Method and equipment for generating business code from fingerprint image
A fingerprint image and business password technology, which is applied in the field of generating business passwords from fingerprint images and in the security field, can solve problems such as failure to generate business passwords, small collections, and high probability of fingerprints generating the same number
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] Specific embodiments of the present application will be described below with reference to the accompanying drawings.
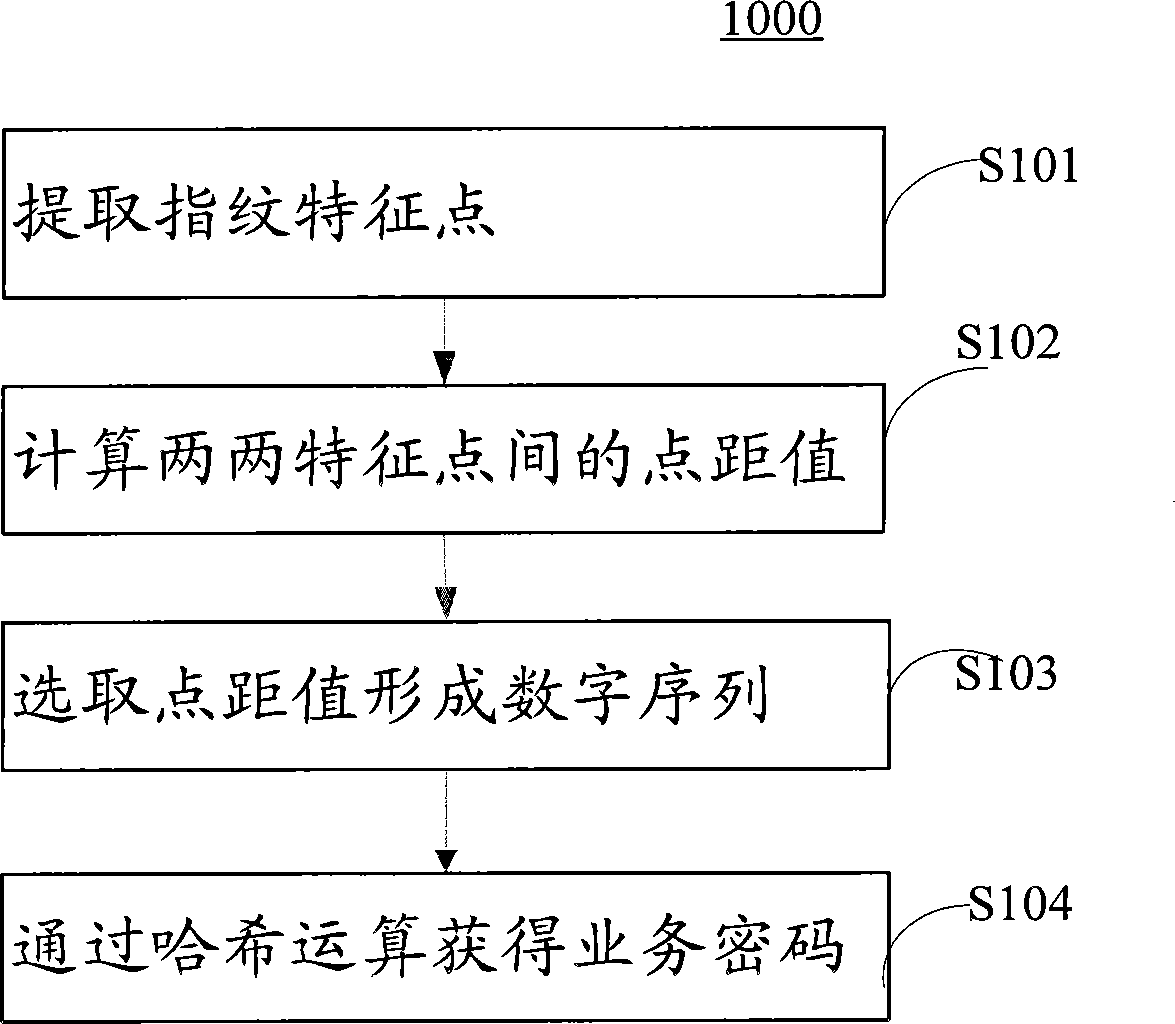
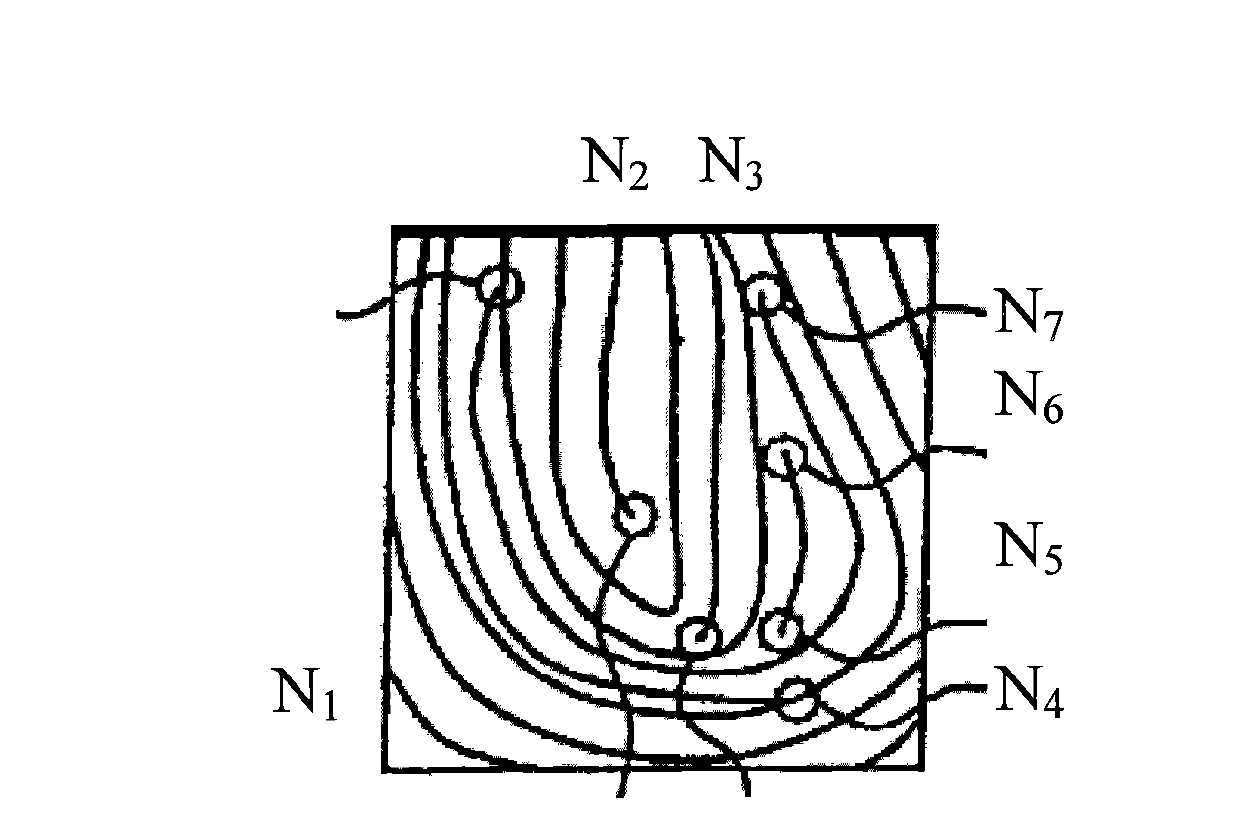
[0019] figure 1 A method 1000 of generating a business password from a fingerprint image according to an embodiment of the present application is shown. like figure 1 As shown, in step S101, a plurality of fingerprint feature points are extracted from the collected fingerprint image. Fingerprint feature points can be extracted by, for example, techniques known to those skilled in the art, and fingerprint feature points include, but are not limited to, intersections and endpoints of ridges. The fingerprint image may, for example, be entered by a user on a fingerprint entry device of a terminal device, where the terminal device includes but is not limited to a USB handset.
[0020] In step S102, the point distance value between the two feature points is calculated according to the extracted fingerprint feature points. In an example, a coordinate syste...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com