Data encryption method and device
A data confidentiality and data technology, applied in the field of electronic information, can solve problems such as increasing user workload, reducing user experience, and consuming user time, so as to improve user experience, reduce the frequency of password input, and save time and workload. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
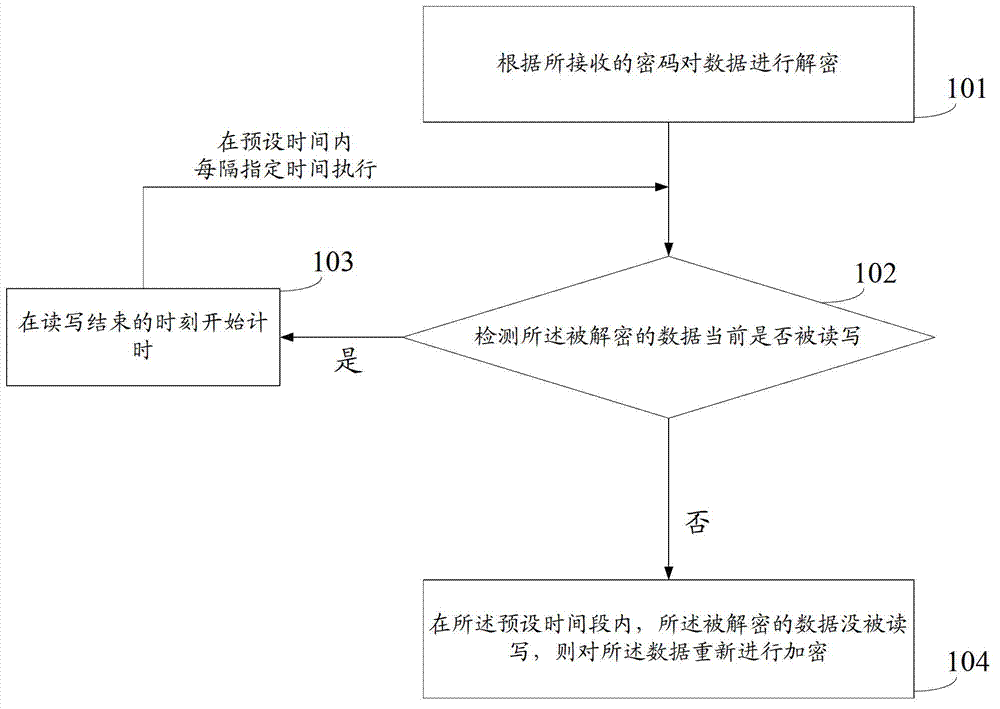
[0030] The embodiment of the present invention provides a data security method, such as figure 1 shown, including:
[0031] It should be noted that, in this embodiment of the present invention, a terminal device for executing the method of the present invention may be a terminal device, such as a smart phone, a mobile computer or other portable terminals, or a personal computer or an electronic reader, etc. equipment.
[0032] Step 101, decrypt the data according to the received password.
[0033] In this embodiment, the terminal device can decrypt the data according to the received password through existing technical means, and the source and location of the decrypted data are not limited, for example, it can be stored in the memory of the terminal device itself It can also be data stored in other devices and the terminal device can directly obtain these data from other devices.
[0034] Step 102: Detect whether the decrypted data is currently being read or written.
[00...
Embodiment 2
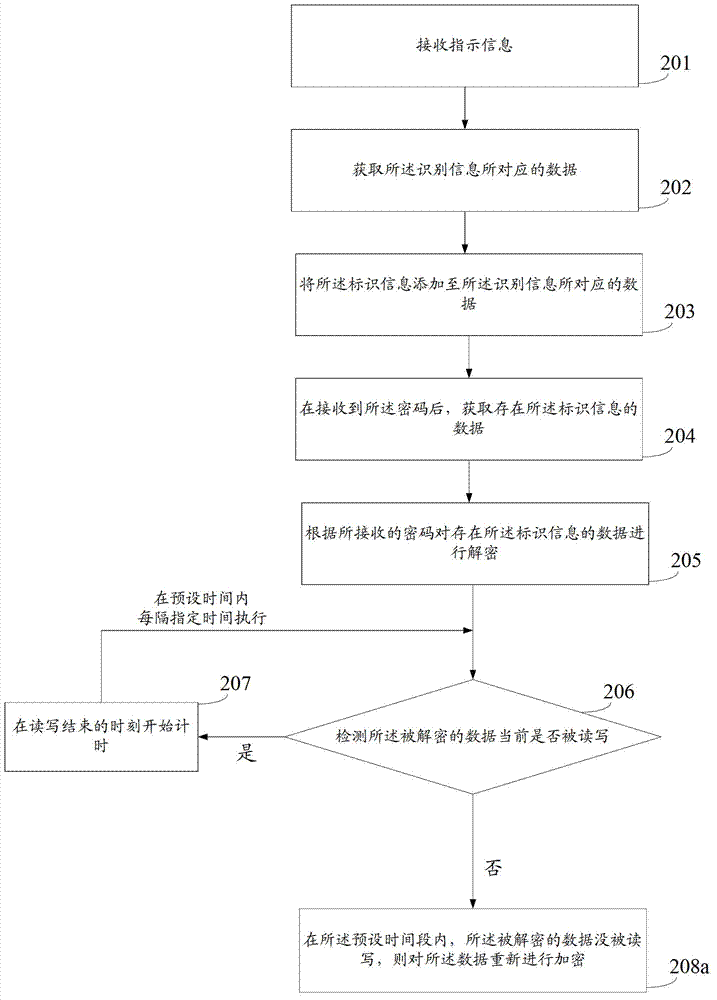
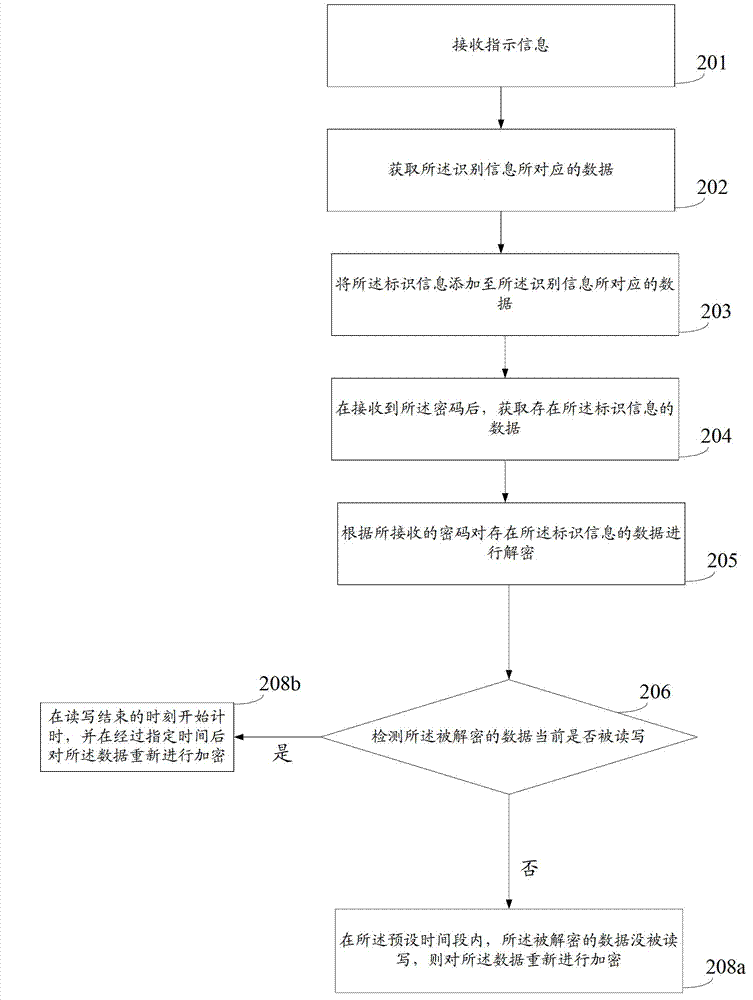
[0046] The embodiment of the present invention provides a data security method, such as Figure 2a shown, including:
[0047] Step 201, receiving indication information.
[0048] Wherein, the indication information includes the identification information and identification information.
[0049] In this embodiment, the terminal device can receive the indication information input by the user through the input device, the indication information is used to instruct the terminal device to mark the data specified by the user, and the identification information included in the indication information is used for the terminal device to identify the data specified by the user. Designated data, the identification information is used to mark the data designated by the user corresponding to the identification information.
[0050] It should be noted that the identification information, the specific information format of the identification information, and the specific implementation for ...
Embodiment 3
[0076] The embodiment of the present invention provides a data security device, such as image 3 shown, including:
[0077] The decryption module 31 is used for decrypting the data according to the received password.
[0078] The detection module 32 is configured to detect whether the decrypted data is currently being read or written every specified time.
[0079] The timing module 33 is configured to start timing when the read and write ends when the detection module detects that the decrypted data is currently being read and written.
[0080] The encryption module 34 is configured to re-encrypt the data if the decrypted data has not been read or written within the preset time period.
[0081] The file encryption device provided by the embodiment of the present invention can not re-encrypt the data that is being read or written within a specified time after the data is decrypted, and if the decrypted data is not used within the preset time, the decrypted data to re-encrypt...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com