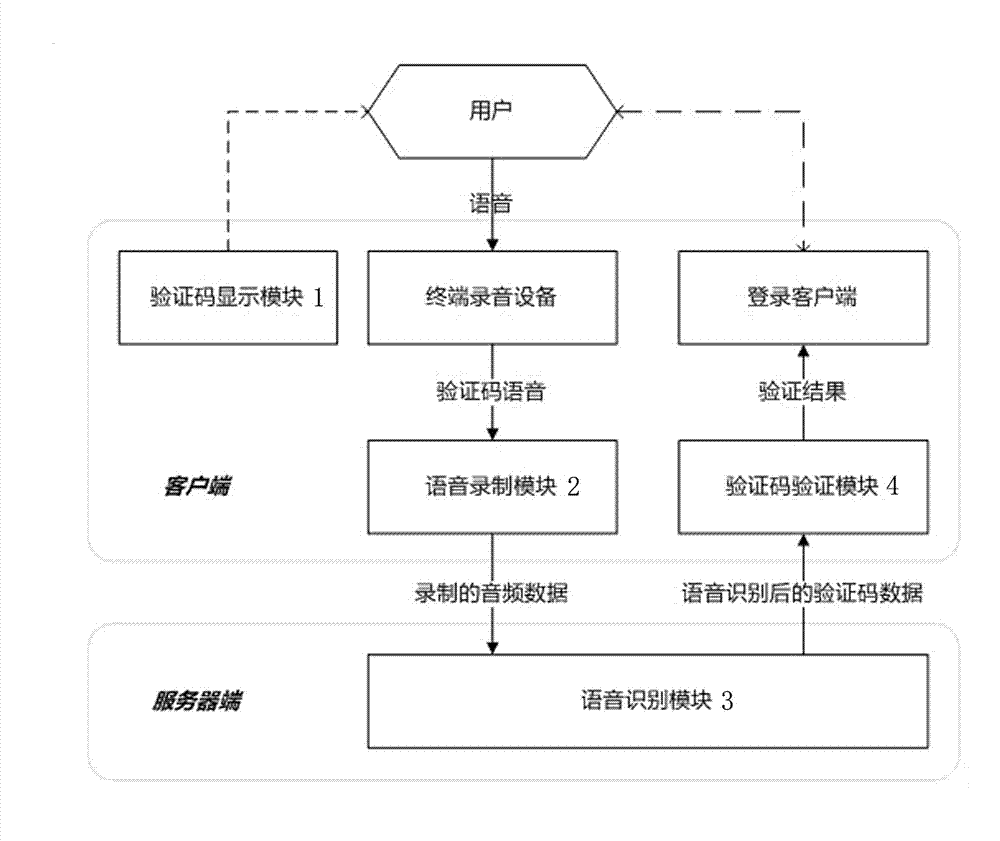
[0024] The voice input verification device of the present invention includes: a verification code display module 1 , a voice recording module 2 , a voice analysis and recognition module 3 , and a verification code verification module 4 . The verification code display module 1 is used to display pictures or videos with verification codes. The pictures or videos can be advertisement pictures or advertisement videos; speech; the speech analysis and recognition module 3, carries out the analysis and recognition operation through relevant algorithms, and obtains specific results, such as Arabic numerals, English letters, special symbols or Chinese characters, and the relevant algorithms can adopt the software sdk provided by the android system or iflytek The algorithm in the verification code verification module 4, compares the currently displayed verification code information a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com