Access control method and device
A technology of permission control and permission configuration, applied in the field of network security, can solve the problem that the RBAC model cannot meet the resource flexibility requirements, and achieve the effect of reducing complexity and management overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] In order to make the above objects, features and advantages of the present application more obvious and comprehensible, the present application will be further described in detail below in conjunction with the accompanying drawings and specific implementation methods.
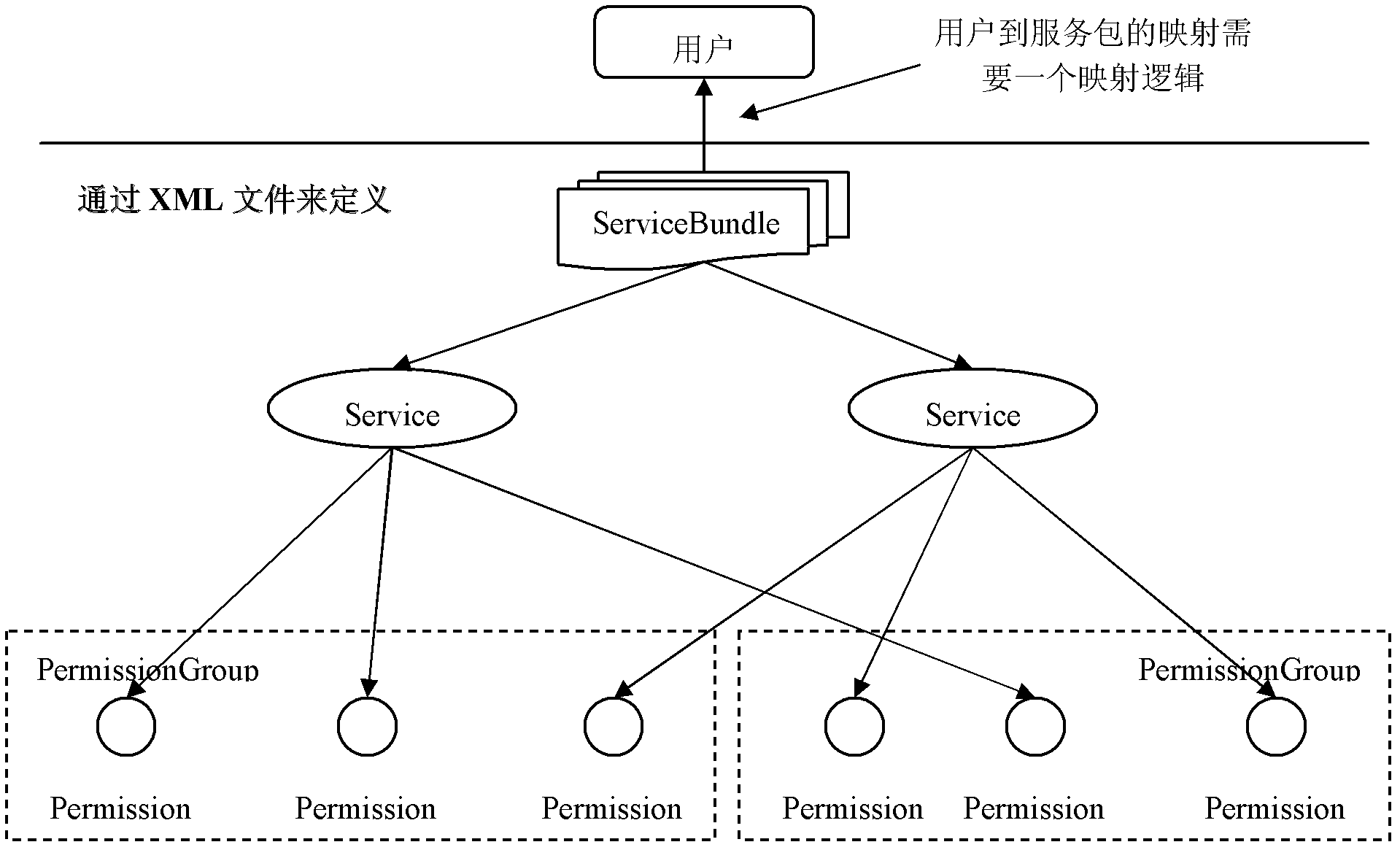
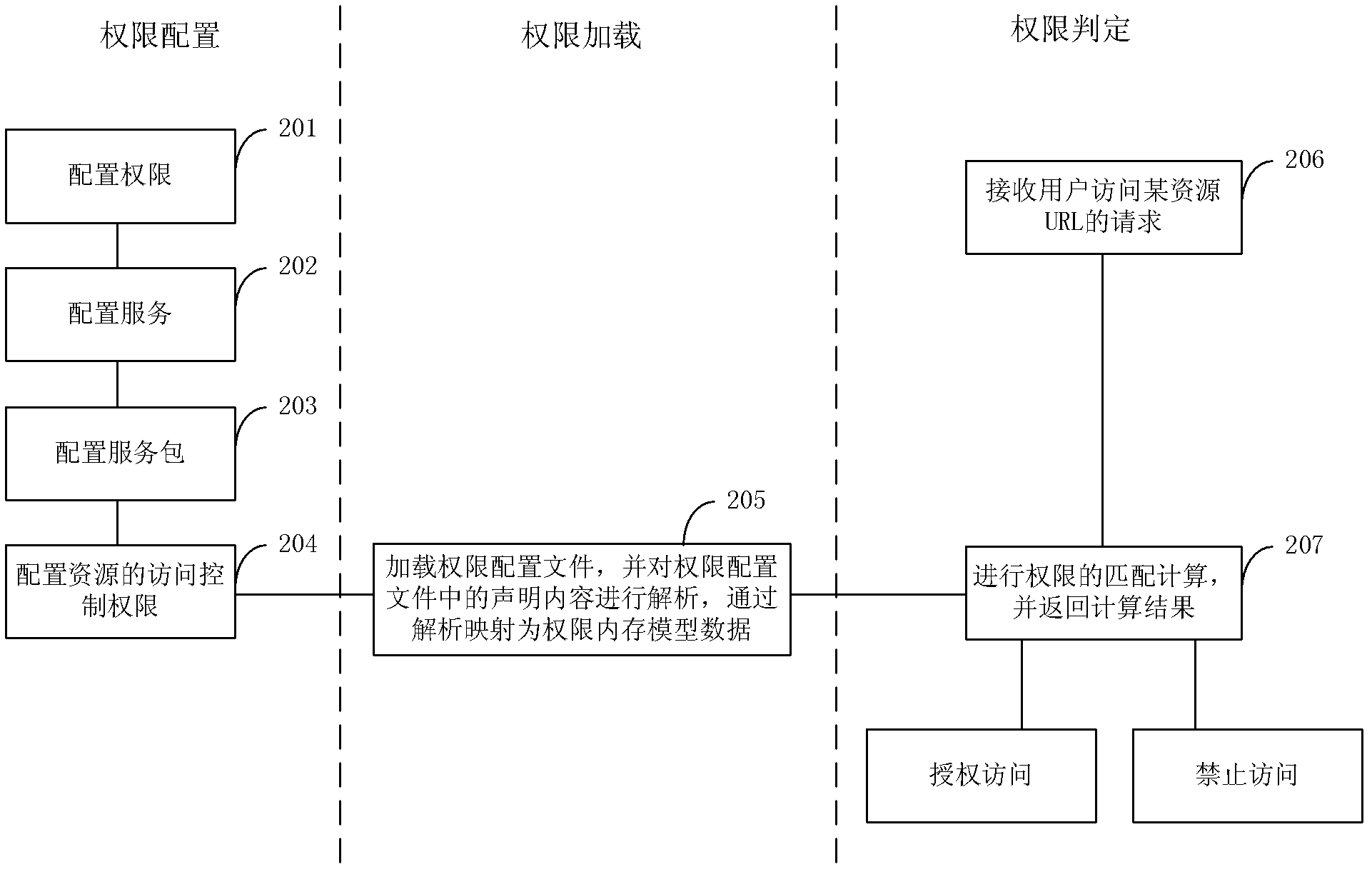
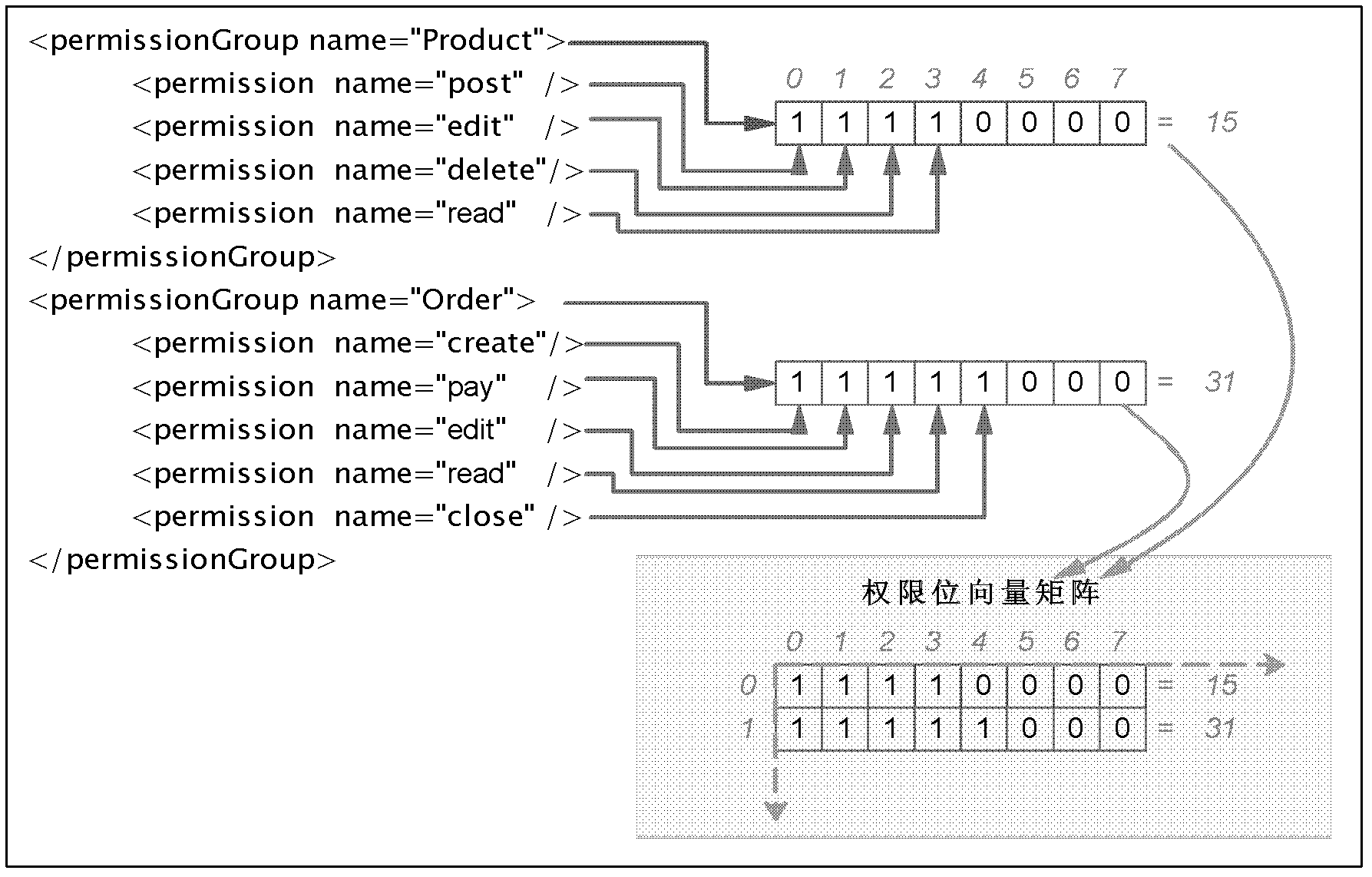
[0048]With the development of website business, websites provide service functions in the form of services or service packages, and the applications of services and service packages are becoming more and more extensive. Based on this, this application proposes an efficient and flexible authority control method, which can directly divide business functions into authority, service and service package according to the business definition, and control the access of website resources according to this division. Of course, the method described in this application is not limited to the authority control of website resources, that is, it is independent of website business functions, and can also be applied to oth...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com